Chapter 7 LOCAL TESTING OF REED-MULLER CODES 7.1 Introduction
advertisement

111
Chapter 7
LOCAL TESTING OF REED-MULLER CODES
From this chapter onwards, we will switch gears and talk about property testing of
codes.
7.1 Introduction
A low degree tester is a probabilistic algorithm which, given a degree parameter _ and
oracle access to a function on arguments (which take values from some finite field ),
has the following behavior. If is the evaluation of a polynomial on variables with total
degree at most _ , then the low degree tester must accept with probability one. On the other
hand, if is “far” from being the evaluation of some polynomial on variables with degree
at most _ , then the tester must reject with constant probability. The tester can query the
function to obtain the evaluation of at any point. However, the tester must accomplish
its task by using as few probes as possible.
Low degree testers play an important part in the construction of Probabilistically Checkable Proofs (or PCPs). In fact, different parameters of low degree testers (for example, the
number of probes and the amount of randomness used) directly affect the parameters of the
corresponding PCPs as well as various inapproximability results obtained from such PCPs
([36, 5]). Low degree testers also form the core of the proof of MIP NEXPTIME in [9].
Blum, Luby, and Rubinfeld designed the first low degree tester, which handled the
linear case, i.e., _s G ([21]), although with a different motivation. This was followed by
a series of works that gave low degree testers that worked for larger values of the degree
parameter ([93, 42, 7]). However, these subsequent results as well as others which use low
degree testers ([9, 43]) only work when the degree is smaller than size of the field . Alon
et al. proposed a low degree tester for any nontrivial degree parameter over the binary field
Á [1].
A natural open problem was to give a low degree tester for all degrees for finite fields of
size between two and the degree parameter. In this chapter we (partially) solve this problem
by presenting a low degree test for multivariate polynomials over any prime field B .
7.1.1 Connection to Coding Theory
The evaluations of polynomials in variables of degree at most _ are well known ReedMuller codes (note that when ùG , we have the Reed-Solomon codes, which we considered in Chapter 6). In particular, the evaluation of polynomials in variables of degree
112
at most _ over ¯ is the Reed-Muller code
or RM¯ ?_\!`j with parameters _ and . These
codes have length and dimension (see [28, 29, 69] for more details). Therefore,
vector of evaluations of) the function is a valid
a function has degree _ if and only if (the
codeword in RM¯ /³!Z_N . In other words, low degree testing is equivalent to locally testing
Reed-Muller codes.
7.1.2 Overview of Our Results
It is easier to define our tester over Á . To test if has degree at most _ , set a
let Í÷<_úntG (mod 2). Pick -vectors ;UZ!¥µ!Z; and ; from , and test if
Z , and
'
ü
ü '
;
Î
Ü ; k !
Ü Zµ
; n
Û Z
×½Ù | T × Û × × T
888
s
; ý
G (and we will stick to this convention
where for notational convenience we use
throughout this chapter). We remark here that a polynomial of degree at most _ always
passes the test, whereas a polynomial of degree greater than _ gets caught with non-negligible
probability . To obtain a constant rejection probability we repeat the test oG6e times.
The analysis of our test follows a similar general structure developed by Rubinfeld and
Sudan in [93] and borrows techniques from [93, 1]. The presence of a doubly-transitive
group suffices for the analysis given in [93]. Essentially we show that the presence of a
doubly-transitive group acting on the coordinates of the dual code does indeed allow us
to localize the test. However, this gives a weaker result. We use techniques developed in
[1] for better results, although the adoption is not immediate. In particular the interplay
between certain geometric objects described below and their polynomial representations
plays a pivotal role in getting results that are only about a quadratic factor away from
optimal query complexity.
In coding theory terminology, we show that Reed-Muller codes over prime fields are
locally testable. We further consider a new basis of Reed-Muller code over prime fields that
in general differs from the minimum weight basis. This allows us to present a novel exact
characterization of the multivariate polynomials of degree _ in variables over prime fields.
Our basis has a clean geometric structure in terms of flats [69], and unions of parallel flats
but with different weights assigned to different parallel flats1 . The equivalent polynomial
and geometric representations allow us to provide an almost optimal test.
Main Result
Our results may be stated quantitatively as follows. For a given Ø integer _òH§
U ILG and a
] Z
;
Z
ý
given real , our testing algorithm queries at W. n8_µh U X 2 points to determine
1
The natural basis given in [28, 29] assigns the same weight to each parallel flat.
113
whether can be described by a polynomial of degree at most _ . If is indeed a polynomial
of degree at most _ , our algorithm always accepts, and if has a relative Hamming distance
at least from every degree _ polynomial, then our algorithm rejects with probability
Z
U IzG , our tester still works but more efficient testers are
at least . (In the case _]RS
known). Our result is almost optimal since any such testing algorithm must query in at
]
Z
least s n U ý p X many points (see Corollary 7.5).
We extend our analysis also to obtain a self-corrector for (as defined in [21]), in case
the function is reasonably close to a degree _ polynomial. Specifically, we show that the
value of the function at any given point ¬+l may be obtained with good probability
random points. Using pairwise independence we can achieve
by querying on yU
even higher probability by querying on U random points and using majority logic
decoding.
7.1.3 Overview of the Analysis
The design of our tester and its analysis follows the following general paradigm first formalized by Rubinfeld and Sudan [93]. The analysis also uses additional ideas used in [1].
In this section, we review the main steps involved.
The first step is coming up with an exact characterization for functions that have low
degree. The characterization identifies a collection of subsets of points and a predicate
such that an input function is of low degree if and only if for every subset in the collection,
the predicate is satisfied by the evaluation of the function at the points in the subset. The
second step entails showing that the characterization is a robust characterization, that is,
the following natural tester is indeed a local tester (see section 2.3 for a formal definition):
Pick one of the subsets in the collection uniformly at random and check if the predicate is
satisfied by the evaluation of the function on the points in the chosen subset. Note that the
number of queries made by the tester is bounded above by the size of the largest subset in
the collection.
There is a natural characterization for polynomials of low degree using their alternative
interpretation as a RM code. As RM code is a linear code, a function is of low degree if
and only if it is orthogonal to every codeword in the dual of the corresponding RM code.
The problem with the above characterization is that the resulting local tester will have to
make as many queries as the maximum number of non-zero position in any dual codeword,
which can be large. To get around this problem, instead of considering all codewords in the
dual of the RM code, we consider a collection of dual codewords that have few non-zero
positions. To obtain an exact characterization, note that this collection has to generate the
dual code.
We use the well known fact that the dual of a RM code is a RM code (with different
parameters). Thus, to obtain a collection of dual codewords with low weight that generate
the dual of a RM code it is enough to find low weight codewords that generate every RM
code. To this end we show that the characteristic vector of any affine subspace (also called a
114
flat in RM terminology [69]) generates certain RM codes. To complete the characterization,
we show that any RM code can be generated by flats and certain weighted characteristic
vectors of affine subspaces (which we call pseudoflats). To prove these we look at the affine
subspaces as the intersection of (a fixed number of) hyperplanes and alternatively represent
the characteristic vectors as polynomials.
To prove that the above exact characterization is robust we use the self-correcting approach ([21, 93]). Given an input we define a related function as follows. The value
of
¬" is defined to be the most frequently occurring value, or plurality, of at correlated
random points. The major part of the analysis is to show that if disagrees from all low
degree polynomials in a lot of places then the tester rejects with high probability.
The analysis proceeds by first showing that and agree on most points. Then we show
that if the tester rejects with low enough probability then is a low degree polynomial. In
other words, if is far enough from all low degree polynomials, then the tester rejects with
high probability. To complete the proof, we take care of the case when is close to some
low degree polynomial separately.
7.2 Preliminaries
Â
Throughout this chapter, we use U to denote a prime and to denote a prime power (U
for some positive integer Á ) to be a prime power. In this chapter, we will mostly deal with
prime fields. We therefore restrict most definitions to the prime field setting.
For any _ò+t k
PILGÑ¡ , let
denote the family of all functions over ¯ that are polynomials of total degree at most _ (and w.l.o.g. individual degree at most }I5G ) in variables. In particular L+Q
if there exists coefficients @ Ù +Q ¯ , for every Íy+Ê ¡ ,
888
;
?Îä+w¢ !¥¥Y!fJIGe¦ , Î Û Z ?Îä>
E _ , such that
û
û
]
ü
Ù Ýiý ¯
8 8 8 Ù 8 8 8 å Z
û
û
à Ù ¤
ýÏ
s
Ù
t
û
Ï
å
¤
¬
Î
Ù
888 Û
û
Î
Z
û
û
@
(7.1)
The codeword corresponding to a function will be the evaluation vector of . We recall the
definition of the (Primitive) Reed-Muller code as described in [69, 29].
of -tuples, for Q G , over the field ¯ .
Definition 7.1. Let ÷"¯ be the vector space
;
order Reed-Muller code RM¯ ÑB!`j is the
For any such that EÊ{E÷k
}I5G , the ¯
subspace of ¯ ¿ ¿ of all -variable polynomial functions (reduced modulo ¬ Î Ig¬Î ) of degree
at most .
This implies that the code corresponding to the family of functions -
is RM¯ ?\_ !Y .
Therefore, a characterization for one will simply translate into a characterization for the
other.
We will be using terminology defined in Section 2.3. We now briefly review the definitions that are relevant to this chapter. For any two functions B! S$ ¯ ) ¯ , the relative
115
;
distance Ýci"! Â+v !¥G¡ between and is defined as Ýci"! Ä Pr Ù |٠ĵ/¬[ Ï
¬"½¡ .
ûÌ
For a function and a family of functions ± (defined over the same domain¾ and range), we
;
say is - close to ± , for some R|gR2G , if, there exists an ~+x± , where ÝUW"! }Ez .
Otherwise it is - far from ± .
A one sided testing algorithm (one-sided tester) for -
is a probabilistic algorithm that
;
is given query access to a function and a distance parameter , R,RG . If S+gJ
, then
the tester should always accept (perfect completeness), and if is -far from -
, then
Z
with probability at least the tester should reject .
product of ¬ and ; , denoted ¬^; , is defined to be
For vectors ¬j!Z;§+]B , the dot (scalar)
Î Û Z ¬ÎX
; Î , where ÐÎ denotes the Í co-ordinate of .
To motivate the next notation which we will use frequently, we give a definition.
;
, a -flat in is a -dimensional affine subspace. Let
Definition 7.2. For any ÷
c; Z\!ä!; +] be linearly independent vectors and ;-+] be a point. Then the subset
'
lq¢
ü '
ÎÛ Z
ÜfÎX
; Îñ
n ;<· BÍ8+ ¡BÜfÎä+]CC¦
is a -dimensional flat. We will say that is generated by ;CZ!Y!; at ; . The incidence
'
vector of the points in a given -flat will be referred to as the codeword corresponding to
the given -flat.
Given a function KX$ " )hC , for ;cZ\!ä!Z; 6! ; +]D we define
ý
<c; Z\!ä!Z; 6! ; Ä ü
ûÌ × Û
×
×
> ;n
ü
ÜfÎ ;XÎWb!
(7.2)
Ù
Ù
Î
Ì
888 | ý
which is the sum of the evaluations of function over an -flat generated by ;Z!¥äZ! ; ! at
H
; . Alternatively, as we will see later in Observation 7.4, this can also be interpreted as the
dot product of the codeword corresponding to the -flat generated by ;Z\!äZ! ; at ; and that
corresponding to the function .
