Creation of Intra-Departmental Battle Lab Claudia Garcia and Kelsey Tankesley
advertisement

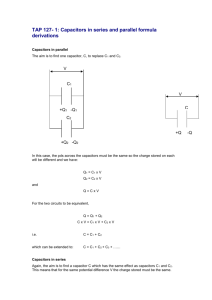
Creation of Intra-Departmental Battle Lab Claudia Garcia and Kelsey Tankesley Naval Postgraduate School, Monterey CA Lecturer Albert Barreto, Virtualization and Cloud Computing Lab Introduction Soldering Rats with brains navigated mazes faster Results Brainectomiz ed Conclusions Time (s) Virtualization and Ethical Hacking lab are The purpose of this project was to integrate excess agency resources per Department of Defense (DoD) consolidation directive. For this, a virtualization lab at NPS was being restructured both physically and virtually throughout the summer. This lab, in the Information Sciences Department, was connected to the Ethical Hacking lab in the Computer Science Department. Both departments are under the Graduate School of Operational and Information Sciences (GSOIS). The connection is to be used in a proof of concept for a master’s level thesis where volunteers are to break into virtual phones and be tracked as they go through mock servers. This project was a journey through the open systems interconnection (OSI) Model as many layers were tempered with in order to have the needed connections. Figure connected and sharing resources Control (brain intact) • Virtualization Lab has updated hardware and software Maze difficulty SAS cards are now • 99% of malfunctioning index fully operational • LT Madden will run his proof of concept late August 2012 The network and hardware we helped lay out will be used in classrooms in GSOIS by students such as LT Madden who will be able to use this new resource to run his proof of concept. Figure 2: The green capacitors that were removed since they were shorted out. We could tell they were no longer functional due to a bulge that developed on the previously flat top of the capacitor. Figure 8: Network map of both labs now linked and sharing resources. Figure 5: Repaired SAS Card being installed back into server. Acknowledgments We thank Hartnell College, Naval Postgraduate School, Cebrowski Institute, Lecturer Albert Barreto, Senior Lecturer Scott Cote, LT Robert Madden, Alison Kerr, Andy Newton, Patrick McNeill, Cassandra Martin, Ana Hernandez Figure 1: Network layout to connect the two labs as one collaborating network Methods and Procedures The Virtualization Lab was prepared to be connected to the Ethical Hacking Lab. Due to the nature of the Ethical Hacking Lab, it was essential that the Virtualization Lab was on an isolated network, away from the internet and the school’s main network. The Server racks in the Virtualization Lab needed to be updated up to ESXi 5.0 for compatibility and IP addresses were changed to avoid conflicting addresses in the new network. Fleet Numerical was outsourcing servers and they were distributed among faculty in NPS. However, all the servers had bad SAS cards due to shorted capacitors. The bad capacitors had to be replaced. Some required unconventional soldering techniques since one of the capacitors on each card had little to no heat plating thus the heat was often distributed to the card rather than the solder. Considerable experimentation was required to find a solution. Servers and switches were physically unscrewed and rearranged. An external CD drive was used to load the new operating system onto all the servers. Figure 3: The black capacitors were purchased to replace the shorted out green capacitors. They were a little taller so we simply would lay them flat on the card upon soldering. Figure 6: Installing repaired SAS cards into server racks in multiple labs. For further information Please contact: abarreto@nps.edu (Albert Barreto) claudiagarcia16@gmail.com (Claudia Garcia) kelseytankesl@aol.com (Kelsey Tankesley) More information can be obtained at: Figure 5. Figure 4: To solder the SAS cards we clamped them down on a table and applied heat with a soldering tool. Solder flux was necessary to properly melt the solder on the capacitors that had no heat plating. Figure 7: Map layout of LT Madden’s honeypot layout for his proof of concept Master’s Thesis. When the two labs had updated hardware, preparations were made to run the proof of concept project. The Ethical hacking room was mapped in order to assign static virtual machines to each workstation for his exercise. 3C Program: Cebrowski Institute: GSOIS: