Multiple Access Links and Protocols Two types of “links”: point-to-point
advertisement

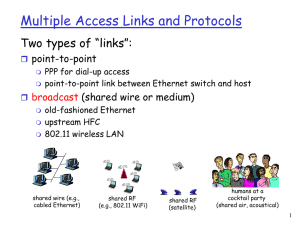
Multiple Access Links and Protocols Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) old-fashioned Ethernet upstream HFC 802.11 wireless LAN shared wire (e.g., cabled Ethernet) shared RF (e.g., 802.11 WiFi) shared RF (satellite) humans at a cocktail party (shared air, acoustical) 1 Multiple Access protocols single shared broadcast channel two or more simultaneous transmissions by nodes: interference collision if node receives two or more signals at the same time multiple access protocol distributed algorithm that determines how nodes share channel, i.e., determine when node can transmit communication about channel sharing must use channel itself! no out-of-band channel for coordination 2 Ideal Multiple Access Protocol Broadcast channel of rate R bps 1. when one node wants to transmit, it can send at rate R. 2. when M nodes want to transmit, each can send at average rate R/M 3. fully decentralized: no special node to coordinate transmissions no synchronization of clocks, slots 4. simple 3 MAC Protocols: a taxonomy Three broad classes: Channel Partitioning divide channel into smaller “pieces” (time slots, frequency, code) allocate piece to node for exclusive use Random Access channel not divided, allow collisions “recover” from collisions “Taking turns” nodes take turns, but nodes with more to send can take longer turns 4 Channel Partitioning MAC protocols: TDMA TDMA: time division multiple access access to channel in "rounds" each station gets fixed length slot (length = pkt trans time) in each round unused slots go idle Example 6-station LAN: 1,3,4 have pkt, slots 2,5,6 idle 6-slot frame 1 3 4 1 3 4 5 Channel Partitioning MAC protocols: FDMA FDMA: frequency division multiple access channel spectrum divided into frequency bands each station assigned fixed frequency band unused transmission time in frequency bands go idle Example 6-station LAN: 1,3,4 have pkt, frequency bands 2,5,6 idle frequency bands 6 Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delayed retransmissions) Examples of random access MAC protocols: slotted ALOHA ALOHA CSMA, CSMA/CD, CSMA/CA 7 Slotted ALOHA Assumptions: all frames same size time divided into equal size slots (time to transmit 1 frame) nodes start to transmit only slot beginning nodes are synchronized if 2 or more nodes transmit in slot, all nodes detect collision Operation: when node obtains fresh frame, transmits in next slot if no collision: node can send new frame in next slot if collision: node retransmits frame in each subsequent slot with prob. p until success 8 Slotted ALOHA Pros single active node can continuously transmit at full rate of channel highly decentralized: only slots in nodes need to be in sync simple Cons collisions, wasting slots idle slots nodes may be able to detect collision in less than time to transmit packet clock synchronization 9 Slotted Aloha efficiency Efficiency : long-run fraction of successful slots (many nodes, all with many frames to send) suppose: N nodes with many frames to send, each transmits in slot with probability p prob that given node has success in a slot = p(1-p)N-1 prob that any node has a success = Np(1-p)N-1 max efficiency: find p* that maximizes Np(1-p)N-1 for many nodes, take limit of Np*(1-p*)N-1 as N goes to infinity, gives: Max efficiency = 1/e = .37 At best: channel used for useful transmissions 37% of time! ! 10 Pure (unslotted) ALOHA unslotted Aloha: simpler, no synchronization when frame first arrives transmit immediately collision probability increases: frame sent at t0 collides with other frames sent in [t0-1,t0+1] 11 Pure Aloha efficiency P(success by given node) = P(node transmits) . P(no other node transmits in [t0-1,t0] . P(no other node transmits in [t0,t0+1] = p . (1-p)N-1 . (1-p)N-1 = p . (1-p)2(N-1) … choosing optimum p and then letting n -> infinity ... = 1/(2e) = .18 even worse than slotted Aloha! 