While -flats are well-known, we define a new geometric object, called a pseudoflat. A
-pseudoflat is a union of .
U IQG parallel ÑIQG -flats.
Definition 7.3. Let ÐZb!ë³!äf! úåZ be parallel ioILG -flats ( 0ÊG ), such that for some
;q+÷ and all _[+% UKIqX
V ¡ ,
Zg½
Â
; n|ä
, where for any set ¶ýO and ;q+÷ ,
def
;.n¶ ù¢¬gn=ú
; · ¬|+÷¶9¦ . We define a -pseudoflat to be the union of the set of points
9Z to úåZ . Further, given an G (where GwEý~
G E USI5V ) and a -pseudoflat, we define
a i"Z! G> pseudoflat vector as follows. Let × be the incidence vector of for _+| UgIqG\¡ .
åZ
Then the Ñ"!ZG> -pseudoflat vector is defined to be Û Z M× . We will also refer to the ÑB!£G
pseudoflat vector as a codeword.
Let be a -pseudoflat. Also, for S+ UuI5G¡ , let be the iaI5G -flat generated by
;cZ\!ä!; åZ at ;"n ÐZ ; , where ;cZ!Y
!; åZ are linearly independent. Then we say that the
'
'
116
i "Z! G> -pseudoflat vector corresponding to as well as the pseudoflat , are generated by
;"Z! ;cZ\!¥¥ä!Z; åZ at ; exponentiated along ; .
'
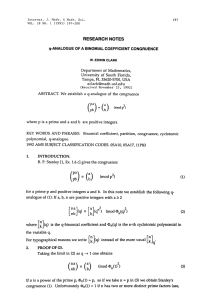
See Figure 7.1 for an illustration of the Definition 7.3.
&
&
%
&
%
&
%
&
%
%
$
$
$
$
$
!
!#"
!
!
!
!
-pseudoflat vector corresponding to
:
:
U Figure 7.1: Illustration of a -pseudoflat defined over with gzVUQ! S
and ´
.
Picture on the left shows the points in (recall that each of Z\!¥¤¥¤¤!f are G -flats or lines).
åZ : points in it. The points in are shown by filled
Each µÎ (for G[E2ÍyEm ) has UB'
circles and the points in (' [ are shown by unfilled circles. The picture on the right is the
'
WVC¥! G -pseudoflat corresponding to .
Given a function Ke$ Î
H
ùC
)
.IXV ¡ , we define
, for ;cZ\!¥¥ä!Z; 6! J
; +g , for all Í3+F U
ü
<;cZ\!¥¥µ!Z; 6! ; Ä Ì
ûÌ × Û
× Ù
888 | ý
×
Ü
Î
ü
; n
Z Xµ ³
Ü ; b¤
Ù
(7.3)
As we will see later in Observation 7.5, the above can also be interpreted as the dot product
of the codeword corresponding to the ½ !ZG> -pseudoflat vector generated by ;DZ\!äZ! ; at ;
exponentiated along ;CZ and the codeword corresponding to the function .
7.2.1 Facts from Finite Fields
In this section we spell out some facts from finite fields which will be used later. We begin
with a simple lemma.
Lemma 7.1. For any _9+F ¸JIG¡ ,
Proof. First note that Ù |
¯ åZ 9 ¾
follows that Ù | @
9
¾
@
9
Ù|
¾
@
k
Ï ; if and only if _ tJIQG .
Ù @ . Observing that for any @_+l ¯X , @ ¯ åZ |
9
;
¾
Ù| G pIGo Ï .
9
¾
G , it
117
;
Ù | @ . Let be a generator of ¯X . The sum
¯ åU Î
åZ 9 ¾
Ï ò
t
I G and
can be re-written as Î ÛCý N ¾ e å Z . The denominator is non-zero for _}q
N
¯ åZ
thus, the fraction is well defined. The proof is complete by noting that
pG .
Ï I_G , Next we show that for all _òt
]
]
This immediately implies the following lemma.
+ »JIQG¡ . Then
Lemma 7.2. Let _ëZ!äZ! _ F
ü
Ù
888 | ¾
Ü
× ×
Ò
Ó
; Ó
è eC ­ ©>­C¨ ) èf_ Zk±
l
_Ð|C±
_ t
JQ
I <G ¤
Z Ü bÜ Ï
Ø
Proof. Note that the left hand side can be rewritten as x Î Ù .
×v
^
Ù|
Ü
Î 2
¾
(7.4)
¤
We will need to transform products of variables to powers of linear functions in those
variables. With this motivation, we present the following identity.
Lemma 7.3. For each "! s.t.
Ü
å
'
' ÎÛ Z
¬ÎÁ
ü '
ÎÛ Z
;
RQ§EpU.IG there exists Ü '
>å Î
¶ Î
IG ' B
where
¶BÎj
+]
*
ü
Û
á
Ú ¹
' ¿ ¹ë¿
´ X such that
Û Î
ü
¬
Ù
'
¤
(7.5)
¹
Proof. Consider the right hand side of the (7.5). Note that all the monomials are of degree
exactly . Also note that x Î' Û Z ¬CÎ appears only in the ¶ and nowhere else. Now consider
'
;
any other monomial of degree that has a support of size , where RüFRH : w.l.o.g.
Î
Î Î
assume that this monomial is à Q¬ Z ¬ ¥ë¬ S such that Z"nF_
n 5 . Now note that
for any × Ê £¡ , à appears with a coefficient of Î Î ' O Î S in the expansion of Ù ¬ ' .
S ¹ åS
Further for every Í*
, the number of choices of ×
£¡ with ·O
× ·äHÍ is exactly ' å> <Î .
'
Therefore, summing up the coefficients of à in the various summands ¶úÎ (along with the
IG' å>Î factor), we get that the coefficient of à in the right hand side of (7.5) is
Í`
Ø
,+
W
þ \Z ! !¥¤¥¤¥¤ !
Í` ͽ
Íÿ
ü '
ÿ
þ Z\! !¥¤¥¤¤¥!
þ Z\! !¥¤¥¤¤¥!
;
¤
Í` Í
Í` Í
Moreover, it is clear that Ü
-+
Ø
I
å>Î *
IG '
þ I´Í
ÎÛ
Í
`Í ÿ
`Í ÿ
ü' å
S
ÛCý
å å
IG ' S
GIG ' å
'
' Å Z½»Z½ O ¸Z 5T" (mod U ) and Ü ' Ï
;
Iÿ
þ I I
for the choice of .
ÿ
118
7.3 Characterization of Low Degree Polynomials over In this section we present an exact characterization for the family -
over prime fields.
Specifically we prove the following:
;
Í §
§
I V .) Let ÐòU IxVPî
I G . Then a
Theorem 7.1. Let _m UÂILG<nºG . (Note E G§E U ~
function belongs to
, if and only if for every ;CZ\!ä!Z; Z 6! ; +]B , we have
Î
H
Ì
;
?;cZ!ä!Z; ' Z 6! ;³
'
(7.6)
As mentioned previously, a characterization for the family (
is equivalent to a characterization for RM<_\!j . It turns out that it is easier to characterize when viewed as
RM<_\!j . Therefore our goal is to determine whether a given word belongs to the RM
code. Since we deal with a linear code, a simple strategy will then be to check whether
the given word is orthogonal to all the codewords in the dual code. Though this yields a
characterization, this is computationally inefficient. Note however that the dot product is
linear in its input. Therefore checking orthogonality with a basis of the dual code suffices.
To make it computationally efficient, we look for a basis with small weights. The above
theorem essentially is a clever restatement of this idea.
We recall the following useful lemma which can be found in [69].
Lemma 7.4. RM¯ Ñ"!j is a linear code with block length and minimum distance i4xn
G È where 4 is the remainder and ö the quotient resulting from dividing WòILG]I,
by
JIG . Then RM¯ i"!Y ó RM¯ WJIGäuI~IG£!Y .
`
Since the dual of a RM code is again a RM code (of appropriate order), we therefore
need the generators of RM code (of arbitrary order). We first establish that flats and pseudoflats (of suitable dimension and exponent) indeed generate the Reed-Muller code. We then
end the section with a proof of Theorem 7.1 and a few remarks.
We begin with few simple observations about flats. Note that an -flat is the intersection of /KI
hyperplanes in general position. Equivalently, it consists of all points
Ç that satisfy /lIê
linear equations over (i.e., one equation
for each hyperplane):
hyperplane (i.e., Ç satisfies
Íu+ ´Iïç¡
B
Û Z ÜfÎ ¬
; Î defines the Í
W;NÎ where ÜëÎ !6N
Û Z ÜëÎ Ç
C; Î ). General position means that the matrix ¢XÜ\Î ¦ has rank ^gI
. Note that
then the characteristic function (and by abuse of notation the incidence vector) of can be
written as
ü å
å
(7.7)
Gt
I ÜfÎ ¬ IZ;NÎ
åZ k ; G if /ÇZ!¥ä!Ç 8+K
otherwise
Û Z
ÎÛ Z
`
.
`
We now record a lemma here that will be used later in this section.
Lemma 7.5. For 0
vectors of -flats.
, the incidence vector of any -flat is a linear sum of the incidence
119
Ø
Proof. Let ¥n G and let
be an -flat. We want to show that it is generated by a linear
combination of flats.
be generated
Let
Z!ä! Z at ; . For each non-zero vector Übε
Z by ;CZ\!ä!Z; åZ!J
È
Æ
ÜfÎçZ!¥¤¤¥¤!NÜ Î Z in ? define:
Ø
ü Z
Îú
Û Z
Ç
Z
Î
Üf
¤
Í[
Z
IÊG such XÎ . Now for each +ö U IõG¡ , define an -flat Î
Clearly there are U generated by ;UZ\!ä!Z; å Z!ÇÎ at ; . Denote the incidence vector of a flat by G , then we
claim that
Ç
G0/
õ÷UaIQG
å Z\!òZ!¥¤¥¤¥¤!
Since the vectors ;UZ\!¥¤¤¥¤Z! ; proof in three sub cases:
yØ
V
ü p å Z
ÎÛ Z
G
¤
(7.8)
Z are all linearly independent, we can divide the
åZ
t+
: Then each flat
is of the form ;(n Î Û Z ?Î?X; Î , for some ?eZ!¥¤¥¤¥¤!N? åZg+|C
äÎ contributes
Z G to the right hand side of (7.8), and therefore, the right hand side is
IG³ G in C .
UaIQG\U Ç
÷
[ÞØ
k
Z
is of the form ; n Î Û Z Te HÎ 9Î for some TZ\!¥¤¥¤¤!NT Zò+wU : Then the flats
Z
that contribute have
@o Î Û Z TeâÎ 9Î , for @0
£
G
¥
!
¤
¥
¤
¤
<! UuI5G . Therefore, the right
G in C .
hand side of (7.8) is UaIG
+
Ç
KÞØ
÷
åZ
Z
is of the form
that contribute
;8n Î Û Z Î : Then the flats
? ÎX; Î"n Î Û Z eT HÎ Ð
Z
have @ Î Û Z T<ÎH9
Î , for @
<
G
!
¥
¤
¥
¤
¤
Q! P
U I´G . Therefore, the right hand side of (7.8)
G in C .
is UaIQG
Ç
+
y÷
÷
As mentioned previously, we give an explicit basis for RMc<G<!j . For the special case
of Ugt , our basis coincides with the min-weight basis given in [29].2 However, in general,
our basis differs from the min-weight basis provided in [29].
