Cyber Security Research at AUB Imad H. Elhajj American University of Beirut
advertisement

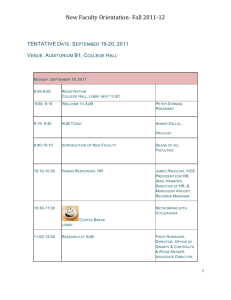
Cyber Security Research at AUB Imad H. Elhajj American University of Beirut Electrical and Computer Engineering ie05@aub.edu.lb ITU-T Study Group 17 February 2012 AUB Department of Electrical and Computer Engineering Macro AUB Department of Electrical and Computer Engineering Macro AUB Department of Electrical and Computer Engineering Micro AUB Department of Electrical and Computer Engineering Nano AUB Department of Electrical and Computer Engineering Nano AUB Department of Electrical and Computer Engineering Play Offices & Lab AUB Department of Electrical and Computer Engineering AUB (Founded in 1866) AUB Department of Electrical and Computer Engineering Electrical and Computer Engineering AUB 7,500 students 73-acre Campus ECE 620 Undergraduate students 50 Graduate students 26 Full-time faculty members Opportunities for graduate students and collaboration AUB Department of Electrical and Computer Engineering Security Group At AUB Dr. Ayman Kayssi Dr. Ali Chehab Dr. Imad Elhajj 3 PhD Students 12 MS Students 10 Undergraduate Students AUB Department of Electrical and Computer Engineering Areas of Research Wireless mobile networks Energy aware Internet Industrial Cloud Misc: VANETs, RFID, wireless sensor networks, body sensor networks AUB Department of Electrical and Computer Engineering Research Relevance to ITU-T SG17 Questions QUESTIONS TITLE Q 1/17 Telecommunications systems security project Q 4/17 Cybersecurity Q 6/17 Security aspects of ubiquitous telecommunication services Q 7/17 Secure application services Q 8/17 Service oriented architecture security Q 10/17 Identity management architecture and mechanisms Q 11/17 Directory services, Directory systems, and publickey/attribute certificates AUB Department of Electrical and Computer Engineering Wireless Mobile Network Security AUB Department of Electrical and Computer Engineering Wireless Signaling: Vulnerabilities, Detection and Mitigation TELUS corporation funded research AUB Department of Electrical and Computer Engineering Signaling AUB Department of Electrical and Computer Engineering Signaling Research 1) Developing a detection algorithm for unusual signaling activities originating from a wireless device 2) Devising granular mitigation techniques 3) Effects of signaling on the backbone AUB Department of Electrical and Computer Engineering Energy Aware AUB Department of Electrical and Computer Engineering Security Using Mobile Devices • Security functions are energy consuming • Human perception limitations reduce security requirements • “the quick brown fox jumped over the lazy dog” requires 44 bytes of storage capacity in textual format • Same sentence requires 3000 bytes of data when it is spoken and encoded by G.729 encoder AUB Department of Electrical and Computer Engineering Audio Experiment AUB Department of Electrical and Computer Engineering G.711 E3VoIP2 N=15 Average N=15 SRTP 0.3 milliseconds 0.25 0.2 0.15 0.1 0.05 0 0 10 20 30 40 Packets AUB Department of Electrical and Computer Engineering 50 60 70 Internet Security AUB Department of Electrical and Computer Engineering IP Spoofing Detection Round Trip Time to Improve Hop Count Filtering AUB Department of Electrical and Computer Engineering Thwarting Cache Poisoning Attacks in DNS Decrease the success probability of DNS spoofing and cache poisoning by preventing man-in-the-middle attacks Provide a backward compatible and simple security solution with low computation and communication overhead Target the different DNS query interaction models Employ an efficient Identity-Based Encryption key management scheme that relieves the different DNS interacting entities from the burden and complexities of traditional public-key infrastructures AUB Department of Electrical and Computer Engineering Secure Delay-Tolerant Communications in the Presence of Oppressive Governments Develop a secure delay-tolerant network system – Enable citizens to communicate freely in an environment where public communication methods, are intercepted and used by the authorities to monitor civilian activities. The proposed system is composed of several disconnected zones – Data marshals between private key generators and normal nodes in different zones – Uses mobile gateway nodes that carry messages between the different zones AUB Department of Electrical and Computer Engineering DTN Network Model CELL1 PKG1 Data Broadcast CELL2 Mobile Gateway PKG2 CELL3 PKG3 Mobile Gateway Data Broadcast AUB Department of Electrical and Computer Engineering Industrial Security AUB Department of Electrical and Computer Engineering Automation and BMS Stuxnet PLC and SCADA vulnerabilities BMS vulnerabilities Industrial IDS AUB Department of Electrical and Computer Engineering Security in Cloud Computing AUB Department of Electrical and Computer Engineering Hardware-based Security for Ensuring Data Privacy in the Cloud • A set of hardware-based security mechanisms for ensuring the privacy, integrity, and legal compliance of customer data as it is stored and processed in the cloud. • Leverage the tamper-proof capabilities of cryptographic coprocessors to establish a secure execution domain in the computing cloud that is physically and logically protected from unauthorized access. • Provide a privacy feedback protocol to inform users of the different privacy operations applied on their data and to make them aware of any data leaks or risks that may jeopardize the confidentiality of their sensitive information. AUB Department of Electrical and Computer Engineering PasS system and