AN FPGA ARCHITECTURE BASED ON LINEAR and MORPHOLOGICAL IMAGE FILTERING
advertisement

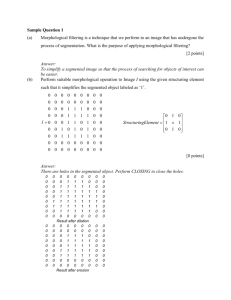
International Journal of Engineering Trends and Technology (IJETT) - Volume4 Issue6- June 2013 AN FPGA ARCHITECTURE BASED ON LINEAR and MORPHOLOGICAL IMAGE FILTERING *BALAKRISHNA RUPAVATH1 M.KEDARESWARA RAO2 1PG Student, Dept. of ECE, Avanthi Institute of Engineering And Technology, Vishakapatnam, AP, India 2Associate Professor, Dept. of ECE, Avanthi Institute of Engineering And Technology, Vishakapatnam, AP, India Abstract: A 3D computer model was evident in the Mask for image segmentation. Morphing is a Technique used to transfer from one image to another. The idea is to make it appear as if one item is physically changing into the other. This paper proposes with the application Of morphing involves working mask worn by the implementation platform which typically consists routing can be programmed aliens in Stargate. This provided a very good illusion. We have to pre-and-post processing the image for better extraction of required image from the acquired image. FPGA can implement these observed results. The image will be transferred from computer to FPGA board using JTAG cable. the FPGA is for communication model. Morphological image filtering using a FPGA Nexys II , Xilinx, Spartan 3E, with educational purposes is presented. Keywords: FPGA architecture, image filtering, segmentation. processing 1. Introduction methods. There exist several Ever since the introduction of television, real- approaches for image segmentation methods for time monitoring has been a growing market. image processing. The after sheds transformation is Adding a video recorder opened up a new world studied in this thesis as a particular method of a for the security industry. Video surveillance soon region-based approach to the segmentation of an made its way into the court rooms and became image. The complete transformation incorporates a convicting evidence. Today, video surveillance pre-processing and post-processing stage that deals systems are omnipresent and part of everyday life with embedded problems such as edge ambiguity and can be found in department stores , banks , bus and the output of a large number of regions. terminals, etc. They are not only used for crime Multiscale Morphological Gradient (MMG) and prevention purposes but also play their role in more Region Adjacency Graph (RAG) are two methods social and industry related applications, e.g. traffic that are pre-processing and post-processing stages, monitoring, processing monitoring, and customer respectively. statistics. With continuously increasing fields of criteria to merge adjacent homogeneous regions. application and integration into our lives. RAG incorporates dissimilarity In this paper, the proposed system has been applied to a set of co-aligned images, which Image segmentation is one of the most include a pair of intensity and range images. It is important categories of image processing. The expected that the hidden edges within the intensity purpose of image segmentation is to divide an image can be detected by observing range data or original image into homogeneous regions. It can be vice versa. Also it is expected that the contribution applied as a pre-processing stage for other image of the range image in region merging can ISSN: 2231-5381 http://www.ijettjournal.org Page 2292 International Journal of Engineering Trends and Technology (IJETT) - Volume4 Issue6- June 2013 compensate for the dominance of shadows within 2. MORPHOLOGICAL IMAGE the intensity image regardless of the original intensity of the object. PROCESSING Morphology is a theory and technique for the analysis and processing of geometrical structures , based on set theory and random functions. Morphology is most commonly applied to digital images, but it can be employed as well on graphs, meshes, solids, and many other spatial structures. Morphology was originally developed for binary images , and was later extended to grayscale functions and images. The purpose of morphological processing is primarily to Figure 1 Elements of Image analysis remove imperfections added during segmentation. The Image processing and analysis is an important basic operations are erosion and dilation .Using the area in the field of robotics. This is particularly true basic operations we can perform opening and closing for the operation of autonomous vehicles. The .More advanced morphological operation can then be operation of an autonomous vehicle is based on implemented using combinations of all of these. first acquiring data that describe its environment. Indeed, the motion planning and control of a fully autonomous vehicle requires an Binary Morphology: Hardware architectures for binary intelligent morphological image is nothing but erosion and controller to be able to make decisions to allow the dilation. the objective is to minimize the number of autonomous