The following Proposition shows that the incidence vectors of flats form a basis for the
Reed-Muller code of orders that are multiples of UaIQG .
` [G\/òIK
b !`j
U I
Proposition 7.6. RMc
is generated by the incidence vectors of the -flats.
2
The equations of the hyperplanes are slightly different in our case; nonetheless, both of them define the
same basis generated by the min-weight codewords.
120
Proof. We first show that the incidence vectors of the -flats are in RMN UIG^oILW b!Y .
Recall that is the intersection of /ÂI
independent hyperplanes. Therefore using (7.7),
can be represented by a polynomial of degree at most ^I
U{IõG in ¬YZ\!ä!`¬ .
Therefore the incidence vectors of -flats are in RMcN UaIG^uI
b ! j .
We prove that RMN U IpG\/{I
\ !j is generated by -flats by induction on wI .
;
When 0I¥
, the code consists of constants, which is clearly generated by -flats i.e.,
the whole space.
;
, we show that any monomial of total degree
To prove for an arbitrary /lI
K
TKE UuIG^SI
can be written as a linear sum of the incidence vectors of -flats. Let
 ¥ ë¬C
. Group into
the monomial be ¬ Z ë¬ Â þ . Rewrite the monomials as ¬úZ"f¬ÁZ ¥¬À"
`
[
03 4
1
03 4
1
2
2
?eZ times
?©Â times
products of UuI5G (not necessarily distinct) variables as much as possible. Rewrite each
group using (7.5) with Fh U I|G . For any incomplete group of size T , use the same
equation by setting the last UgIGòI,T>ª variables to the constant 1. After expansion, the
monomial can be seen to be a sum of products of at most ^wI
linear terms raised to
the power of UgIG . We can add to it a polynomial of degree at most UgIG\/SIúIG
so as to represent the resulting polynomial as a sum of polynomials, each polynomial as
in (7.7). Each such non-zero polynomial is generated by a flat, P . By induction, the
polynomial we added is generated by >f nuG flats. Thus, by Lemma 7.5 our given monomial
is generated by -flats.
û
û
[
_
_
This leads to the following observation:
Observation 7.4. Consider an -flat generated by ;Z\!¥¥äZ! ; at ; . Denote the incidence
vector of this flat by . Then the right hand side of (7.2) may be identified as y< , where
and denote the vector corresponding to respective codewords and is the dot (scalar)
product.
×
×
×
To generate a Reed-Muller code of any arbitrary order, we need pseudoflats. Note that
the points in a -pseudoflat may alternatively be viewed as the space given by the union
of intersections of /0IaILG hyperplanes, where the union is parameterized by another
hyperplane that does not take one particular value. Concretely, it is the set of points Ç which
satisfy the following constraints over :
BÍ3+F uI~IQG¡
ü Û Z
ëÎ
Ü
ï`; Î/º and
¬ ü Ü å ¬
Û Z '
Ï
;å '¤
Ñ
Thus the values taken by the points of a -pseudoflat in its corresponding "Z! G> -pseudoflat
vector is given by the polynomial
å ' åZ
å
ÎÛ Z
Gt
I ü Û Z
ëÎ
Ü
;
¬ IZNÎW åZ äc
ü I; å ' Ü å ¬
Û Z '
(7.9)
121
Remark 7.1. Note the difference between (7.9) and the basis polynomial in [29] that (along
with the action of the affine general linear group) yields the min-weight codewords:
j
k
/¬ÁZ\!ä`! ¬ $
Ë Z\!ä!Ë
' åZ!ú
where òZ!¥ä!
' åZ
å
ÎÛ Z
+]U
`GIQ
¬C"Î I Ð ÎW ¥åZ å
Û Z
¬ ' I´Ë \!
.
The next lemma shows that the code generated by the incidence vectors of -flats is a
subcode of the code generated by the ½Z! G> -pseudoflats vectors.
gIVX¡ , generate a code
Claim 7.7. The ½ !ZG> -pseudoflats vectors, where %G and GK+p U
containing the incidence vectors of -flats.
Proof. Let Ø be the incidence vector of an -flat generated by ;Z!¥äZ! ; at ; . Since pseudoflat vector corresponding to an -pseudoflat (as well as a flat) assigns the same value to all
vector) by
points in the same IuG -flat, we can describe Ø (as well as any ½! -pseudoflat
È
giving its values on each of its U IyG -flats. In particular, Ø zÆG£!¥¤¥¤¥¤!¥G . Let be a pseud
oflat generated by ;UZ\!ä!Z; exponentiated along ;CZ at ;Bn ÐP;cZ , for each +]C , and let
be the corresponding >½ !£G - pseudoflat vector. By Definition 7.3, assigns a value Í to the
><
-flat generated by ;>!ä!; at ;Dn´ nu ; . Rewriting them in terms of the values on
È
its bIuG -flats yields that zÆN 8
U IøU% ! U8IøÁ
ngG!ä! U8I ún* !Y! U8IøY
+] .
;
!¥ !Y!Q*
U IG£! each taking values in . Then a solution
Let Ù denote U variables for y
to the following system of equations
I_G
G£
ü
GJ
implies that Ø
k
Ù
|
ý
Ù
/ÍjI
U Í`
Í` for every
;
a
IuG
E ä
EãUaIG
¥åZ
Cý , which suffices to establish the claim. Consider the identity
ü
sn´ åZ å G-zIG
Û
Ù
Ù
|
ý
Í`
which may be verified by expanding and applying Lemma 7.1. Setting Ù to IG\I U
establishes the claim.
¥åZå
The next Proposition complements Proposition 7.6. Together they say that by choosing
pseudoflats appropriately, Reed-Muller codes of any given order can be generated. This
gives an equivalent representation of Reed-Muller codes. An exact characterization then
follows from this alternate representation.
I|VX
Proposition 7.8. For every G|+ U{
¡ , the linear code generated by ½Z! G> -pseudoflat
U IQG^uI
ú8
n G<!Y .
vectors is equivalent to RMc a
`
122
Proof. For the forward direction, consider an -pseudoflat . Its corresponding >½ !£G pseudoflat vector is given by an equation similar to (7.9). Thus the codeword corresponding
to the evaluation vector of this flat can be represented by a polynomial of degree at most
UaIQG\/uIZ
jî
n G . This completes the forward direction.
Since monomials of degree at most UÐIgG\/-IF
are generated by the incidence vectors
of -flats, Claim 7.7 will establish the proposition for such monomials. Thus, to prove the
other direction of the proposition, we restrict our attention to monomials of degree at least
U3IÂG^IW¥n and show that these monomials are generated by > !ZG> -pseudoflats vectors.
Now consider any such monomial. Let the degree of the monomial be UäIyG^kI
ëná>
G ( GPE
GÁ=
E G ). Rewrite it as in Proposition 7.6. Since the degree of the monomial is U.IQG^gI
³>
n G , we will be left with an incomplete group of degree G . We make any incomplete
group complete by adding 1’s (as necessary) to the product. We then use Lemma 7.3 to
rewrite each (complete) group as a linear sum of G powered terms. After expansion,
the
powered
/
gI
U
.
Q
I
G
degree
monomial can be seen
to
be
a
sum
of
product
of
at
most
linear terms and a G powered linear terms. Each such polynomial is generated either by
an >½ ! G£ -pseudoflat vector or an -flat. Claim 7.7 completes the proof.
uG
X
£
ñ
The following is analogous to Observation 7.4.
Observation 7.5. Consider an -pseudoflat, generated by ;Z\!¥¥µZ! ; at ; exponentiated
along ;UZ . Let # be its corresponding ½ !ZG> -pseudoflat vector. Then the right hand side of
(7.3) may be interpreted as #5 .
X
Now we prove the exact characterization.
Proof of Theorem 7.1: The proof directly follows from Lemma 7.4, Proposition 7.6,
Proposition 7.8 and Observation 7.4 and Observation 7.5. Indeed by Observation 7.4, Observation 7.5 and (7.6) are essentially tests to determine whether the dot product of the
function with every vector in the dual space of RMc?\!Y evaluates to zero. ó
_
Remark 7.2. One can obtain an alternate characterization from Remark 7.1 which we state
here without proof.
;
U
). Let GîU F F . Let Ø x with
U IGäe}nF4 (note
Let z.
k
4pE÷ .IV>
aI
4QI V
· 2·U G . Define the polynomial
¬" Ä x
/
.¬ I if is non-empty; and /¬9õG
N
Ì
otherwise. Then a function belong to (
if and only if for every ;UZ\!ä!Z; Z6! ;a+FD , we
'
R
_
-Ø
Ø
Ù
û
have
ü
×
Ù
|
05 /
ý
WÜN
Z ü
Ø
888 ×
×
T
p
Ù
| ýT
n
>;
ü' Z
ÎÛ Z
X k
ÜfÎ"r
; Î
;
¤
Moreover, this characterization can also be extended to certain degrees for more general
fields, i.e., C (see the next remark).
þ
Remark 7.3. The exact characterization of low degree polynomials as claimed in [42] may
be proved using duality. Note that their proof works as long as the dual code has a minweight basis (see [29]). Suppose that the polynomial has degree TlE IQ< 6,U] , then
I|G
123
ItGÑ]IF ItG£!Y
pG
T
the dual of RM¯
TD!Y is RM¯ `Wò
and therefore has a min-weight basis.
. Therefore, assuming the minimum
Note that then the dual code has min-weight WT*n
weight codewords constitute a basis (that is, the span of all codewords with the minimum
Hamming weight is the same as the code), any T8n´G evaluations of the original polynomial
on a line are dependent and vice-versa.
7.4 A Tester for Low Degree Polynomials over In this section we present and analyze a one-sided tester for (
. The analysis of the algorithm roughly follows the proof structure given in [93, 1]. We emphasize that the generalization from [1] to our case is not straightforward. As in [93, 1] we define a self-corrected
version of the (possibly corrupted) function being tested. The straightforward adoption of
the analysis given in [93] gives reasonable bounds. However, a better bound is achieved
by following the techniques developed in [1]. In there, they show that the self-corrector
function can be interpolated with overwhelming probability. However their approach appears to use special properties of ú and it is not clear how to generalize their technique for
arbitrary prime fields. We give a clean formulation which relies on the flats being represented through polynomials as described earlier. In particular, Claims 7.14, 7.15 and their
generalizations appear to require our new polynomial based view.
7.4.1 Tester in In this subsection we describe the algorithm when underlying field is B .
Algorithm Test-
in C
k÷
;
aIFV
Et4| .
IF4
a
U IQGäe}nF4 ,
U
ò
¥U IG . Denote G8
0. Let
.
1. Uniformly and independently at random select ;Z\!äZ! ; Z 6! ;-+] .
'
;
2. If H < ;cZ\!¥¥µ
!Z; Z\!¤\òÏ , then reject, else accept.
_
Ì
R
; '
Theorem 7.2. The algorithm
Z Test-
Z in U is a one-sided tester ;for with a success
probability at least min
Ü< U"' <\ ! 76 T Ø for some constant ÜJ .
'
p
Z
Corollary 7.3. Repeating the algorithm Test--
in C for y T
n,rU ' times, the probp
ability of error can be reduced to less than < .
G6 V
We will provide a general proof framework. However, for the ease of exposition we
prove the main technical lemmas for the case of j . The proof idea in the general case is
similar and the details are omitted. Therefore we will essentially prove the following.
