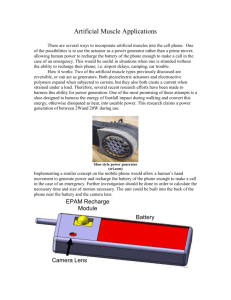
EPAM Systems
advertisement

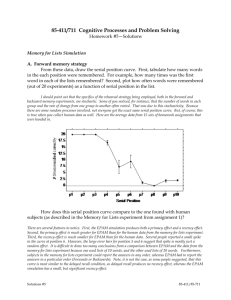
EPAM Systems Creating trend analysis and calculating risks by security incidents for ISMS on ISO/IEC 27001:2005 compliance using @RISK and StatTools 2011 © EPAM Systems Introduction to ISMS of EPAM Systems EPAM Systems, the leading provider of IT outsourcing and software services and solutions in Central and Eastern Europe, provides software development, e-commerce and content management services to forward-thinking companies and government organizations in over 30 countries worldwide. EPAM Systems Integrated Quality Management System is based on the EPAM Quality Policy and Information Security Policy reflecting most of the requirements of: ISO 9001:2008, Quality Management Systems – Requirements ISO/IEC 27001:2005, Information technology - Security techniques Information security management systems – Requirements CMMI® for Development, Version 1.2 ISAE 3000 (SAS 70) TYPE II COBIT V4.1 ISMS is part of the overall management system, based on a business risk approach, to establish, implement, operate, monitor, review, maintain and improve information security. 2011 © EPAM Systems 2 My Introduction. Prerequisites for this work • • • • Huge Project Management Scientist experience: Creation and Implementation of Industrial Project Management Systems for Nuclear and Thermal Power Plants, Power Systems Ph.D. Thesis was defended For that purpose System Development Strategy, Vision, Requirements, Design, Mathematical Models, Algorithms, Database and Software were developed Optimization models were elaborated using: LP, NLP, IP, Heuristic Models, Network and Flow Algorithms Large CMMI experience (SPICE, CMM, CMMI x.x) from 1999 BSI Management Systems certificates: Information Security Management System BS ISO/IEC 27001 Implementation, BS ISO/IEC 27001 Internal Auditor (November, 2007) www.bsi-global.com; Basic statistical tools and approaches we are using for CMMI ML4: Regression Analysis, Control Charts, ANOVA, Pareto Analysis Hypothesis Test, Confidence Interval, Time Series Analysis, Monte Carlo Simulation, Earned Value Management 2011 © EPAM Systems 3 ISO/IEC 27001:2005 ISO/IEC 27001:2005 specifies the requirements for establishing, implementing, operating, monitoring, reviewing, maintaining and improving documented ISMS within the context of the organization’s overall business risks It specifies requirements for the implementation of security controls customized to the needs of individual organizations or parts thereof The ISMS is designed to ensure the selection of adequate and proportionate security controls that protect information assets and give confidence to interested parties Features of ISO/IEC 27001:2005: Plan, Do, Check, Act (PDCA) Process Model Process Based Approach Stress on Continual Process Improvements Covers People, Process and Technology 11 Domains, 39 Control objectives, 133 controls 2011 © EPAM Systems 4 ISMS main processes are presented in the layer view 2011 © EPAM Systems 5 Information Security Risk Management Process by ISO 27005 Risk Management is composed of the following parts: • Defining the risk assessment approach of the organization, context • Identifying risks • Estimating and evaluating risks • Identifying and evaluating options for the treatment of risks • Selecting control objectives and controls for the treatment of risks • Obtaining management approval of the proposed residual risks • Obtaining management authorization to implement and operate the ISMS • Preparing the Statement of Applicability • Preparing the Risk Treatment Plan • Implementing the Risk Treatment Plan 2011 © EPAM Systems 6 Risk Assessment for 2011(fragment) Asset Name Threat Vulnerability Likelihood Likelihood