Information se cur ity.
advertisement

Information secur
ity. The pr otection of information and information
systems against unauthorized access or modi¼cation of information,
whether in storage, processing, or transit, and against denial of service
to authorized users.
Information Operations. J oint Chiefs of S taff of the U nited S tates
Armed Forces, Joint Publication 3-13 (13 F ebruary 2006).
Principles of Computer System Design Saltzer & Kaashoek
2009
Complete mediation
Fo r e very requ este d ac tion, c hec k au thenticity , integ rity, and autho rization.
Principles of Computer System Design Saltzer & Kaashoek
2009
Curren t
Bad
Principles of Computer System Design Saltzer & Kaashoek
2009
Open design principle
Let any one comm ent on the de sig n. You need all th e help you can get.
Principles of Computer System Design Saltzer & Kaashoek
2009
Minimize secrets
Because the y proba bly won ’t remain se cret for lo ng.
Principles of Computer System Design Saltzer & Kaashoek
2009
Economy of mechanism
Th e less th ere is, the mo re like ly yo u will g et it righ t.
Principles of Computer System Design Saltzer & Kaashoek
2009
Minimize common mechanism
Sh ared me cha nisms p ro vide unwante d co mmun ica tion p aths.
Principles of Computer System Design Saltzer & Kaashoek
2009
Fail-safe defaults
Most use rs won’t chan ge the m, so make sure th at defa ults do someth ing safe
Principles of Computer System Design Saltzer & Kaashoek
2009
Least privilege principle
Don ’t sto re lunch in the safe with th e jewels.
Principles of Computer System Design Saltzer & Kaashoek
2009
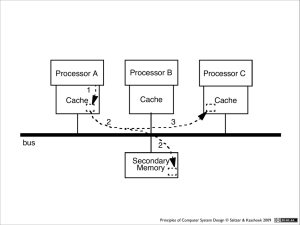
Comp uter system
au then ticatio n
mo dule
pri nci pal
au thori za tion
mo dule
yes/no
au thori ze d? yes/no
req uest
pe rform action
au then tic?
gu ard
OK
pe rform
actio n
ob ject
au dit trail
lo g
Principles of Computer System Design Saltzer & Kaashoek
2009
Requ est
Prin cip al
To : se rvi ce
Fro m: Alice
Se rvi ce
Buy Gen eric
Mone ym aki ng, Inc.
gu ard
Al ice ’s
tra ding
acco unt
Al ice
Principles of Computer System Design Saltzer & Kaashoek
2009
M
M
M
ACC EPT
Tag
S IGN
Ali ce
secure area
or
REJEC T
VE RIFY
Bob
secure area
Principles of Computer System Design Saltzer & Kaashoek
2009
M
M
M
ACC EPT
Tag
S IGN
REJEC T
VE RIFY
Ali ce
secure area
or
Bob
K1
K2
secure area
Principles of Computer System Design Saltzer & Kaashoek
2009
M
ENC RYPT
K1
secure area
ENCR YPT
( M, K1)
DECR YPT
DEC RYPT (ENCR YPT
(M, K1), K2)
K2
ins ecu re are a
secure area
Principles of Computer System Design Saltzer & Kaashoek
2009
Principles of Computer System Design Saltzer & Kaashoek
2009
Comp artme nt
Guard
Untru sted
pro gram
Obje ct
Prin cip al
Principles of Computer System Design Saltzer & Kaashoek
2009
Fi le s ervice
In terfa ce 14
In terfa ce 5
Quiz
Al ice
Wo rkstatio n
To : se rvi ce
Fro m: Alice
Sen d me the qui z
Principles of Computer System Design Saltzer & Kaashoek
2009
Rule 1: Delegating authority:
If
the n
A)
A says(B spe aks for
A
B spe aks for
.
Rule 2: Use of delegate d authority
If
and
the n
B
A spe aks for
A says(B saysX)
B saysX
Rule 3: Chaining of dele gation.