Theorem 7.4. The algorithm
Test-
in is a one-sided tester for with success prob Z
;
ability at least min WÜeW
e\! 76 Z Ø for some constant ÜJ .
Ó p
>'
]
124
7.4.2 Analysis of Algorithm Test-
K
In this subsection we analyze the algorithm described in Section 7.4.1. From Claim 7.1 it
is clear that if +[
, then the tester accepts. Thus, the bulk of the proof is to show that if
is -far from
, then the tester rejects with significant probability. Our proof structure
follows that of the analysis of the test in [1]. In particular, let be the function to be tested
for membership in
. Assume we perform Test H for an appropriate as required by the
algorithm described in Section 7.4.1. For such anÌ , we define > U as follows:
! denote U B N PrB 8 8 8 B T ĵ? ;³IºH ?;Iº;cZ\!Z; Y! ; ZZ! ;cZN- j¡ .
For ; +~± !fQ+wC
Define X < ;³L such that Ï
C
<U B N p ãU B » withÌ ties broken arbitrarily. With this
;
¡hS
½ ¢ ¦ , e can be written as:
meaning of plurality, for all + U
Î
K
Î
,tl+] !
Í8F .IVX
Î Î
e ? ;µã
plurality T
I H
B 888 B p
X ?;
8
Further we define
Î Ä Oá G
H
B 888 B T p A
Ì
û
Í
£!
Î I cZ\! £ !ä! '
<; 8;
Ì
Î cZ\!¥¥ä! '
Z; <;
Ì
Îs$Á
Î
Í
Z; Z; Z6! ;ò
Ï
;
)
÷
'
ZZ! ;cZN g ¤
¡
(7.10)
(7.11)
The next lemma follows from a Markov-type8 argument.
8
Î! Î be defined as above. Then, Ýci <Îi9EtV Î .
Î }I cZ\! £ ! ¥ä! ' Z\! cZ ½¡ G6<V ,
, Pr T ĵ kLµ I
Proof. If for some Â
8
8
8
8 we only need
then µ . Thus,
to worry about the set of elements such that
Î
Pr T ĵ g
ù
I
]
I
c
\
Z
!
£
!
¥ä! ' Z\! cZ Ñ¡oE G6eV . If the fraction of such
888
elements is more
than V Î then that contradicts the condition that
8
Î Pr 8 8 8 T Î cÎ Z\!ä! ' Z\! ; ¡ ;
Pr Ø 8 8 8 T cZµI ;! £ ! ä! ' Z! ¡
Î *ãI ;cZ\! £ !¥ä! ' Z\! cZ ½¡i¤
L äI
Pr 8 8 8 T ¸8 s
! eÎ 9ELV Î .
Therefore, we obtain Ý iB
Note that Pr T XÎ Ð
|
³I Î yI cZ! £!ä! ' Z! cZ Ñ¡ Z . We now show
8
8
8
K
Lemma 7.9. For a fixed e$ hU , let X
B
<; ]
<;
; +]" <;
B p
B
?;
"!
)
?;
B p
H
?; ;
<; Y¥H
; Z; Ì
Z; ; <; #;
Z; f ú
;
Z; f
Ì
B
B p
B B
B p
B B
U
A
B p
H
Z; A
?;
Ì
H
?; Ì
<;
Ï
Z
Z; ?;
8H
6
; ò
Ï
Z; <;
6
; ò
Ï
; Z; Z; f
Ì
W
<;
?; 8H <; î; Z; Z; Z; f
B p
that this probability is actually much higher.
The next lemma gives a weak bound in that
Ì
B
direction following the analysis in [93]. For the sake of completeness, we present the proof.
8
Lemma 7.10. À;L+q
Ð !U Z .
G IFV ' Î
, IJ
Î
Î uI c £
cÑ
Ù | Ù X <;.Mµ< ;I=H < ; =; Z\! ; !äZ! ; Z\!Z; Zf ¡
'
B 888 B T p ý
Ì
125
Ñ G dimensional vectors over . Now note that
Z
'
Î I ;cZ ún <;X
Dnîc; ZN½ ¡
| Z µ Z<;*ã
B 888 B T p
| T p <; ZÑ ý >ý =
888
¹
¹
Z ntG Î µ Z¥?;*ã
I ;cZ
å Ø | B B B 888 B T p
| T p <; ý >ý =
888
¹
¹
Ò o
! × !sÒ to denote ³
nS
Proof. We will use ×D!Û
Î
I:X <;
Ik¨:a
9 J^C<¨
ªÕ
ü
Ó
)
Ù
×
Ù
Ik¨:a
9 J^C<¨
n
ü
ªÕ
ü
ýÙ
ý
Û
Û
Ú
ü
Ó
)
>× j
ý Ù
Ù
Ù
' Z
ý
Ú
Dnî
; ½¡
×ë<;X
Ik¨:a
9 J^C<¨
f
>×
Û
Û
×ë
f
>×
ªÕ
T Ù | ýÙ 888 B p
Ù | ýT
p ¹
¹
ü
Ó
)
B
'
ntG Î µ
Z
<; ý 8 8 8 ý =
#
Û
>×
Zú
Z
Ñ
b
<;X
D8
n ; ¡
ü
×
(7.12)
Û
È
È
;
; È
Let ÷r%Æ?;UZ\!ä!Z; Z and ÷ rÆ?; Z !ä!Z; Z . Also we will denote Æ ! ä!
by
'
8
'
ñ . Now note that
ÎäE
GÐI
Îc
;
k
¡
'
Î µ ; Z ok ; ¡
H <; Z\!¥¥ä!Z;
B 888 B T p A
I J T Ì
N
× Z
>³n
B 888 B p A
T
Ù | ý
p
¹
INJ T ĵ> ³
; n8; Zfún
B 888 B p A
IJ
ü
IJ
IJ
¸?; jn
B 888 B T p B
¸?; jn
B 888 B T p B
Z6! ; ©÷
×
c
Ú
¹
ü
| ýT p
Ù
<; Z½ ý 8 8 8 ý =
¹
#
Û
| ýT p
¹
Î µ n yk
;
;
©÷
×
¡
Î µ c <; ý ý>=
¹ ZÑ 8 8 8 ntG Î µ Pn o³
;
I ; Zún
× ©
÷yk
Z < ;*8
×
¡
Û
;
Ú
ü
<; ý 8 8 8 ý>=
| ýT p
¹
¹
Ù
Z
Ú
ü
Ù
×
>×
<;
Zú
×
©÷
¡
Û
Ú
8
Therefore for any given ×[L
Ï
ñ we have the following:
IJ#<
? ?
Z
ĵ?
; n
× ©
÷yk
and for any given
I#J ?< ?
~Lñ ,
Ò
Ô
ü
| ýT p
Ù
@
I* ÒCZjnQG
Ô
×
©÷
½
u© ÷ ú
¡ pGI
Ò
Î
Ú
| ýT p
¹
¹
tG Î µ<;}nZr5
÷ n
I*> × Zjn
ü
Ù
<;
Û
Ï
¸µ< ;}nÒu© ÷ k
Î µ }nZ 5n
@
Û
Ú
×
8
Òu©
÷
½ |G
¡ú
I
Τ
126
Combining the above two and using the union bound we get,
IJ#<
? ?
Î
>× ZúntG ? }
; nש÷y DE
ü
BAC
| ýT p
Ù
¹
@
¹
ü
Û
Ú
ü
| ýT p
¹
¹
Ù
@
Û
Ô
Ú
ü
Ù
Ô
| ýT p
|GIVU
@
| ýT p
Ù
Î
@
Û
Ô
ÒCZjnQ8 G ? ;}n
' Z
Ú
IQG |GIV!U
Ú
<;
×
Òu©÷
©÷
Ñ
g© ÷ 8 ¡
Ò
Û
Ô
Î tG Î µ }n} Ln
I*8 × ZjnQG ÒCZún
' Z Î
(7.13)
The lemma now follows from the observation that the probability that the same object
is drawn from a set in two independent trials lower bounds the probability of drawing the
most likely object in one trial: Suppose the objects are ordered so that U is the probability
U 2¥ . Then the probability of drawing the same object
of drawing object , and UúZ =B
U ZU ãU Z .
twice is U
"Î
Í
s
Î Î E Î Á ÎäE Á
However, when the degree being tested is larger than the field size, we can improve the
above lemma considerably. The following lemma strengthens Lemma 7.10 when _ÐãUPI´G
or equivalently |G . We now focus on the ú case. The proof appears in Section 7.4.3.
Â
Î uI cZ\! £!ä! ' Z\! cZ Ñ¡
888 T
XÎ .Mµ I
Lemma 7.11. L
,
GÐt
I sntGc8 Î .
Lemma 7.11 will be instrumental in proving the next lemma, which shows that sufficiently small Î implies XÎ is the self-corrected version of the function (the proof appears
8
in Section 7.4.4).
Lemma 7.12. Over Á , if P
Î ' Z/Z T , then the function eÎ belongs to (assuming
.|G ).
8
8
By combining Lemma 7.9 and Lemma 7.12 we obtain that if is PG6Ci ¥' N -far from
Ð
then Î is at least s`G6 Ñ £¥' . We next consider the case in which Î is small. By Lemma
7.9, in this case, the distance Ýy|
Ý W" ! is small. TheZ next lemma shows that in this case
8
À;
/U
IJ
+q B
Ù
B p
| Ù <;
s
<;
<; =;
=H
Z; ; Z; f
Ì
R
p
U U
UU
N
U
'
Ý . This follows from the fact
the test rejects with probability that is close to
Z that in
points
this case, the probability over the selection of ;Z\!ä!Z; Z\!6; , that among the
'
(where
?X
; Dn
N
Z
8 Z-+{" ), the functions and differ in precisely one point,
Ý . Observe that if they do, then the test rejects.
is close to
Î ÜfÎ Î ;£'
ÜZ !¥¤¥¤¥¤! Ü '
;
ÎòE
Z
£'
Lemma 7.13. Suppose E
T . Let Ý denote the relative distance between
Z
' Z
p . Then, when ;UZ\!ä!Z; Z!6; are chosen randomly, the probability
and and
Z
+S
X
; Dnñ (where WÜZ\!¥¤¤¥¤!NÜ Zf
that for exactly one point among
the
points
),
å µ^
/ is at least Z S © Ý .
Ç
ò Ï
Ç
£'
Z
Ç
S
' Î ÜfÎ Î ;
'
'
127
8
Î
' Z
Ý< . The proof of Lemma 7.13 is deferred to SecObserve that
is at least PW
tion 7.4.5.
Proof of Theorem 7.4: Clearly if belongs to (
, then by Claim 7.1 the tester accepts 8
8
with
probability 1.
Therefore let Ýci"!
. Let T ÝUiB
! , where8 G is as in algorithm Test- . If
Z
R Z
T then by Lemma 7.12 +]Ð
and, by Lemma 7.13, is at least P
Z TU ,
Ñ.
'
p
PW
which by the definition of is at least
;
for some fixed constant
.
ÜJ
Z < . Hence
>'
Î
Ît§ ÍÑ Ü<
£'
.
'
Z <b ! Z
T 2 ,
'
Z p
ó
Remark 7.4. Theorem 7.2 follows from a similar argument.
