Win-Coupon: An Incentive Framework for 3G Traffic Offloading Xuejun Zhuo Wei Gao
advertisement

Win-Coupon: An Incentive Framework for
3G Traffic Offloading
Xuejun Zhuo1, Wei Gao2, Guohong Cao2, Yiqi Dai1
5/29/2016
1Tsinghua University, 2The Pennsylvania
State University
Outline
Background and Motivation
Existing work and Challenges
Main Approach of Win-Coupon
Evaluation
Conclusion
Background & Motivation
3G Data Traffic
o The smart mobile devices offer ubiquitous
Internet access and diverse multimedia authoring
and playback capabilities.
o 3G data traffic is growing at an unprecedented
rate.
• By 2014, an average broadband mobile user
will consume 7GB of traffic per month.
• The total data traffic throughout the world
will reach 3.6 exabytes per month.
Overload!!!
Background & Motivation
How to solve the 3G overload problem ?
o Increase 3G network capacity
1.
2.
Expensive
Inefficient
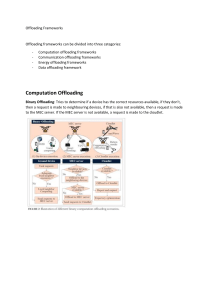
o Offloading part of the 3G data traffic to other networks
•Delay Tolerant Networks
- DTN is a general paradigm of network in which nodes communicate
without stable and continuous end-to-end connectivity.
• WiFi hotspots
Low Cost
Efficient
Background & Motivation
How to utilize DTNs or WiFi hotspots for 3G traffic offloading?
Extra Delay
•Short range
•High mobility
•Large data file
Outline
Background and Motivation
Existing work and Challenges
Main Approach of Win-Coupon
Evaluation
Conclusion
Existing work and Challenges
Offloading 3G traffic by DTNs
o [1] WoWMoM 2011 designs a framework, called PUSH-and-TRACK, which includes
multiple strategies to determine how many copies should be injected by 3G and to whom,
and then leverages DTNs to offload 3G traffic.
o [2] CHANTS 2010 provides three simple algorithms to exploit DTNs to facilitate data
dissemination among mobile users, in order to reduce the overall 3G traffic.
o [3] CHANTS 2008, [4] MOBIHOC 2009 propose social-based algorithms to improve the
performance of data dissemination in DTNs.
Offloading 3G traffic by WiFi hotspots
o [5]MOBISYS 2010 measures the offloading potential of the public WiFi based on city wide
vehicular traces.
o [6]CoNEXT 2010 considers a more general mobile scenario, and present a quantitative
study on the performance of on-the-spot and delayed offloading by using WiFi.
However these works have not considered the satisfaction loss of the users
when a longer delay is caused by traffic offloading!
Existing work and Challenges
How to stimulate users to leverage their delay tolerance for 3G
traffic offloading?
o Incentive mechanism
The users with high delay tolerance and large
offloading potential should be prioritized for 3G
traffic offloading.
How to retrieve users’ delay tolerance, and how to determine pricing
model?
o Auction
bids
3G operator: buyer
Mobile user: seller
How to measure users’ offloading potential?
o Stochastic analysis
Outline
Background and Motivation
Existing work and Challenges
Main Approach of Win-Coupon
Evaluation
Conclusion
Main Approach of Win-Coupon
Overview
o Reserve-auction based incentive mechanism
• Allocation: the 3G operator decides which bidders are the winners and how
long they need to wait.
• Pricing: the 3G operator decides how much to pay for each winner.
o Optimal auction outcome
• min. incentive cost
• s.t. expected offloading traffic ≥ offloading target
Main Approach of Win-Coupon
User Delay Tolerance
o Satisfaction function S(t) – represents the price that the user is willing to pay for
the data service with the delay t.
= 800 $ (Private value)
Price: 1000 $ (Bid)
Gain 200 $ (Utility)
Reverse Auction
OK. Deal! Pay 1000 $
(Market clearing price)
o Involving a single buyer and multiple sellers, and the buyer decides its purchase
based on the bids sent by the sellers.
oBid (bi): It is submitted by bidder i to express i’s valuation on the resource for sale,
which is not necessarily true.
o Private value (xi): It is the true valuation made by bidder i for the resource.
o Market clearing price (pi): It is the price actually paid by the buyer to bidder i.
o Utility (ui): It is the residual worth of the sold resource for bidder i.
Main Approach of Win-Coupon
Bidding
Main Approach of Win-Coupon
Bidding
o tbound : Upper bound of user’s delay tolerance Resources for sale
o User can divide tbound into multiple time units to sell
o bid format: b = {b1, b2, …, bl}
Main Approach of Win-Coupon
Allocation
Main Approach of Win-Coupon
Allocation
o Goals:
• Which bidders are the winners
• How long they need to wait
o Problem formulation
• min. incentive cost
• s.t. expected offloading traffic ≥ offloading target
NP-Hard!!!