12 13 Now, let’s improve things … 14 IEEE 802.11: multiple access avoid collisions: 2+ nodes transmitting at same time 802.11: CSMA - sense before transmitting don’t collide with ongoing transmission by other node 802.11: no collision detection! difficult to receive (sense collisions) when transmitting due to weak received signals (fading) can’t sense all collisions in any case: hidden terminal, fading goal: avoid collisions: CSMA/C(ollision)A(voidance) A C A B B C C’s signal strength A’s signal strength space 15 IEEE 802.11 MAC Protocol: CSMA/CA 802.11 sender 1 if sense channel idle for DIFS then transmit entire frame (no CD) 2 if sense channel busy then start random backoff time timer counts down while channel idle transmit when timer expires 3 if no ACK then increase random backoff interval, repeat step 2 802.11 receiver - if frame received OK sender receiver DIFS data SIFS ACK return ACK after SIFS (service model is connectionless, acked) 16 IEEE 802.11 MAC: Distributed Coordination Function (DCF) • Make use of CSMA (carrier sense multiple access) • Use set of delays generic called Interframe Space (IFS) Algorithm Logic: 1. Station sense the medium 2. If medium idle, wait IFS, then if still idle transmit frame 3. If medium busy or become busy, defer and monitor the medium until idle 4. Then, delay IFS and sense medium 5. If medium idle, exponential backoff and if then idle, station transmit • Binary exponential backoff -> handle heavy load 17 IEEE 802.11 MAC: Distributed Coordination Function (DCF) • Make use of CSMA (carrier sense multiple access) • Use set of delays generic called Interframe Space (IFS) Algorithm Logic: 1. Station sense the medium 2. If medium idle, wait IFS, then if still idle transmit frame 3. If medium busy or become busy, defer and monitor the medium until idle 4. Then, delay IFS and sense medium 5. If medium idle, exponential backoff and if then idle, station transmit • Binary exponential backoff -> handle heavy load 18 IEEE 802.11 MAC: DCF, cont’d Priority-based scheme - use 3 values for IFS: – SIFS (short IFS): shortest IFS used for immediate responses such as ACK, CTS, poll response – PIFS (point coordination function IFS): middle length IFS used for issuing polls by a centralized controller – DIFS (distributed coordination function IFS): longest IFS used for regular asynchronous frames 19 Hidden Terminal Problem Hidden terminal problem (ad-hoc and WLAN) B A C C’s signal strength A’s signal strength space C A B 20 Hidden Terminal Problem Hidden terminal problem (ad-hoc and WLAN) B A C C’s signal strength A’s signal strength space C A B 21 Hidden Terminal Problem Hidden terminal problem (ad-hoc and WLAN) - medium free near the transmitter - medium not free near the receiver => Packet collision B A C C’s signal strength A’s signal strength space C A B 22 Hidden Terminal Problem Hidden terminal problem (ad-hoc and WLAN) - medium free near the transmitter - medium not free near the receiver => Packet collision Possible solution: - MAC scheme using RTS-CTS scheme B A C C’s signal strength A’s signal strength space C A B 23 Avoiding collisions (more) idea: allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to base station using CSMA RTS may still collide with each other (but they’re short) BS broadcasts clear-to-send CTS to host in response to RTS RTS heard by all nodes because of broadcast property sender transmits (large) data frame other stations defer transmissions until it is done Avoid data frame collisions completely using small reservation packets! 24 Collision Avoidance: RTS-CTS exchange A AP B reservation collision DATA (A) defer time 25 Hidden Terminal Problem [2] Problems with RTS-CTS solution: - possible collisions between CTS and RTS - collisions between data packets due to multiple different CTS granted to different neighboring nodes - Also, adds delay and overhead … 26 Exposed Terminal Problems Exposed terminal problem (ad-hoc and WLAN) - medium free near the receiver - medium busy near the transmitter => Waist of bandwidth Possible solutions: - directional antennas - separate channels for control and data 27 Issues, medium access schemes Distributed operation Synchronization Hidden terminals Exposed terminals Throughput Access delay Fairness Real-time traffic support Resource reservation Ability to measure resource availability Capability for power control Adaptive rate control Use of directional antennas 28 Issues, medium access schemes Distributed operation Synchronization Hidden terminals Exposed terminals Throughput Access delay Fairness Real-time traffic support Resource reservation Ability to measure resource availability Capability for power control Adaptive rate control Use of directional antennas 29 Issues, medium access schemes Distributed operation Synchronization Hidden terminals Exposed terminals Throughput