7.4.3 Proof of Lemma 7.11
Î
Observe that the goal of Lemma 7.11 is to show that at any fixed point ; , if £ is interpolated
from a random hyperplane, then w.h.p. the interpolated value is the most popular vote. To
ensure this we show that if e is interpolated on two independently random hyperplanes,
then the probability that these interpolated values are the same, that is the collision probability, is large. To estimate this collision probability, we show that the difference of the
interpolation values can be rewritten as a sum of H on small number of random hyperplanes. Thus if the test passes often (that is, H evaluates
to zero w.h.p.), then this sum (by
Ì
a simple union bound) evaluates to zero often,Ì which proves the high collision probability.
The improvement will arise because we will express differences involving H as a
telescoping series to essentially reduce the number of events in the union bound.Ì To do this
we will need the following claims. We note that a similar claim for Uw V was proven by
expanding the terms on both sides in [1]. However, the latter does not give much insight
into the general case i.e., for . We provide proofs that have a much cleaner structure
based on the underlying geometric structure, i.e., flats or pseudoflats.
Î
Î
Î
Î
Ê
Á
y
Claim 7.14. For every ä+w¢eVC!Y!bCn XG ¦ , for every ; i±;CZfb!
; Z9+0 , let let
'
¶
Ì
<;"! ±H
def
¶
Ì
?; !
"! !
ý
sµ IF
¶
Ì
<;"! "!
Ì
The the following holds:
ý <; Z;£!ä!Z; åZ !
k
Ù
|
eª¶
ü
ý
Ì
!Z;
<}
; nF?*!
!!6;
Z
!Z;£!ä!Z; å!Z;
Z!¥ä!
' ;
Z\!ä!Z; Z\!¤\\¤
µI¶
Ì
k¤
?;n? !PEg
;
Proof. Assume ;
are independent. If not then both sides are equal to and hence the
equality is trivially satisfied. To see why this claim is true for the left hand side, recall the
definition of H and note that the sets of points in the flat generated by ;"!Z; !¥¥ä!Z; å\!*!
; Z!¥ä!Z; Z Ì at ; and the flat generated by ;Z! ;>!¥¥äZ! ; å\! !Z; Z\!ä!Z; Z at ; are the
'
same. A similar argument works for the expression on the right hand side of the equality.
û
Z
c
'
Z
128
u
;
We claim that it is enough to prove the result for 2G and ò÷ñ . A linear transform
(or renaming the co-ordinate system appropriately) reduces the case of {%G and ñ
to the case of q G and ´ ñ . We now show how to reduce the case of z G to
!NÜ å\!NÜ Z\!ä !NÜ Z and note that one can write
the ´öG case. Fix some values ä
n
P; P; n \h; n5b å; å n
n Z%; Z n; as P; n Q
n ;N , where ;fY å Z
Z à ; n; . Thus,
Ù
888
888
;
Ü¥!
Z
ÜZ y,Ü £k Ü Z Zµ,Ü Q,Ü Z Z ,Ü ' ' µ ' ÜZ y,Ü
Z½ Ñ ' Ü
åZ
'
?;! sk µ
ÜZ ;}nFÜ ~nñ;
Ø T
|
| Ø
8 8 8 e p 8 8 8 p
;0Ï
Ý
ü
ü
¶
P
Ì
×
×
×
Ù
×
ý
Ù
×
×
\¤
ý
Z
One can rewrite the other ¶ terms similarly. Note that for a fixed vector WÜ¥!Y!fÜ å!
Ü \!ä
!NÜ ZN ,åthe value ofÌ ;ë is the same. Finally note that the equality in the general case
is satisfied if U"
similar equalities hold in the pG case.
Now consider the space F generated by ;! and at 0. Note that ¶ ?;! (with
;
.
Ð5ñ ) is just -fG , where G is the incidence vector of the flat given by the equation
Ì
å over . Similarly ¶ <;"! 5 Therefore G is equivalent to the polynomial I
¥
å
where is given by the polynomial L
over . We use the following
polynomial
Ì
identity (in )
Z
' ' Z
;
`G Z
`G8I
Z I åZ s
k 9ÑG
Z
Z ¡IL GIQW? nî; ¥åZ ¡ög
(7.14)
åZ is the incidence vector of the flat
Now observe that the polynomial `G*IvW? ÷n ;
å
Z
and . Similarly, the polynomial `G9,
generated by ;Iw?
I
? n åZ is the incidence
åZ
¥å
î
eW GItW?*~n ;
ü
Ù
|
ý
û
¥å
*
#;
and . Therefore, interpreting the above equation
vector of the flat generated by ;yIF?
in terms of incidence vectors of flats, Observation 7.4 completes the proof assuming (7.14)
is true.
We complete the proof by proving (7.14). Consider the sum: Ù | ý W*? Qº
n ; ¥å . Ex
¥å å å å
å å .
;} Ù | ý ?
panding the terms and rearranging the sums we get C
¥å I ; ¥å . Similarly, Ù W? n ; å By Lemma 7.1 the sum evaluates to I
|ý
å
¥
å
which proves (7.14).
I
I
Z
Z ã; Z Z Z Z ^
Û
ý
Z
û
û
Z
Z½
Z
û
We will also need the following claim.
Í8 cG£! aIFV¦ , for every ä+{¢eVC!Y! }nteG ¦ and for every
Z Z!Y! ' Z9+0D , denote
Îæ
Î £!ä! åZ! ! Z!ä! ' Z\! ;\\¤
¶ ! s Then there exists Ü Î such that
Îæ ! sµ IF Îæ ! ktÜ Î Îæ }nF? ! äIF¶ Îæ }nF? ! sE m(¤
cZN\!
Claim 7.15. For every +{¢
;i=;
;
ä!<U
!!¤! ;£!äZ! ; å !Z; ë
¶
Ì
?;
def
?;
; Z; <;"!Z;
±H
; ë
Z; ¤
Ì
Ì
¶
Ì
ü
?;
ë
û
Ù
|
ý
j^¶
Ì
?;
*
Ì
<;
129
Îæ
Î Z
G and
Proof. As in the proof of
Claim 7.14, we only need to prove the claim for
a ñ . Observe that ¶ ?;"! S #
, where #
denotes the iVC!Í -pseudoflat vector
by ;"! at ; exponentiated along ; . Note that the polynomial
of the pseudoflat generated
Ì å
IG . Similarly
we can identify the other terms with polynomials
defining #
is just ; v
over . To complete the proof, we need to prove the following identity (which is similar
to the one in (7.14)):
;
Î åZ I åZ k tÜfÎ
c
Z ¡DIQ }nF? Î G It *I? ¥åZ ¡ökg ¤
(7.15)
åZ
where Ü yùV . Before we prove the identity, note that IG
G in C . This is
. Therefore äOIG Î ¥ ¥å ååZ Z holds in C .
, OIG gI,0
because for GgEv E
Substitution yields the desired result. Also note that
n,? s 2I (expand and
; v
Ù
Î
ëÎ
Î
ü
|
ý
å
e
?;}n?*P GIQ<;I*? P
<;
k
U
apply Lemma 7.1). Now consider the sum
|
ý
s Z
?;}n*? P Î <;I?* ¥ å
Ù
À"
Ù
û
/
ü
?;
| ý <;
*
UaIQG
:;
HÎ G
Z Îç
û
Í
HG
¥å å å
?
ý å Z
þ >ÿ þ ÿ
ý
?
IG >Í ÿ U. IG ÿ ; ¥åZ Îçå å
þ þ
|
ý ý å Z
U.IG
Í
IG ; Î åZ ¡
I:; åZ Î nLIG
a
U
I
G
I
>
ÿ
£
ÿ
ÛCýþ þ 03 4
IG
ü
ü
|
Ù
ý
¤Ï
6Ï
Ï
Ï Î
;
$
$
$
$
$
û
û
ü
ü
6Ï
¤Ï
Ï
Ï Î
Î
î
Î
ZV
¥å
Î
û
1
Î
n;
ZV
¥å
Î
ÛZ
2
Î
uI Z I
Similarly one has Ù
simplifying one gets (7.15).
$
ý
ü
IG¥ ; n ;
¡
Î
å
G ;
| ý <;.n5? ?; 5?
$
Ù
$
$
$
Î
(7.16)
¡ . Substituting and
û
Finally, we will also need the following claim.
c!
£
Z
æ *! µI¶ æ ! k
tG
Claim 7.16. For every Í3+w¢ £G Y!<U.Ic
V ¦ , for every Y+w¢eVC!Y!6 n e¦ and for every
; ±; b! !!6; !Z; !ä!; å\!; Z\!ä!Z; ZÐ+] , there exists ÜbÎä+] such that
Ñ
Î ¶
â
Î Z;
Ì
Ì
ç¶ Îæ }n? *! yI? sµ I¶ Îæ xn? ! QI? Nn
æ
¶ n? ! Il? µI¶ }n? ! *Il? nòÜf ç¶ Îæ }n? *! µIF¶ æ PnF? ! P mm
ü
Z;
'
Ù
?;
j
|
û
ý
Ì
Î Ì
X
Î j
Z;
*
j;
ή j;
?;
*
*
j;
Ì
<;
Ì Î
j;
â
;
<;
Ì
Proof. As in the proof of Claim 7.15, the proof
boils down to Ì proving a polynomial identity
over C . In particular, we need to prove the following identity over D :
Î
`GI
Z cI `G I åZ ³ ÷
å
Î
F
v
Î
I
;
Î
Z
Á
Z
I ; Î G Ig ¥å <n
\`GI ¥å I[ Î D
; â
Î
Z I ¥åZ \ ¤
¥å
130
We also use that ÜfÎúLV Î as before.
K
; | ý vwn ?j
Ù
|I
Î
Î
and Claim 7.15 to expand the last term. Note that
û
ÇÎÑ
Û Z ÇÎ
ÛZ
We need one more simple fact before we can prove Lemma 7.11. For a probabil;
Ç G
MaxÎ Ù ¢ ¦Q MaxÎ Ù ÇXÎi¦j% Î ÇÎW[ Î
3
ity vector ÷+ö !¥G¡ , G H
Çν¦ Û Z Ç
Ç
MaxÎ Ù G G
G GJI
¢
GÇ G.
GG GG
8
Proof of Lemma 7.11: We first prove the lemma for Î
Î
ý <; . We fix ;´+x and let Y Ä ý
INJ T
| ý ?;3µ<;µî
I H ?y
; I8;cZZ! ;£!Y! ; Z\!Z;cZfÑ¡ . Recall that we want to lower
'
B 888 B p s
bound Y by GsIp npGc ý . In that direction, we bound a slightly different but related
probability. Define
ý I ;cZZ! ;£!ä!Z; Z\!c; Zf³±H ý <;*I Z\! !ä! Z\! ZN½¡
K IJ | H ?;*ã
'
'
B 888 B T p 888 T p s
È
Denote ÷ Æ?;
Z; Z and similarly ú . Then by the definitions of K and Y we have,
'
K
. Note that we have
Y[
ý
ý
;
K IJ | H <;Iá;cZZ! ;£!äZ! ; ZZ! ;cZf I{H ?;ÁI Z\! !¥ä! Z! ZNk
'
' ¡Ñ¤
B 888 B T p 888 T p s
We will now use a hybrid argument. Now, for any choice of ;Z\!ä!Z; Z and Z\!¥µ
!