level Impact Impact level Risk Risk Level Residual Risk 2010 Residual Risk Level Residual Risk 2011 Residual Risk Level Backup equipment Environmental issues Fire 0.1 Unlikely 0.6 Damaging 0.06 Low 0.0005 Low 0.0005 Low Backup equipment Environmental issues Loss of power 0.1 Unlikely 0.1 Minor 0.01 Low 0.0050 Low 0.0050 Low Backup equipment Environmental issues Unlikely 0.6 Damaging 0.12 Medium 0.0100 Low 0.0100 Low Human error Snow/Ice/Hail/Rain Storm/Flood Lack of awareness training and training 0.2 Backup equipment 0.1 Unlikely 0.4 Significant 0.04 Low 0.0200 Low 0.0150 Low Backup equipment Ineffective Security Safeguards Lack of adequate physical controls to protect assets 0.2 Unlikely 0.1 Minor 0.02 Low 0.0100 Low 0.0050 Low Backup equipment System failure Technical failures 0.3 Fairly likely 0.2 Minor 0.05 Low 0.0100 Low 0.0100 Low Backup equipment Unauthorized entry into premises Unauthorized access to sensitive areas 0.2 Unlikely 0.2 Serious 0.16 Medium 0.0300 Low 0.0150 Low Backup tape Environmental issues Fire 0.1 Unlikely 0.3 Significant 0.03 Low 0.0005 Low 0.0005 Low Backup tape Environmental issues Snow/Ice/Hail/Rain Storm/Flood 0.2 Unlikely 0.3 Significant 0.06 Low 0.0100 Low 0.0100 Low Backup tape Ineffective Security Safeguards Lack of adequate physical controls to protect assets 0.2 Unlikely 0.2 Minor 0.04 Low 0.0100 Low 0.0100 Low Backup tape System failure Technical failures 0.3 Fairly likely 0.4 Significant 0.05 Low 0.0100 Low 0.0100 Low Backup tape Unauthorized entry into premises Unauthorized access to sensitive areas 0.2 Unlikely 0.2 Serious 0.16 Medium 0.0300 Low 0.0150 Low Building space H29 Environmental issues Explosion, Terrorist Action, Sabotage 0.01 Very unlikely 0.8 Serious 0.008 Low 0.0001 Low 0.0001 Low Building space H29 Environmental issues Fire 0.25 Unlikely 0.4 Significant 0.1 Medium 0.0009 Low 0.0009 Low Building space H29 Environmental issues High humidity 0.2 Unlikely 0.3 Significant 0.06 Low 0.0200 Low 0.0200 Low Building space H29 Environmental issues Loss of power 0.2 Unlikely 0.2 Minor 0.04 Low 0.0100 Low 0.0100 Low Building space H29 Environmental issues Snow/Ice/Hail/Rain Storm/Flood/Earthquake 0.1 Unlikely 0.2 Minor 0.02 Low 0.0100 Low 0.0100 Low Building space H29 Environmental issues Water 0.4 Fairly likely 0.3 Significant 0.12 Medium 0.0400 Low 0.0400 Low 2011 © EPAM Systems 7 Ranges Likelihood Value Uncertainty Statement 0 Impossible 0.01 Very unlikely 0.1 Unlikely 0.3 Fairly likely 0.5 Likely 0.7 Very likely 0.9 Certain Explanation Impact Value Explanation No impact Minor impact to business objectives Tangible harm, extra effort required to repair Significant expenditure of resources required Extended outage and / or loss of connectivity Permanent shutdown 0 0.01 0.3 0.5 0.7 0.9 Risk Value Impossible Unlikely to occur 2-3 times every 5 year Up to twice a year Up to once per month More than once a month Several times a week or a day Impact Statement Insignificant Minor Significant Damaging Serious Grave Statement 0 Low 0.07 Medium 0.45 High 0 0.01 0.3 0.5 0.7 0.9 Explanation Minor impact and unlikely to occur at a maximum. Acceptable risk, treatment plan is not mandatory. Medium risk. Action is required within 1 year. At least very likely with serious impact. Immediate action (within 1-3 months) is required. 