Lecture Roadmap
advertisement
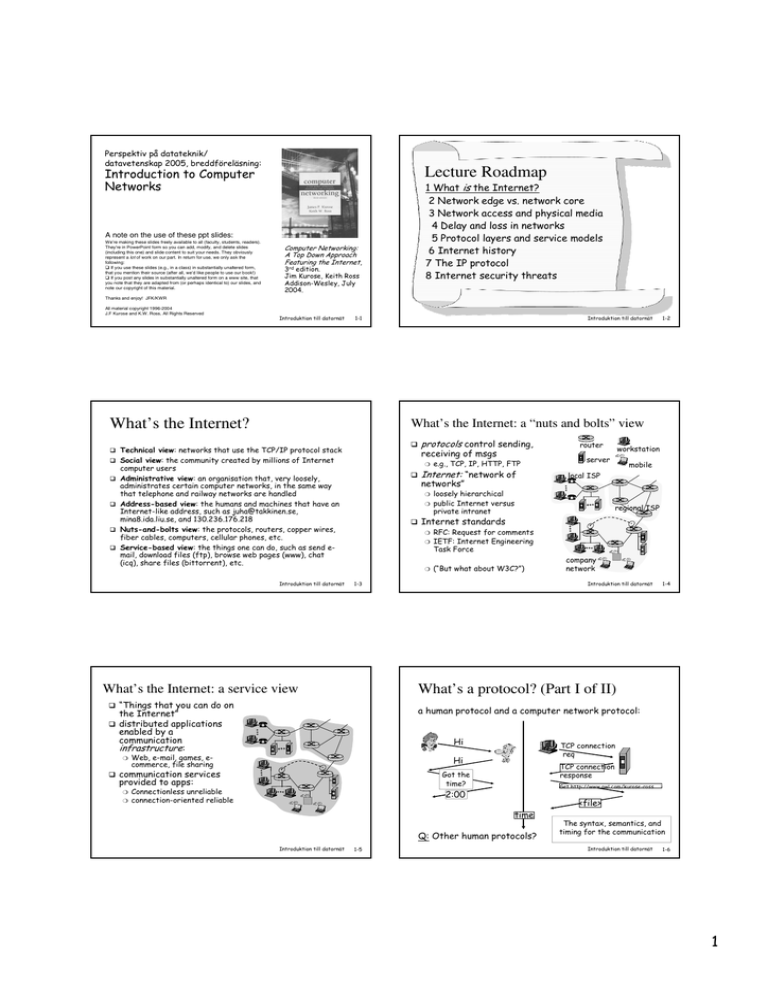
Perspektiv på datateknik/ datavetenskap 2005, breddföreläsning: Introduction to Computer Networks Lecture Roadmap 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Computer Networking: A Top Down Approach Featuring the Internet, 3rd edition. Jim Kurose, Keith Ross Addison-Wesley, July 2004. Thanks and enjoy! JFK/KWR All material copyright 1996-2004 J.F Kurose and K.W. Ross, All Rights Reserved Introduktion till datornät Introduktion till datornät 1-1 What’s the Internet? What’s the Internet: a “nuts and bolts” view Technical view: networks that use the TCP/IP protocol stack Social view: the community created by millions of Internet computer users administrates certain computer networks, in the same way that telephone and railway networks are handled Address-based view: the humans and machines that have an Internet-like address, such as juha@takkinen.se, mina8.ida.liu.se, and 130.236.176.218 Nuts-and-bolts view: the protocols, routers, copper wires, fiber cables, computers, cellular phones, etc. Service-based view: the things one can do, such as send email, download files (ftp), browse web pages (www), chat (icq), share files (bittorrent), etc. Introduktion till datornät ❍ networks” router workstation server mobile local ISP loosely hierarchical public Internet versus private intranet regional ISP Internet standards ❍ RFC: Request for comments IETF: Internet Engineering Task Force ❍ (“But what about W3C?”) ❍ company network Introduktion till datornät 1-3 1-4 What’s a protocol? (Part I of II) a human protocol and a computer network protocol: Hi Web, e-mail, games, ecommerce, file sharing TCP connection req Hi communication services provided to apps: ❍ e.g., TCP, IP, HTTP, FTP Internet: “network of ❍ “Things that you can do on the Internet” distributed applications enabled by a communication infrastructure: ❍ receiving of msgs ❍ What’s the Internet: a service view protocols control sending, ❍ Administrative view: an organisation that, very loosely, 1-2 TCP connection response Got the time? Connectionless unreliable connection-oriented reliable Get http://www.awl.com/kurose-ross 2:00 <file> time Q: Other human protocols? Introduktion till datornät 1-5 The syntax, semantics, and timing for the communication Introduktion till datornät 1-6 1 The network edge Lecture Roadmap end systems (hosts): 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats ❍ ❍ ❍ client/server model: ❍ ❍ ❍ Introduktion till datornät ❍ ❍ Hello, hello back human protocol set up “state” in two communicating hosts TCP - Transmission Control Protocol ❍ Internet’s connectionoriented service between end systems stream data transfer ❍ loss: acknowledgements and retransmissions flow control: ❍ Introduktion till datornät Goal: data transfer reliable, in-order byte❍ sender won’t overwhelm receiver congestion control: ❍ senders “slow down sending rate” when network congested Introduktion till datornät Next: services same as before! UDP - User Datagram Protocol [RFC 768]: ❍ connectionless ❍ unreliable data transfer ❍ no flow control ❍ no congestion control Apps using TCP: HTTP (Web), FTP (file transfer), Telnet (remote login), SMTP (e-mail) Apps using UDP: streaming media, teleconferencing, DNS, Internet telephony Introduktion till datornät 1-9 The network core Network core: Circuit switching mesh of interconnected routers the fundamental question: how is data transferred through net? ❍ circuit switching: dedicated circuit per call: telephone net ❍ packet-switching: data sent thru net in discrete “chunks” End-to-end resources reserved for “call” Introduktion till datornät 1-8 Network edge: Connectionless service TCP service [RFC 793] minimal (or no) use of dedicated servers e.g. Gnutella, KaZaA 1-7 Network edge: Connection-oriented service between end systems handshaking: setup (prepare for) data transfer ahead of time client host requests, receives service from always-on server e.g. Web browser/server; e-mail client/server peer-peer model: ❍ Goal: data transfer run application programs e.g. Web, e-mail at “edge of network” 1-11 1-10 link bandwidth, switch capacity dedicated resources: no sharing circuit-like (guaranteed) performance call setup required FDM or TDM Introduktion till datornät 1-12 2 Statistical multiplexing, example 1 Network core: Packet switching each end-to-end data stream divided into packets user A, B packets share network resources each packet uses full link bandwidth resources used as • • • 10-Mbps Ethernet A C statistical multiplexing 1.5 Mbps B queue of packets waiting for output link D E needed Sequence of A & B packets does not have fixed pattern -> statistical multiplexing. (In TDM each host gets same slot in revolving TDM frame.) Introduktion till datornät Introduktion till datornät 1-13 Statistical multiplexing, example 2 Packet switching vs. circuit switching Packet switching vs circuit switching: Is packet switching a “slam dunk winner?” assume 1-Mbps link each user: ❍ ❍ ❍ N users 1-Mbps link 10 users packet switching: ❍ with 35 users, probability > 10 active less than .0004 Conclusion: Packet switching allows more users to use network! Introduktion till datornät Takes L/R seconds to transmit (push out) packet of L bits on to link or R bps Entire packet must arrive at router before it can be transmitted on next link: store-and R Example: L = 7.5 Mbits R = 1.5 Mbps delay = 3L/R = 15 sec Goal: move packets through routers from source to destination datagram network: ❍ we’ll study several path selection (i.e. routing) algorithms ❍ destination address in packet determines next hop ❍ ❍ ❍ forward ❍ 1-17 routes may change during session analogy: driving, asking directions virtual circuit network: ❍ Introduktion till datornät 1-16 Packet-switched networks: Forwarding L R Introduktion till datornät 1-15 Packet-switching: Store-and-forward R Great for bursty data ❍ resource sharing ❍ simpler, no call setup Excessive congestion: packet delay and loss (more later) ❍ protocols needed for reliable data transfer, congestion control Q: How to provide circuit-like behavior? ❍ bandwidth guarantees needed for audio/video apps ❍ still an unsolved problem 100 kbps when “active” active 10 % of time circuit-switching: 1-14 each packet carries tag (virtual circuit ID), tag determines next hop fixed path determined at call setup time, remains fixed through call routers maintain per-call state Introduktion till datornät 1-18 3 Network Taxonomy Lecture Roadmap Telecommunication networks Circuit-switched networks FDM TDM 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats Packet-switched networks Networks with VCs Datagram networks • Datagram network is not either connection-oriented or connectionless. • Internet provides both connection-oriented (TCP) and connectionless services (UDP) to apps. Introduktion till datornät Network access and physical media ❍ ❍ company/univ local area network (LAN) connects end system to edge router Ethernet: ❍ shared (multiple access) or dedicated (switched) link connects endsystem and router ❍ 10 Mbps, 100 Mbps, and Gigabit Ethernet residential access nets: often point-to-point (telephone network) institutional access networks (school, company) wireless access networks Keep in mind: ❍ ❍ bandwidth (bits per second) of access network? shared or dedicated? Introduktion till datornät Wireless access networks shared wireless access network connects end system to router ❍ via base station aka “access point” wireless LANs: wide-area wireless access ❍ ❍ ❍ ❍ 1-20 Institutional access: Local area networks Q: How to connect end systems to edge router? ❍ Introduktion till datornät 1-19 802.11b (WiFi): 11 Mbps mobile phone network access provided by telecommunication operator 3G ~ 384 kbps, and up to a couple Mbps Introduktion till datornät 1-21 Physical media to wired network Ethernet) bit: propagates between transmitter/rcvr pairs physical link: what lies between transmitter & receiver guided media: router base station ❍ mobile hosts Introduktion till datornät 1-22 ❍ ❍ Category 3: traditional phone wires, 10-Mbps Ethernet Category 5: 100-Mbps Ethernet unguided media: ❍ 1-23 signals propagate in solid media: copper, fiber, coax Twisted Pair (TP): two insulated copper wires signals propagate freely, e.g., radio Introduktion till datornät 1-24 4 Physical media: Coaxial, fiber optic Coaxial cable: two concentric copper conductors bidirectional baseband: ❍ ❍ single channel on cable legacy Ethernet glass fiber carrying light pulses, each pulse a bit high-speed operation: ❍ broadband: ❍ ❍ Physical media: Radio Fiber optic cable: multiple channel on cable HFC high-speed point-to-point transmission (e.g., 5 Gbps) low error rate: repeaters spaced far apart; immune to electromagnetic noise Radio link types: signal carried in electromagnetic spectrum no physical “wire” bidirectional propagation environment effects: ❍ ❍ ❍ ❍ terrestrial microwave WLAN (e.g., Wifi) wide-area (e.g., cellular) satellite ❍ ❍ ❍ reflection obstruction by objects interference high error rate! ❍ ❍ ❍ Introduktion till datornät 2 Mbps, 11 Mbps, 54 Mbps e.g. 3G: hundreds of kbps up to 50 Mbps channel (or multiple smaller channels) 270 msec end-to-end delay geosynchronous versus low altitude Introduktion till datornät 1-25 1-26 Four sources of packet delay Lecture Roadmap 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats Introduktion till datornät 1. nodal processing: ❍ ❍ check bit errors determine output link 2. queueing ❍ ❍ depends on congestion level of router 4. B 1. nodal processing 2. queueing Introduktion till datornät 1-27 4. Propagation delay: d = length of physical link s = propagation speed in medium (~2x108 m/sec) propagation delay = d/s time waiting at output link for transmission 3. A Four sources of packet delay, cont'd 3. Transmission delay: R = link bandwidth (bps) L = packet length (bits) time to send bits into link = L/R e.g. up to 45 Mbps channels 1-28 Transmission delay vs. Propagation delay: ”TCP over snails” Note: s and R are very different quantities! 3. transmission A 4. propagation B 1. nodal processing 2. queueing Introduktion till datornät 1-29 http://www.notes.co.il/benbassat/10991.asp Ami Ben-Bassat, Israel Introduktion till datornät 1-30 5 Summary: Nodal delay Packet loss: And then what? d nodal = d proc + d queue + d trans + d prop Typical scenario: queue (aka buffer) for outgoing link has finite capacity ❍ when packet arrives to full queue, packet is dropped (aka lost) ❍ dproc = processing delay dqueue = queuing delay dtrans = transmission delay dprop = propagation delay ❍ ❍ ❍ ❍ typically a few microsecs or less Then what? ❍ lost packet may be retransmitted by previous node, by source end-system, or not retransmitted at all depends on congestion = L/R, significant for low-speed links a few microsecs to hundreds of msecs Introduktion till datornät Introduktion till datornät 1-31 1-32 Example: Organisation of air travel Lecture Roadmap 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats ticket (purchase) ticket (complain) baggage (check) baggage (claim) gates (load) gates (unload) runway takeoff runway landing airplane routing airplane