Access delay Fairness Real-time traffic support Resource reservation Ability to measure resource availability Capability for power control Adaptive rate control Use of directional antennas 30 31 802.11 frame: addressing 2 2 6 6 6 frame address address address duration control 1 2 3 Address 1: MAC address of wireless host or AP to receive this frame 2 6 seq address 4 control 0 - 2312 4 payload CRC Address 4: used only in ad hoc mode Address 3: MAC address of router interface to which AP is attached Address 2: MAC address of wireless host or AP transmitting this frame 32 802.11 frame: addressing R1 router H1 Internet AP R1 MAC addr H1 MAC addr dest. address source address 802.3 frame AP MAC addr H1 MAC addr R1 MAC addr address 1 address 2 address 3 802.11 frame 33 802.11 frame: more frame seq # (for reliable ARQ) duration of reserved transmission time (RTS/CTS) 2 2 6 6 6 frame address address address duration control 1 2 3 2 Protocol version 2 4 1 Type Subtype To AP 6 2 1 seq address 4 control 1 From More AP frag 1 Retry 1 0 - 2312 4 payload CRC 1 Power More mgt data 1 1 WEP Rsvd frame type (RTS, CTS, ACK, data) 34 35 A few more about QoS 36 IEEE 802.11 MAC: Point Coordination Function (PCF) • • • • Alternative access method on top of DCF Polling operation by a centralized master Use PIFS when issuing polls For avoiding locking out the asynchronous traffic the superframe is used 37 IEEE 802.11 MAC protocol 38 IEEE 802.11 MAC Frame Types • – – – – – – Six types of control frames Power save - poll (PS-poll) Request to send (RTS) Clear to send (CTS) Acknowledgment (ACK) Contention-free (CF)-end CF-end + CF-Ack •Management frames – – – – – – – • Eight types of data frames Carry user data – Data – Data + CF-Ack – Data + CF-poll – Data + CF-Ack + CF-poll Do not carry user data – – – – Null Function CF-Ack CF-Poll CF-Ack + CF-Poll association request and association response reassociation request and reassociation response probe request and probe response beacon announcement traffic indication message disassociation authentication and deauthentication 39 IEEE 802.11e: Enhanced Distribution Coordination Function (EDCF) 40 IEEE 802.11 MAC protocol: parameters 41 42 Two Popular 2.4 GHz Standards: IEEE 802.11 (WiFi) Fast (11 Mbps) High power Long range Single-purpose Typically channel 1, 6, or 11 Ethernet replacement Easily available Bluetooth Slow (1 Mbps) Low power Short range Flexible Frequency hopping Cable replacement (e.g., device-to-device) 43 Example What technology/device? 44 Example Figures from: A. Mahanti et al., ”Ambient Interference Effects in Wi-Fi Networks”, Proc. IFIP Networking, 2010. Many devices and technologies sharing the medium … resulting in different degrees of interference 45 Example: Channel Utilization Channel utilization: The % of time a transmission is present from a known RF source, in a given channel Channels 1 and 6, utilization peaked near 60%, while for channel 11 it was over 90%. Channel 11 spikes caused due to microwave ovens, cordless phones, and other fixed-frequency devices. Figure from: A. Mahanti et al., ”Ambient Interference Effects in Wi-Fi Networks”, Proc. IFIP Networking, 2010. 46 47 Background: Cellular network technology Overview 1G: Analog voice (no global standard …) 2G: Digital voice (again … GSM vs. CDMA) 3G: Digital voice and data • Again ... UMTS (WCDMA) vs. CDMA2000 (both CDMA-based) • and … 2.5G: EDGE (GSM-based) 4G: LTE, LTE-Advanced … • OFDM (OFDMA for downlink and SC-OFDM for uplink) Trends More data, packet-based switching, shared channel, directional (spatial reuse), multi-antenna, etc. Other goals: Seamless with other technologies, QoS for multimedia, etc. 48 Components of cellular network architecture MSC connects cells to wired tel. net. manages call setup (more later!) handles mobility (more later!) cell covers geographical region base station (BS) analogous to 802.11 AP mobile users attach to network through BS air-interface: physical and link layer protocol between mobile and BS Mobile Switching Center Public telephone network Mobile Switching Center wired network Wireless, Mobile Networks 6-49 Cellular networks: the first hop Techniques for sharing mobile-to-BS radio spectrum combined FDMA/TDMA: divide spectrum in frequency channels, divide each channel into time slots frequency bands CDMA: code division multiple access SDMA: space division multiple access time slots 50 2G (voice) network