vehicle to maneuver in an unknown operations, memory requirement, and memory field based on these data. These data sets include accesses per pixel. Therefore, a fast stall-free low range data, 2D images, and position measurements. complexity architecture is proposed that takes This data is used to identify and avoid obstacles advantage of the morphological duality principle and to map the surrounding terrain. and structuring element decomposition. The main The elements of an image analysis system are advantage of this architecture is that for the shown in Figure 1. Image analysis usually starts common class of flat and rectangular structuring with a pre-processing stage, which includes elements, complexity and number of memory operations such as noise reduction. For the actual accesses per pixel is independent of both image recognition stage, segmentation should be done and structuring element size. before it to extract out only the part that has useful information. Image segmentation is a primary and 3. LABELING ALGORITHM BASED ON critical component of image analysis. The quality CONTOUR TRACING of the final results of an image analysis could The algorithm has lower memory requirements depend on the segmentation step. On the other compared to other labeling techniques and can hand, segmentation is one of the most difficult guarantee labeling of a predefined number of tasks in image processing, especially automatic clusters independent of their shape. In addition, image segmentation. features especially important in this particular application are extracted during the contour tracing ISSN: 2231-5381 http://www.ijettjournal.org Page 2293 International Journal of Engineering Trends and Technology (IJETT) - Volume4 Issue6- June 2013 with little increase in hardware complexity. The Hit-and-Miss implementation is verified on an FPGA in an When eroding, the ―0‖s in the structuring element embedded system environment with an image act like ―don’t care‖ conditions—they don’t really resolution of 320×240 at a frame rate of 25 fps. require that the image be on or off at that point, only that the remaining ―1 pixels fit inside the object. In other words, it finds places that ―look like this‖ (for the 1s), but has no way to say ―but doesn’t look like this‖ (for the 0s). We can combine erosion and dilation to produce an operator that acts like this: the ―hit and miss‖ operator. The operator takes two elements: one that must ―hit‖ and one that must ―miss‖. The operator is defined as follows. If the structuring Figure 2 Morphological Dilation of a Binary Image elements J (hit) and K (miss) are applied to the image A: A ⊗ (J,K) = (A _ J) ∩ (Ac _ K) In other words, the structuring element J must fit inside the object and the element K must fit outside the Region Filling object at that position. Adding the intelligence to detect a black inner point This gives us a form of binary template of sphere, we can use region filling to fill up the sphere matching. For example, the following structuring to be completely white. elements give an ―upper right‖ corner detector: 000 110 010 011 001 000 Figure 3 Region Filling JK Pruning The J element finds the points with connected left Pruning methods are an essential complement to the procedures that tend to leave parasitic components that need to be cleaned up‖ by post processing. For example, the automated recognition of hand printed characters. and lower neighbors, and the H element finds the points without upper, upper right, and right neighbors. In some cases, we will simply use a single structuring element B, with the assumption that J = B and Thickening K = Bc. The structuring elements have the same form as in thinning but with all 1’s and 0’s interchanged, i.e., A ⊗ B = A ⊗ (B, Bc) = (AB) ∩ (Ac _ Bc) However, a separate algorithm for thickening is seldom Notice that this doesn’t, however, allow for a third used in practice. The usual procedure is to thin the case: don’t care‖ pixels ones that could be either inside background instead. ISSN: 2231-5381 or outside the shape. Some authors will for this reason http://www.ijettjournal.org Page 2294 International Journal of Engineering Trends and Technology (IJETT) - Volume4 Issue6- June 2013 write the two operators as a single one using 1s for the The creation of the verification platform is for the don’t care optional and is based on the hardware platform. The positions. In the previous example, this would be MHS file is taken as an input by the Simgen tool to written as create simulation files for a specific simulator. Three x00 types of simulation models can be generated by the 110 Simgen tool: behavioral, structural and timing models. x1x Some other useful tools available in EDK are Platform This form is perhaps more useful for visualizing Studio which provides the GUI for creating the MHS what the structuring element is designed to find. and MSS files. Create / Import IP Wizard which allows Remember, though, that