Computer-System Structures Operating System Concepts Computer System Operation I/O Structure
advertisement
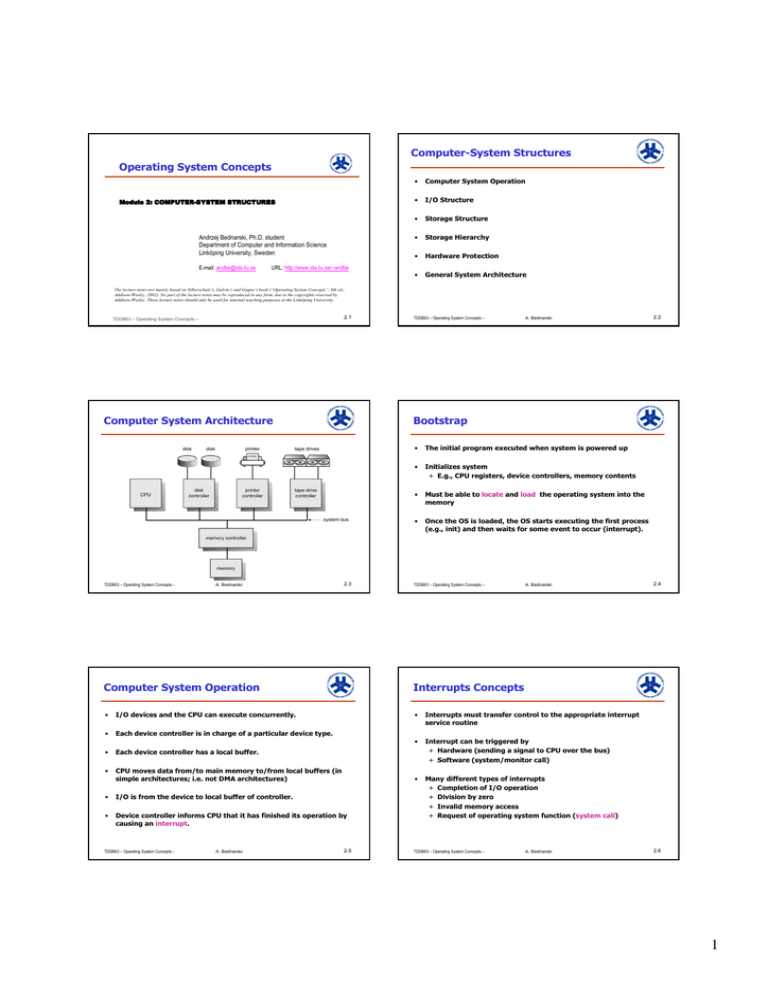
Computer-System Structures Operating System Concepts Module 2: COMPUTERCOMPUTER-SYSTEM STRUCTURES Andrzej Bednarski, Ph.D. student Department of Computer and Information Science Linköping University, Sweden E-mail: andbe@ida.liu.se URL: http://www.ida.liu.se/~andbe • Computer System Operation • I/O Structure • Storage Structure • Storage Hierarchy • Hardware Protection • General System Architecture The lecture notes are mainly based on Silberschatz’s, Galvin’s and Gagne’s book (“Operating System Concepts”, 6th ed., Addison-Wesley, 2002). No part of the lecture notes may be reproduced in any form, due to the copyrights reserved by Addison-Wesley. These lecture notes should only be used for internal teaching purposes at the Linköping University. 2.1 TDDB63 – Operating System Concepts – Computer System Architecture TDDB63 – Operating System Concepts – A. Bednarski TDDB63 – Operating System Concepts – A. Bednarski Bootstrap 2.3 • The initial program executed when system is powered up • Initializes system + E.g., CPU registers, device controllers, memory contents • Must be able to locate and load the operating system into the memory • Once the OS is loaded, the OS starts executing the first process (e.g., init) and then waits for some event to occur (interrupt). TDDB63 – Operating System Concepts – A. Bednarski Computer System Operation Interrupts Concepts • I/O devices and the CPU can execute concurrently. • Interrupts must transfer control to the appropriate interrupt service routine • Each device controller is in charge of a particular device type. • • Each device controller has a local buffer. Interrupt can be triggered by + Hardware (sending a signal to CPU over the bus) + Software (system/monitor call) • CPU moves data from/to main memory to/from local buffers (in simple architectures; i.e. not DMA architectures) • • I/O is from the device to local buffer of controller. • Device controller informs CPU that it has finished its operation by causing an interrupt. Many different types of interrupts + Completion of I/O operation + Division by zero + Invalid memory access + Request of operating system function (system call) TDDB63 – Operating System Concepts – A. Bednarski 2.2 2.5 TDDB63 – Operating System Concepts – A. Bednarski 2.4 2.6 1 Common Functions of Interrupts Interrupt Handling • Interrupt transfers control to the interrupt service routine generally, through the interrupt vector, which contains the addresses of all the service routines. • The operating system preserves the state of the CPU by storing registers and the program counter. • Interrupt architecture must save the address of the interrupted instruction. + E.g., interrupt address in a fixed location; location indexed by the device number; or return address stored on a stack • Determines which type of interrupt has occurred: + polling - querying all I/O devices to detect the one requesting service + vectored interrupt system • Incoming interrupts are disabled while another interrupt is being processed to prevent a lost interrupt. • Separate segments of code determine what action should be taken for each type of interrupt • A trap is a software-generated interrupt caused either by an error or a user request. (traps are also called exceptions) • An operating system is interrupt driven. TDDB63 – Operating System Concepts – A. Bednarski 2.7 Interrupt Time Line For a Single Process Doing Output TDDB63 – Operating System Concepts – 2.8 A. Bednarski I/O Structure: Synchronous • After I/O starts, control returns to user program only upon I/O completion. + wait instruction