routing airplane routing a series of steps Introduktion till datornät Introduktion till datornät 1-33 Example: Layering of airline functionality A textbook's Internet network architecture: Five layers application: supporting network applications ❍ ticket (purchase) ticket (complain) ticket baggage (check) baggage (claim baggage gates (load) gates (unload) gate runway (takeoff) runway (land) takeoff/landing airplane routing airplane routing airplane routing departure airport airplane routing airplane routing intermediate air-traffic control centers FTP, SMTP, HTTP transport: host-to-host data transfer ❍ TCP, UDP network: routing of datagrams from source to destination ❍ arrival airport IP, routing protocols link: data transfer between neighbouring network elements Layering hides complexity! Each layer implements a service ❍ via its own internal-layer actions ❍ relying on services provided by layer below Introduktion till datornät 1-34 ❍ PPP, Ethernet, WLAN physical: bits “on the wire” application transport network link physical Network architecture = giving structure by creating layers Reference model = certain de facto/de jure network architectures Protocol stack = a network architecture with explicit protocols listed 1-35 Introduktion till datornät 1-36 6 source What’s a protocol? (Part II of II) Protocols and services message H segment datagram H protocols the building blocks of network frame architecture each protocol object has two different interfaces ❍ ❍ t H n H t H H l n t M M M M Encapsulation application transport network link physical H H H l n M t link physical H H H l n M t switch service interface defines operations on this protocol peer-to-peer interface defines messages destination exchanged with peer M term ”protocol” overloaded ❍ specification of peer-to-peer interface (see Part I earlier) ❍ module that implements this interface Introduktion till datornät H M t H M H n H t H H l n t M application transport network link physical H H n H t H H l n t M M network link physical H H n H t H H l n t M M router Introduktion till datornät 1-37 1-38 Internet History 1961-1972: Early packet-switching principles Lecture Roadmap 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats Introduktion till datornät 1945: principle for 1967: ARPAnet conceived by 1960: name ”hypertext” 1969, Sep. 1: 1st ARPAnet node hypertext [Bush 1945] coined [Nelson 1960] Advanced Research Projects Agency operational at UCLA Network Measurement Center theory & packet-switching 1970: ALOHAnet satellite network in Hawaii (Norm Abramson) 1962: Baran - packetswitching in military nets; 1972: Licklider – first paper on ❍ ARPAnet demonstration Internet concept ❍ NCP (Network Control Protocol) 1965: Moore's law first host-to-host protocol postulated by Gordon Moore; (“TCP/IP”) Davies describes UK ❍ first e-mail program packetizing data for store❍ ARPAnet has 15 nodes and-forward communications 1961: Kleinrock: queueing 1-39 Source: Segaller, Nerds 2.0.1 – A brief history of the Internet Introduktion till datornät 1-40 1-41 Source: Tanenbaum, Computer networks Introduktion till datornät 1-42 Internet History 1973-1979: Internetworking, new and proprietary nets 1973: Metcalfe’s PhD thesis proposes Ethernet 1974: Cerf and Kahn architecture for interconnecting networks (NCP redefined as ”TCP”) Late 1970s: proprietary architectures: DECnet, SNA, XNA late 1970s: switching fixed length packets (ATM precursor) 1978: ”TCP” split into today's TCP and IP; Cerf & Kahn demonstrate internetworking ❍ 1979: Steve Jobs visits Xerox Palo Alto for demonstration of Alto workstation; ARPAnet has 200 nodes Cerf and Kahn’s internetworking principles: ❍ minimalism, autonomy - no internal changes required to