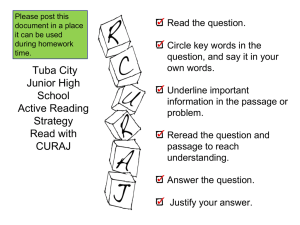
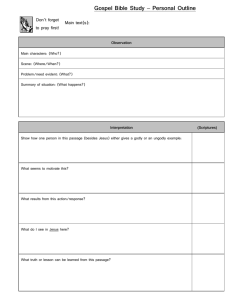
B. to use - HUBT Sharing
advertisement

Reading 1.In the last decade, computers have come an integral part of every life at home, work, school, and nearly everywhere else. Of course, almost every computer user encounters a problem occasionally, whether it is the annoyance of a forgotten password or the disaster of a crashing hard drive. The explosive use of computers has created demand for specialists who provide advice to users, as well as for the day-to-day administration, maintenance, and support of computer systems and networks. The word 'integral' in the passage is referred to____. basic essential fundamental *All the choices are correct 2.In the last decade, computers have come an integral part of every life at home, work, school, and nearly everywhere else. Of course, almost every computer user encounters a problem occasionally, whether it is the annoyance of a forgotten password or the disaster of a crashing hard drive. The explosive use of computers has created demand for specialists who provide advice to users, as well as for the day-to-day administration, maintenance, and support of computer systems and networks. The word ' explosive' in the passage is referred to___. burning *increasing bombing deceasing 3.However, machine code as a means of communication is very difficult to write. For this reason, we use symbolic languages that are easier to understand. Then, by using a special program, these languages can be translated into machine code. For example, the so-called assembly languages use abbreviations such as ADD, SUB, MPY to represent instructions. These mnemonic codes are like labels easily associated with the items to which they refer. According to the passage, machine code is___. impossible to write not easy to write easy to write *very difficult to write 4.However, machine code as a means of communication is very difficult to write. For this reason, we use symbolic languages that are easier to understand. Then, by using a special program, these languages can be translated into machine code. For example, the so-called assembly languages use abbreviations such as ADD, SUB, MPY to represent instructions. These mnemonic codes are like labels easily associated with the items to which they refer. Which of the following does these languages in the passage refer to? assembly languages special programs *symbolic languages machine code 5.However, machine code as a means of communication is very difficult to write. For this reason, we use symbolic languages that are easier to understand. Then, by using a special program, these languages can be translated into machine code. For example, the so-called assembly languages use abbreviations such as ADD, SUB, MPY to represent instructions. These mnemonic codes are like labels easily associated with the items to which they refer. Which of the following is the word 'instructions' in the passage closest to? comments *commands translations explanations 6.Basic languages, where the program is similar to the machine code version, are know as low-level languages. In these languages, each instruction is equivalent to a single machine code instruction, and the program is converted into machine code by a special program called an assembler. These languages are still quite complex and restricted to particular machines. Which of the following does ' these languages' in the passage refer to? machine code version assemblers high-level languages *low-level languages 7.Basic languages, where the program is similar to the machine code version, are know as low-level languages. In these languages, each instruction is equivalent to a single machine code instruction, and the program is converted into machine code by a special program called an assembler. These languages are still quite complex and restricted to particular machines. Which of the following is not TRUE about the passage? *Low-level languages are still quite complex and restricted to any machines. The program is converted into machine code by an assembler. In these languages, each instruction is equal to a single machine code instruction. Basic languages are know as low-level languages. 8.To make the program easier to write and to overcome the problem of intercommunication between different types of machines, higher level languages were designed such as BASIC, COBOL, FORTRAN or Pascal. These are all problem-oriented rather than machine-oriented. Programs written in one of these languages (know as source programs) are converted into a lower-level language by means of a compiler (generating the object program). On compilation, each statement in a high-level language is generally translated into many machine code instructions. Which of the following can be inferred from the passage? The function of a compiler in a program The intercommunication between a high-level language and a low-level language. The difference between problem-oriented and machine-oriented. *Higher level languages were designed to solve the problem of intercommunication between different types of machines 9.To make the program easier to write and to overcome the problem of intercommunication between different types of machines, higher level languages were designed such as BASIC, COBOL, FORTRAN or Pascal. These are all problem-oriented rather than machine-oriented. Programs written in one of these languages (know as source programs) are converted into a lower-level language by means of a compiler (generating the object program). On compilation, each statement in a high-level language is generally translated into many machine code instructions. Which of the following does 'these languages' in the passage refer to? machine code instruction *higher level languages low-level languages Compilers 10.To make the programs easier to write and to overcome the problem of intercommunication between different types of machines, higher level languages were designed such as BASIC, COBOL, FORTRAN or PASCAL. There are all problem-oriented rather than machineoriented. Programs written in one of these languages ( known as source programs) are converted into a lower-level language by mean of compiler (generating the object program). On compilation, each statement in a high-level language is generally translated into many machine code instructions. The word 'translated' in the passage is the closet to___. Turned Changed *Converted Transferred 11.People communicate instructions to the computer in symbolic languages and the easier this communication can be made the wider the application of computers will be. Scientists are already working on Artificial Intelligence and the next generation of computers may be able to understand human languages. The word 'communicate' in the passage is the closet to__ *Send Talk Transfer Order 12.People communicate instructions to the computer in symbolic languages and the easier this communication can be made the wider the application of computers will be. Scientists are already working on Artificial Intelligence and the next generation of computers may be able to understand human languages. Which of the following is true about the passage? Symbolic languages can make a wider application of computers. *The next generation of computers may be able to understand human languages. Scientists have been working on Artificial Intelligence People communicate with the computer in symbolic languages 13.The question of security is crucial when sending confidential information such as credit card number. For example, consider the process of buying a book on the Web. You have to type your credit card number into an order from which passes from computer on its way to the online bookstore. If one of the intermediary computers is infiltrated by hackers, your data can be copied. it is difficult to say how often this happens, but it's technically possible. Which of the following is the passage about? sending confidential data such as credit card number *the importance of security when sending confidential data the process of buying a book on the Web data can be copied by intermediary computers 14.The question of security is crucial when sending confidential information such as credit card number. For example, consider the process of buying a book on the Web. You have to type your credit card number into an order from which passes from computer on its way to the online bookstore. If one of the intermediary computers is infiltrated by hackers, your data can be copied. it is difficult to say how often this happens, but it's technically possible. The word 'which' in the passage referred to___ *An order form Your credit card number credit card number the process of buying a book 15.The question of security is crucial when sending confidential information such as credit card number. For example, consider the process of buying a book on the Web. You have to type your credit card number into an order from which passes from computer on its way to the online bookstore. If one of the intermediary computers is infiltrated by hackers, your data can be copied. it is difficult to say how often this happens, but it's technically possible. The word 'its' in the passage referred to___ credit card number Data Computer *An order form 16. A computer displays images on the phosphor-coated surface of a graphics display screen by means of an electron beam that sweeps the screen many times each second. Those portions of the screen energized by the beam emit light, And changes in the intensity of the beam determine their brightness and hue. The brightness of the resulting image fades quickly, however, and must be continuously 'refreshed' by the beam, typically 30 times per second. Which of the following is the passage about? Performance of an electron beam The role of the brightness of the resulting image on screen *How a computer displays images on a graphics display The interaction between brightness and hue on the screen. 17.A computer displays images on the phosphor-coated surface of a graphics display screen by means of an electron beam that sweeps the screen many times each second. Those portions of the screen energized by the beam emit light, And changes in the intensity of the beam determine their brightness and hue. The brightness of the resulting image fades quickly, however, and must be continuously 'refreshed' by the beam, typically 30 times per second. The word 'portion' in the passage is closest to_____ Rates *Sections Divisions Groups 18. Private networks connected to the internet can be attacked by intruders who attempt to take valuable information such as Social security numbers, bank accounts or research and business reports. To protect crucial data, companies hire security consultants who analyze the risks and provide security solution. The most common methods of protection are passwords for access control, encryption and decryption systems, and firewalls. The word 'intruders' in the passage is referred to_____ *Hackers. Consultants Pirates While hackers 19.Private networks connected to the internet can be attacked by intruders who attempt to take valuable information such as Social security numbers, bank accounts or research and business reports. To protect crucial data, companies hire security consultants who analyze the risks and provide security solution. The most common methods of protection are passwords for access control, encryption and decryption systems, and firewalls. According to the passage, which of the following do security consultants do? *Analyze the risks and provide security solutions Take valuable information Provide common methods of protection Protect crucial data 20. If your friend suddenly had an accident and was unconscious or incoherent, could you provide any information to an ambulance crew? Would you know her type, her allergies, the prescription drugs she takes? Probably not. Even family members may not have this information, or be too distraught themselves to provide needed medical information. Enter the MediCard, a plastic card that has an embedded chip containing all that patient information. Small computers that can read the cards are installed in ambulances and in hospital emergency rooms. This system is working successfully in some communities. The biggest problem is making sure that people carry their cards at all times. Which of the following is the passage about? Performance of an ambulance crew Providing needed medical information *Introduction of the MediCard Installing small computers in ambulances and in hospital emergency rooms 21. If your friend suddenly had an accident and was unconscious or incoherent, could you provide any information to an ambulance crew? Would you know her type, her allergies, the prescription drugs she takes? Probably not. Even family members may not have this information, or be too distraught themselves to provide needed medical information. Enter the Medicard, a plastic card that has an embedded chip containing all that patient information. Small computers that can read the cards are installed in ambulances and in hospital emergency rooms. This system is working successfully in some communities. The biggest problem is making sure that people carry their cards at all times. According to the passage which of the following is NOT TRUE about the Medicard A plastic card with an embedded chip providing a person's needed medical information A plastic card with an embedded chip providing a person's blood type, her allergies, the prescription drugs A plastic card with an embedded chip containing all that patient information *the Medicard is installed in ambulances and in hospital emergency rooms 22. If your friend suddenly had an accident and was unconscious or incoherent, could you provide any information to an ambulance crew? Would you know her type, her allergies, the prescription drugs she takes? Probably not. Even family members may not have this information, or be too distraught themselves to provide needed medical information. Enter the Medicard, a plastic card that has an embedded chip containing all that patient information. Small computers that can read the cards are installed in ambulances and in hospital emergency rooms. This system is working successfully in some communities. The biggest problem is making sure that people carry their cards at all times. the passage is closest to_____ Nervous *Distracted Worried Unconscious The word 'distraught' in 23. This may sound very much like shopping by the internet, but in fifty years' time it will be very different. Shoppers will be able to scan down virtual supermarket aisles on their PC and click on to whatever they want, the goods will then be delivered shortly afterwards. Customers may well be able ta call up a virtual assistant who will talk them through their shopping or to ask the computer for suggestions. Moreover, people will be able to get background information on shops and goods, and will be able to boycott any that offend their ethical considerations. Which of the following is the passage is mainly about? Goods delivery Getting background information on shops and goods *Computer shopping Shopping by the internet. 24. Computer support specialists provide technical assistance, support, and advice to customers and other users. This occupational group includes technical support specialists and help-desk technicians. These troubleshooters interpret problems and provide technical support for hardware, software, and systems. They answer telephone calls, analyze problems by using automated diagnostic program, and resolve recurring difficulties. What do TROUBLESHOOTERS refer to? *technical support specialists and help-desk technicians help-desk technicians technical support specialists customers and other users 25. Computer support specialists provide technical assistance, support, and advice to customers and other users. This occupational group includes technical support specialists and help-desk technicians. These troubleshooters interpret problems and provide technical support for hardware, software, and systems. They answer telephone calls, analyze problems by using automated diagnostic program, and resolve recurring difficulties. What is not the job task of computer support specialists? Providing technical support for hardware and software *Providing technical support and diagnosis program to customers Providing advice to customers via telephone Using automated diagnostic programs to analyze problems 26. Experts advise us to register country-specific do main names such as '.fr' for France, '.mx' for Mexico or '.vn' for Vietnam. That way, we can protect our brand name in other countries and be ready to expand our business internationally. There are now more than 191 countrycode domain names available, each with its own set of regulations. A Belgian company's country-code domain names will most probably be� AAA.com.fr AAA.com.vn AAA.com.mx *None of the choices is accepted EXCEPT THIS ONE 27. Experts advise us to register country-specific do main names such as '.fr' for France, '.mx' for Mexico or '.vn' for Vietnam. That way, we can protect our brand name in other countries and be ready to expand our business internationally. There are now more than 191 countrycode domain names available, each with its own set of regulations. What is not true about country-specific domain names ? They are, for example , .fr, .mx, or .vn There are nearly 100 country- specific domain names now *Country- specific domain names may the same for some countries Country-code domain names has different regulations 28. Experts advise us to register country-specific do main names such as '.fr' for France, '.mx' for Mexico or '.vn' for Vietnam. That way, we can protect our brand name in other countries and be ready to expand our business internationally. There are now more than 191 countrycode domain names available, each with its own set of regulations. Why should we register country- specific domain names? *To protect our brand in other countries To expand locally To have a set of regulations To protect your business domestically 29. the U.S. Anti-cyber squatting Consumer Protection Act, which makes it easier for business to sue pirates holding domain names for ransom, has just been approved. However, the effectiveness of the new remains an open question. Moreover, small companies and individuals cannot afford a lengthy court battle. What can RANSOM most probably be? facilities *money human jobs 30. the U.S. Anti-cyber squatting Consumer Protection Act, which makes it easier for businesses to sue pirates holding domain names for ransom, has just been approved. However, the effectiveness of the new law remains an open question. Moreover, small companies and individuals cannot afford a lengthy court battle. Which statement is not true? In the US, there has been an anti-cyber squatting Consumer Act *There is a question about the anti-cyber squatting Consumer Act If you cyber squat in the US, you may be sued People are still not sure about the effectiveness of the anti-cyber squatting Consumer Act 31. a new batch of domain extensions would open the field for businesses and consumers who have been shut out of the '.com' Web land. Based on negotiations among ICANN members, there ultimately could be many more extensions. No final decisions have been made -ICANN is expected to debate this issue at its next international conference -but new extensions under consideration include .biz, .firm, .shop, .airline. What is not true about the text? ICANN members decide what new extensions should be included ICANN hasn't decided what new extensions should be *biz, .firm, .airline and .shop are four new extensions that ICANN has decided to have one of the topics to be discussed at ICANN's next international conference is a new batch of domain extensions 32. A new batch of domain extensions would open the field for businesses and consumers who have been shut out of the 'com' web land. Based on negotiations among ICANN members , there ultimately could be many more extension. No final decisions have been made-ICANN is expected to debate this is sue at its next international conference- but new extensions under consideration include .biz, .firm, .shop, .airline. What is the main idea of the text? ICANN ICANN members ICANN's next international conference *new domain extensions 33. A new batch of domain extensions would open the field for businesses and consumers who have been shut out of the 'com' web land. Based on negotiations among ICANN members , there ultimately could be many more extension. No final decisions have been made-ICANN is expected to debate this is sue at its next international conference- but new extensions under consideration include .biz, .firm, .shop, .airline. What dose BATCH mean in this text? collection *roup or set use registration 34. Cyber squatters only have to pay $35 for a domain name and the return on a $35 investment can range hundreds to thousands- and sometime even millions- of dollars, depending on the buyer. A trio of cyber squatters made headlines last year when they tried to sell barrydiller.Com for $10 million. But rather than pay, USA Networks CEO Barry Diller took them to court and won. How much did Barry Diller pay for 'barrydiller.com'? *$0 $10m $35 thousands 35. Cyber squatters only have to pay $35 for a domain name and the return on a $35 investment can range hundreds to thousands- and sometime even millions- of dollars, depending on the buyer. A trio of cyber squatters made headlines last year when they tried to sell barrydiller.Com for $10 million. But rather than pay, USA Networks CEO Barry Diller took them to court and won. How much does a domain name cost? $1000 $100 $10 *$35 36. Viruses can enter a PC through files from disks, the internet or bulletin board systems. If you want to protect your system, don't open e-mail attachments from strangers and take care when downloading files from the web. What dose the writer advise us to do to avoid viruses? *never open email attachments from a person you do not know never download files from the internet never use removable disks without scanning you do not know never join a bulletin board system 37. To protect crucial data, companies hire security consultants who analyze the risks and provide security solutions. The most common methods of protection are access control, encryption and decryption systems, and firewalls. Which of the following are the ways to protect data that people often use? hiring security consultants, using passwords, firewalls and decryption and decryption systems analyzing risks and using password , firewalls and decryption and decryption systems *using password , firewalls and decryption and decryption systems all of the choices are true 38. To protect crucial data, companies hire security consultants who analyze the risks and provide security solutions. The most common methods of protection are access control, encryption and decryption systems, and firewalls. This is an extract from an article about____ crucial *internet security the job of security consultant coding systems 39. pictures are stored and processed in a computer's memory by either of two methods: raster graphics and vector graphics. Raster-type graphics maintain an image as a matrix of independently controlled dots, while vector graphics maintain it as a collection of points, lines, and arcs. Raster graphics are now the domain computer graphics technology Which type of graphics is more popularly used nowadays? *raster graphics vector graphics the one that uses points and lines the one that uses dots and arcs 40. pictures are stored and processed in a computer's memory by either of two methods: raster graphics and vector graphics. Raster-type graphics maintain an image as a matrix of independently controlled dots, while vector graphics maintain it as a collection of points, lines, and arcs. Raster graphics are now the domain computer graphics technology What is the text mainly about? *how pictures are stored and processed a prospect for raster graphics dominant computer graphics technology the similarity between raster and vector graphics. 41. a computer-graphics system basically consists of a computer to store and manipulate images, a display screen, various input and output devices, and a graphics software package, i.e. a program that enables a computer to process graphics images by means of mathematical language. these program enable the computer to draw, colour, shade, and manipulate the images held in its memory. What can users do with a graphics package? store images process mathematical language. *draw pictures or images hold images in memory 42. a computer-graphics system basically consists of a computer to store and manipulate images, a display screen, various input and output devices, and a graphics software package, i.e. a program that enables a computer to process graphics images by means of mathematical language. these program enable the computer to draw, colour, shade, and manipulate the images held in its memory. What is a graphics package? devices storing and manipulating images input and output devices a mathematical languages *a program enabling computers to process graphics images 43. a computer-graphics system basically consists of a computer to store and manipulate images, a display screen, various input and output devices, and a graphics software package, i.e. a program that enables a computer to process graphics images by means of mathematical language. these program enable the computer to draw, colour, shade, and manipulate the images held in its memory. How many main parts or components needed in a computergraphics system are mentioned in the text? 2 3 *4 6 44.justin Hall, who began eleven years of personal blogging in 1994 while a student at Swarthmore College is generally recognized as one of the earliest bloggers, as is Jerry Pournelle. What can we say about Justin Hall? he's amongst the first people who had a blog he studied at Swarthmore he first blogged in 1994 *all of the choices are right 45.support specialists may write training manuals and train computer users in how to use new computer hardware and software. What are training manuals? *instructions to use computers books on training documents for advertising computers leaflets about computers 46.to create the illusion of movement, an image is displayed o the computer screen then quickly replaced by a new image that is similar to the previous image, but shifted slightly. What does the phrase SHIFTED SLIGHTLY mean? moved a bit *changed a bit changed a lot remained unchanged 47.there are a lot of benefirts from an open system like the internet, but we are also exposed to hackers who break into computer system just for fun, as well as to steal information or propagate viruses.so how do you go about making online transactions secure? What does the word PROPAGATE mean in this text? scan stop clean *spread 48.there are a lot of benefirts from an open system like the internet, but we are also exposed to hackers who break into computer system just for fun, as well as to steal information or propagate viruses.so how do you go about making online transactions secure? What is NOT true about the text? The internet has good side as well as bad side there are three reasons why hackers breaking into computer system our system can be attacked if we are connected to an open system *all hackers want to steal data from the system they break into 49.after a slow star ,blogging rapidly gained in popularity. blog usage the near-simultaneous arrival of the first hosted blog tools such as open diary which was launched in October 1998,soon growing to thousands of online diaries. open diary innovated the reader comment, becoming the first blog community where readers could add comments to other writes' blog entries. According to the passage, which of the following statements is right? people liked blogging from the first time Blog appeared first in1999 *blogging didn't develop well at first blogging was named Open Diary 50. After a slow star, blogging rapidly gained in popularity. Blog usage spread during 1999 and the years following, being further popularized by the near - simultaneous arrival of the first hosed blog tools such as Open diary which was launched in October 1998, soon growing to thousands of online diaries. Open Diary innovated the reader comment becoming the fist blog community where reads could and comments to other writer's blog entries. The phrase � gain in popularity� in the passage means ____. became more and more popular became less and less developed *attracted the attention of few people became attracted by the population 51. After a slow star, blogging rapidly gained in popularity. Blog usage spread during 1999 and the years following, being further popularized by the near - simultaneous arrival of the first hosed blog tools such as Open diary which was launched in October 1998, soon growing to thousands of online diaries. Open Diary innovated the reader comment becoming the fist blog community where reads could and comments to other writer's blog entries. What can be inferred from the passage? *After a slow start, a lot of users liked and supported blogging After a slow start, blogging became popular until 1999 The launching of Open diary made lots of people know about blogging People liked blogging because they could write comments to it 52. However, the evolution of tools to facilitate the production and maintenance of web articles posted in reverse chronological order made the publishing process feasible to a much larger, less technical, population. How are web articles arranged? The oldest entry is followed by others *The latest entry is followed by the less recent Entries are randomly selected to appear Entries are shown according to their page view counts 53. Cyber - squatters only have to pay $35 for a domain name and the return on a $35 investment can range from hundreds to thousands and sometime even millions depending on the buyer. A trio of cyber - squatters made headlines last year when they tried to sell barrydiller.com for $10 million . But rather than pay, USA Networks CEO Barry Diller took them to court and won. Which statement is TRUE? *The fee for registering a domain name $ barrydiller.com 35 Cyber - squatter only have to invest $35 USA Network had to pay $10 million for domain name It is the Cyber - squatters who decide the price of a domain name 54. Cyber - squatters only have to pay $35 for a domain name and the return on a $35 investment can range from hundreds to thousands and sometime even millions depending on the buyer. A trio of cyber - squatters made headlines last year when they tried to sell barrydiller.com for $10 million. But rather than pay, USA Networks CEO Barry Diller took them to court and won. Make headlines' means_____. To make headline for barydiller.com *To be an important item of news in newspapers or on the radio or television To make barrydiller.com famous To be an important item in the Internet 55. Now let's turn our attention to speed. Access times vary from 8ms to 20ms. Access time' or seek time - is the time it takes your read/write heads to find any particular record. You have to distinguish8 clearly between seek time (e.g.20ms) �and data transfer rate� ( the average speed required to transmit data from a disk system to the RAM, e.g. at 20 megabits per second). Remember that the transfer rate also depend on the power o your computer. Which statement is TRUE according to the text? Access time and data transfer rate mean the same Seek time and data transfer rate mean the same *Access time and seek time mean the same Access time is the average time required for the recording 56. Now let's turn our attention to speed. Access times vary from 8ms to 20ms. Access time' or seek time - is the time it takes your read/write heads to find any particular record. You have to distinguish8 clearly between seek time (e.g.20ms) �and data transfer rate� ( the average speed required to transmit data from a disk system to the RAM, e.g. at 20 megabits per second). Remember that the transfer rate also depend on the power o your computer. The access time is always____. Over 20ms Under 8ms 8ms or 20ms *Between 8ms and 20ms 57. The Maltese Amoeba may sound like a cartoon character, but if attacked your computer, you wouldn't be laughing. The Maltese Amoeba is a computer virus. It is a form of software which can �infect� your system and destroy your data. Making computer viruses is only one type of computer crime. Others include hacking ( changing data in a computer without permission) and pirating ( illegally copying software programs). How many types of computer crimes are mentioned is the passage? One Tow *Three Four 58.the Maltese amoeba may sound like a cartoon character but if it attacked your computer you wouldn't be laughing the Maltese amoeba is a computer virus.it is a from of software which can infect your system and destroy your data making computer viruses is only one type of computer crime. others include hacking and pirating( illegally copying software programs). Which one is NOT MENTIONED name of a computer virus *How can a virus work types of computer crimes the definition of computer virus 59, the Maltese amoeba may sound like a cartoon character but if it attacked your computer you wouldn't be laughing the Maltese amoeba is a computer virus.it is a from of software which can infect your system and destroy your data making computer viruses is only one type of computer crime. others include hacking and pirating( illegally copying software programs). Which is NOT TRUER about the text *pirating means legally copying software programs hacking is one type of computer crime computer virus is a form of software which can infect your system and destroy your data when Maltese amoeba attacked your computer your wouldn't be laughing 60. a postscript file consists of two main parts: the prolong which contains a set of subroutines used to from different graphic elements and the script which contains the elements introduced by the user the script calls up the subroutines stored in the subroutines stored in the prolog and adds the parameters for example, if you have drawn a square of 10x5 cm the script calls up the subroutines square and specifies the values 10x5. Which statement is NOT TRUE prolog and script are two main parts of a postscript file *prolong contains different graphic element such as rectangle and curves subroutines used to form different graphic element are stored in the prolog the script calls up the subroutines and adds the parameters 61. a postscript file consists of two main parts: the prolong which contains a set of subroutines used to from different graphic elements and the script which contains the elements introduced by the user the script calls up the subroutines stored in the subroutines stored in the prolog and adds the parameters for example, if you have drawn a square of 10x5 cm the script calls up the subroutines square and specifies the values 10x5. If you want to draw an equilateral triangle of 5cm the script calls up the subroutines____. square and specifies the values 5 square stored in the prolog and adds the parameter 5 *triangle stored in the prolog and add the parameter 5 triangle in the script and specifies the values 5 62. Graphics software programs enable the user to draw colour and shade and manipulate an image on a display screen with command input by a keyboard. What can be inferred from the passage? *the keyboard can be used to input commands we can use the keyboard to draw graphics software can store an image graphics software lets users to manipulate different kinds of texts 63.help-desk technicians deal directly with customer issues and companies value them ass a source of feedback on their products. they are consulted for information about what gives customers the most trouble as well as other customer concerns most computer support specialists start out at the help desk. Help desk technicians���_______. make deals with customers value customers as source of feedback *collect information about customers issues help customers through telephone line 64. help-desk technicians deal directly with customer issues and companies value them ass a source of feedback on their products. they are consulted for information about what gives customers the most trouble as well as other customer concerns most computer support specialists start out at the help desk. According to the passage which one is NOT TRUE about help technicians? they deals directly with the customers they may start their job at the help desk they know customers problems *they value customers 65. They are talking to each other. The very first job of the Internet was to move files from one computer to another even when these computers were very far apart, and Files Transfer protocol was used for this job. If you use the Net just to browse your favorite website, you may not use FTP a lot, but the people who built those websites almost certainly used a FTP program to put the pages on the web in the first place. Which of the following is the best definition of a protocol? The way that a computer talk Something made from FTP A method between two computers *An agreed means of communication 66. one of the earliest bits of the Net is FTP, which stands for Files Transfer Protocol. 