'
Z we have:
' ý
ý
; 8
I ;cZ\!£; !ä!Z; ' ZZ! ;cZfäIãH ?;*I Z\! !¥¥ä! ' Z\! Zf
H ?*
ý ; ãI ;cZZ! ;£!Y!; Z\!Z;cZfäI8H ý <;*ãI ;cZ\!£; !¥ä!Z; ! Z\!Z;cZf
±H ?*
ý I ;cZ\!£; !ä'!Z; ! ZZ! ;cZNä8I H ý <;*8I ;cZ\!Z;£!' ¥ä'!Z; åZ! ! ZZ! ;cZN
nîH ?;*8
ý I ;cZ\!¥¥ä!Z; åZ' ! ' ! Z\!Z;cZfäI8H ý ?;*8I ;cZ\!äZ! ; 'å ! 'åZ\! ' ! Z\!Z;cZf
nîH ?;*8
' ' ' '
' ' '
..
.
ý
ý
nîH ?;*8
I ;cZ\! ! !ä! ' Z\!Z;cZfäI8H <;*I Z\! !ä! ' Z\!Z;cZf
ý I ;cZ\! !ä! Z\! ZN
ý
I H <;*8
nîH ?;*I Zb! ! !Y! ' ZZ! ;cZNä8
ý I ;cZ\! ! !ä! Z\! ZNäI8H ý <;*I Z\! !ä! ' Z\! ZN
nîH ?;*8
'
'
ý
ý
Consider any pair H <;*8
I ;cZ\!Z;£!¥µ
!Z; ! Z!Y! ' ZZ! ;cZNä8
I ;cZ\!£; !¥ä!Z; åZ\! !
I H <;*ã
¥ Y! ' Z!Z;cZf that appears in the first ý “rows” in the sum above. Note that H ý ?;{I
;cZ\Z! ;£!¥ä!Z; ! Z\!ä! Z\!Z;cZf and H <;oIî;cZ\!Z;£!¥¥ä!Z; åZ\! !ä! Z\!Z;cZf differ only
'
'
in a single parameter. We apply Claim 7.14 and obtain:
ý
ý
ýH ?H;YøI ?;c-; ZI n ;c; Z!ZZ! ;£;£!!äY!Z!; ; å! Z! Z\!!¥¥Yä! ! ' ZZ\Z! !;cc; ZNZNDn I H H ý <;Y<;(I I ;cZ;cI ZZ! ; ;£!Z!;£¥!ä!Z;ä!Zå; Z\! åZb! !!¥ä¥! µ ' ! Z\!Z ;cZbZf! k;cZf I:H ý ?;BI:;cZfn !Z;£!¥¥ä!Z; ! Z\!ä! ' ' Z\!Z;cZf I:H ý <B; I:; I !Z;£!ä!Z; ! Z\!Y! ' ' ZZ! ;cZN .
¢
Ù
Ù
Ì
û
/U
Ì
Ù
Ù
UZ\!ä!
Ì
Ì
Ù
Ù
Ì
Ì
Ì
Ì
Ì
Ì
Ì
ë
Ì
Ì
Ì
Ì
Ì
Ì
Ì
Ì
Ì
Ì
U
Ì
Ì
Ì
Ì
Ì
Ì
Ì
Ì
Ì
Z + are chosen uniformly at
Recall that ; is fixed and ;>!äZ! ; Z! !ä! l
'
'
random, so all the parameters on the right hand side of the equation are independent and
131
Hý
cý Z
cZ
'
! '
' ý cZf
!
uniformly distributed. Similarly one can expand the pairs <;ÐI ; \! ! Y! Z!Z; NUI
and H <;BI:; ! ! ä! Z\! Ì ZNbI:H ?"
; I Z! Y! Z! ZN
H <;BI Z\! Y! ZZ! ;
8
into
four H with all parameters being
independent and uniformlyÌ distributed 3 . Finally noÌ
Ì
ZZ! ; N and H <;BI Zb! !¥ä!
ZZ! ;
tice that theÌ parameters in both H <;BI Z\8 ! ! !¥ä!
'
are independent and uniformly Ì distributed. Further recall that by
the definition of ,
Ì
;
for independent and uniformly distributed G s.
IJ T H ?G<Z\!¥¥ä!ZG Zfx Ï
§
¡
E
888 p
8
Thus,
by the Ìunion bound, we have:
ý
' cZf
ý!
ý
'
ý
ý
cZ
!
'
cZ
ý
cZ
ý
Hý
ý
Î
ý¤
;
8 ! ; ZN"I H Z\!¥¥ä! ZNò Ï ; ú÷
Ù | Ù T
?; \!ä
E /cnG (7.17)
T
B 888 B p 888 p s
Ì
Ì
Therefore YS K
^UPn ; . A similar argument proves the lemma for CZ¥?; . The
8 argument. Thus, we use
only catch is that H `¤ is not symmetric– in particular in its first
another identity as given in Claim 7.16 to resolve the issue and get four extra terms than in
IJ
'
pGIt tG ý
ý
'
Ì
the case of , which results in the claimed bound of
/
¡
UPt
n G\U
Î
.
8
ó
§+]
Remark 7.5. Analogously, in the case we have: for every ;
| Ù XÎ<;
, INJ
B B 888 B T p ý
Î 8
<;*I Z! ;£Y! ; Z\!Z;cZfú n~µ<; ½j|GIV NU
`Pnº
q U
Î.
Lµ<;µI
G I~VN U L `
n
The proof isÌ similar to that of Lemma 7.11 where it can be shown K Î8vK
qU IQG únQG Î , for each Î defined for XÎ<
; .
ã;cZ
ãH
!
'
a
aIQG
¡
aIG út
n G
Ø
8
7.4.4 Proof of Lemma 7.12
Z
Ù
§I G
cZ\
'
From Theorem 7.1, it suffices to prove that if Îä Z
T then H P
<; !¥¥äZ! ; Z!
;
' p
Z\!6{
for every
;
!
¥
ä
Z
!
;
; +÷ . Fix the choice of ;UZ!äZ! ; Z6
! ; . Define
§
È
Æ?; !ä!Z; Z . We will express H P Î
Q8!¤\ as the sum of Î with random arguments. We
EL"n
, and
EL"n G .
uniformly select i"n G random
È variables Î over for Ì E
Define úäγHÆ Î !¥ µ
! ή Z . We also select uniformly i*n5G random variables G over
8
. We
B for E 8EL
Z use Î and G¥Î ’s to set up the random arguments. Now
; by Lemma
V ¦ ), with
7.11, for every ×_+
(i.e. think of × as an ordered i nq -tuple over !¥£!fc
probability at least
/U
Î over the choice of ή and G¥Î ,
;
cZ
cZ
'
.
'
Ðn´G
'
÷ ;
H
æ»Z
Gs,Í
Î
R
æ
æ
GP,Í3 .G
'
÷
GsE . .
Î
'
y G
G
GQ
I PQ
n GU
X Á ÷§n ;kLµ ÷§n ; ¥ø
I H Á ÷§n ;<I Áú ZI G<Z\! Áú³n G!ä! ú ' Zn G ' Z\! Á ú8Zn G<Z \!
(7.18)
Z
O ' Û Z Z ÷yO , holds.
where for vectors OK! ÷v+] ' , ÷qrM
Z
8 the union bound:
Let # Z be the event that (7.18) holds for all a+] ' . By
Z
/c}nQGU ¤
Pr # Z ¡j|GI
(7.19)
È
Assume that # Z holds. We now need the following claims. Let lÈ Æ DZ!¥ä! Z be a
'
ntG dimensional vector over Á , and denote õÆ !¥ä! ' Z .
¢
Î8×
Ð
I
>×
Ð
Î
]
8× Ð
I
Ì
×
o×
8
Î
Î
×
ò
¸ò½
o×
Î
Î
'
Ò
ò
i}
3
÷
o×
Since LNO M h n is symmetric in all but its last argument.
Ò
Ò
sÒ
Ò
sÒ
`
132
. '
Claim 7.17. If (7.18) holds for all × +g
`
Z
H P
ý ÷ ! k Æ
ýÛ
Q86;
| T
Ù
Ô
ü
j
Ì
s `
I:H ý V;cZµI
| T
s
Z
'
V 3Iã<G Z n
Ú
n
ý <;cZ n '
I:H
ü
ü
Û
i
Ù
Ô
^
ü
Proof.
H P
ý 9÷ ! Æ
<
6;
ü
ü
Ù
¹
I
Ò
j
8×
'
^»Z!Y!ëV ; ZäI
ñ
N
ún
Û
ü
| T
¹ sp
AC AC
n
'
×
Ô
½
ü
' Z
<
Û s
Z n
' j
o×
Ù
Ô
| T
s
Ò
}© ÷Ln~pV 3; IZ×}Ãú8Zµã
I G<Zjn
Û
Ù
Ù
ü
ACRAC
ü
AC
| T
¹ sp
Ù
(7.20)
s
| T
¹ sp
Ù
îG ' Z\!
' Z
Û
<
<GÑ
Ò
ü
ü
ü
Ò 8×
Ò
ü
8×
Ú
Ô
ü
Ò >×}
ü
| T
s
Ò
ED
' Z <
à úä
Dn
ü
×
AC
Ù
Û
ü
Ò >×
8×
j
ü
I
' Z <
?G¥
Ñ b
ç ' Z !ZG<Zjn
ü
8j
Ô
Û
ü
Ò
Z
Z
'
'
sµ }Ãú Z nîGeZ n Û <
à úµ
n Û e
<G¥
i bb
' Z
' Z
I
r5
÷ n³; n Û <
<GD
n Û
ý Û | sT ¹ | T p
>×
' Z
¡
ü
µi V
T
ñ ü
n
<
?G¥
Ñ b
Ò
Z ' Z n
Ò ^
Z !
e
'
ü
o×
>×
Ú
AC
ÙQP
*
ü
n
Û
Ì
Ù
; n
ç ' Z !6³
' Z
>×}
×
<
Ò
ü
ý ©5
÷ n;
ý
e^I:H ©÷Ln 3
;
IZ}Ãú9ZäI8G<Z\! Ãú³äî
n G!ä! Ãú
| Tp
s
}Ã ú9Z îG<Z nsµ © ÷Ln ;Ñ
Z
' Z
'
µ r÷5n
; n Û e
úµ
Dn Û <
?G¥
Ñ
Ù | T
¹ sp
Û
j
ç¸Z\!ä! ZÑ Zjn
ü
Ì
' Z n Û ä
! ;
Òe
' Z
Ò
»Z\!
' Z
ü
Z
'
ý
îH Z½»Z n Û <
n
, then
<
?G¥
Ñ
Û
ü
j
ZѸZún
Ì
p;
Òe
Z
Ò
µWV
× ©
÷LnFpV 3
; IZ×}Ãú9Zµã
I G<Zjn
à îG
µ8 × ú8Zjn <ú
Z n
ü
' Z
Û
Ãúä
Dn
Òe
>×}
ü
' Z
Û
Ãúµ
i
<
Ò >
×}
ü
' Z
Û
<
<G¥
iDESDE
Ò
<
DE
Ãúä
Dn
Ò 8
×
ü
' Z
Û
<
?G¥
iQ DE
Ò
133
ý ?;cZYn ' Z
`
ýÛ
I:H
ü
Ô
Ú
ü
| T
`s
Ù
Ì
<
µ! '
ç¸Zb!¥¥ Z; Zjn
Ò
Z
'
ý
I:H V;cZµI ZѸZ
Û | T
s
Z
' <
?¥G Ñ
V 3IãG<Z n
W
Ù
Ô
ü
p;
ý
H
j
ZѸZún
Ì
ü
Û
Z
Ò
'
Û
<
Û
Ò
' µI
Z
ýÛ
<
^»Z\!¥¥ä! ü
ü
'
ZÑ Zjn
' Z
Û
ü
<
Ò
ü
Ô
Z ÷9! s
<
6;
Vp3; IãG<Zjn
| T
¹ sp
Ù
Ù
I
| Tp
s
Û
Û
ü
(7.21)
o}
×
ún
>×
ñ ÙQP
Ô
×
ACRAC
*
>×
ñ
s
T
| T
s
AC
|
s
×
| T
¹ sp
Ù
×ZNµ8 ×
r÷5n;n
Ò
Ò 8×
}© ÷Ln~pV 3; IZ×}Ãú8Zµã
I G<Zjn
µi V
ü
Ù
Ù
Z n8G Z!