interconnect networks ❍ best-effort service model ❍ stateless routers ❍ decentralized control define today’s Internet architecture Introduktion till datornät 7 Internet History Internet history 1990, 2000s: Commercialization, the Web, new apps 1980-1990: Important technologies invented 1981: IBM announces the IBM Personal Computer; Microsoft creates the DOS operating system (40 employees); Unix BSD4.1 with sockets 1982: Sun Microsystems founded 1983: ❍ Unix BSD4.2 with TCP/IP preinstalled (free) ❍ Sockets ❍ Object-oriented language (Smalltalk) ❍ DNS ❍ ❍ 1991: NSF lifts restrictions on Internet is born: ARPAnet and Defense Data Networks start using TCP/IP Cisco Systems founded 1984: Apple Macintosh launched; 1,024 hosts on the ARPAnet/Internet 1988: Sunet (Sweden) joins more killer apps: instant messaging, P2P file sharing network security to forefront est. 50 million hosts, 100 late 1990s: commercialization of the Web the Internet 1989: Internet has 100,000 million+ users backbone links running at Gbps nodes 1990: Arpanet ”deinstalled”; Berners-Lee creates WWW at CERN Introduktion till datornät Introduktion till datornät 1-43 1-44 Key Network-Layer Functions Lecture Roadmap • The IP layer • forwarding: move packets from router’s input to appropriate router output 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats • routing: determine route taken by packets from source to dest. – Routing algorithms Introduktion till datornät application transport network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical application transport network data link physical IP ”best effort” Introduktion till datornät 1-45 IP Fragmentation & Reassembly 1-46 IP Fragmentation and Reassembly network links have MTU (max.transfer size) - largest possible link-level frame. ❍ different link types, different MTUs large IP datagram divided (“fragmented”) within net ❍ one datagram becomes several datagrams ❍ “reassembled” only at final destination ❍ IP header bits used to identify, order related fragments Late 1990s–2000s: commercial use of NSFnet (decommissioned, 1995) early 1990s: Web ❍ HTML, HTTP: Berners-Lee ❍ 1993: Mosaic by Andreessen and Bina, 1994 Netscape fragmentation: in: one large datagram out: 3 smaller datagrams reassembly Example 4000 byte datagram MTU = 1500 bytes (Ethernet or WLAN) 1480 bytes in data field offset = 1480/8 length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =185 length ID fragflag offset =1040 =x =0 =370 Three new IP packets Introduktion till datornät 1-47 Introduktion till datornät 1-48 8 Subnets IP Addressing: introduction IP address: 32-bit identifier for host, router interface interface: connection between host/router and physical link ❍ ❍ ❍ routers typically have multiple interfaces host may have multiple interfaces IP addresses associated with each interface 223.1.1.1 223.1.1.2 223.1.1.4 223.1.2.9 ❍ 223.1.1.3 223.1.3.27 223.1.2.2 ❍ ❍ 223.1.1.1 = 11011111 00000001 00000001 00000001 1 1 Recipe To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. 223.1.2.1 223.1.1.2 223.1.1.4 223.1.1.3 223.1.2.9 223.1.3.27 223.1.2.2 LAN device interfaces with same subnet part of IP address can physically reach each other without intervening router 223.1.3.2 223.1.3.1 network consisting of 3 subnets 1 Introduktion till datornät 223.1.1.0/24 223.1.1.1 subnet part (high order bits) host part (low order bits) What’s a subnet ? 