If
and
the n
rB
A spe aks fo
C
B spe aks for
C
A spe aks for
Principles of Computer System Design Saltzer & Kaashoek
2009
pr ocedureR C4_GENERATE ()
i (i + 1) modulo 25 6
j (j + S[i]) modulo 25 6
SWAP (S[i], S[j])
t (S[i] + S[j]) modulo 25 6
k S[t ]
r etur n k
proc edureRC 4_ INIT (se ed)
for i from 0 to 255 do
S[i] i
K[i] se ed[i]
j 0
for i from 0 to 255 do
j (j + S[i] + K[i]) modulo 256
SWAP (S[i], S[j])
ij 0
Principles of Computer System Design Saltzer & Kaashoek
2009
in put
ou tput
state
i0
i4
i8
i12
s 0,0 s0,1 s0,2 s 0,3
o0
o4
o8 o12
i1
i5
i9
i13
s1,0 s 1,1 s1.2 s1,3
o1
o5
o9 o13
i2
i6
i10 i14
s 2,0 s 2,1 s2,2 s 2.3
o2
o6 o10 o14
i3
i7
i11 i15
s 3,0 s3,1 s3,2 s3,3
o3
o7
o11 o15
Principles of Computer System Design Saltzer & Kaashoek
2009
proc edureAES (in , out, key)
sta te in
// c opy in into sta te
A DD R OUND K EY (sta te, key)
// m ix key into sta te
for r from 1 to 9 do
SUB B YTES (sta te)
// s ubstitute som e byte s insta te
SHIFT R OWS (sta te)
// s hift rows ofsta te cy clically
MIX C OLUMNS (sta te)
// m ix the columns up
ADD ROUND KEY (sta te, key[r4, (r+1)4 – 1 ]) // e xpan d key , mix in
S UB BYTES (sta te)
S HIFT ROWS (sta te)
A DD R OUND K EY (sta te, key[104, 114 – 1 ])
out sta te
// c opy sta te into out
Principles of Computer System Design Saltzer & Kaashoek
2009
IV
M1
M2
M3
E
E
E
IV
C1
C2
(a) Enci pher
C3
C1
C2
C3
D
D
D
M1
M2
M3
(b) De cip her
Principles of Computer System Design Saltzer & Kaashoek
2009
Service
Clie nt
1. {Clien tHello , clien t_versi on, rando mcl ient, se ssio n_id , ciphe r_sui tes, co mpres sion _f}
2. {ServerHell o, s erver_versi on, rando mserver, ses sion _id, ci pher_ suite, comp ressi on_f}
3. {ServerCerti ficate, c ertific ate_list}
4. {ServerHell oDone}
5. {Clien tKeyExcha nge, ENCR YPT (pre_ mas ter_se cret
, Se rv erPubKe y
)}
6. {Chang eCiphe rSpec, ciphe r_sui te}
client _write_key
7. {Finis hed, MA C (ma ster_s ec re ,t mess ages 1, 2, 3 , 4, 5)}client _write_MAC_secret
8. {Chang eCiphe rSpec, ciphe r_sui te}
server_writ e_key
9. {Fin ishe d, m ac (master_se cret, me ssag es 1 , 2, 3, 4, 5 , 7)}
server_writ e_MAC_secret
client _write_key
10 . {Data , pl aintext}
client _write_MAC_secret
Principles of Computer System Design Saltzer & Kaashoek
2009
struc tur eX_50 9_v3 _ce rtifica te
version
se rial_n umbe r
signatu re _cipher_identifier
issue r_ sig nature
issue r_ name
su bject_nam e
su bject_pub lic_key _cipher_identifier
su bject_pub lic_key
validity _perio d
Principles of Computer System Design Saltzer & Kaashoek
2009
pr ocedureDELETE _FILE (file_na me)
au th C HECK _DELETE _PERMISSION (file_na me, this_u ser_id
)
if au th = PERMITTED
then DESTROY (file_na me)
else s ignal(“You d o not h ave p ermissio n to de lete
file_na me”)
Principles of Computer System Design Saltzer & Kaashoek
2009
Enig ma Rotor with eig ht contacts
.
Side view, s howing co ntacts.
Edge view, s howing som e conne cti ons.
Principles of Computer System Design Saltzer & Kaashoek
2009
In
Out
Principles of Computer System Design Saltzer & Kaashoek
2009