0 0 0 0 0 0 0 0.01 0 0.0001 0.003 0.005 0.007 0.009 2011 © EPAM Systems 0.1 0 0.001 0.03 0.05 0.07 0.09 0.3 0 0.003 0.09 0.15 0.21 0.27 0.5 0 0.005 0.15 0.25 0.35 0.45 0.7 0 0.007 0.21 0.35 0.49 0.63 0.9 0 0.009 0.27 0.45 0.63 0.81 8 Pareto Chart of Residual Risk by Asset Group and Assets 2011 © EPAM Systems 9 Overlay results graphs of Residual Risks Risk 2011 Residual Risk 2011 Risk 2012 Residual Risk 2012 166 166 166 166 Mean (Average of Risks) 0.05261 0.02088 0.05261 0.01931 Standard Deviation 0.04366 0.01661 0.04366 0.01514 Statistical Inferences Size (Number of Risks) 2011 © EPAM Systems 10 Security Incidents Summary Security Incidents - 2011 Country Office Jan BY Brest 1 BY Grodno 0 BY Gomel 0 BY Minsk 13 BY Mogilev 0 HU Budapest 2 KZ Astana 0 KZ Karaganda 1 RU Izhevsk 0 RU Moscow 1 RU St. Petersburg 0 RU Ryazan 0 RU Samara 0 RU Saratov 1 RU Tver 0 UA Dnipropetrovsk 0 UA Kharkov 0 UA Kyiv 5 UA Lviv 2 UA Vinnitsa 0 US Newtown 0 26 Total by EPAM Feb 0 1 0 11 0 0 0 1 0 1 1 0 1 0 0 1 0 2 1 0 0 20 Mar 0 0 0 14 0 0 0 0 0 4 0 0 1 0 1 0 0 3 0 1 0 24 Apr 0 1 0 10 0 0 0 2 0 0 0 1 2 0 0 0 1 0 2 1 0 20 May 0 0 0 17 0 0 0 1 0 0 0 0 0 0 0 0 0 3 2 0 0 23 Jun 0 0 2 13 0 0 0 0 2 6 3 0 0 3 0 0 1 9 4 1 0 44 Jul 0 1 0 19 1 0 0 0 2 0 0 0 0 0 0 1 2 14 2 0 0 42 Aug 0 1 0 16 0 0 0 3 2 2 1 0 3 0 0 0 1 8 4 0 0 41 Sep 1 0 1 11 0 0 1 4 2 5 2 0 0 2 0 0 1 10 0 1 0 41 Oct 0 3 2 13 0 0 0 3 3 2 2 3 2 2 0 0 2 17 3 1 0 58 Nov 1 0 0 8 0 1 0 6 1 2 2 0 6 2 0 3 1 15 4 1 0 53 2011 © EPAM Systems Dec 2 0 0 6 0 0 0 3 0 2 4 0 4 3 0 1 2 9 3 0 0 39 Security Incidents by Offices 5 7 5 151 1 3 1 24 12 25 15 4 19 13 1 6 11 95 27 6 0 431 Risks by Offices 2011 0.41666667 0.58333333 0.41666667 12.5833333 0.08333333 0.25 0.08333333 2 1 2.08333333 1.25 0.33333333 1.58333333 1.08333333 0.08333333 0.5 0.91666667 7.91666667 2.25 0.5 0 35.9166667 SERVER S 5 20 34 1198 26 236 7 207 30 133 93 61 107 161 16 4 70 247 156 8 1 2820 Work Stations 75 103 175 2783 70 428 42 167 90 172 160 182 126 285 36 75 188 740 285 46 110 6338 Security Security Total Incident/Wor Incident/Total Equipment kstation, % Equipment, % 80 123 209 3981 96 664 49 374 120 305 253 243 233 446 52 79 258 987 441 54 111 9158 6.67 6.80 2.86 5.43 1.43 0.70 2.38 14.37 13.33 14.53 9.38 2.20 15.08 4.56 2.78 8.00 5.85 12.84 9.47 13.04 0.00 6.80 6.25 5.69 2.39 3.79 1.04 0.45 2.04 6.42 10.00 8.20 5.93 1.65 8.15 2.91 1.92 7.59 4.26 9.63 6.12 11.11 0.00 4.71 11 Security Incidents by Offices using Control Charts One of the techniques that are used to establish operational limits for acceptable variation is the use of Control Charts. It is used for quantifying process behavior. Security Incidents Jan-Dec 2011 Security Incidents, mean Center Line, Mean Lower Sig1 Limit Upper Sig1 Limit Lower Ctrl Limit, (LCL) Upper Ctrl Limit, (UCL) 1.63 1.632575758 1.298060606 1.967090909 0.629030303 2.636121212 2011 © EPAM Systems 12 Regression Analysis • • Simple Multiple is used for predictions. It builds an equation using the selected explanatory variables. Regression equation: SECURITY INCIDENTS TOTAL BY OFFICES = 3.392 + 0.0393 * TOTAL EQUIPMENT 2011 © EPAM Systems 13 Regression Analysis reports Reports from each analysis include summary measures of each regression equation run, an ANOVA table for each regression, and a table of estimated regression coefficients, their standard errors, their tvalues, their p-values, and 95% confidence intervals for them for each regression. Multiple Summary ANOVA Table Explained Unexplained R R-Square Adjusted StErr of R-Square Estimate 14.74269784 0.9176 0.8420 0.8336 Degrees of Sum of Mean of Freedom Squares Squares 1 19 21999.64245 4129.59565 21999.64245 217.3471395 F-Ratio p-Value 101.2189 < 0.0001 Standard Confidence Interval 95% Regression Table Coefficient t-Value Constant Total Equipment 3.392079508 3.639983727 0.9319 0.039284378 0.003904712 10.0608 p-Value Error 2011 © EPAM Systems Lower Upper 0.3631 -4.22649399 11.01065301 < 0.0001 0.031111721 0.047457034 14 Time Series and Forecasting of Security Incidents • The Forecasting provides a number of methods for forecasting a time series variable. We are using Holt's exponential smoothing method for capturing trend. • The forecast reports include a set of columns to show the various calculations (for example, the smoothed levels and trends for Holt's method, and so on), the forecasts, and the forecast errors. 