architecture Base station system (BSS) MSC BTS G BSC Public telephone network Gateway MSC Legend Base transceiver station (BTS) Base station controller (BSC) Mobile Switching Center (MSC) Mobile subscribers Wireless, Mobile Networks 6-51 3G (voice+data) network architecture MSC G radio network controller Gateway MSC G SGSN Key insight: new cellular data network operates in parallel (except at edge) with existing cellular voice network voice network unchanged in core data network operates in parallel Public telephone network Public Internet GGSN Serving GPRS Support Node (SGSN) Gateway GPRS Support Node (GGSN) Wireless, Mobile Networks 6-52 3G (voice+data) network architecture MSC G radio network controller Public telephone network Gateway MSC G SGSN Public Internet GGSN radio interface (WCDMA, HSPA) radio access network Universal Terrestrial Radio Access Network (UTRAN) core network General Packet Radio Service (GPRS) Core Network public Internet Wireless, Mobile Networks 6-53 Code Division Multiple Access (CDMA) used in several wireless broadcast channels (cellular, satellite, etc) standards unique “code” assigned to each user; i.e., code set partitioning all users share same frequency, but each user has own “chipping” sequence (i.e., code) to encode data encoded signal = (original data) X (chipping sequence) decoding: inner-product of encoded signal and chipping sequence allows multiple users to “coexist” and transmit simultaneously with minimal interference (if codes are “orthogonal”) 54 CDMA Encode/Decode sender d0 = 1 data bits code Zi,m= di.cm -1 -1 -1 1 -1 1 1 1 -1 -1 -1 slot 1 -1 slot 1 channel output 1 -1 1 1 1 1 1 1 1 d1 = -1 1 1 1 channel output Zi,m -1 -1 -1 slot 0 1 -1 -1 -1 -1 slot 0 channel output M Di = S Zi,m.cm m=1 received input code receiver 1 1 1 1 1 1 1 -1 -1 -1 -1 1 1 1 1 -1 -1 -1 -1 -1 1 1 1 -1 -1 -1 slot 1 M 1 1 -1 -1 -1 -1 slot 0 d0 = 1 d1 = -1 slot 1 channel output slot 0 channel output 55 CDMA: two-sender interference 56 Practical chipping codes … Orthogonal even under offset? No synchronization … Random sequence; high probability low cross-correlation Different chip lengths? different rates, take advantage of silence, more calls 57 LTE and LTE-Advanced ITU, IMT-advanced, 3GPP, and LTE-Advavnced ... All traffic is IP-based Base station called enhanced NodeB, eNodeB or eNB Downlink (OFDMA) vs uplink (SC-OFDM) 58 LTE downlink (OFDMA-based) Figure from: 3GPP TR 25.892; Feasibility Study for Orthogonal Frequency Division Multiplexing (OFDM) for UTRAN enhancement (Release 6) Data symbols are independently modulated and transmitted over a high number of closely spaced orthogonal subcarriers. Availible modulation schemes for E-UTRA downlink: QPSK, 16QAM, and 64QAM OFDM signal is generated using Inverse Fast Fourier Transform (IFFT) digital signal processingƒ 59 Figure from: S. Parkvall, “LTE – The Global Standard for Mobile Broadband”, presentation, Ericsson Research Time domain structure: 10 ms frame consisting of 10 subframes of length 1 ms Each subframe consists of 2 slots of length 0.5 ms Each slot consists of 7 OFDM symbols (6 symbols in case of extended CP) ƒResource element (RE) One subcarier during one OFDM symbol ƒResource block (RB) 12 subcarriers during one slot (180 kHz × 0.5 ms) 60 Scheduling decisions done in the base station Scheduling algorithm is a vendor-specific, but typically takes into account Radio link quality situation of different users Overall interference situation Quality of Service requirements Service priorities, etc. 61 Downlink vs uplink Parallel transmission on large number of narrowband subcarriers Avoids own-cell interference Robust to time dispersion ƒ Bad power-amplifier efficiency Single carrier properties Better battery lifetime at phones/sender (reduced power-amplifier power) More complexity at receiver (equalizer needed) Lower throughput 62 Current LTE status GSA Fast Facts based on their "Evolution to LTE Report" (updated September 2014): 526 operators are investing in LTE in 156 countries Over 21% of operators are deploying LTE-Advanced technologies. 16 operators have commercially launched LTE-Advanced systems. 66 operators in 35 countries are investing in VoLTE studies, trials, deployments 10 operators have commercially launched HD voice service using VoLTE GSA forecasts there will be at least 350 commercially launched LTE networks by end 2014 More material later ... (e.g., eMBMS and MIMO) 63