223.1.3.2 223.1.3.1 223 Subnets IP address: ❍ 223.1.2.1 Introduktion till datornät 1-49 223.1.2.0/24 Subnets 1-50 223.1.1.2 How many? 223.1.1.1 223.1.1.4 223.1.1.3 223.1.9.2 223.1.7.0 223.1.9.1 223.1.7.1 223.1.8.1 223.1.3.0/24 223.1.2.6 Subnet mask: /24 or 255.255.255.0 Introduktion till datornät 223.1.8.0 223.1.2.1 223.1.3.1 223.1.3.2 Introduktion till datornät 1-51 IP addresses: how to get one? 223.1.3.27 223.1.2.2 1-52 IP addresses: how to get one? Q: How does network get subnet part of IP addr? A: gets allocated portion of its provider ISP’s address space Q: How does host get IP address? hard-coded by system admin in a file ❍ Wintel: control-panel->network>configuration->tcp/ip->properties ❍ UNIX: /etc/rc.config DHCP: Dynamic Host Configuration Protocol: dynamically get address from as server ❍ “plug-and-play” ISP's block 11001000 00010111 00010000 00000000 200.23.16.0/20 Organisation 0 Organisation 1 Organisation 2 ... 11001000 00010111 00010000 00000000 11001000 00010111 00010010 00000000 11001000 00010111 00010100 00000000 ….. …. 200.23.16.0/23 200.23.18.0/23 200.23.20.0/23 …. Organisation 7 11001000 00010111 00011110 00000000 200.23.30.0/23 3 bits, 8 organisations Introduktion till datornät 1-53 Introduktion till datornät 1-54 9 Hierarchical addressing: route aggregation Hierarchical addressing: more specific routes assume FbN-ISP acquires ISPs-R-Us and then organisation 1 moves to the other ISP … Hierarchical addressing allows efficient advertisement of routing information: ISPs-R-Us has a more specific route to Organisation 1 smaller forwarding tables Organisation 0 Organisation 0 200.23.16.0/23 200.23.16.0/23 Organisation 1 200.23.18.0/23 Organisation 2 200.23.20.0/23 Organisation 7 . . . . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200.23.16.0/20” Organisation 2 200.23.20.0/23 Organisation 7 Internet ... ... Fly-By-Night-ISP Internet 200.23.30.0/23 200.23.30.0/23 ISPs-R-Us ISPs-R-Us “Send me anything with addresses beginning 199.31.0.0/16” Introduktion till datornät “Send me anything with addresses beginning 200.23.16.0/20” Organisation 1 200.23.18.0/23 “Send me anything with addresses beginning 199.31.0.0/16 or 200.23.18.0/23” ”longest-prefix matching” Introduktion till datornät 1-55 1-56 IP addressing: the last word ... Lecture Roadmap Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned 1 What is the Internet? 2 Network edge vs. network core 3 Network access and physical media 4 Delay and loss in networks 5 Protocol layers and service models 6 Internet history 7 The IP protocol 8 Internet security threats Names and Numbers ❍ allocates addresses ❍ manages DNS ❍ assigns domain names, resolves disputes Introduktion till datornät Introduktion till datornät 1-57 Firewalls 1-58 Firewalls: Why? firewall isolates organisation’s internal net from larger Internet, allowing some packets to pass, blocking others. administered network prevent denial of service attacks: ❍ SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections. prevent illegal modification/access of internal data. ❍ e.g., attacker replaces CIA’s homepage with something else allow only authorized access to inside network (set of authenticated users/hosts) two types of firewalls: ❍ application-level ❍ packet-filtering public Internet firewall Introduktion till datornät 1-59 Introduktion till datornät 1-60 10 Packet Filtering Should arriving packet be allowed in? Departing packet let out? Packet Filtering: Examples Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. ❍ All incoming and outgoing UDP flows and telnet connections are blocked. Example 2: Block inbound TCP segments with ACK=0. ❍ Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. Internet internal network connected to Internet via router firewall router filters packet-by-packet, decision to forward/drop packet based on: ❍ ❍ ❍ ❍ source IP address, destination IP address TCP/UDP source and destination port numbers ICMP message type TCP SYN and ACK bits Introduktion till datornät Application gateways Filters packets on application data as well as on IP/TCP/UDP fields. Example: allow select internal users to telnet outside. host-to-gateway telnet session gateway-to-remote host telnet session router and filter 1. Require all telnet users to telnet through gateway. 