Document 11906344
advertisement
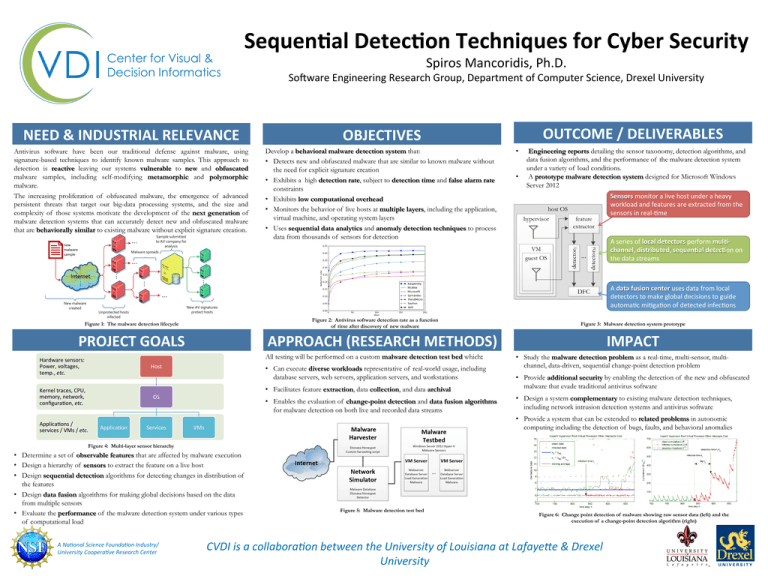
Sequen/al Detec/on Techniques for Cyber Security Spiros Mancoridis, Ph.D. So2ware Engineering Research Group, Department of Computer Science, Drexel University NEED & INDUSTRIAL RELEVANCE Antivirus software have been our traditional defense against malware, using signature-based techniques to identify known malware samples. This approach to detection is reactive leaving our systems vulnerable to new and obfuscated malware samples, including self-modifying metamorphic and polymorphic malware. The increasing proliferation of obfuscated malware, the emergence of advanced persistent threats that target our big-data processing systems, and the size and complexity of those systems motivate the development of the next generation of malware detection systems that can accurately detect new and obfuscated malware that are behaviorally similar to existing malware without explicit signature creation. OUTCOME / DELIVERABLES OBJECTIVES Develop a behavioral malware detection system that: • Detects new and obfuscated malware that are similar to known malware without the need for explicit signature creation • Exhibits a high detection rate, subject to detection time and false alarm rate constraints • Exhibits low computational overhead • Monitors the behavior of live hosts at multiple layers, including the application, virtual machine, and operating system layers • Uses sequential data analytics and anomaly detection techniques to process data from thousands of sensors for detection • • Engineering reports detailing the sensor taxonomy, detection algorithms, and data fusion algorithms, and the performance of the malware detection system under a variety of load conditions. A prototype malware detection system designed for Microsoft Windows Server 2012 Sensors monitor a live host under a heavy workload and features are extracted from the sensors in real-­‐Dme A series of local detectors perform mul/-­‐ channel, distributed, sequen/al detec/on on the data streams A data fusion center uses data from local detectors to make global decisions to guide automaDc miDgaDon of detected infecDons Figure 2: Antivirus software detection rate as a function of time after discovery of new malware Figure 1: The malware detection lifecycle PROJECT GOALS APPROACH (RESEARCH METHODS) All testing will be performed on a custom malware detection test bed which: Hardware sensors: Power, voltages, temp., etc. Host Kernel traces, CPU, memory, network, configuraDon, etc. • Can execute diverse workloads representative of real-world usage, including database servers, web servers, application servers, and workstations OS ApplicaDons / services / VMs / etc. ApplicaDon Services Figure 3: Malware detection system prototype IMPACT • Study the malware detection problem as a real-time, multi-sensor, multichannel, data-driven, sequential change-point detection problem • Facilitates feature extraction, data collection, and data archival • Provide additional security by enabling the detection of the new and obfuscated malware that evade traditional antivirus software • Enables the evaluation of change-point detection and data fusion algorithms for malware detection on both live and recorded data streams • Design a system complementary to existing malware detection techniques, including network intrusion detection systems and antivirus software • Provide a system that can be extended to related problems in autonomic computing including the detection of bugs, faults, and behavioral anomalies VMs Figure 4: Multi-layer sensor hierarchy • Determine a set of observable features that are affected by malware execution • Design a hierarchy of sensors to extract the feature on a live host • Design sequential detection algorithms for detecting changes in distribution of the features • Design data fusion algorithms for making global decisions based on the data from multiple sensors • Evaluate the performance of the malware detection system under various types of computational load A Na.onal Science Founda.on Industry/ University Coopera.ve Research Center Figure 5: Malware detection test bed Figure 6: Change point detection of malware showing raw sensor data (left) and the execution of a change-point detection algorithm (right) CVDI is a collabora.on between the University of Louisiana at Lafaye:e & Drexel University