interaction model CSP Cloud Customer Services Layer Privacy categorized data and software Output results and privacy feedback Cu om st re so rs er TTP n Crypto Coprocessor Physical Hardware Virtual Machine Storage Facility AUB Department of Electrical and Computer Engineering Co tio pr oc ra st es gi Cloud Service Provider (CSP) Configured Crypto Trusted Third Party (TTP) Virtual Machine using a Crypto Coprocessor Reputation as a Service • RaaS is a secure and accountable reputation system for ranking service providers in cloud computing architectures. • Secure audit logging provides a reputation reporting system whose results and recommendations can be published as a service and verified by trusted third parties or by the cloud service providers themselves. • Ranking criteria: – – – – Performance Quality of service measures Security Pricing • RaaS provides verifiable and accountable compliance with service-level agreements and regulatory policies • RaaS is implemented in a real cloud computing architecture using the VMware vSphere 4 cloud operating system. – Imposes minimal overhead on the overall system performance AUB Department of Electrical and Computer Engineering The Bulk Data Fetch Protocol Cloud Provider Cloud Storage Facility Application Servers (1) (2) (11) (12) (10) (7) (3) (8) (6) (4) (5) (9) Cloud Customer (1) Resource Query + Authentication Info. (3) Resource Query (5) Requested Resource Data (7) Set t2, Verify Hash (9) Send Resource Data to Customer (11) Validate commitment hash (2) Authenticate Query and Set t1 (4) Fetch Data from Cloud Storage (6) Send Hash(Resource Data) (8) Authorization Signal (10) Send Hash(Resource Data) (12) Generate Secure Log Entry AUB Department of Electrical and Computer Engineering SNUAGE • Platform-as-a-service security framework for building secure and scalable multi-layered services based on the cloud computing model. • SNUAGE ensures the authenticity, integrity, and confidentiality of data communication over the network links by creating a set of security associations between the data-bound components on the presentation layer and their respective data sources on the data persistence layer. • Implementation using Java and deployed and tested in a real cloud computing infrastructure using the Google App Engine service platform. AUB Department of Electrical and Computer Engineering BGP-Inspired Autonomic Service Routing for the Cloud • ServBGP: a service routing protocol for managing service collaboration among cloud providers in cloud computing. • Based on the policy-driven design of the well-known BGP Internet routing • Autonomously manage the different aspects of service interaction and collaboration among service providers from service discovery and advertisement to service consumption and revocation. • ServBGP routing decision engine is planned to operate by processing cost-bidding and QoS advertisement messages from the different cloud providers. • Implemented on Google, Amazon, and Microsoft clouds AUB Department of Electrical and Computer Engineering ServBGP System Architecture Service Router Service Request In RR Service Request Out SIB CSP6 CSP2 CSP3 CSP1 CSP7 Cloud Customer CSP4 CSP5 Cloud Service Provider (CSP) ServBGP Information Base Reputation Repository (RR) Service Router ServBGP Service Advertisment Service Reputation Scores AUB Department of Electrical and Computer Engineering Mobile Cloud Computing Set of policy-driven security protocols for ensuring the confidentiality and integrity of enterprise data in mobile cloud computing environments. Offloading the intensive asymmetric key agreement mechanisms from the mobile Designing a customizable policy-based security architecture that considers the sensitivity of cloud data to provide multi-level and fine-grained data protection methodologies that suit the energy-limited mobile devices and the low-bandwidth wireless networks characterizing current mobile cloud computing models. The system is implemented in a real cloud computing environment and the savings in terms of energy consumption and execution time are analyzed. AUB Department of Electrical and Computer Engineering VANETs, RFID, wireless sensor networks, body sensor networks AUB Department of Electrical and Computer Engineering Keyless Authentication of Position and Velocity for VANETs AUB Department of Electrical and Computer Engineering A Privacy-Preserving Trust Model for VANETs A trust-based privacy-preserving model for VANETs. The model is unique in its ability to protect privacy while maintaining accurate reputation-based trust. We use the notion of groups in order to make the VANET users anonymous within their groups and yet identifiable and accountable to their group managers. The use of groups simplifies the task of building reputation and calculating trust in the received messages in order to provide better and more confident decisions. Simulations verify correctness and reliability AUB Department of Electrical and Computer Engineering A PUF-Based Ultra-Lightweight Mutual-Authentication RFID Protocol A novel approach to achieve mutual authentication for ultra-lightweight tags is proposed using Physically Unclonable Functions (PUFs). Provide robust security properties as well as good performance for limited tags AUB Department of Electrical and Computer Engineering TRACE: A Centralized Trust and Competence-Based EnergyEfficient Routing Scheme for Wireless Sensor Networks Protect wireless sensor networks from various attacks and misbehaving nodes. TRACE identifies different types of bad nodes that can affect the correct routing operation and the reliability of the message delivery to the sink