2011 © EPAM Systems 15 Pareto Chart of Security Incidents by Offices and by Countries 2011 © EPAM Systems 16 Monte Carlo Simulation • @RISK uses Monte Carlo simulation to analyze thousands of different possible outcomes, showing us the likelihood of each occurring. Monte Carlo simulation is a computer-intensive technique for assessing how a statistic will perform under repeated sampling. In Monte Carlo methods, the computer uses random number simulation techniques to mimic a statistical population. • Outcomes of Monte Carlo Simulation using Confidence Intervals are prediction number of incidents expected in each office. • The predictions are represented by the upper control limit, the central value and the lower control limit and the confidence of achieving them. • The model summarizes also the total number of incidents expected at organizational level, represented too by the upper control limit, the central value and the lower control limit and the confidence of achieving them, and the associated confidence interval. 2011 © EPAM Systems 17 Define Distribution of Risks by Offices and Risks by Offices 2011 2011 © EPAM Systems 18 Output results summary by Offices (fragment) Name Worksheet Cell Graph Min Mean Max 5% 95% Errors Brest / Risks by Offices 2011 Summary_2 P3 011 -2.175979 0.4166674 3.026024 -0.683154 1.516106 0 Grodno / Risks by Offices 2011 Summary_2 P4 011 -3.347512 0.5833397 4.634865 -0.8977569 2.063855 0 Gomel / Risks by Offices 2011 Summary_2 P5 011 -2.547892 0.4167063 3.856878 -0.8877159 1.720214 0 Minsk / Risks by Offices 2011 Summary_2 P6 011 -2.499412 12.58321 26.73282 6.48934 18.67316 0 Mogilev / Risks by Offices 2011 Summary_2 P7 011 -1.001166 0.08333025 1.179311 -0.3915962 0.5579265 0 Budapest / Risks by Offices 2011 Summary_2 P8 011 -2.080682 0.2500368 2.960976 -0.7725362 1.272372 0 Astana / Risks by Offices 2011 Summary_2 P9 011 -1.020973 0.08333907 1.237291 -0.391588 0.5580279 0 Karaganda / Risks by Offices 2011 Summary_2 P10 011 -5.932271 1.999917 8.974371 -1.057276 5.05664 0 Izhevsk / Risks by Offices 2011 Summary_2 P11 011 -3.62505 1.000029 6.004847 -0.8563967 2.854966 0 Moscow / Risks by Offices 2011 Summary_2 P12 011 -5.311656 2.083381 9.774927 -1.16638 5.332192 0 St. Petersburg / Risks by Offices 2011 Summary_2 P13 011 -4.094762 1.249985 6.313061 -0.9817926 3.480608 0 2011 © EPAM Systems 19 Output results by Offices (fragment)– Cumulative function 2011 © EPAM Systems 20 Security Incident / Workstation /Total Equipment, % 2011 © EPAM Systems 21 Overlay Graphs Security Incident/Workstation/Total Equipment, % 2011 © EPAM Systems 22 Summary Thanks to @Risk and StatTools applications of Palisade software EPAM Systems has effectively implemented statistical process control to manage and improve of trend analysis of security incidents for ISMS on ISO/IEC 27001:2005 compliance. EPAM Systems has used the following basic statistical techniques: Regression Analysis, Control Charts, ANOVA, Hypothesis Test, Confidence Interval, Time Series Analysis, Monte Carlo Simulation. To support CMMI High Maturity of Process Performance Baselines and Models EPAM Systems is going to implement additionally tools and approaches of DecisionTools Suite: Six Sigma, Decision Tree Analysis, Sensitivity Analysis and others. 2011 © EPAM Systems 23 Questions Thanks for your attention Creating trend analysis and calculating risks by security incidents for ISMS on ISO/IEC 27001:2005 compliance using @RISK and StatTools By Vladimir Savin, Ph.D. Vladimir_Savin@epam.com EPAM Systems 41 University Drive, Suite 202 | Newtown, PA 18940 p: +1 267 759 9000 | f: +1 +1 267 759 8989 | e: info@epam.com | w: www.epam.com