'File' and 'transfer' are easy enough to understand, but what is a 'protocol'? Put simply, a protocol is a method that two computer have agreed to use when they are talking to each other. The very first job of the Internet was to move files from one computer to another even when these computers were very far apart, and File Transfer Protocol was used for this job. If you use the Net just to browses your favorite websites, you may not use FTB a lot, but the people who built those website almost certainly used a FTB program to put the pages on the web in the first place. Which of the following sentence is not true according to the passage? You may not use ATP very often if you the internet just to browses your favorite website *The very first job of the Internet was to move files from one computer to another if these computer were not very far apart File Transfer Protocol was used for moving files between computer People use a ATP program to put the pages on the website 67. we all know what e-mail is, but did you know that you usually use two different protocols with it? We usually send mail by SMTP( Simple Mail Transfer protocol) and pick it up, as you might expect by POP ( Post Office Protocol). And yes, the World Wide Web also uses a protocol. The links on a web page that you click to take you to another part � the Net are call ' hypertext links'. Now look at the top of your web page, and you should see 'http://www.english-online.org.uk/'. Http stands for(you guessed it!) Hypertext Transfer Protocol and that 'www' after that show that this page is part of the world wide web. How many protocol dose the text mention? *Three Four Five Six 68. we all know what e-mail is, but did you know that you usually use two different protocols with it? We usually send mail by SMTP( Simple Mail Transfer protocol) and pick it up, as you might expect by POP ( Post Office Protocol). And yes, the World Wide Web also uses a protocol. The links on a web page that you click to take you to another part � the Net are call ' hypertext links'. Now look at the top of your web page, and you should see 'http://www.english-online.org.uk/'. Http stands for(you guessed it!) Hypertext Transfer Protocol and that 'www' after that show that this page is part of the world wide web. How many protocol dose the text mention? At the top of the web page shows that it is part of the world 'www' wide web Http stands for hypertext Transfer Protocol Hypertext links is the links from a web page to another part of the net *http means you guessed it 69. we all know what e-mail is, but did you know that you usually use two different protocols with it? We usually send mail by SMTP( Simple Mail Transfer protocol) and pick it up, as you might expect by POP ( Post Office Protocol). And yes, the World Wide Web also uses a protocol. The links on a web page that you click to take you to another part � the Net are call ' hypertext links'. Now look at the top of your web page, and you should see 'http://www.english-online.org.uk/'. Http stands for(you guessed it!) Hypertext Transfer Protocol and that 'www' after that show that this page is part of the world wide web. How many protocol are used to send an email? *One Two Three Four 70. we all know what e-mail is, but did you know that you usually use two different protocols with it? We usually send mail by SMTP( Simple Mail Transfer protocol) and pick it up, as you might expect by POP ( Post Office Protocol). And yes, the World Wide Web also uses a protocol. The links on a web page that you click to take you to another part � the Net are call ' hypertext links'. Now look at the top of your web page, and you should see 'http://www.english-online.org.uk/'. Http stands for(you guessed it!) Hypertext Transfer Protocol and that 'www' after that show that this page is part of the world wide web. Which of the following statement is true? You use Http to send an email You use SMTP and POP to send an email *You use SMTP to send an email You use two different protocols to send an email 71. A blog is website in which items are posted on a regular basis and displayed in reverse chronological order. The term blog is a shortened from of web log, maintaining a blog or adding an article to an existing blog is called 'blogging'. Individual articles on a blog are called 'blog post', 'posts' or 'entries'. A person who posts these entries is called a 'blogger'. 'blog' can also be used as a verb, meaning to maintain or add content to a blog. Blogs use a conversational style of document. Often blogs focus on particular area of interest s, such as Washington D.C.'s political going-on. Some blogs discuss personal experiences. Blog definition and related term *What is a blog? Blog definition and uses Blog definition and topics 72. A blogs is a website in which items are posted on a regular basis and displayed in reverse chronological order. The term blog is a shortened form of weblog or web log .Authoring a blog, maintaining a blog or adding an article to an existing blog is called 'blogging'. Individual articles on a blog are called 'blog posts', 'posts', or 'entries'. A person who posts these entries is called a 'blogger'. 'Blog' can also be used as a verb, meaning to maintain or add content to a blog. Blogs conversational style documentation. often blogs focus on particular ' area of interest', such as Washington D.C.'s political goings-on. Some blogs discuss personal experiences. Which of the following is NOT mentioned in the paragraph? Blog's related terms *types od blog blog's is topics blog definiton 73. A blogs is a website in which items are posted on a regular basis and displayed in reverse chronological order. The term blog is a shortened form of weblog or web log .Authoring a blog, maintaining a blog or adding an article to an existing blog is called 'blogging'. Individual articles on a blog are called 'blog posts', 'posts', or 'entries'. A person who posts these entries is called a 'blogger'. 'Blog' can also be used as a verb, meaning to maintain or add content to a blog. Blogs conversational style documentation. often blogs focus on particular ' area of interest', such as Washington D.C.'s political goings-on. Some blogs discuss personal experiences. Which of the following statement is NOT TRUE? Blog can be used as a verb blog is short form of weblog Blog can be used as a noun *Blog can be used as an adverb 74. A blogs is a website in which items are posted on a regular basis and displayed in reverse chronological order. The term blog is a shortened form of weblog or web log .Authoring a blog, maintaining a blog or adding an article to an existing blog is called 'blogging'. Individual articles on a blog are called 'blog posts', 'posts', or 'entries'. A person who posts these entries is called a 'blogger'. 'Blog' can also be used as a verb, meaning to maintain or add content to a blog. Blogs conversational style documentation. often blogs focus on particular ' area of interest', such as Washington D.C.'s political goings-on. Some blogs discuss personal experiences. Items displayed in reverse chronological order means_______. *events arranged in reverse order in which they happened Items arranged in chronological order in which they happened Items displayed upside down events arranged in the order in which they happened 75. A blogs is a website in which items are posted on a regular basis and displayed in reverse chronological order. The term blog is a shortened form of weblog or web log .Authoring a blog, maintaining a blog or adding an article to an existing blog is called 'blogging'. Individual articles on a blog are called 'blog posts', 'posts', or 'entries'. A person who posts these entries is called a 'blogger'. 'Blog' can also be used as a verb, meaning to maintain or add content to a blog. Blogs conversational style documentation. often blogs focus on particular ' area of interest', such as Washington D.C.'s political goings-on. Some blogs discuss personal experiences. which of the following statement is true? Articles on a blog are called ' blogging' Blog always focus on a particular 'are of interest' *author of a blog is called a 'blogger' Posting articles into a blog is called 'posts' 76.viruses are programs which are written deliberately to damage data. viruses can hide themselves in a computer system. Some viruses are fairly harmless. They may flash a message on screen, such as ' gotcha! bet you don't know how i crept in'. The Yankee Doodle virus plays this American tune on the computer's small internal speaker every eight days at 5 p.m. Others have serious effects. They attach themselves to the operating system and can wipe out all your data or turn it into gobbledygook. When the Cascade virus attacks, all the letters in a file fall into a heap at the bottom of the screen. This looks spectacular but it's hard to see the funny side when it's your document. Others' refers to_____. Other message *other viruses other programs other tunes 77. viruses are programs which are written deliberately to damage data. viruses can hide themselves in a computer system. Some viruses are fairly harmless. They may flash a message on screen, such as ' gotcha! bet you don't know how i crept in'. The Yankee Doodle virus plays this American tune on the computer's small internal speaker every eight days at 5 p.m. Others have serious effects. They attach themselves to the operating system and can wipe out all your data or turn it into gobbledygook. When the Cascade virus attacks, all the letters in a file fall into a heap at the bottom of the screen. This looks spectacular but it's hard to see the funny side when it's your document. which of the following statement is true? *The Cascade can turn your into gobbledygook All viruses have serious effects on your computers The Yankee Doodle flashes a message on screen Some viruses are totally harmless 78. viruses are programs which are written deliberately to damage data. viruses can hide themselves in a computer system. Some viruses are fairly harmless. They may flash a message on screen, such as ' gotcha! bet you don't know how i crept in'. The Yankee Doodle virus plays this American tune on the computer's small internal speaker every eight days at 5 p.m. Others have serious effects. They attach themselves to the operating system and can wipe out all your data or turn it into gobbledygook. When the Cascade virus attacks, all the letters in a file fall into a heap at the bottom of the screen. This looks spectacular but it's hard to see the funny side when it's your document. Which of the following statement is true? *The Yankee Doodle virus activates at 5 p.m every eight days The Yankee doodle virus plays this American tune on the computer's small internal speaker every days at 5p.m the Cascade can wipe out all your data When the Cascade virus attacks you are funny because the screen looks spectacular 79. A PostScript file consists of two main parts: the 'prolog' which contains a set of subroutines used to form different graphic elements (rectangles, curves, etc�), and the script, which contains the elements introduced by the user. The script calls up the subroutines stored in the prolog and adds the parameters: for example, if you have drawn a square of 10x5 cm, the script calls up the subroutine Square and specifies the values 10x5. Which of the following statement is Not True? Prolog and script are two main parts of a Postscript file Subroutines used to form different graphic elements are stored in the prolog *Prolog contains different graphic elements such as rectangles and curves The script calls up the subroutines ands the parameters. 80. . A PostScript file consists of two main parts: the 'prolog' which contains a set of subroutines used to form different graphic elements (rectangles, curves, etc�), and the script, which contains the elements introduced by the user. The script calls up the subroutines stored in the prolog and adds the parameters: for example, if you have drawn a square of 10x5 cm, the script calls up the subroutine Square and specifies the values 10x5. If you want to draw an equilateral triangle of 5cm the script calls up the subroutines _____. Triangle in the script and specifies the values 5 Square stored in the prolog and adds the parameter 5 Square and specifies the values 5 *Triangle stored in the prolog and adds the parameter 5 81. Graphics software program enable the user to draw, colour and shade; and manipulate an image on a display screen with commands input by a keyboard. What can be inferred from the passage? *The keyboard can be used to input commands Graphics software lets user to manipulate different kinds of texts Graphics software can store an image We can use the keyboard to draw 82. Project managers develop requirements, budgets, and schedules for their firms' information technology projects. They coordinate such projects from development through implementation, working with internal and external clients, vendors, consultants, and computer specialists. These managers are increasingly involved in projects that upgrade the information security of an organization. Project managers in IT often responsible for_____. Being involved in projects Upgrade the information security of an organization Coordinating the different projects *Developing requirements, budgets, and schedules for their firms' information technology projects. 83. when buying a hard disk you should considers the kinds of drive mechanisms and products available. There are 'internal' and 'external' drives which are bots fixed hard drive, i.e. rigid disks sealed into the drive unit, either within or attached to the computer. A third type of hard drive, known as 'removable', allows in formation to be recorded on 'cartridges', which can be removed and stored off-line for security purposes. Popular removable hard disks include Jaz and Zip drives. A Jaz cartridge can store up to 2 GB of data, whereas a Zip drive can store up to 250 MB of data. How many factors should you consider when buying a hard disk? One *Two Three Four 84. when buying a hard disk you should considers the kinds of drive mechanisms and products available. There are 'internal' and 'external' drives which are bots fixed hard drive, i.e. rigid disks sealed into the drive unit, either within or attached to the computer. A third type of hard drive, known as 'removable', allows in formation to be recorded on 'cartridges', which can be removed and stored off-line for security purposes. Popular removable hard disks include Jaz and Zip drives. A Jaz cartridge can store up to 2 GB of data, whereas a Zip drive can store up to 250 MB of data. How many types of hard drives are ment ioned in the passage? One Two *Three Four 85. when buying a hard disk you should considers the kinds of drive mechanisms and products available. There are 'internal' and 'external' drives which are bots fixed hard drive, i.e. rigid disks sealed into the drive unit, either within or attached to the computer. A third type of hard drive, known as 'removable', allows in formation to be recorded on 'cartridges', which can be removed and stored off-line for security purposes. Popular removable hard disks include Jaz and Zip drives. A Jaz cartridge can store up to 2 GB of data, whereas a Zip drive can store up to 250 MB of data. Which type of hard disk can be stored off-line for security puposes? *Removable Cartridges external internal 86.As your e-mail message travels across the net, it is copied temporarily on many computers in between. This means it can be read by unscrupulous people who illegally enter computer systems. The only way to protect a message is to put it in a sort of' envelope' , that is, to encode it with some form of encryption. A system designed to send e-mail privately is Pretty Good Privacy, a freeware program written by Phil Zimmerman According to the passage, which statement is NOT TRUE? Using encryption to make your message safer online. A kind of 'envelope' is used for your message. *You can send messages securely through the net Your e-mail messages travels through the net 87 As your e-mail message travels across the net, it is copied temporarily on many computers in between. This means it can be read by unscrupulous people who illegally enter computer systems. The only way to protect a message is to put it in a sort of' envelope' , that is, to encode it with some form of encryption. A system designed to send e-mail privately is Pretty Good Privacy, a freeware program written by Phil Zimmerman. The word 'it' in the passage is referred to�����_____. The envelope Encryption The form *E-mail-message 88. As your e-mail message travels across the net, it is copied temporarily on many computers in between. This means it can be read by unscrupulous people who illegally enter computer systems. The only way to protect a message is to put it in a sort of' envelope' , that is, to encode it with some form of encryption. A system designed to send e-mail privately is Pretty Good Privacy, a freeware program written by Phil Zimmerman. What can be referred from the passage ? Using 'envelope' is the safest way to protect your message *Your messages through the net are sometimes exposed to others Most of Internet users are illegally It is very sending e-mail through the Internet 89. private networks connected to the Internet can be attacked by intruders who attempt to take valuable information such as Social Security numbers, bank account or research and business reports. To protect crucial data, companies hire security consultants who analyze the risks and provide security solutions. The most common methods of protection are password for access control, encryption and decryption system, and firewalls. How many ways to protect private networks are mentioned in the passage? One Two *Three four 90. Security is crucial when you send confidential information online. Consider, for example, the process of buying a book on the web. You have to type your credit card number into an order form which passes form computer to computer on its way to the online book store. If one of the intermediary computer is infiltrated by hacker, you data can by copied. Which of the following does the passage imply? You have to use credit card buying online. Someone might copy your data when you send it on the Internet. You can visit a book store online. *You should pay attention when sending important data online. 91. There are many benefits form an open system like the Internet, but one of the ricks is that we are often exposed to hackers, who break into computer system just for fun, to steal information, or to spread viruses. Which of the following is NOT TRUE about the passage? People can get both the good side as well as the bad side of the Internet. The Internet is an open system. *Hackers do no harm on the Internet. People who break into computer system are called hackers. 92. Publishing has existed in its current form for centuries. Ever since paper was first invented, human being have found ways of using it to pass on message to each other. Book, magazines, and newspapers are now part of our everyday lives, but with invention of the Internet and the speed of new technological advances, the word of publishing is changing. Online newspapers and magazines, blogs, and even e-book are changing the way we get information. Which of the following is TRUE about the passage? Paper publication is the only way of getting information for users. *Online publishing have great effect towards the way people get information. Books, newspapers and magazines are sold online. The Internet hasn't made any change in the world of publishing. 93. The only language a PC can directly execute is machine code, which is consists of 1s or 0s. This language is difficult to write, so we use symbolic languages that are easier to understand. For example, assembly languages use abbreviations such as ADD, SUB, and MPY to represent instructions. The program is then translated into machine code by software called an assembler. Which of the following is NOT TRUE according to the passage? *People easily understand machine code. Programmers use abbreviation to write instruction. An assembler translates symbolic languages into machine code. Machine code is a kind of computer languages consists of 1s and 0s. 94. The only language a PC can directly execute is machine code, which is consists of 1s or 0s. This language is difficult to write, so we use symbolic languages that are easier to understand. For example, assembly languages use abbreviations such as ADD, SUB, and MPY to represent instructions. The program is then translated into machine code by software called an assembler. Which of the following is TRUE according to the passage? An assembler is used to translate machine code into normal language. Machine code is the language that people can understand. *It's not easy for programmers to write machine code. People can't understand symbolic languages. 95.You don't need a sophisticated cell phone to surf the Internet when you are on the road just your own voice. That's the idea behind a new breed of voice service that is popping up all over the place. Subscribers dial a toll-free phone number and use spoken commands to listen to anything from weather conditions to stock quotes, or flight information to news stories. Which of following is TRUE about the passage? People can use any phone surf web. People can't get news when they are driving. People don't have to subscribe to voice services but they still use them. *People can use their voice to start a program. 96. You don't need a sophisticated cell phone to surf the Internet when you are on the road just your own voice. That's the idea behind a new breed of voice service that is popping up all over the place. Subscribers dial a toll-free phone number and use spoken commands to listen to anything from weather conditions to stock quotes, or flight information to news stories. The word 'toll-free' in passage is closest to ___. *no charge a lot of money no service smart 97. The basic equipment has changed drastically in the last few years. You no longer need a computer to use the Internet. Web TV provides email and access to the Web via normal TV set plus a high-speed modem. More recently, 3-Generation mobile phones and PDAs, personal digital assistants, also allow you to go online with wireless connection, with cables. Which of the following is NOT TRUE about the passage? The basic equipment is changing quickly these days. People can use Web TV to surf the Internet. *You must have a computer to access the Internet nowadays. You can connect webs through a 3-G mobile. 98. The basic equipment has changed drastically in the last few years. You no longer need a computer to use the Internet. Web TV provides email and access to the Web via normal TV set plus a high-speed modem. More recently, 3-Generation mobile phones and PDAs, personal digital assistants, also allow you to go online with wireless connection, with cables. According to the passage, to the Internet, you don't need to have ___. *a computer a PDA a modem a mobile phone 99. The basic equipment has changed DRASTICALLY in the last few years. You no longer need a computer to use the Internet. Web TV provides email and access to the Web via normal TV set plus a high-speed modem. More recently, 3-Generation mobile phones and PDAs, personal digital assistants, also allow you to go online with wireless connection, with cables. The word 'drastically' in the passage is closest to ___. lightly slowly *extremely freely 100. If you want to protect your PC, don't open email attachments from strangers and take care when downloading files from th Web. Remember to update you're anti-virus software as open as possible, since new viruses are being created all the time. Which of the following is NOT TRUE about the passage? user should protect their computer carefully *open whatever e-mail attachments you get update the latest anti-virus regularly New viruses are born every time 101. Kevin Mitnick, a legend among hackers, began hacking into banking networks and altering the credit reports of his enemies. He didn't expect that his most famous exploit hacking into North American Defense Command in Colorado Springs - would inspire the film War Games in 1983. Which of the following is TRUE about Kevin Mitnick? He is a computing legend He stole all the credits reports in bank networks *Film directors got inspiration from his work The film War Games was on display in 1983 102. In modern commercial printing, DTP files output directly to the printing plates without using film as an intermediate step. This new technology is known as Computer-to-Plate (CTP) or direct to plate, and the machine that generates plates for a printing press is called plate-setter. CTP machines are expensive, so most people take their files to a service bureau, a company that specializes in printing other people's files. Service bureaus offer a full range of scanning and printing solutions. According to the passage, people _____use film when printing DTP files. have to *don't have to must can 103. In modern commercial printing, DTP files output directly to the printing plates without using film as an intermediate step. This new technology is known as Computer-to-Plate (CTP) or direct to plate, and the machine that generates plates for a printing press is called plate-setter. CTP machines are expensive, so most people take their files to a service bureau, a company that specializes in printing other people's files. Service bureaus offer a full range of scanning and printing solutions. Which of the following is TRUE about the passage? CTP isn't a new technique in modern printing Everyone can print DTP files using CTP machines Plate-setter can print DTP files *A service bureau is one kind of printing companies 104. Audio is becoming a key element of the Web. Many radio stations broadcast live over the Internet using streaming audio technology, which lets you listen to audio in a continuous stream while it is being transmitted. The broadcast of an event over the Web, for example a concert, is called a webcast. Be aware that you won't be able to play audio and video on the Web unless you have a plug-in like RealPlayer or QuickTime. What can be inferred from the passage? People have to make a clip before they want to broadcast on the Internet *Some small program are needed to play audio or video on the Web Audio cannot transmitted over the Internet You won't be able to play audio or video on the Web 105. Audio is becoming a key element of the Web. Many radio stations broadcast live over the Internet using streaming audio technology, which lets you listen to audio in a continuous stream while it is being transmitted. The broadcast of an event over the Web, for example a concert, is called a webcast. Be aware that you won't be able to play audio and video on the Web unless you have a plug-in like RealPlayer or QuickTime. Which of the following is TRUE about the passage? You won't be able to play audio or video on the Web It's not easy to transmit audio over the Internet A plug-in effects badly to the Web *A webcast is an event which you can listen to or watch on the Internet 106. If you want to inject something special into your web pages, you can use Adobe Flash to include interactive animations and streaming audio. Additionally, you can insert Java applets - small programs that enable the creation of interactive files. Animations are made up of a series of independence picture put together in sequence to look like moving pictures. To see or hear all these files, you must have the right plug-in, an auxiliary program that expands the capabilities of your web browser. What is the function of Java program? Streaming audio over the Internet *Providing interactive features to web applications Integrating with plug-in programs Expanding the abilities of web browsers 107. If you want to inject something special into your web pages, you can use Adobe Flash to include interactive animations and streaming audio. Additionally, you can insert Java applets - small programs that enable the creation of interactive files. Animations are made up of a series of independence picture put together in sequence to look like moving pictures. To see or hear all these files, you must have the right plug-in, an auxiliary program that expands the capabilities of your web browser. The word 'auxiliary' in the passage is closest to____. *additional exceptional further special 108. It is important not to confuse programming languages with markup languages, used to create web documents. Markup languages use instructions, known as markup tags, to format and link text files. Which of the following is TRUE about the passage? Programming languages are very confusing *Programming languages and markup languages are not the same There aren't any differences between programming languages and markup languages Markup languages are used to create web documents 109. Visual Basic was developed by Microsoft in 1990. The name BASIC stands for Beginner's All-purpose Symbolic Instruction Code. The adjective Visual refers to the technique used to create a graphical user interface. Instead of writing a lot of instructions to describe interface elements, you just add pre-defined objects such as buttons, icons and dialog boxes. It enables programmers to create a variety of Windows applications. Which of the following is NOT TRUE about the passage? Visual Basic was generated in 1990 Visual Basic helps programmers create Windows applications *In Visual Basic, programmers have to write a lot of instructions to describe interface elements In Visual Basic, programmers use a lot of pre-defined objects to describe interface elements. 1.Java is an object-oriented language, similar to C + +, but more dynamic and simplified to eliminate possible programming errors. A Java program is both compiles and interpreted. First, the source code is compiled and converted into a format called bytecode, which can then be executed by a Java interpreter.[cr]The word in bold in the passage is closest to: A.attractive *B. active C. interesting D. compatible 2.Java is an object-oriented language, similar to C + +, but more dynamic and simplified to eliminate possible programming errors. A Java program is both compiles and interpreted. First, the source code is compiled and converted into a format called bytecode, which can then be executed by a Java interpreter.[cr]The word in bold in the passage is closest in meaning to: A.remove B. take away C. cancel *D. All are correct 3.Most programmers like Java because it allows them to write applets which make web pages moreinteractive and attractive. They can create graphic objects (for example, bar charts and diagrams) and new controls (for example, check boxes and push buttons with special properties). A web page that uses Java can have sounds that play in real time, music that plays in the background, cartoon-style animations, real-time video and interactive games.[cr]Which of the following can be used as the heading of the paragraph? A. The Java language B.Characteristics of the Java language *C.Why is Java popular? D.Alternatives to Java 4.Most programmers like Java because it allows them to write applets which make web pages more interactive and attractive. They can create graphic objects (for example, bar charts and diagrams) and new controls (for example, check boxes and push buttons with special properties). A web page that uses Java can have sounds that play in real time, music that plays in the background, cartoon-style animations, real�time video and interactive games.[cr]The word in bold in the passage is closest in meaning to: A. advents *B. check/ supervision C. attention D. manipulations 5.Most programmers like Java because it allows them to write applets which make web pages more interactive and attractive. They can create graphic objects (for example, bar charts and diagrams) and new controls (for example, check boxes and push buttons with special properties). A web page that uses Java can have sounds that play in real time, music that plays in the background, cartoon-style animations, real�time video and interactive games.[cr]The word in bold in the passage is closest to: A. real estates B. realties *C. attributes D. animations 6.Most programmers like Java because it allows them to write applets which make web pages more interactive and attractive. They can create graphic objects (for example, bar charts and diagrams) and new controls (for example, check boxes and push buttons with special properties). A web page that uses Java can have sounds that play in real time, music that plays in the background, cartoon-style animations, real�time video and interactive games.[cr]Which of the following is NOT TRUE about the passage? A.Bar charts and diagrams are graphic objects in a web page using Java. B.Interactive games can run in web pages that use Java. C.Thanks to Java, programmers can play music in the background of a web page. *D.Phones are configured to use Java games with animations and music in the background. 7.Most programmers like Java because it allows them to write applets which make web pages more interactive and attractive. They can create graphic objects (for example, bar charts and diagrams) and new controls (for example, check boxes and push buttons with special properties). A web page that uses Java can have sounds that play in real time, music that plays in the background, cartoon-style animations, real�time video and interactive games.[cr]How many new controls are mentioned in the passage? A. one *B. two C.three D. four 8.Senior Programmer required by DigitumUK, a leading supplier of business systems to the insurance industry. You will be able to work on the full range of software development activities - analysis, design, coding, testing, debugging and implementation.[cr]The word in bold in the passage is closest in meaning to: A.ordinary B. normal *C.best D. minor 9.Senior Programmer required by DigitumUK, a leading supplier of business systems to the insurance industry. You will be able to work on the full range of software development activities - analysis, design, coding, testing, debugging and implementation.[cr]The word in bold in the passage is closest to: A.field B. area C.sphere *D. All are correct 10.Senior Programmer required by DigitumUK, a leading supplier of business systems to the insurance industry. You will be able to work on the full range of software development activities - analysis, design, coding, testing, debugging and implementation.[cr]Which of the following is the passage about? *A.A job advert for a senior programmer. B.DigitumUK is a leading supplier of business system to the insurance industry. C.You can work as a software engineer. D.You need to develop the software. 11.it We are looking for a bright, competent QuarkXPress operator with at least three years� experience in design and layout. Skills in Photoshop, Freehand or Illustrator an advance. Ability to work in a team and to tight deadline is vital.[cr]The word in bold in the passage is closest to: A. proficient *B.competitive c. handsome D. nice 12.We are looking for a bright, competent QuarkXPress operator with at least three years� experience in design and layout. Skills in Photoshop, Freehand or Illustrator an advance. Ability to work in a team and to tight deadline is vital.[cr]Which of the following years of experience in design and layout is best suitable for the requirement? A. 0 B.1 c.2 *D.4 13.We are looking for a bright, competent QuarkXPress operator with at least three years� experience in design and layout. Skills in Photoshop, Freehand or Illustrator an advance. Ability to work in a team and to tight deadline is vital.[cr]Which of the following is NOT MENTIONED in the passage? *A.The QuarkXPress operator with three years experience has a high salary. B.The candidate needs to be excellent in Photoshop, Freehand or Illustrator, c. The candidate is capable of working in group D.The candidate can be able to finish work under pressure of time. 14.In recent years, TV and radio broadcasting has been revolutionized by developments in satellite and digital transmission. Digital TV is a way of transmitting pictures by means of digital signals, in contrast to the analogue signal used by traditional TV.[cr]The word in bold in the passage is closest in meaning to: A. assist B.emit *c. reform / change D.receive 15.In recent years, TV and radio broadcasting has been revolutionized by developments in satellite and digital transmission. Digital TV is a way of transmitting pictures by means of digital signals, in contrast to the analogue signal used by traditional TV.[cr]The word in bold in the passage is closest to: *A. by B.for c. because of D.according to 16.In recent years, TV and radio broadcasting has been revolutionized by developments in satellite and digital transmission. Digital TV is a way of transmitting pictures by means of digital signals, in contrast to the analogue signal used by traditional TV.[cr]The word in bold in the passage is closest to: *A.in opposition to B. compare with c. similar to D.similar with 17.In recent years, TV and radio broadcasting has been revolutionized by developments in satellite and digital transmission. Digital TV is a way of ?ansmitting pictures by means of digital signals, in contrast to the analogue signals used by traditional TV.[cr]Which of the following is NOT MENTIONED in the passage? A. Digital transmission changes radio broadcasting recently. *B.Digital TV provides a better quality of picture and sound, c. Digital signals are used to transmit pictures on digital TV. D.Traditional TV uses analogue signals to transmit pictures. 18.The use of GPS in cars and PDAs is widespread, so you can easily navigate in a foreign city or find the nearest petrol station. In the next few years, GPS chips will be incorporated into most of mobile phones.[cr]The word in bold in the passage is closest in meaning to: A.limited B.local c.narrow *D. popular 19.The use of GPS in cars and PDAs is widespread, so you can easily navigate in a foreign city or find the nearest petrol station.[cr]Which of the following does the passage IMPLY? A.You can find a foreign city easily. B.It takes a little time for you to find a gas station, c. There is always a petrol station around you. *D.Wherever you are, with GPS, you can�t be lost. 20.The use of GPS in cars and PDAs is widespread, so you can easily navigate in a foreign city or find the nearest petrol station. In the next few years, GPS chips will be incorporated into most of mobile phones.[cr]Which of the following is NOT TRUE about the passage? A.Cars and PDAs are popularly equipped with GPS. B.With GPS, you can easily navigate in a strange city. C.GPS chips will be embedded in most of cell phones in the near future. *D.Mobile phones are equipped with GPS nowadays. 21.It is important that you remember to log off after using the Internet. An open line increases the risk of viruses, and hackers might break into your computer to steal confidential data.[cr]The word in bold in the passage is closest to: A. safety B. security *C. danger D. truth 22.It is important that you remember to log off after using the Internet. An open line increases the risk of viruses, and hackers might break into your computer to steal confidential data.[cr]The word in bold in the passage is closest to: A. secret B. private C. intimate *D. All are correct 23.It is important that you remember to log off after using the Internet. An open line increases the risk of viruses, and hackers might break into your computer to steal confidential data.[cr]Which of the following is the main idea of the passage? *A.You need to exit the line on the Internet to avoid the dangers of viruses and hackers. B.Viruses exist on the Internet C.Hackers can steal your private data. D.All are correct 24.Wireless networks let you move, roam, from one access point to another, but they are less secure and subject to interference.[cr]The word in bold in the passage refers to: *A. Wireless networks B. you C. one access point D. another access point 25.Wireless networks let you move, roam, from one access point to another, but they are less secure and subject to interference.[cr]The word in bold in the passage is closest to: A. backup B. accommodation C. circulation *D. intervention 26.In a client-server network, a computer acts as a server and stores and distributes information to the nodes, or clients.[cr]The word in bold in the passage is closest to: A. build *B.dispense C. raise D. communicate 27.In a peer-to-peer network, all the computers have the same capabilities - that is, share files and peripherals without requiring a separate server computer.[cr]The word in bold in the passage is closest to: A. mobility B.relay *C. ability to perform D. extract 28.A lot of modem games certainly draw inspiration from films and even TV. You can see it in the look of the characters, the sound of the dialogue, and in even more artistic elements such as lighting and camera work.[cr]The word in bold in the passage is closest to? A. picture B.sense *C. genius D. view 29.A lot of modem games certainly draw inspiration from films and even TV. You can see it in the look of the characters, the sound of the dialogue, and in even more artistic elements such as lighting and camera work.[cr]The word in bold in the passage is closest to? A. to see or to watch *B. the appearance C.glance D. glimpse 30.A lot of modem games certainly draw inspiration from films and even TV.You can see it in the look of the characters, the sound of the dialogue, and in even more artistic elements such as lighting and camera work.[cr]Which of the following is the passage about? *A.Many modem games are influenced by films and TV. B.The characters are beautiful. C.Characters make dialogues. D.The lighting and camera work are artistic. 31.The use of A-list Hollywood actors to provide voice work in games is no coincidence either and is a good example of the two media coming together.[cr]The words in bold in the passage refers to: A.the alphabet *B.famous C.a list of A D.a series 32The use of A-list Hollywood actors to provide voice work in games is no coincidence either and is a good example of the two media coming together.[cr]Which of the following is TRUE about the passage? *A.Well-known Hollywood actors dub in video games. B.Well-known Hollywood actors appear in video games. c. Hollywood actors� appearance in video games is no coincidence. D.Hollywood actors appear in video games by accident. 33.TV and video games are amusing and can be educational. But too much of this kind of entertainment can be addictive and make children become accustomed to violence.[cr]What does �this kind of entertainment� mean? A. TV B.video games *c. TV and video games D. amusing and can be educational 34.TV and video games are amusing and can be educational. But too much of this kind of entertainment can be addictive and make children become accustomed to violence.[cr]Which of the following is the main idea of the passage? A.Video games are not good for children. B.TV and video games can help in education. c. Video games distract children from school and homework. *D.On the one hand, TV and video games are helpful. On the other hand, they make children become familiar with violence. 35.The term Artificial Intelligence originated in the 1940s, when Alan Turing said: �A machine has artificial intelligence when there is no discernible difference between the conversation generated by the machine and that of an intelligent person.�[cr]The word �that� in the passage refers to: A. the machine B. artificial intelligence *c.the conversation D. intelligent person 36.The term Artificial Intelligence originated in the 1940s, when Alan Turing said: �A machine has artificial intelligence when there is no discernible difference between the conversation generated by the machine and that of an intelligent person.�[cr]What does �1940s� in the passage mean? *A. From 1940 to 1949 B. From 1940 to 1950 c. From 1941 to 1950 D. From 1939 to 1950 37.The term Artificial Intelligence originated in the 1940s, when Alan Turing said: �A machine has artificial intelligence when there is no discernible difference between the conversation generated by the machine and that of an intelligent person.�[cr]The word �discernible� in the passage is closest in meaning to: *A. perceptible B. capable c.sensible D. intelligent 38.When you enter the airport, a hidden camera compares the digitized image of your face to that of suspected criminals. At the immigration checkpoint, you swipe a card and place your hand on a small metal surface. The geometry of your hand matches the code on the card, and the gate opens.[cr]The word �hidden� in the passage is closest in meaning to: A. reliable *B. concealed c.expensive D. modem 39.When you enter the airport, a hidden camera compares the digitized image of your face to that of suspected criminals. At the immigration checkpoint, you swipe a card and place your hand on a small metal surface. The geometry of your hand matches the code on the card, and the gate opens.[cr]The word �that� in the passage refers to: A. the airport B. the hidden camera *c.the digitized image D. your face 40.When you enter the airport, a hidden camera compares the digitized image of your face to that of suspected criminals. At the immigration checkpoint, you swipe a card and place your hand on a small metal surface. The geometry of your hand matches the code on the card, and the gate opens.[cr]The phrase �immigration checkpoint� in the passage refers to: A. immigration B. immigration control c.reception *D. A & B are correct 41.When you enter the airport, a hidden camera compares the digitized image of your face to that of suspected criminals. At the immigration checkpoint, you swipe a card and place your hand on a small metal surface. The geometry of your hand matches the code on the card, and the gate opens.[cr]The word �matches� in the passage means: A.short pieces of wood used for lighting a fire B. contestes *c. to combine well with D. to give in marriage Gammar 1.Dot matrix printers are noisy, ___ laser printer are quiet. so because there for *but 2.Graphics software programs enable the user ___ an image on a display screen with commands input by s keyboard. manipulate manipulating *to manipulate to manipulating 3.Images on paper ___ into the computer through the use of scanners, digitizers, patternrecognition devices, or digital cameras. *can be scanned can scan can be scan can scanned 4.Various output devices such as image-setters or film recorders___recently. has been developed *have been developed have developed has developed 5.Pictures___in a computer's momory by either of two methods: raster graphics and vector graphics. *are stored and processed store and process is stored and processed are storing and processing 6.This technique is identical ___ how the illusion of movement is achieved with television and motion pictures. for with of *to 7.___ security for online banking services, most banks use digital certificates. assure *to assure Assuring to assuring 8.When an e-mail message travels across the net, it ___ temporarily on many computers in between copies was copied *is copied is copying 9.An extortionist is someone who ___ registers trademarked names. *intentionally intentional intention intend 10.Network and computer systems administrators are responsible ___ local-area networks ( LAN ), wide-area networks (WAN), network segment, and internet and intranet systems. *for to with about 11.They are ___ involved with the upkeep, maintenance, and security of networks. increase increased *increasingly increasing 12.If you close a text file that you are editing, the computer will request ___ the file. to save you to save you save *save 13.There is a message displayed on the screen to tell you ___ to log on. not try not trying to not try *not to try 14.The data bus is bidirectional,___ the address bus is unidirectional. *whereas and although because 15.Early weblogs were simply manually ___ components of common websites. updating were update *update to update 16.In Delphi, the code ___ to the objects is written in a form of Pascal attaches which attaches *which is attached is attached 17.Server is a specia list computer ___ a server to a network. provides provided *providing is provided 18.A network is simply two or more computers ___ together to allow users to share files, software, and hardware. *linked linking are linked are linking 19.Help-desk technicians ___ telephone calls and e-mail messages from customers looking for help with computer problems. have responded to responding responds to *respond to 20.Systems administrators ___ maintaining network efficiency. are responsible for are in charge for are accountable for *all choices are right 21.Network and computer systems administrators ___ local-area networks (LAN), wide-area networks (WAN), network segment, and internet and intranet systems. are in charge with *are in charge of are responsible to are accountable to 22.CIOs are responsible ___ the overall technological direction of their organizations. about with *for to 23.The chief technology officer often ___ the organization's chief information officer. reports for *reports to account to be responsible to 24.Floppy disks store small amounts of data ___ hard disks store large amounts of data *whereas though so and 25.Handheld computers fit into your pocket ___ supercomputers occupy a whole room although because therefore *in contrast 26.High-level languages are easy to understand, ___ machine code is very difficult to understand. so *whereas because even though 27.Basic is a simple language, ___ C++ is complex *but so and nevertheless 28.Modern computers are powerful and relatively cheap ___ older computers were less powerful and quiet expensive in addition according to *in contrast therefore 29.An analyst analyses problems and finds solutions, ___ a programmer turns these solutions into computer programs and *whereas because so 30.A graphics package produces images and designs ___ a word processer produces texts in contrast although so *but 31.___ a printer runs out of paper, an interrupts carries a signal to the CPU if *when after until 32.___ the CPU receives the signal, it interrupts its takes. *when unless after before 33.The CPU sends a message to the user ___ it saves its current status in a special area of memory before until *after as soon as 34.___ the user reloads the paper tray, the processor returns to its previous state if *when unless before 35.___ computers are general purpose instruments, they can be used in many different ways. as well as although so *because 36.Robots inhuman from ___ often featured in Science fiction. *have has are is 37.Robotic arms ___ commonly used for car manufacture, nuclear plants, and for bomb disposal is *are get gets 38.In the future, insect-sized robot micro-machines ( tiny mechanisms built on electronic chips) ___ used as or for doing work in very small spaces which are difficult to access is are is being *may be 39.Insect-sized robot micro-machines may even be used __ the human body for drug delivery, curing common ailments *inside outside in across 40.Virtual reality (VR)___ already___ for games and entertainment are/used *is/used have/used has/used 41.Medical cards, ___ store information about the user's medical history, may become common; and banks are already when where *which that 42.Smart cards are already being used for storing information about the user, for controlling access to facilities, and as a means of providing money __ _ an electronic form. *in by on with 43.Computing is changing and developing ___ a very fast pace by with in *at 44.Videophones, electronic pets, and robots already exist and may become ___ in the future more commonly *more common commoner more commoner 45.postscript is mainly used to ___ the appearance of text, graphics and images on the printed page *describe describing described be described 46.The development of smaller computers and computing networks s making it ____ for computers to be used in more stuations. More easy More easily *Easier Easily 47. It is already necessary ____ some computing skills for most jobs. *To have Have Having Had 48. We will produce students who are not good ____ communicating with others and working as a team In *At On By 49. PostScript war ____ by Adobe Systems, Inc. In 1982 as a page description language for printers. Written Opened Installed *Developed 50. Picture created in PostScript and saved as separate files ( khown as Encapsulated PostScript (EPS) files) can be _____ into a document. Exported *Inported Sored Drawn 51. The CPU sent a message to the user _____ it saves current status in the memory. While Before *After Whereas 52. When buying a hard disk, you _____ consider the kinds of drive mechanisms. *Should Must Have to Can 53. In programming, it is necessary to ____ the coding among a team of program. Divede on Divede to Divede into *Divede up 54. Went the user and the computer are active on communication on a graphics system, we refer to this as ___ active graphics. Dec*InterMicroMulti55. Micro-machines ____ used for drug delivery Is going to Are going to *Are going to be Is going to be 56. Simple programs can be written in a few hours but some programs may _____ more than a year to create. Taken Be talking *Take Taking 57. If a website _____ too long to download, people will _____ and go to other sites. *Takes/ give up Take/ giving up Took/ gave Taking/ giving 58. Modeling refers to the process ____ buiding objects on the computer monitor. At *Of On In 59. It's importan ______ what computer uses you need before ____ one. Define/ buy To define/ buy Define/ buying *To define/ buying 60. The modern blog evoived from the online diary, ____ people would keep a running account of their personal lives. Who What *Where Why 61. The brightness of the resulting image must be ____ 'refreshed' by the beam *Continuously Continuous Continued Continuing 62. He tries to ____ every interesting articles from IT magazines Pick off *Pick up Pick on Pick at 63. Text and graphics are adjusted ____ they all fit well. *Until Before After When 64. After a slow start, blogging rapidly gained ____ popularity. At By *In On 65. Pupils will have access _____ a world of leaning. On *To By With 66. You can avoid ____ the surface of a CD-ROM by _____ it by the edges Marks/ hold To mark/ to hold Marking/ held *Marking/ holding 67. 3D graphics ARE SUITABLE WITH broadband connection. Which one is similar to the CAPITALS? Can go with Accompanied by *Are compatible with Used with 68. _____ we finish a project, we often put a copy of the software as a record. *Whenever In addition On purpose However 69. Thanks to advanced technology, our lives will become _____ Easily and comfortably *Easier and more comfortable Harder and cheaper More difficult and complicated 70. The best way to ____ development in computer science is to subscribe to PC magazines Keep up Keep on Keep up to *Keep uo with 71. Picture _____ in a computer's memory by either of two methods: raster graphics and vector graphics *Are processed Is processing Processing Processed 72. To keep your message safe, you should _____ it with some form of encyption. Encoding *Encode Encoded Be encoded 73. Java is originally designed ____ programming small electronic devices such as mobile phones. Of At To *For 74. He teacher me how ____ some programming languages. Use Used *To use Using 75. He has to ____ some projects on high technology. *Carry out To carry out Be carried out Carrying out 76. Modern computer are lighter and more powerful _____ old computer were quite big and less powerful Therefore Because Nevertheless *Whereas 77. Simple programs can be written in a few hours but some programs may ____ more than a year to create. Talking *Take Taken Be taking 78. People may ____ your website by chance when they are browsing the net. To come across Become across *Come across Coming across 79. Modeling refers to the process ____ building objects on the computer monito. *Of In On At 80. Yoy can protect your computer from viruses by ______ anti-virus program frequently. Run To run *Running Ran 81. The data bus is bidirectional, ______ the address bus is unidirectional. But *Whereas And However 82. CGI is another way people call computer animation which ______ in films. Uses Used Using *Is used 83. It's importan _____ what computer uses you need before _____ one. *To define/ buying To define/ buy Define/ buying Define/ buy 84. We are now familiar ____ the term of ' body chips ' To For *With Within 85. A computer system has two or more cental processors which are under common control, it is called a _____ processor system. What is the right prefix? Mini Micro Mono *Multi 86. Computing technology is likely _____ in popularity today. *To gain Gaining On gaining To gaining 87. 3D graphics _____ suitable with broadband connection. Is *Are Been Being 88. A Jaz cartridge can store up to 2 GB of data, _____ a Zip drive can store up to 250 MB of data. *But Althought However In contrast 89. The brightness of the resulting image must be _____ refreshed by the beam. Continued Continuous *Continuously Continuting 90. To avoid risks, you should set all the security alerts to high ____ your web browser. *On Of In Into 91. He tries to _____ every interesting articles from IT magazines. To pick up *Pick up Picking up Picked up 92. In Delphi, the code attached to the objects _____ in a form of Pascal. Write Wrote Writing *Is written 93. There _____ lots of benefits from an open system like the internet. Is *Are Was Were 94. A blog ______ by a mobile device like a mobile phone or PDA is called a mob log. Written Which is written *Both ' which is written' & ' written are' correct None of the choices is correct 95. Computing is relatively new and is developing _____ an incresingly fast rate. In With *At By 96. JavaScipt can ______ to perform simple tasks or tie other programs together. Use *Be used Be using Uses 97. I usually ____ about JavaScrip but this week I ____ to learn how to use Active Server pages. Learn/ try Learning/ am trying Learning/ trying *Learn/ am trying 98. A rare type of blog hosted on the Gopher Photocol is know____ a Phlog. *As Like Such as For 99. You can get rid ______ logic errors by hand- testing the program. Off *Of On About 100. It is ____ to transfer the rendered animation into another format. Impossible Impossibly *Possible Possibly 101. Doctors will experiment computing technology ______ simulated patients. *On Of In For 102. While your email message travels along the net, it can be read by unscrupulous people who _____ enter the system. illegal *illegally legal legally 103.Mind Mega XT is compatible ______.IBM PCs or Macintosh computer. *with for by of 104.Raster graphics maintains an image as an array of controlled dots."an array of" mean ______ a variety of *a collection of a lot of a type of 105.when you test a progam, different kinds of problem ______ comes up came up *come up is coming up 106.Graphics program enables users ______ the images help in its memory. *to manipulate manipulate manipulated manipulating 107. 3-D virtual reality systems ______ ,the internet to make shopping easier, and smart cards ______ to provide an electronic money system. *can be used on/ may be used can use in/ may use are used in/ can used can being used on/ may be using 108. if your password is simple, someone ______ guess what it is and access your files. should have to must *may 109.it is unusual ______ a program to work properly the first time it's tested. with to *for of 110. there are always some technical assistants ______ on duty at the help desk. *working is working work will work 111. reading about new developments ______ a lot of Colin's free time to take up *takes up take up taking up 112. various output devices ______ recently in computing industry. develop *have been developed developed have developed 113. the technique used in computer animations is identical ______ how the illusion of movement is achieved with television. *to with for of 114.children will ______ communicate directly with experts through the net in the feature. able able to be able *be able to 115.when you are online, you are sometimes exposed to hackers ______ break into your computer system. which *who whom whose 116.the transfer rate depends ______ the power of the computer. *on for of at 117.live connections to classes and lectures will be ______ in the near future. impossible impossibly *impossible possibly 118.we ______ start our websites with abrief piece of information to attract readers must *should have to mustn't 119 I have worked for several IT businesses and ______ for IBM currently. work will work was working *am working 120. you can return to your starting page on the web by ______ the home button. *selecting selected to select select 121 the total number of pixels in which the display ______ both horlizontally and vertically is known as the resolution. divides is dividing required *is divided 122. dot-matrix printers use pins to print the dots ______ to shape a character. to require requiring *required to be required 123.all the features of postscript can ______ with macintosh, windows or os/2 environments. used *be used to use use 124.however, an IC ANN spokesperson suggests______ a domain name from an official registrar so you have a contract and the protections that go with it. bought to buy *buying have bought 125. they are ______ involved with the upkeep, maintenance, and security of networks. *increasingly increasing increased increasable 126.computer and information systems managers do everything from______.to construct a business plan to ______.network security to directing internet operations. help/overseeing *helping/overseeing help/oversee helping/oversee 127.A blog______ by a mobile device like a mobile phone or PDA is called a mob log. written which is written *A&B only B 128.A vertical or horizontal bar at the side or bottom of a window that can be used______ a mouse for moving around in a document. *with in no word on 129. the grandfather, father, son method is one way of______ your document. transmitting sending entering *backing up 130. the computer mouse is a hand-operated device that______ you______ control more easily the location of the pointer on your screen. let/to *lets/x lets/to let/x 131. you can share idea with other internet users______ a subject you're interested in by joining a newgroup. with between *on in 132.you can get rid of logic errors by______ the program. *hand-testing handing-testing test-handing handing 133.the brightness of the resulting image fades quickly, ______,and must be continuously �refreshed� by the beam. then otherwise therefore *however 134.the bill______ by multiplying the number of weeks by the rate. is divided is executed *is calculated is taken 135.the language______ will depend on a number of factors incluing what system the program will run on, what the function of the program is, and the knowledge of the programmer. chose being chosen choosing *chosen 136. the Active Server system______ by the analyst/programmer is a system that allows web pages______.for running small programs on the main server computer on a network. mentioning / using *mentioned / to be used mentioned/to be using mentioning/ to be using 137. in this program the value of total will always be more than 0, and ______.the program will go on forever. This is called and infinite loop. *therefore however otherwise but 138. handheld computers fits into your pocket______ ,supercomputers occupy a whole room. *in contrast therefore so that however 139. An analyst analyses problems and finds solution, whereas a programmer______.these solution______ computer programs. make/into *turns/into turns/onto puts/into 140. It is likely that VR______.in many ways in the future, including providing a home shopping environment, and allowing premises to be guarded remotely . is used *will be used will use uses 141. although it is ______ to predict the future with any certainty, one thing we can be sure of is that the hardware and software we will be using in twenty or thirty years' time will be very different from what is in use today. *impossible possible possibly impossibly 142.email will allow pupils ______.will pupils in another part of the UK and in different parts of the world. communicate *to communicate communicating communicated 143.pupils will become______ IT from an early age. Computer skills will help them when they leave school. famililar *familliar with familliar for familliar of 144.perhaps humans______.one day travel to other planets and even discover other worlds. could must *may going on 145. when a piece of virus code______,the virus can be identified. *is found finds is finding found 146.the modern blog evolved from the online diary, ______.people would keep a running account of their personal lives. what *who why where 147.An anlyst analyses problems and finds solutions, then a programmer______ these solutions______ computer programs. turns/out *turn/into turn/onto turned/into 148.Small computers that can read the cards______.ambulances and in hospital emergence rooms. installed in installing in *are installed in is installed in 149. Experience in the US has shown that greater use of computers______.school standards. have not raised *has not raised didn't raise don't raise 150. A smart card can be used in many ways, it can be used______.a key to the building. for like such as *as 151. Experts foresee, within twenty years, implanted chips that can correct our ability to interact______.the word. *with for in by 152.Customers may well be able to______ a virtual assistant who will talk them through their shopping or to ask the computer for suggestions. being called up calling up to call up *call up 153.bank customers can now download money from their account to an electronic wallet, a smart card, using a specially ______ phone equipped with a smart card reader. design *designed to design designing 154. banks in the future are likely to develop a ______ currency payment engine which allows online retailer to sell their goods in sixteen countries. mono*multimixmini155 . The Maltese Amoeda is a very dangerous virus and it looks funny but if it ___your computer , you ___laughing. *attacked /wouldn't be attacked/would be attack/would be attack/wouldn't be 156. Most viruses remain dormant___activated by something. after before when *until 157.If you do catch a virus , there are antivirus programs to hunt___and eradicate the virus for up *down with 158.It is likely that VR___in many ways in the future , including providing a home shopping environment, and allowing premises to be guarded remotely. is using *will be used will use is being used 159.It is also likely _for air traffic control and for training doctors , allowing them to practise diffrcult operations safely. be used *to be used will be used being used 160.Computers may be connected directly to the humen brain using a direct neural interface (DN1) to change the brain of the user ,___them to do things they couldn't do before to allow allow *allowing allowed 161.Smart cards are already ___for storing information about the user , for controlling access to facilities , and as a means of providing money in an electronic form. used using to be used *being used 162.Smart cards will have a wide variety of uses and___to become very common in the near future is likely *are likely will be likely are like 163.The development of smaller computers and computing networks is making it easier for computers__in more situations be used are used *to be used being used 164.It would be better to spend the money__teaching reading , numeracy,and taking pupils on field trips for under *on in 165.Email will allow pupils__with pupils in another part of the UK and in different parts of the world communicate communicating will communicate *to communicate 166.Computers will free teachers___paperwork *from right away away at once 167.They will make a big change___computing and will inevitanly encourage a lot more people to use computers___everyday situations *in/in in/on on/in by/in 168.We will produce students who are not good___communicating with others and working as a team on about *at in 169.Computers are likely to continue to become___,and more efficient faster,more cheap *faster , cheaper fast , cheaper more fast ,cheaper 170.It is difficult ___a good time to buy a computer because they are always being improved *to find finding find to be found 171.This is___important in a network where many users are storing vast amounts of data special specially specialized *especially 172.Networks also require security systems___access controlling *to control controlled control 173.Electrolic computers ___around for a relatively short time will be *have only been are were 174.Mainframes are still in use however and have continued___developed be being *to be have only been 175.When a piece of virus code is found , the virus___,and an appropriate program run to delete the virus code from the disk or file is identified will be identified *can be identified identifies 176.Experts advise us__country-specific domain names such as 'fr' for France, '.mx' for Mexico or '.vn' for Vietnam *to register register registering registered 177.The mobile phone is a device___people use for communicating with each other what *which who why 178.The amount of light produced by an LCD screen is called___, or luminance , measured in cd/m2 bright *brightness brightly bright less 179.New digital cameras offer innovative features such us Bluetooth___ connect connecting connection *connectivity 180.The human brain is far___powerful than be ___advanced computer working at its full capacity more/more most/more *more/most most/most 181.I recomment getting the ___resolution monitor you can afford *highest higher highly high 182.Plasma screen are___than LCD screens heavy heavily heavyer *heavier 183.You___write on discs with permanent pens must have to should *shouldn't 184.Don't___hit or move the computer while the hard disk is spinning *O should must can 185.A virus entered my computer . ___,many files have been destroyed on the other hand in contrast moreover *as a result 186.We need more money to ___the school library computer *computerize computerization computing 187.Today,most of the information we produce is stored___ *digitally digital digit digitized 188.To make a movie on the PC,user needs a special video___program edit edited editor *editing 189.___is the technique used to make a graphic object look realistic,by adding reflection , shadows and highlights to render render *rendering being rendered 190.We are looking for a web master who___design , improve and mmanitain our website have to must *can could 191.I___use a computer when I was only five years old can *could might may 192.It you want to create your own MP3 files from your CDs , you___have a CD ripper can could need *must 193.If I ___you,I would buy the fastest computer to play encyclopedia version was *were had been would have been 194.People___buy cracked software or download music illegally from the internet *shouldn't should must have to 195.The Help facility enables the user___advice on most problems get gets *to get getting 196.Adding more RAM lets your computer___faster *work works to work working 197.Users should avoid___off main power while they are working on the computer turn to turn *turning being turned 198.They use special applets to create___fractals amaze *amazing amazed to amaze 199.It is advisable___test the programs under different conditions testing being tested test *to test 200.He refused___the project with me *to do doing being done have done 201.Programs written in a high-level language require____-that is , translation into machine cade , the language understood by the processor compile compiling *compilation compiler 202.A___is a program used to test and____other programs *debugger/debug debugger/debugging debug/debugger debugging/debugger 203.A___keyboard alllows the user to configure the layout and the meaning of the keys program programmers programming *programmable 204.These days,you___learn how to use complicated HTML codes . Modern web design software is user-friendly and converts a visual layout into HTML code mustn't shouldn't *needn't can't 205.To view a PDF file , you___have Adobe Acrobat Reader *must need should can 206.If I had the money,I___invest in some new multimedia software can will should *would 207.A 23-year-old man known as Captain Zap on the networks hacked___the While House and the Pentagon in 1981 to *into onto by 208.In 1991, Kevin Paulsen was___stealing military files in America *accused of accused accusing of accuse of 209.IBM international ___by hackers when they wanted to arrest a dangerous black-hacker paralyzed *is paralyzed were paralyzed was paralyzed 1.A banner applet displays graphic images on websites_______advertise products or services. A. in order to B. to c. so as to *D.All are correct 2.The Jman for Java applet permits medical researchers to view_____MRI (Magnetic Resonance Images) of the brain. *A. sequential B. sequentially c. sequence D.sequencing 3.One of the competitors of Java is Microsofts c #,______as C sharp. A. pronounce B. pronunciation *c. pronounced D. pronoun 4.The idea for Java started in 1990, when a team of software engineers at Sun Microsystems decided_____ a language for a handheld device. *A. to create B. create c. created D. creating 5.With the advent of the Web in 1993, the company made a web browser based______ A. in *B. on c. under D. with 6.Don’t let your children_____too much time on playing computer games. *A. spend B. to spend c. spent D. spending the Oak langu 7.My boss doesnt allow me_______the company�s telephone for private calls. A. use *B. to use c. used D. using 8.The Java language_______ A. invents *B. was invented c. invented D. inventing 9.When_________ *A. did - play B. was I played c. are I playing D. do - to play by a team of software engineers at Sun Microsystems. you first_______a computer game? 10.How old were you when you______your first Java language lesson at school? A. take B. have taken *c. took D. are taking 11. Computer specialists________ about the computer system security when they found a malicious virus attacking the system. A. worry *B. were worried c. have worried D. to worry 12.Plug-in is an auxiliary program that enables web browser_______ example animation. A. support B. supported c. supporting *D. to support new content, for 13. He interacts very well______other students in his programming language class at college. A. to *B. with c. on D. in 14.The new technology should enable doctors_______the disease. A. detect B. detected c. detecting *D. to detect 15.With the compiler, a program is first converted_________Java bytecodes. A. to B. with *c. into D. on 16.The new analyst programmer makes her boss pleased with her high labor______ . A.efficiently B. efficient c. efficienced *D. efficiency 17.The seft-discipline is one of the most important qualities for a senior programmer because he has to control himself and to make______work hard in a particular way without needing anyone else to tell him what to do. 'A. he *B. himself C. his D.him 18.A computer security specialist needs to have a high_____in debugging. A. accurate B. accurately *C. accuracy D.accurating 19.A DTP operator needs to have_____ *A. imagination B. imagine C. imaginary D.imanaging 20.Why don�t you apply_____ to form great pictures or layouts. the post of Web master at Digitum-UK? - Because I�m lack______experience. *A. for/of B. in/of C. for/in D.in/in 21.Charles cannot play this game on his computer because it is not compatible_______Window XP. A. in *B. with C. on D.for 22.He___ A. do/in *B. did/in a course_____ graphic design at Highland ArtSchool in 2003. C. do/on D.did/on 23.An anti-virus software is a necessity to protect your computer______viruses. A. in B. on *C. from D. under 24. Mike stayed at high school_______ coding and debugging at Aston University. A. for B. since C. ago *D. until he was 18 and went on to do a course in 25.I started______ in the DTP field six years ago and now I work as a DTP operator for a leading financial magazine. A. work B. working *C. to work D. worked 26.Lisa worked as an analyst programmer for Computer Sciences______a year as part of her degree. *A. for B. since C. ago D. until 27 ._____, I spent six months in America testing our new software for general commercial use. A. Two years so far B. Since two years *C. Two years ago D. Until two years 28.I have designed four programs in COBOL, and_______January I have been writing programs in C. A. for *B. since C. ago D. until 29.She_______an IT consultant at Media Market, a company specializing in e-commerce and IT strategy since 2004. A. was B. is C. will be *D. has been 30.How long ____you______ A. have - use *B. have - been using C. are - used D. are - using computer? - Since 2007. 31.How many spam emails________you______ *A. have - received B. have - been receiving C. had - received D. had - been receiving today? - More than twenty. 32.______you ever in another country? -1 spent 6 months in London learning hardware computer and networking at Cybernetics College. A. Are - living *B. Have - lived C. Did - live D. Have - been living 33.I______my CV of computer security specialist last Monday.______it yet? *A.sent - Have you received C. send - Have you received B.sent - Have you been receiving D. sent - Have you been receiving 34.How can a PC be connected______ A. to B. with C. X *D. A & B are correct another computer in a network? 35.Davis spent 1500 dollars________his course of graphic design and page layout at Highland Art School. A. in *B. on C. X D. over 36.Mobile phones help you keep in touch with your family and friends but prolonged use of them can affect _________your health. A. in B. on *C. X D. over 37.Wearable computers are designed to be worn on the body or integrated_________the user�s clothing. *A. into B. for C. X D. A & B are correct 38.Most existing TV sets can be upgraded to digital TV by________a digital decoder. A. connect B. connected *C. connecting D. to connect 39.The term cyborg _______by M Clynes and N Kline in 1960, with the meaning of a cybernetic organism, a being that a part robot, part human. A. invent B. invented C. is invented *D. was invented 40.In recent years, most mobile phones_______ helps cell phones communicate over short distances. A. equip B. equipped C. are equipped *D. have been equipped with Bluetooth, a technology that 41.I had to use my laptop this morning while my PC______ A. is fixed B. was fixed *C. was being fixed D.is being fixed . 42.Computer chips_______ of silicon with a certain grain size: 0,063 to 2mm. A. made *B. are made C. make D.have made 43.The examination papers are scored by machine. The students______their results next week. *A. will be told B. are told C. were told D.have been told 44.Social scientists warn that mobile phones_________while driving because they can make drivers lose their concentration. A. aren�t used *B. shouldn�t be used C.weren�t used D. won�t be used 45.I applied for the job of help desk technician for IBM last week and now I_______for interview. A. am invited B. was invited *C. have been invited D.will be invited 46.Why do you go to your programming language class on foot? Where�s your car? It_______at the moment. A. is repairing *B. is being repaired C .is repaired D. was repaired 47.It�s a pity the computer game was called off________rain. A. because *B. because of C.for D. A & B are correct 48.Separate networks are_______a public network, the Internet, the largest LAN in existence. *A. linked over B. linked out C.linking in D. link with 49.Do you think it is secure_______financial transactions via mobile phones? A. carry on *B.to carry out C. carries in D. to carry 50.To establish an Internet connection at home, you need to contact with your local ISP,_______their form and wait. A. filling over B.to fill out *C. fill in D. filled up 51.To communicate with your friends, you need______an Internet connection for your computer. A. setting out B.setting C. set in *D. to set up 52.When you see a strange word, try to make your best guess before you_____it______ A. looked/on in a dictionary B.looking/on *C. look/up D. looked/off 53.Remember_____the computer____ A. switch/in B.switching/on C. switch/up *D. to switch/off before leaving your office. 54.It�s dark here. I can�t see anything clearly._____the light______, please. A. Turning - in *B.Turn - on C. To turn - up D. Turned - off 55.If you save your password in your web browser, your password appears when you_______your username . *A. type - in B.are typing-on C. have typed - up D. will type - off 56.The wireless network in Los Angeles_______ a wireless access point or a wireless router, which links multiple computers without using cables. *A. consists of B.consist C. consisted up D. consist off 57. These files_____a lot of disk space. A. are take up B.are taken into *C. take up D. has taken on 58.She______a secret box when cleaning her house. A. founded B.finding C.has found out *D. finds out 59.In a bus network, all the computers_______a main cable, or bus. A. plug in *B. are plugged into C. have plugged into D. have been plugged to 60.Several LANs connected together______a WAN. A. are made by B. have been made up C.made of *D. make up 61.Before purchasing a piece of new software, you should_________ first. *A. try out B. to try on C.trying in D. be tried up their trial version 62.You can play Typing Games on a personal computer. These games will challenge you to type as _______as possible. *A. quickly B. quick C.quicklier D. quicker 63. Java is a programming language__________ A. express - distributed B.express - distributing *C.expressly - distributed D. expressly - distributing designed for use in the_____ 64.Serious video games are games that are designed______to convey information or a learning experience of some sort to the player. *A. primarily B. primary C.primariness D. primality 65.The first______ A. full automatic *B. fully automatic C.full automatically D. fully automatically mobile phone was introduced by Motorola in 1981. 66.In banks, computers store information about the money held by each customer and enable staff to access databases and to carry out__________ transactions at high speed. *A. large financial B. large financially C. largely financial D. largely financially 67.Games are now even more life-like and A. visual attractive B. visual attractively *C. visually attractive D. visually attractively . environment o 68.Wii is_______ the most________ of the three machines. A. current/popular *B. currently/popupar C. current/popularly D. currently/popularly 69.E-commerce has become_______ over the last decade. A. increasing popular *B. increasingly popular C.increasing popularly D. increasingly popularly 70. Stratergy games are mainly restricted______ A. with B. on C. in *D. to PC. 71.The new concept of party games - where people play together in multiplayer mode - has recently injected new life_________ Adventure game and Puzzle game genres. *A. into B. out of C. up D. on 72.It is important_________ programming languages with markup languages. A. not confuse B. to not confuse C. don�t confuse *D. not to confuse 73. By 2020, scientists believe that nanobots will be injected_______ bloodstream to treat diseases at the cellular level. *A. into B. from C. on D. by the body�s 74.Nanotechnology is going to have a huge impact______both business and our daily lives. *A. on B. in C. into D.over 75.As I was about_________when you interrupted me in the Computing class yesterday. A. say *B. to say C. saying D.said 76.Paula and Tom were on their summer vacation when the thieves broke____ smart house. A. on B. in *C. into D.onto 77. In the future, doctors will use nanobots to inject medicine______ A. in B. on C. X *D.into 78. Listening to music on my Ipod makes me_____ A. happily *B. happy C. happiness D.happilier their patients� body. . 79.They hope that people__________naturally with hundreds of smart devices at a time. *A. will interact B. are going to interact C. will be interacting D. will have interacted 80.My lovely computer_______me a lot with your homework. *A. helps B. is going to help C.will be helping D.will have helped 81.By this time next year, I__________for IBM. A. will work B. is going to work *C. will be working D.will have worked 82.By this time next month, I________the Iphone 6 plus that I have wanted to buy for months. A. will buy B. is going to buy C. will be buying *D.will have bought 83.By 2050, scientists believe that everyone___________in smart houses. A. will live B. is going to live *C. will be living D. will have lived Revison 1.HTML stand for____ language. *Hypertext Markup Hightext Markup Hypertext Makeup Hypertask Markup 2.C++ was ___ from the C language. Designed converted *Developed Invented 3.C++ is___, i.e. programs written in C++ can be easily adapted for use on different types of computer systems. Removable *Portable Regrettable Transferable 4.HTML is a page description language used for creating___. System programs *Web pages Applications Text files 5.Java is designed for programming small electronic devices such as___. Servers Desktops Mainframes *Mobile phones 6.JavaScript, a___form of Java language, is powerful and easy to use. Copy Old *Simplified Embedded 7.Scripts are small programs that can be used to___simple task or tie other programs together. *Perfom Adapt Respond Produce 8.Both VisalBasic and Delphi are___for developing programs for the Windows OS. Machine codes *Programming environments Natural languages Programming objects 9.CPU consits of Control Unit, ALU and___. Buses Adapters *Registers Processors 10.ALU stands for___Unit. *Arithmetic Logic Access Logic Arithmetic Local Access Local 11.The set of conductors that carry the memory address signals between different parts of a computer system is called___. Data bus *Address bus Control bus All of choices are right 12.___are connectors that carry signals between the processor and other part of the computers. Devices Units Registers *Buses 13.Data bus is a___bus as it carries data from the memory to the CPU and from the CPU memory. Unidirectional Mono-directional *Bidirectional Multi-directional 14.Clock line carries a signal from the clock chip to___the oprations of processor. Fetch *Synchronize Execute Direct 15.Personal computers can___instrutions in less than one-milionth of a second. *Execute Create Make Configure 16.___refers to the combination of I-time and E-time. Instruction time *Machine cycle Execution time Machine code 17.Many people like using___computers as they fit into their pockets our pocket. Notebook Portable Desktop *Handheld 18.The control Unit DECODES the instructions ang dirests that the necessary data be moved from memory to ALU. Find a word which best replaces the word DECODES. Stores *Translates Executes Fetches 19.VR headset, which can aso called___, showed graphics on a screen in fonts of our eyes. *Head-mounted display Head-wear display Head display set 3-D headset 20.___is a very small mechanism containing a tiny computer. It is used in sensors, gyros and drug delivery. *Micro-machine Microchip Robotics Micro-robots 21.A plastic card containing a processor and memory chip is calles a___. Electronic card *Smart card Robotics Chip card 22.An input device worn on the hand in a virtual reality system is called a___. VR mouse Hand glove VR hand *Data glove 23.If all schools and universities are___and develop e-learning, there will be paper-free education. Integrated Disconnected *Netwoked Offline 24.There will possibly be___computers inside human body to monitor and regulate our heart rate or blood pressure. MicroMini*Miniature Small 25.___chips, chips inserted into your body parts, can correct our ability to interact with the world. *Implanted Imported Included Integreted 26.In the first computer generation, vacuum tubes, also called___, were used. Transistors *Valves Circuits Chips 27.In 1965, ___(Ics) were introduced, which reduced the computer size considerably. *Integrated circuits Incorporated circles Incorporated circuits Integrated circles 28.A disk which is protected against writing is called___disk. Wtite against Write-aided Write protect *Write-protected 29.In the near future, ___ screens will replace monitors. Liquid *Flat panel Crystal Flat 30.The second generation of computers were___by transistors. Controlled Invented *Operated Introduced 31.___ refers to the unauthorized access to a computer system and changing its data. *Hacking Pirating Making virus Tampering 32.If you illegally copy software programs, you may be accused of___. Hacking Cracking Attacking *Pirating 33.A plastic card with a magnetic strip containing a user�s identification number is called a___. PIN card *Swipe card Bank card Access card 34.___ is a form of program which infects your computer and destroys your data or damages your system. *Virus Spam Bug Adware 35.Some viruses are___but some are destructive. Harmful Useless *Harmless Serious 36.Viruses can be___ via removed disks, LANs, bulletin boards and email attchments. Infected *Spread Activated Scanned 37.Do not open email attachments send by strangers without___for viruses. Cleaning Opening Downloading *Checking 38.If your computer is infected with a virus, there are antivirus programs to hunt down and___the virus. Eradicate Clean Remove *All of choices all correct 39.Compuserve was___ trafficking pornography and neo-Nazi propadanda. *Accused of Told Warned Charged 40.A___sells computer hardware and arranges support or training for customers. Hardware engineer Software designer *Computer salesperson Computer System Support person 41.