base station. Sink BS processes and validates the information received from the sensor nodes and calculates the maliciousness, competence, and cooperation levels of each node. The sink BS calculates trust values for each. TRACE accounts for the energy requirements of the severely-constrained network nodes by detecting and isolating the bad nodes while eliminating the powerconsuming reputation inquiries and computations required by each node in a distributed approach. AUB Department of Electrical and Computer Engineering A Decentralized Energy-Aware Key Management Scheme for Wireless Sensor Networks • WSN nodes are limited in terms of processing capabilities and battery life. – Encryption is usually avoided and the readings are sent in the clear. – Lightweight encryption techniques are proposed to overcome the limitations of sensor nodes. • Identity-based encryption (IBE) that uses elliptic curve cryptography (ECC) seems to be very promising in terms of energy efficiency. • We propose a novel decentralized IBE-based key management scheme that reduces the energy by using multiple base stations. • The keys are pre-distributed in the WSN and refreshed at specific time intervals. • The system ensures confidentiality of the messages and the availability of WSN service even when multiple nodes and base stations are compromised, at a significant reduction in overall system energy. AUB Department of Electrical and Computer Engineering Security and Privacy in Body Sensor Networks Study two main challenges in the body sensor network security and privacy context – Achieving the correct balance between the complexity of the protocol security operations employed and the energy consumption they incur – Attaining the right tradeoff between privacy and safety by utilizing the patient’s vital signals and other context-related information to minimize the amount of private data released We present a blueprint body sensor network security framework AUB Department of Electrical and Computer Engineering Typical Body Sensor Network Architecture BSN Controller Internet/ Intranet Base Station Hospital Servers Body Sensor Node Wireless Link Wired Link AUB Department of Electrical and Computer Engineering Courses AUB Department of Electrical and Computer Engineering Graduate Courses Offered Cryptography and Computer Security Internet Security Wireless Security Information Security Management Network and Computer Security Laboratory AUB Department of Electrical and Computer Engineering Laboratory Description This laboratory addresses advanced network and computer security topics. Experiments include the execution of attacks, the setup of intrusion detection and prevention, securing computers and wired and wireless networks, and digital forensics. AUB Department of Electrical and Computer Engineering Topics Covered • Section 1 — Networking Basics - How do networks work? – • Section 2 — Vulnerabilities and Threats - How can networks be compromised? – – – – – • Lab 2: Scanning and Enumerating the Network for Targets and Address Spoofing Lab 3: Denial of Service Attacks and Network Applications Exploits Lab 4: Malware Analysis and Botnets Lab 5: Escalating Privilege – Sniffing, Keylogging, Password Cracking and Man in the Middle Attacks Lab 6: Security in Wireless Systems Section 3 — Prevention - How do we prevent harm to the networks? – – • Lab 1: Security Lab Setup and Networking Basics Lab 7: Firewalls Lab 8: Hardening the Host Computer and Securing Network Communications Section 4 — Detection and Response – How do we detect and respond to attacks? – – – Lab 9: Preparing for and Detecting Attacks Lab 10: Identify and Mitigate Network Attacks Lab 11: Digital Forensics AUB Department of Electrical and Computer Engineering Lab Overall Diagram AUB Department of Electrical and Computer Engineering Lab Group Diagram AUB Department of Electrical and Computer Engineering Cabinets Juniper IPS AUB Department of Electrical and Computer Engineering Photos AUB Department of Electrical and Computer Engineering Photos AUB Department of Electrical and Computer Engineering Potential Uses Customized training for industry Testing and benchmarking of equipment Vendor demonstrations Lab could potentially be virtualized to duplicate at low cost AUB Department of Electrical and Computer Engineering ITU Resolutions Relevant to AUB Collaboration ITU Plenipotentiary Resolution 130: Strengthening the role of ITU in building confidence and security in the use of information and communication technologies (Guadalajara, 2010) ITU WTDC Resolution 45: Mechanisms for enhancing cooperation on cybersecurity, including combating spam (Hyderabad, 2010) ITU WTDC Resolution 69: Creation of national computer incident response teams, particularly for developing countries, and cooperation between them (Hyderabad, 2010) ITU WTSA Resolution 58: Encourage the creation of national computer incident response teams, particularly for developing countries (Johannesburg, 2008) UN Resolutions 57/239 (2002) and 58/199 (2004): Creation of a global culture of cybersecurity and the protection of critical information infrastructures AUB Department of Electrical and Computer Engineering Potential Collaboration Research projects Test lab for ITU-T standards conformance Contributions to standards (ITU-T SG17). Several of the questions for Study Group 17 are areas of research at AUB Organizing events (workshops, seminars) Capacity building and Awareness Help establish CERT (AUB Member of the PAN Arab Cyber Security Observatory) AUB Department of Electrical and Computer Engineering Thank you ie05@aub.edu.lb AUB Department of Electrical and Computer Engineering