2. For authorized users, gateway sets up telnet connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all telnet connections not originating from gateway. Introduktion till datornät IP spoofing: router can’t know if data “really” comes from claimed source if multiple apps. need special treatment, each has own app. gateway. client software must know how to contact gateway. ❍ filters often use all or nothing policy for UDP. tradeoff: degree of communication with outside world, level of security many highly protected sites still suffer from attacks. e.g., must set IP address of proxy in Web browser Introduktion till datornät 1-63 Internet security threats Internet security threats Mapping: Mapping: countermeasures before attacking: “case the joint” – find out what services are implemented on network ❍ Use ping to determine what hosts have addresses on network ❍ Port-scanning: try to establish TCP connection to each port in sequence (see what happens) ❍ nmap (http://www.insecure.org/nmap/) mapper: “network exploration and security auditing” ❍ 1-62 Limitations of firewalls and gateways application gateway Introduktion till datornät 1-61 ❍ ❍ 1-64 record traffic entering network look for suspicious activity (IP addresses, ports being scanned sequentially) Countermeasures? Introduktion till datornät 1-65 Introduktion till datornät 1-66 11 Internet security threats Internet security threats Packet sniffing: Packet sniffing: countermeasures all hosts in organisation run software that checks periodically if host interface in promiscuous mode. ❍ one host per segment of broadcast media (switched Ethernet at hub) broadcast media ❍ promiscuous NIC reads all packets passing by ❍ can read all unencrypted data (e.g. passwords) ❍ e.g.: C sniffs B’s packets ❍ ❍ C A src:B dest:A Countermeasures? C A payload src:B dest:A B Internet payload Introduktion till datornät Introduktion till datornät 1-67 Internet security threats Internet security threats IP Spoofing: IP Spoofing: countermeasures can generate “raw” IP packets directly from application, putting any value into IP source address field ❍ receiver can’t tell if source is spoofed ❍ e.g.: C pretends to be B ❍ ❍ Countermeasures? ingress filtering C A payload src:B dest:A payload B Internet Introduktion till datornät B Internet 1-69 Introduktion till datornät Internet security threats Internet security threats Denial of service (DOS): Denial of service (DOS): countermeasures ❍ C SYN SYN C A SYN SYN SYN SYN SYN SYN SYN SYN B Countermeasures? B SYN SYN 1-70 filter out flooded packets (e.g., SYN) before reaching host: throw out good with bad ❍ traceback to source of floods (most likely an innocent, compromised machine) flood of maliciously generated packets “swamp” receiver ❍ Distributed DOS (DDOS): multiple coordinated sources swamp receiver ❍ e.g., C and remote host SYN-attack A ❍ A 1-68 • routers should not forward outgoing packets with invalid source addresses (e.g., datagram source address not in router’s network) • great, but ingress filtering can not be mandated for all networks C A src:B dest:A B Internet SYN Internet Introduktion till datornät 1-71 SYN Internet Introduktion till datornät 1-72 12 Summary Covered a “ton” of material! Internet overview What’s a protocol? network edge, core, access ❍ packet-switching versus circuit-switching performance: loss, delay layering and service models Internet history the IP protocol Internet security threats You now have: context, overview, “feel” of networking Introduktion till datornät 1-73 13