' j
'
ü
ü
Ô
Ú
ü
Ô
6×
¡
ü
| T
¹ sp
Ú
Z 6! ;³n
Ò<
<GÑ
b
' Z
Z n
Òe
^ ' Z !
¤
>×}©5ñ
n 3I
× ú8ZµI
×
ü
ýÛ
½
' Z
ü
Ì
AC
I
<
?¥G Ñ b
Ò
Û
'
÷
Z
e I:H
ü
Û
'
; ô Ã ã<G Z! ÃúkänîG!Y! ú
}Ã ú9Zj8
n G<NZ ÷µ }©÷Ln ; Ñ
' Z
' Z
Z
Û T µ ©÷Ln ; n Û <
Ãúä
Dn Û <
<GÑ
×Z
Ù
n
Z
Û
ü
Ò
÷ ;
ü
¹
'
'
'
<
<GÑ
b
Û
×Z Z¥8ש5n
ü
Û
ü
ü
Proof.
H P
'
' Z
ç ' Z !eG Zjn
ü
a+] ' Z
cZµI
H
Ú
Û
Û
ü
Claim 7.18. If (7.18) holds for all ×
, then
`
Z
Z
Z
Z
H P Q8!6;k
Òe
^»Z!Y!; Zjn
Ò<
^
I:H <;cZún
'
Ù | T
Ì
Ô
s `
Z
Z
n
iV;
Z½»Zún
Òe
^»Z!Y!ë
V ; ä
Z I Z '
Ù | T
Ì
÷
' Z
Ò<
?G¥
Ñ b
ç ' Z !¤;n
' Z
ZÑ Z n
Ò<
^ Z !
'
'
ü
Ò
' Z
Ò
jn
Ì
ü
<
ç¸Zb!¥¥ µ f! V ;
ü
n
n
Û
ü
ü
' Z
Û
ü
' Z <
Ãúä
Dn
Û
Òe
<G¥
Dn
Ò 8×
ü
' Z
Û
<
Ò 8
×
ü
DE
' Z
Û
Ãúä
i
DE
<
<GÑ
DERDE
Ò
134
I
AC
Ô
ýÛ
Ô
ü
Ô
Ù | T
| T
p
s ` ¹ s
Ù
Ù
Z
I:H
ü
Ú
n
Ù
| T
`s
Ì
÷
~pV 3; IZ×}Ãú8Zµã
I G<Zjn
<
Z
'
ç¸Z\!ä!Z; ' Y
Z n Û V
×ZNµi ש
Ln
ü
ü
Z
'
<;cZ n
Û ü
Ì
ü
;8
j
Ò
j
Û
Ò
Û
k
+]
cZ
Î
ý cZ\I ½»Z Û Û
¡
Òe
^
»Z!Y! ;
' ZbI Z ' Z Zfn
ZNn ' Ò<
½
\
8
pGIl ' Z
Pr ¸#(Nú
8
' Z
<
?G¥
Ñ DE
Û
Ò
Û
Û
Let #( be the event that for every ÒÁB Á' !H <; Nn ; Î
Z
}nQG<
Z Nn ' Òe
^Ì»Z!Y!ëV ;
Ò ?G¥
i
, H 8 iV;
Z
;
Z
GeZNn ' Ò<
?¥G ѳ
, andÌ H ZѸZNn ' Ò<
^»Z !ä
! Z '
;
. By the definition of Î and
the union bound, we have:
Ì
Û
ü
ü
' Z
ç ' Z !6;³n
Ò<?
G¥
i b
' Z
Ò<
ç Z !
ZÑ ' Z n
'
ü
W
ü
Ò 8×
<
Ò
Z
'
H V;cZµI Z½»Z n Û <
ç¸Z\!ä !fV; ' ZµI
| T
s
Z
' <
<G Ñ
b
V IãG<Z n
Z
Û
ü
Ò
j
' Z <
à úä
Dn
ü
Û
½
' fZ n Z Ò<
^ ' Z 6! ;n
' Ò<
ç Z !fVp; I
' Z
ç ' Z\!ZG<fZ n ' Ò<
?G¥
ѳ
Û
Τ
Û
(7.22)
Z
Suppose that γE Z
T holds. Then by (7.19) and (7.22), the probability that #}Z
' p In other words, there exists a choice
8 of the Îæ ’s and G¥Î ’s
and #( hold is strictly positive.
for which all summands in either Claim 7.17 or in Claim 7.18, whichever is appropriate, is
;
Î
0. This implies that H P
?; !ä
!; ' Z\!6 . In other words, if Î(E Z/Z T , then XÎ
'
p
belongs to
.
cZ\
;s
8
ó
Remark 7.6. Over we have: if Îo
.|G ).
R
Z
® ¥åZ ' ¥åZ Z T p , then X Î belongs to
(if
# Z denote the
In case of U , we can generalize (7.18) in a straightforward manner. Let
event that all such events holds. We can similarly obtain
8
Pr ¸# Z ¡j|GI
U
' Z X VN Ua
IQG
aIGúntG
n U
`Pºq
ν¤
(7.23)
135
.
Claim 7.19. Assume equivalent of (7.18) holds for all × +g '
`
Z
Z
Î
÷ ;
H P
Q8!6
ýÛ
I:H Î < ;
ü
| ýT
Ù
Ô
Ì
cZ n Û <
j
| ýT
Ù
Ô
AC
Ô
Ô
Ù /
|ý
f
Î
<÷9!6;
×
| ýT p
¹
I
×
ü
n
Ì
ún
Ô
n
I
ü
ÛZ
'
Û
Ô
Ù
AC
| ýT
AC
Ù
Ô
ü
Ô
Ú
Ù
| ýT
ü
8
| ýT
' Z
Û
Ò
<G
Ãúä
Dn
Òe
>×}
ü
' Z
Û
îG ' Zún
Z\!
<
?¥G i
DE
Ò
| ýT
Ù
| ýT p
¹
|
ý
ÛZ
Ô
ü
' Z
' Z
Û
Z
Î
Û
Î
| ýT p
¹
<
Ò 8
×
ü
Ãúä
Dn
' Z
Û
Òe
ü
ü
' Z
Û
<
?G¥D
n
Ò
P
Ò
' Z
Û
<
Ò 8
×
Ãúä
Ñ
DE
;3IQ CZäIQG Ã ú8ZäIt CZµIQG<G Z
' Z
Û
Ò
×
Ò
<
<GÑ
bb
Ò
' Z
Û
^»Z!Y! ; ' j
Z n
ü
ü
Î
ÒCZ×r ÷5n CÒ Zo
Zµ
×
Ù
I:H <;cZún
Ì
÷ ñ;
ü
AC
×
i bµb
Ò
Ò
Òe
<G¥
Î
> ×}©Ln ³n
Zµ
×
Ú
ü
;3IQ CZäIQG ú9ZäIt CZµIG G<Z
÷
µ ÒCZ}
× ©5n C
Ò Zo
ü
AC
Ù
`
ýÛ
Ô
ü
n
Î
ü
| ýT
Ù
Ãúµ
n
<
ü
Ù
Û <
¥i
bµb
k
8
Ò >
×}
ü
Ô
IQG Z
(7.24)
ü
Ô
Ú
I
Z
Ò
Ú
ýÛ
;
ü
sÒ P
Ú
|ý Ô
Z f
Ù
Û
*
ü
AC
Òe
<G¥
µ! CZ ; ' Z\I
ü
Ãú8Zjî
n GeZf p ש÷Ln;½¡
Î
µ שL
÷ ñ
n ;n
× Z
AC AC
Ù | ýT
p
¹
½»Z Û
Û
ü
i b
Û
8×}©÷5n;8Iô×Ãú8ZµIãG<Z\!6×}Ãú ä n8G!¥ä !o
× Ãú '
Î
Î
Z ^e I:H
ü
Ù
' Z
;
×
| ýT p
¹
Û
ü
Î
÷ n Z XÎ>×r5
ü
Ù
Ò
½
ÒCZµIG Ú
Proof.
H P
ü
It
ÛZ
ü
ü
'
Z , then
Ò ^
Z !¤;n
e
ç¸Z\!äZ! ; ' j
Z n
'
`
Z
'
Î
Ò Z
I:H Î ÒCPZ ;cµZ ÒCZäIQG Z jn
Ò<
ç¸Zb!¥¥
Ì
'
' Z
! ÒUoZ 8IQÒUµ
Z PG<ú
Z n
Òe
^ Z Û
Z ' Z n
'
ü
Ú
n
'
<
^ ' Ò
' Z
Û
; n
Z 6! ³
ü
<
<G Ñ
b
Ò
136
n
ÛZ
T
I* UZµQ
I G Z½ '
ü
ü
Ô
AC
|
Ù
ý
|
Ù
Ô
ý
Ô
Ò
Z
Ò
Î
`
cZµIQ CZäIQG I:H Î ÒCZP;
Ì
Ú
Z n
ü
' Z
<
Û Ò
Ò
ZѸZún
ü
' Z
<
Û Ò
ç¸Zb!¥¥ä!
' Z
; It CZµIG GeZ n Û ^ ' Z !sÒCZ8
ü
Ò
P j
' Z
ÒCPZ ;
<
<GÑ
bb
Ò
8
Let #P be the event analogous to the event #J in Claim 7.18. Then by the definition of
8
Î and the union bound, we have
Z
8
Τ
Pr ¸# ¡j|GI!V U '
(7.25)
Z
Then if we are given that ÎÐ ¥åZ ¥åZ Z T , then the probability that # Z and #
®
' Î p
;
hold is strictly positive. Therefore, this implies H P
<; !äZ! ; Z6! ³
.