you still have to apply two the creation of the designer's own peripheral and import different operators, one for hit (the 1s) and one for miss them into EDK projects. Platform Generator customizes (the 0s), when implementing hit-and-miss. and generates the processor system in the form of hits, 0s for the misses, and x‖s hardware netlists. There are two options available for debugging the Morphological Smoothing Since opening suppresses bright details smaller application created using EDK namely: Xilinx than the specified SE, and closing suppresses dark Microprocessor Debug (XMD) for debugging the details, they are often used in combination as application software using a Microprocessor Debug morphological filters for image smoothing and noise Module (MDM) in the embedded processor system, and removal Software Debugger that invokes the software debugger Top‐hat and bottom‐hat transformations corresponding to the compiler being used for the Combining image subtraction with openings and closings results in top-hat and bottom processor. C. hat transformations. The top-hat transformation of a grayscale image f is defines as f minus its opening: That ( f ) = f − ( f b) Similarly, the bottom-hat transformation of a grayscale image f is defines as the closing of minus f: B( f) = f •b − f One principal application of these transforms is in removing objects from an image by using an SE in the opening and closing that does not fit the objects to be removed. The difference then yields an image with only the removed objects. The top-hat is used for light objects on a dark background and the bottom-hat – for dark objects on a light background Figure 4 Simulation Results 4. RESULTS The software application can be written in a "C or C++" then the complete embedded processor system for ISSN: 2231-5381 http://www.ijettjournal.org Page 2295 International Journal of Engineering Trends and Technology (IJETT) - Volume4 Issue6- June 2013 user application will be completed, else debug & download the bit file into FPGA. Then FPGA behaves like processor implemented on it in a Xilinx Field Programmable Gate Array (FPGA) device. [3] Bruce A. Draper, J. Ross Beveridge, A.P. Willem Böhm, Charles Ross, Monica Chaw the, ―Accelerated Image Processing on FPGAs‖, IEEE Transactions on Image Processing, Vol. 12, No. 12. Pp. 1543-1551, 2003. [4] A. Castillo, J. Vázquez, J. Ortegón y C. Rodriguez, ―Prácticas de laboratorio Para estudiantes de ingeniería con FPGA‖, IEEE Latin America Transactions, Vol. 6, No.2, pp. 130- 5. Conclusions In this paper, we have proposed to make it 136, 2008. [5] K. T. Gribbon, D. G. Bailey and C. T. Johnston, ―Design appear as if one item is physically changing into the Patterns for Image Processing Algorithm Development on other. The purpose of morphological processing is FPGAs‖, TENCON 2005,pp. 1-6, November 21-24, 2005. primarily to remove imperfections added during [6] Bob L. Sturm and Jerry D. Gibson, ―Signals and Systems Using MATLAB: An Integrated Suite of Applications for segmentation. The basic operations are erosion and dilation .Using the basic operations we can perform opening and closing .More advanced morphological operation can then be implemented using combinations of all of these. The proposed method is inherently parallel, since computations for each pixel of each sequence frame can be done concurrently with no need for communications. This can help in Exploring and Teaching Media Signal Processing‖, 35th ASEE/IEEE Frontiers in Education Conference, pp. 21-25, October 19 – 22, Indianapolis, Indiana,USA,2005. [7] Javier Vicente, Begoña García, Ibon Ruiz, Amaia Méndez, Oscar Lage,―EasySP: Nueva Aplicación Para la Enseñanza de Procesado de Señal‖, IEEE-RITA, Vol. 2, No. 1, 2007. [8] David Báez-López, David Báez-Villegas, René Alcántara, Juan José Romero, Tomás Escalante, ―A package for filter design based on MATLAB‖, Computer Applications in Engineering Education, Vol. 9, No. 4, pp. 259-264, 2002. lowering execution times for high-resolution sequences. Moreover, the approach is suitable to be adopted in a layered framework, where, operating at region-level, it can improve detection results allowing to more efficiently tackle the camouflage problem and to distinguish morphological Image by the morphological operator. Acknowledgements The authors would like to thank the anonymous reviewers for their comments which were very helpful in improving the quality and presentation of this paper. References: [1] C.T. Johnston, K.T.Gribbon, D.G.Bailey, ―Implementing Image Processing Algorithms on FPGAs‖, Eleventh Electronics New Zealand Conference, Palmerston North, New Zealand, 2004. [2] D.G. Bariamis, D.K. Iakovidis, D.E. Maroulis, S. A. Karkanis, ―An FPGA-based Architecture for Real Time Image Feature Extraction‖, Proceedings of the 17th International Conference on Pattern Recognition, August 23-26, Cambridge, UK, 2004. ISSN: 2231-5381 http://www.ijettjournal.org Page 2296