idles the CPU until the next interrupt + wait loop (tight loop: Loop: jmp Loop) continues until the interrupt + At most one I/O request is outstanding at a time, no simultaneous I/O processing, that is, you know the device. Disadvantages: • Burns CPU cycles • Excludes concurrent I/O operations to multiple devices • Excludes overlapping useful computation with I/O TDDB63 – Operating System Concepts – A. Bednarski 2.9 I/O Structure: Asynchronous • TDDB63 – Operating System Concepts – 2.10 A. Bednarski Two I/O methods After I/O starts, the CPU does not wait for I/O completion, instead other OS and user programs are executed + control is returned to the user program before I/O completion + System call – request to the operating system to allow user to wait for I/O completion. + Device-status table contains entry for each I/O device indicating its type, address, and state. + Operating system indexes into I/O device table to determine device status and to modify table entry to include interrupt. Synchronous Asynchronous Advantage: + Efficient usage of the CPU resource TDDB63 – Operating System Concepts – A. Bednarski 2.11 TDDB63 – Operating System Concepts – A. Bednarski 2.12 2 Direct Memory Access (DMA) Structure Device-Status Table TDDB63 – Operating System Concepts – A. Bednarski 2.13 Storage Structure Used for high-speed I/O devices able to transmit information at close to memory speeds. • Device controller transfers blocks of data from buffer storage directly to main memory without CPU intervention. • Only one interrupt is generated per block, rather than the one interrupt per byte. • DMA “steals” memory cycles from the CPU, which might slow down the processor while a DMA transfer is in progress. TDDB63 – Operating System Concepts – A. Bednarski Primary storage, that is main memory – only large storage media that the CPU can access directly. • Secondary storage – extension of main memory that provides large nonvolatile storage capacity. • Magnetic disks – rigid metal or glass platters covered with magnetic recording material + Disk surface is logically divided into tracks, which are subdivided into sectors. + The disk controller determines the logical interaction between the device and the computer. A. Bednarski 2.15 TDDB63 – Operating System Concepts – A. Bednarski Main Memory Storage Hierarchy •Array of words or bytes, where each word has its own address •Used for storing data and program code •The only storage that the CPU can access directly (except for CPU registers) • Storage systems organized in hierarchy. + Speed + Cost + Volatility • Caching – copying information into faster storage system; main memory can be viewed as a last cache for secondary storage. Ideally, programs and data should be stored in main memory permanently, but + main memory is usually too small to store all needed programs and data permanently; and + main memory is volatile storage device, loosing its contents when power is turned off or otherwise lost. TDDB63 – Operating System Concepts – 2.14 Moving-Head Disk Mechanism • TDDB63 – Operating System Concepts – • A. Bednarski 2.17 TDDB63 – Operating System Concepts – A. Bednarski 2.16 2.18 3 Storage-Device Hierarchy TDDB63 – Operating System Concepts – A. Bednarski Hardware Protection 2.19 Dual-Mode Operation • Dual-Mode Operation • I/O Protection • Memory Protection • CPU Protection TDDB63 – Operating System Concepts – Dual-Mode Operation (Cont.) • Sharing system resources requires the operating system to ensure that an incorrect program cannot cause other programs to execute incorrectly. • Provide hardware support to differentiate between at least two modes of operations. 1. User mode – execution done on behalf of a user. 2. Monitor mode (also supervisor mode or system mode) – execution done on behalf of operating system. Executes only privileged instructions (instructions that may be harmful) e.g., system login, set priorities, system halt, etc. • • A. Bednarski 2.21 Mode bit added to computer hardware to indicate the current mode: monitor (0) or user (1). When an interrupt or fault occurs hardware switches to monitor mode. Interrupt/fault monitor user set user mode • TDDB63 – Operating System Concepts – Privileged instructions can be issued only in monitor mode. TDDB63 – Operating System Concepts – A. Bednarski I/O Protection Memory Protection • All I/O instructions are privileged instructions. • • Must ensure that a user program could never gain control of the computer in monitor mode (i.e., a user program that, as part of its execution, stores a new address in the interrupt vector). Must provide memory protection at least for the interrupt vector and the interrupt service routines • In order to have memory protection, add two registers that determine the range of legal addresses a program may access: + base register – holds the smallest legal physical memory address + limit register – contains the size of the range • Memory outside the defined range is protected TDDB63 – Operating System Concepts – A. Bednarski 2.20 A. Bednarski 2.23 TDDB63 – Operating System Concepts – • A. Bednarski 2.22 A base and a limit registers define a Logical Address Space 2.24 4 Protection Hardware • • CPU Protection • Timer – interrupts computer after specified period to ensure operating system maintains control. + Timer is decremented every clock tick. + When timer reaches the value 0, an interrupt occurs. • Timer commonly used to implement time sharing. • Timer also used to compute the current time. • Load-timer is a privileged instruction. When executing in monitor mode, the operating system has unrestricted access to both monitor and user’s memory. The load instructions for the base and limit registers are privileged instructions. TDDB63 – Operating System Concepts – A. Bednarski 2.25 General-System Architecture Given the I/O instructions are privileged, how does the user program perform I/O? • System call – the method used by a process to request action by the operating system. + Usually takes the form of a trap to a specific location in the interrupt vector. + Control passes through the interrupt vector to a service routine in the OS, and the mode bit is set to monitor mode. + The monitor verifies that the parameters are correct and legal, executes the request, and returns control to the instruction following the system call. A. Bednarski A. Bednarski 2.27 TDDB63 – Operating System Concepts – A. Bednarski System Calls Summary • • General computer architecture • Concept of interrupts + Hardware vs software interrupts vs traps • Storage devices • Protection • • • • UNIX: ”man -s 2 intro” + Introduction to UNIX system calls (timers, file management, …) Process Control + End, abort, load, execute, create, terminate, suspend, allocate and free memory File Manipulation + Create, delete, open, close, read, write files; attach/detach devices Information maintenance + Get/set date, time, system date, attributes (process, file, and device) Communications + Create, delete communication channels; send/receive messages etc. TDDB63 – Operating System Concepts – A. Bednarski 2.26 Use of a System Call to Perform I/O • TDDB63 – Operating System Concepts – TDDB63 – Operating System Concepts – 2.29 TDDB63 – Operating System Concepts – A. Bednarski 2.28 2.30 5 Recommended Reading and Exercises • Reading: + Chapter 2 + Section 2.6 (optional) • Exercises: + All (2.12 and 2.13 optional) TDDB63 – Operating System Concepts – A. Bednarski 2.31 6