'
cZ\
R
;
7.4.5 Proof of Lemma 7.13
For each 1z+g '
Wl1 ÷lð; Z
, let O
W1 Z÷l ;
÷zõÆ cZ
!
tÝ
be the indicator random variable
whose value is 1 if and only if
È
µ n ò Ï
?; !¥¤¥¤¥¤ Z;
' Z . Clearly, Pr O À pG¡ for every
O
. It follows that the random variable O
which counts the number
of points Ç
Z
À
À
X . It is not
of the required form in which µ/ÇC Ï Ç has expectation ã O0¡³5'
are pairwise independent, since for any two
difficult to check that the random variables O
Z
distinct -Zoù Z½»Z\!¥¤¤¥¤!f ZN and Ð ùiÀ и\Z !¥¤¥¤¥¤f! Ð ZN , the sums Î'
ZÑ Î X; Îj
'
'
Z
Ð Î X; Î; attain each pair of distinct values in " with equal probability when
and Î'
’s are pairwise independent,
the vectors are chosen randomly and independently. Since
À
Var ’s are boolean random variables,
we note
Var ¡ ¡ . Since
1
1
O[
W1(
ÛZ1 n
nòÀ , where
À
P ^ 1. 1
13Îæ
O
À
Ý
1
O
O
À
¡ItH(
ã O
À
À
À
Thus we obtain Var O[¡E O[¡ , so ( O
O
O
¡
ã ã
Û Z 1( n ;
O
O
O ñ O[
[
well known inequality which holds for a random variable O
values,
O[^¡ ;
Pr O ¡j
O ¡ ¤
Indeed if O attains value Í with probability UDÎ , then we have
Var Ý
O
ã
¡/ ã ¡IQâ ã ¡/ E¥ã ¡i¤
À
À
À
¡E ã ¡ n ã( ¡ . Next we use the following
taking nonnegative, integer
âã
ã
O[¡/
âã
ü
ÎUT ý
Í UÎ
ü
ÎUT
Í U Î U Î
ý
ER
ü
ÎVT ý
Í UÎ
ü
ÎUT
ý
UÎ
ã( O[Á¡ Pr O
;
¡Ñ!
where the inequality follows by the Cauchy-Schwartz inequality. In our case, this implies
O
Pr ù
;
¡ú OO0¡/ ¡
âã
ã
O
âã 0¡/ ã (
B¡ nLH(
ã O[
O[^¡ G8n
O[¡ ¤
O[¡
ã( ã
137
Therefore,
O0¡w
ã
Pr O
G¡UnFV
p
V O0¡
tã
G3n ã O[¡
O
Pr ùtVX¡u
Pr OM
Gc¡ n~V
p
O
I
O0¡
ã
þ
G9n (
ã I
O[¡
Pr OO÷G\¡ ÿ
Pr MpG¡i¤
After simplification we obtain,
O[¡ * O[i¡ ¤
G8G nI ( O[
¡
¡ Ý .
The proof is complete by recalling that ( O[ä
Pr OM÷G¡
ú
ã
ã
ã
ã
ó
7.5 A Lower Bound and Improved Self-correction
7.5.1 A Lower Bound
The next theorem is a simple modification of a theorem in [1] and essentially implies that
our result is almost optimal.
U that corresponds to
be any family of functions $ Proposition 7.20. Let
a linear code â . Let T denote the minimum distance of the code â and let T denote the
minimum distance of the dual code of â .
Every one-sided testing algorithm for
must perform TU queries, and if the
Z the family
distance parameter is at most TU,6 U , then `G6Xe is also a lower bound for the necessary
number of queries.
W
)
X
P s X
W
Lemma 7.4 and Proposition 7.20 gives us the following corollary.
with distance parameter must perCorollary 7.5. Every one-sided tester for testing (
Z
ý] p
form max ! nL`< _
mod U
`NU
e N queries.
P
G9
úntG
aIQG 7.5.2 Improved Self-correction
From Lemmas 7.9, 7.11 and 7.12 the following corollary is immediate:
Corollary 7.6. Consider a function ~$ ) that is -close to a degree-_ polynomial
Ê$(D )
, where LR Z
Z T . (Assume G .) Then the function can be
' p
self-corrected. That is, for any given ¬x+x , it is possible to obtain the value
¬ with
Z
Z points on .
probability at least GIl>' by querying on >'
õ
An analogous result may be obtained for the general case. We, however, improve
the
Z
above corollary slightly. The above corrector does not allow any error in the U'
points it
queries. We obtain a stronger result by querying on a slightly larger flat ² , but allowing
some errors. Errors are handled by decoding the induced Reed-Muller code on ² .
138
K
Proposition 7.21. Consider a function $e" hC that is -close to a degree-_ polynomial
$ÁD )
U . Then the function can be self-corrected. That is, assume
Ñonq ,
then for any given ¬ + , the value of /¬ can be obtained with probability at least
ÐI Zå T
U å 8åU ' åc with U queries to .
/8 p
õz
G
G
)
Ø
c\
gI 3 Q4
Ý ,4
G
,
Proof. Our goal is to correct the RM <_ !Y at the point ¬ . Assume _}öU qG con
;
å
where E
UuI V> . Then the relative distance of the code is `G-I }6,U U ' . Note
å åZ E÷ E±U å ' . Recall that the local testability test requires a Ñn -flat, i.e., it
that V!U '
Z
;
åUNå
µ? ; n Î' Û Z ÜfÎX; Î
3 , where ;XÎä+]D .
tests × × T Ù | ý Ü Z
888 p
hiÂnzG to be chosen later.
We choose a slightly larger flat, i.e., a -flat with
We consider the code restricted to this -flat with point ¬ being the origin. We query
on this -flat. It is known that a majority logic decoding algorithm exists that can decode
Reed-Muller codes up to half the minimum distance for any choice of parameters (see [99]).
Thus if the number of errors is small we can recover /¬ .
Let the relative distance of from the code be and let ¶ be the set of points where it
disagrees with the closest codeword. Let the random -flat be ² m¢¬an Î Û Z _ÑÎçË`Î · _ÑÎ+
variable takeÈ the value G if ¬ n Î Û Z ËÎ _ÑÎä+K¶ and 0
µ`! ËÎ3+( D ¦ . Let the random
8
8
8
;
[ ¦ and q
w ÊÆ^Ë Z\! ä!`Ë1 . Define
otherwise. Let 7HQ
88 8 Ù 88 8
and ÷U
IQG . We would like to bound the probability
õ4HE ,
ݧ
Â
ý
÷;
ú
¢
k
÷õ
=
÷ l
Pr æ· qI ·c÷
Ý<6<VòIle
A
k 1÷
÷
zÆ _fZ!ä!Z_
A
G 1÷¡"
ü
@
E
å
iýà
ð
-Il
JI´
1øÇ 1÷ ! ÷
ü
Û
ð
Ý
ún
-Il ún
Ù |
I@G 1÷ ¡Un
1øÇ 1÷ ! ÷
ð
¡Un
ð
Û7Y
UaIQG
ð
aIV>/- Il
cU
ð
Ú
Hm
1 1÷ ÷
1÷ 1÷
ü
Û7Y
ð
ð
È
. Now
ð
ð
?
¡
ð
Ú
ü
=
¡i¤
Since Pr ³ pG¡Q , by linearity we get ã Ð }¡t . Let HL
888
A
= ÷;
;
ð
Z Û7Y Ù |
1 ÇÁ ÷ ! ÷
ð
¡
ð
Ú
÷
The above follows from the fact that when ç
Ï Ùl(
H then the corresponding events
and
;
. Also, when
and are dependent
! ¡"
are independent and therefore ø Ç ¡j³ã Ð ¡jE-Il . å Z
then ø ! ¡ ã Ð ¡I ã³Ð Therefore, by Chebyshev’s inequality we have (assuming R U ' )
÷
ð
1 ÇÁ ÷ ÷
ð
ð
k
÷ ÷
A
ð
÷
ð
A
ð
ð
ð
ð
#
A
ð
Pr æ· |I´ ·Up
Ý<6<VòIle
A
÷
¡jE
U GI´<\ U.I
G
WÝ<e6 VsI´<
÷
ð
ð
139
Now note W<Ý e6 VsIle9pU
÷
å ' å Z
I´<k÷`G I´JU '
Pr ³ ®· |I´ ·c÷WÝe6<VòIle
A
¡jE
Z U å ' å Z . We thus have
c`G Il< \ UaIG
GIl-h U ' Z U Uå ' åU
^ U
Z åU U
GIl-h U ' U ' å nQG
å 8åU ' cå
Z h U
¤
GIl-h U ' E
7.6 Bibliographics Notes
The results presented in this chapter appear in [72].
As was mentioned earlier, the study of low degree testing (along with self-correction)
dates back to the work of Blum, Luby and Rubinfeld ([21]), where an algorithm was required to test whether a given function is linear. The approach in [21] later naturally extended to yield testers for low degree polynomials over fields larger than the total degree.
Roughly, the idea is to project the given function on to a random line and then test if the
projected univariate polynomial has low degree. Specifically, for a purported degree _ function ,$B¯ ) ¯ , the test works as follows. Pick vectors ; and from Á¯ (uniformly at
random), and distinct Á<Z! Y!,Á Z from ¯ arbitrarily. Query the oracle representing at
the _cnwG points Dn ÁÎ ; and extrapolate to a degree _ polynomial in one variable Á . Now
A B
test for a random Á+g if
ÁX Lµ ;nºÁr;
;
;
A
k
B
(for details see [93],[42]). Similar ideas are also employed to test whether a given function
is a low degree polynomial in each of its variable (see [36, 8, 6]).
Alon et al. give a tester over field for any degree up to the number of inputs to the
function (i.e., for any non-trivial degree) [1]. In other words, their work shows that ReedMuller codes are locally testable. Under the coding theory interpretation, their tester picks
a random minimum-weight codeword from the dual code and checks if it is orthogonal to
the input vector. It is important to note that these minimum-weight code words generate
the Reed-Muller code.
;
;
Specifically their test works as follows: given a function $C¢ !¥Ge¦X
!¥Ge¦ , to test if
;
the given function has degree at most _ , pick <_änLG -vectors ; Z\!¥¥äZ! ;X
Z-+~ !¥Ge¦ and
test if
Á
K
)
¢
¢
ü
Û
* 4Þ á
Z ü
ÎÙ
Þ
;XÎWk
;
¤
Ú
Independent of [72], Kaufman and Ron, generalizing a characterization result of [42],
gave a tester for low degree polynomials over general finite fields (see [74]). They show
that a given polynomial is of degree at most _ if and only if the restriction of the polynomial to every affine subspace of suitable dimension is of degree at most _ . Following this
140
idea, their tester chooses a random affine subspace of a suitable dimension, computes the
polynomial restricted to this subspace, and verifies that the coefficients of the higher degree
terms are zero4 . To obtain constant soundness, the test is repeated many times. An advantage of the approach presented in this chapter is that in one round of the test (over the prime
field) we test only one linear constraint, whereas their approach needs to test multiple linear
constraints.
A basis of RM consisting of minimum-weight codewords was considered in [28, 29].
We extend their result to obtain a different exact characterization for low-degree polynomials. Furthermore, it seems likely that their exact characterization can be turned into a
robust characterization following analysis similar to our robust characterization. However,
our basis is cleaner and yields a simpler analysis. We point out that for degree smaller than
the field size, the exact characterization obtained from [28, 29] coincides with [21, 93, 42].
This provides an alternate proof to the exact characterization of [42] (for more details, see
Remark 7.3 and [42]).
In an attempt to generalize our result to more general fields, we obtain an exact characterization of low degree polynomials over general finite fields [71] (see [86] for more
details). This provides an alternate proof to the result of Kaufman and Ron [74] described
earlier. Specifically the result says that a given polynomial is of degree at most _ if and
Z only if the restriction of the polynomial to every affine subspace of dimension ¯ å ¯ (and
higher) is of degree at most _ .
Recently Kaufman and Litsyn ([73]) show that the dual of BCH codes are locally
testable. They also give a sufficient condition for a code to be locally testable. The condition roughly says that if the number of fixed length codewords in the dual of the union
of the code and its -far coset is suitably smaller than the same in the dual of the code,
then the code is locally testable. Their argument is more combinatorial in nature and needs
the knowledge of weight-distribution of the code and thus differs from the self-correction
approach used in this work.
4
Since the coefficients can be written as linear sums of the evaluations of the polynomial, this is equivalent
to check several linear constraints