Main Approach of Win-Coupon
Pricing
Main Approach of Win-Coupon
Pricing
o Goals:
• How much to pay for each winner
• Assure Truthfulness and Individual Rationality
o VCG-style pricing
• Each winning bidder is paid by its “opportunity cost”
• Opportunity cost: the cost of an alternative that must be forgone in order to
pursue a certain action – the benefits you could received by taking an
alternative action.
•3G operator pays bidder i the coupon with value equal to the “opportunity
cost” exerted to all the other bidders due to i’s presence.
c1: The total value of coupons requested by all the bidders under the optimal
allocation solution without the presence of bidder i
c2: The total value of coupons requested by all the bidders except for bidder I
under the current optimal allocation solution.
Main Approach of Win-Coupon
Pricing
o Theorem 1: In Win-Coupon, for each bidder, say i, setting its bids truthfully, i.e.,
bi = xi, is a weakly dominant strategy.
Truthfulness
oTheorem 2: In Win-Coupon, all bidders are guaranteed to obtain non-negative
utility.
Individual Rationality
Main Approach of Win-Coupon
Predicting the bidders’ offloading potential
Main Approach of Win-Coupon
Predicting the bidders’ offloading potential
o Network Model
• Contact frequency: Exponential inter-contact time
• Short contact duration: Random Linear Network Coding (RLNC)
o Stochastic Analysis
• Ordinary Differential Equation (ODE)
Outline
Background and Motivation
Existing work and Challenges
Main Approach of Win-Coupon
Evaluation
Conclusion
Evaluation
Numerical Results
o Verify the accuracy of our prediction model
o Compared the numerical results derived by using Matlab to the actual results
derived by using Monte-Carlo simulations.
Accurate!!
Evaluation
Real trace driven simulations
o UCSD trace: recording the contact distory of 275 HP Jornada PDAs carried by
students over 77 days.
o Synthetic user delay tolerance
o Synthetic data query information
o We generate 50 data items, and each contains 8 packets
o Length of one auction round: one hour
o Performance metrics:
• Offloaded traffic
• Allocated coupons
• Average downloading delay
Evaluation
Impact of Num. of bidders
Impact of Reserve Price
40% of the 3G traffic can be offloaded
Evaluation
Impact of User Delay Tolerance
Evaluation
Large-scale trace driven simulations
o Large-scale trace includes 2750 nodes by replicating the nodes in UCSD trace 10
times
o Length of one auction round: ten minute
Simulation Results
40% of the 3G traffic can be offloaded
The corresponding delay is less than 5 hours
Outline
Background and Motivation
Existing work and Challenges
Main Approach of Win-Coupon
Evaluation
Conclusion
Conclusion
We propose a novel incentive framework to motivate users to
leverage their delay tolerance for 3G offloading.
We design a reverse auction based incentive mechanism, Win-
Coupon, and formally prove that it has two desirable properties: 1)
Truthfulness, 2) Individual Rationality.
Taking DTNs as a study case, we provide an accurate model to predict
users’ offloading potential.
We implement Win-Coupon by using realistic DTN trace UCSD, and
evaluate its practical use.
Thanks
Q&A
Network Security Lab, Computer Science and Technology, Tsinghua University
Selected References
[1] J. Whitbeck, Y. Lopez, J. Leguay, V. Conan, M. D, Amorim, “Relieving the wireless infrastructure: When
opportunistic networks meet guaranteed delays”, in Proc. of IEEE WoWMoM, 2011.
[2] B. Han, P. Hui, V. Kumar, M. V. Marathe, G. Pei, A. Srinivasan, “Cellular traffic offloading through
opportunistic communications: A case study”, in Proc. of ACM CHANTS, 2010.
[3] C. Boldrini, M. Conti, A. Passarella, “Modelling data dissemination in opportunistic networks”, in Proc.
of ACM CHANTS, 2008.
[4] W. Gao, Q. Li, B. Zhao, G. Cao, “Multicasting in delay tolerant networks: a social network perspective”,
in Proc. of ACM MOBIHOC, 2009.
[5] A. Bala, R. Mahajan, A. Venkataramani, “Augmenting mobile 3G using wifi”, in Proc. of ACM MOBISYS,
2010.
[6] K. Lee, I. Rhee, J. Lee, S. Chong, Y. Yi, “Mobile data offloading: how much can wifi deliver?”, in Proc. of
ACM CoNETX, 2010.