___ designs, writes, compiles, and tests the systems and applications of all kinds. Hardware engineer *Software engineer System Analyst Network Support person 42.A___ maintains all aspects of networks including software, wiring and workstations. Software engineer Hardware engineer System Support person *Network Support person 43.Software engineers often___ programs from libraries or sub-programs and combine them to make up a complete system program. *Compile Translate Design Specialize 44.A___ researches designs and develops computer, or parts of computers, and the computerized element of appliances and vehicles. System Analyst Network administrator *Hardware engineer System Support person 45.Website with entrics posted on regular basis and displayed in reverse chronological order is called a___. Weblog Web log Blog *All choices are correct 46.Authoring a blog. Maintaining a blog or adding an articcle to an existing blog is called___. Blogger *Blogging Entry-posting Content-adding 47.It is possible for readers to leave___in an interactive format on blogs. Entries Posts *Comments Articles 48.Micro-blogging is a type of blogging which consists of blogs with___. *Short posts Photographs Sketches Mixed media types 49.Blogs can be___ by dedicated blog hosting services, or they can be run using blog software. Displayed Posted Read *Hosted 50.The morden blog ENVOLVED from the online diary, where people would keep a running account of their personal lives. Which of the following can word ENVOLVED be best replaced with? Came *Developed Imported Recognized 51.A PostScript file consists of two main parts, one of which is the �prolog� containing a set of___ used to form different graphic elements. Script Scripts *Subroutines Subroutine 52.A piece of equipment that is connected the CPU of a computer system is called a___. Backup device CU *Peripheral ALU 53.System Analyst Programmers have to___a feasibility study in the company before writing a program. *Carry out Work out Make up Play back 54. my job is to persuade customers tha it�s ____ investing in new computer system on extending the systems they already have good *worth valule expensive 55. Technical sales managers have to _________ after the sale and make sure things are working well. keep on touch keep in tour keep in distance *keep in touch 56. it�s my job to try _____ new components before they�re used in our computers. *out on in with in 57. software designers have to change the specifications for a system into a ____ that can be programmed. logical put logical constructions *logical order logical sequence 58. software engineers are also ___ for developing new systems. *responsible able charge capable account feasible look 59. unauthorzized access to compyter systems and tampering with other users data is know as_____ pirating *hacking making viruses spreading viruses 60. intentionally attempting to spread viruses is considered as computer______ guilty peripheral criminal illegal *crime 61. because faults can be develop in computer systems , it is important to keep copies of valuable data using a_____ storage device peripheral store system *backup system 62. connector that carry signals between the processor and oter parts of the computer are called___ wires ports *buses ports 63. in the machine cycle, the fetch an decode steps together are called___ *instruction time decoding time fetching time excecution 64. the person who advises potenential customers about available hardware and sells equipment to suit individual requirements is a____. software engineer *commputer salesperson help desk hardware producer 65. �com� or net is so called ___. *extension domain name identify axpansion 66.A _____ is someone to snaps up generic domain name. *prospector extortionist cyber-squatter domain owner 67. in low-level laguages, cash instruction is ____ to a sigle machine code instruction alike equal *equivalent corresponding 68.the _____ of mocement with television and motion pictures is achieved in the same way as the technique used in computer animation. sense *appearance impression illusion 69.one of the most important steps in computing technology in the coming year is ____ to be a return to mechanical methods. similar *likely alike unlikely 70.only a step further is the idea of building insect ____ robots that could do difficult job in very small places. *sized shaped designed imaged 71. average time required for the recording heads to move and access data is ___. data transfer rate move time search time *access time 72. prolog , which is the short form of programming in logic, contains a set of __ used to form different graphic elements. *subroutimes equations compiler assemblers 73. technical sales managers have to ____ after the sale and make sure things are working well. post subrountine *script element 74. the data transfer rate also ____ on the power of your computer. *depends independ rely base 75. a piece of equipment that is connected the CPU of a computer system is called a_______. access CU ALU *peripheral 76. it is common to _______ computers together to form a network. access *connect mix share 77. system analyst programmers have to ___ a feasibility study in the company before writing a program. *carry out work out take up set up 78. the aim is to see whether a new program would be better ____ the methods they use at present more much much more *than 79. the language I choose for coding will deend____ various factors. in *on up upon 80. viruses can be found and removed by _____ program. kill-virus protect-virus anti-virus & kill-virus *anti-virus 81. it�s my job to try ____ new componects before they�re used in our computer. in on *out with in 82. we have 2.600 pubs and 550____ engineers. server *service maintain reinforce 83. intentionally attempting to spread viruses � considered � computer____. criminal guilty offence *crime 84. most viruses remain______ until activated by something. *dormant silent active the same 85. because faults can develop in computer systems, it is important to keep copies of valuable data using a_____. stock *backup system store store system 86. some computer systems use____ that scan and identify characteristics of the user such as their fingerprints, facial features, voice , or eyes. identify system recognition system& backup system backup system *recognition systems 87. always ________ an email attachment before opening it. virus-test *virus-check virus-exam virus-proof 88.bacsic languages , where the program is similar to the machine code version, are ___ as alow-level languages. *known realized understood appreciated 89. the___ is made up of 1s and 0s. digits digital *binary system decimal system 90. processors follow a fixed sequence of steps, called the____ , to process a program instruction *machine cycle cycle machine cycle process process cycle 91. the arithmetic /logic unit excutes the arithmetic or ___. *logical operations logical instructions lgic instructions logic operations 92.in the machine cycle the, the fetch and decode steps together are called___ decoding time storing *instruction time execution time 93. in the machine cycle the execute and store steps together are called_______. *execution time storing time executing time instruction time 94. each postscript-based printer has a microprocessor, at least 2 MB of RAM , and an operating system that ____ the postscript code. encrypts *decpypers transfers interprets 95. in the first steps of the machine Cycle, the control unit ___ the instruction from memory. takes systems analyst software engineer *software designer 96. the person who studies employer�s requirements and working pattern, reports on different options, and writes specifications for programmers is a ______. computer salesperson *systems analyst software enginer software designer 97. the person who often compiles program from libraries or sub�programs, combining these to make up a complete systems program is a________. software engineer *software designer& software engineer software designer computer systems analyst programmer 98. the person who researches, designs, and develops computers, or parts of computers and the computerized element of applicances , machine, and vehicles is a________. *hardware engineer systems analyst software engineer hardware designer 99. maintaining the link between PCs and workstations connected in a network is a part of a ___ job. network designer network engineer *network support person network analyst 100. You have to know the ___ to enter the system, in the same way that you have to know your personal identification number to get money out of a bank cash machine security system *correct password safety transaction identity card 90-b. the ___ is a unidirectional bus. Data flows one way only. It carries addresses from the processor to memory. data bus control bus *address bus all are correct 91-b. the ___ control bus is bidirectional.it carries instructions to and from the CPU and other parts of the computer. address bus *control bus data bus all are correct 92-b. ___ are program that have been written to make a computer behave in an unexpected and undesired way. *viruses sharewares free ware none is correct 93-b. as networking develops _______ is likely to become more common, although people will prefer to meet face �to �face where possible email newsgroup *video conferencing relay chat 94-b. it is likely that computer will play a bigger role in teaching in the future. Teaching , however, requires________ and is unlikely to be done entiren by computers. technology machines *human skills computer 95-b. three _____ of our daily lives that are certainly likely to be affected are health, shopping and money *features fields areas factors 96-b. A ___ is a glove with pressure pads which make yor hand feel as if it�s picking up object or touching surfaces. VR glove data glove data gole, or VR glove *all of the choices are right 97-b. In the near future all schools and libraries will be linked together to from a ___ for Learning - just like the electricity grid which connects all consumers. electricity centre *National Grid national library national data 98-b. All study and most jobs in the future will require ___ computer literacy. computer data computer information *computer literacy computer illiteracy 99-b. Email will allow pupils to ___easily with other puplis in different parts of the country and in different parts of the world. *communicate talk speak say 101. Every individual is unique. Some security system us ____. physical gestures personalities appearances *individual body characteristics 102. A new product called �Facelt� uses ___to protect individual files. *face recognition voice recognition speech recognition fingerprint 103. Easy access to online ___ will not help pupils to develop original ideas. information systems *resources data 104. In some companies, wrokers wear an ___ with an embedded chip, which signals where the wearer is at any time. *active badge-an ID card plastic card business card smart card 105. ___ is mainly used to describe the appearance of text, graphics and images on the printed page. Delphi Cobol Java *PostScript 106. ___ refer to the process of encoding data so that unauthorized users can�t read it. Decryption *Encrytion Certification Authentication 107. Small files used by Web servers to know if you have visited their site before are ___. certificates contemporary files *cookies properties 108. ___ are files that identify users and Web servers on the net, like digital identification cards. *certificates cookies locks cards 109. A(n) ___ is made of two or more computers linked together to allow user to share files, software and hardware. web cyberspace browers *network 110. A person who obtains unauthorized access to computer system is called ___. breaker *hacker blogger poster 111. Computer ___ are pictorial images producted by computer and refer particularly to images displayed on a video display screen, or display monitor. animations *graphics pictures images 112. A program that enables a computer to process graphic images by means of mathematical language is called ___. *graphic sofware package desktop publishing package image-setter package paint and drawing package 113. A computer display images on the phosphor- ___ surface of graphics display screen by means of an electron beam. dressed worn *coated wearable 114. Changes in the intensity of light beam determine their brightness and HUE of the screen. Which of the followinf can be the word HUE be best replaced with? size *colour resolution clearness 115. A picture can be drawn or redrawn onto the screen with the euse of a mouse, a ___ tablet, or a light pen. *formats pressure-sensitive light-sensitive pressure-attracted 116. An output device which print the image on paper or on photographic film is called ___. pattern-recognition devices plotter digitizer *imag-setter 117. The computer can also generate hard copy by means of ___. image-setter digital camera *plotters digitizer 118. ___-type graphics maintain an image as a matrix of independently controlled dots. Vector *Raster Raster and vector alphanumeric 119. Computer animation is the art of � �___ moving images via the use of computers. producing generating creating *all the choices are correct 120. CGI stands for computer-generated ___ or computer-generated imaging. *imagery icon interface interrupt 121. The differences in appearance between key frames are automatically calculated by the computer in a process known as ___. *Tweening modeling rendering rigging 122. the question of security is crucial when sending ___ information such sa credit card numbers. corporate *confidential business academic 123. To void the risks of being hacked, you should set all the ___ to high on your Web browser. mail alerts cookies alerts pop-up blockers *security alerts 124. ___ is the simple combination of a word with an extension like �.com� or �.net�. Web identity Web address *Domain names security alerts 125. ___ is the practice of registering dozens, even hundreds of popular, trademarked names with the purose of selling them for big money. Purchasing Tracking *Cyber-squatting Browsing 126. It�s advisable to buy a domain name from an official ___ so you have a contract and the protections that go with it. *registrar subcriber domain user Inter Service Provider 127.Experts advise us to register ___ domain names such as �.fr�, �.mx� or �.vn�. extension-specific code-specific country-extension *country-specific 128. ___ often request a large amount of money for domain names but sometimes they do not receive any and even are taken to court. Experts *Cyber-squatters Hackers Crackers 129. If you want to set up an e-commerce business, firstly you must ___ a good domain name. *register subcribe mange negotiate 130. A prospector is someone to snaps up ___ domain names. pirated protected *generic trademarked 131. Almost every computer user occasionally ENCOUNTERS a problem such as forgotten password or the disaster of a crashing hard drive. What dose �ENCOUNTERS� mean? *have solve raise create 132. The EXPLOSIVEuse of computers has assistance has created demand for specialists who provide advice to users. Which of the follwing is EXPLOSIVE closest in meaning to? decresing limited well-known *fast-growing 133. Computer ___ provide technical assistance, support, and advice to customers and other users. programmers *support specialists developers analysts 134. Helpdesk specialists answer telephone calls, analyze problems by using automated diagnostic programs, and recurring difficulties. resolve *solve find solutions to all of the choices are right 135. Computer hardware or software vendors are ___. companies producing hardware and software *companies that sell hardware and software hardware and software specialists scientists in software and hardware 136. If computer system break down due to hardware or software problems, technical support specialists are responsible for ___ them. modifying cleaning *repairing installing 137. Helpdesk technicians also OVERSEE the daily perfromance of their company�s computer systems. What does the word OVERSEE mean? supervise manage monitor *all answers are right 138. These workers GATHER data to identify customer needs and the use the information to identify, interpret, and evaluate system and network requirements. What does the word GATHER mean? verify *collect evaluate coordinate 139. Computer and information system managers plan, coordinate, and direct research and facilitate the ___ activities of firms. business administrative *computer-related project 140. Computer and information system mangers ___ the work of system anlysts, computer programmers, support specialists, and other computer-related workers. *direct share support facilitate 141. Computer and information system managers plan and coordinate activities such as implementation of Internet and ___ sites in their organizations. wide area external *intranet worldwide 142. Computer and information systems managers assign and review the work of their ___. bosses *subordinates directors employers 143. Computer and information system ___ are Chief technology officers (CTO), Management information systems (MIS) directors or infoermation technology (IT) directors. analysts *managers technicians help-desk supporter 144. If you have any questions or problems with your computer, you can call an IT company�s ___. sales department administrative *hep-desk development section 145. ___ managers develop requirement, budgets, and schedules for their firm�s information technology projects. *Project Technology Software Information system 146. ___ (CIOs) are who computer and information systems managers report to. *Chief Information Officers Computer Information Officers Computer Input Operators Chief lnformation Operators 147. PDt stands for _____ Postscript Description Laguage *page Description Languagce Postscript Digital languge page Data Language 148. Producing the programs which control the internal Operators of Computer converting the systerm aralysl's specificatior to a logical series of steps are parts of a ___'s job hardware engineer *Software engineer systems analyst hardware desinger 149. the simple combination of a word with an ex tent\sion, serve as both the address and the identity of a Web company, is a ____. *domain name extension expansion website 150. the person who illegally buys and officially records an address on the Internet that is the name of an existing company or a well-known person, with the intention of selling it to the owner in order to make money is called a _____. cyber owner domain owner *cyber-squater website owner 151. the illegal activty of buying and officially recording an address on the Internet that is the name of an existing company or a well-known person, with the intention of selling it to the owner in order to make money is so called _____. *cyber-squatting cyber-owning cyber-conquering A&C 152.A(n) ____ is someone to snaps up generic domain name. domain owner cyber-squater extortionist *prospector 153.A(n)_________is someone who intentionaliy registers trademaker name. prospector *bextortionist cyber-squater domain owner 154.A(n)______ translales the original code into a lower.-level langunge or machine code so that the CPU can understand it *compiler assembler debugger. None of the choices 155.postscipt can speak to different output devides and adjust the quality � the final output to the highest capacities of the output devides do it is independent devide dependent devide *devide dependent devide independent 156.picture created in postscipt and saved as separates file which is called ESP file.in this case ESP stand for ____ especial PostScript English for specific purposes *encapsulated PostScript especial purposes 157.in low-level language, each instruction is ____ to a single machine code instruction. *equivalent alike equal corresponding 158.Individual articles on a blog are ____ "blog posts" , "posts" or "entries" telephone rang *called labeled 159.blog can be _____ by dedicared blog hosting servies or they can be run using blog software. accommodated *hosted held received 160.graphics software programs ___ the user to draw, colour and shade assist support aid *enable 161.A picture csn be drawn or radrawn onto the ____ with the use of the mouse, a pressuresensitive tablet, or a light pen. output display monitor *screen 162. the computers can also ____ hard copy by means of flotters and laser or dot-matrix printers make *generate group collect 163.C++ was used to ____ Microsoft Windows operating system *produce creat make manufacture 164.java is a programming language originally___ for programming small electronic devices such as mobile phone reserved planned *designed contructed 165visual basic is useed to write general purpose____ for the window operating system supplies *applications provision installation 166.program instructions and data must be ____ into memory from an input devide or a secondary storage device located *placed rested left 167 modern computer are ___ and relatively cheap. older computer werer less powerful and quite expensive *powerful violent strong hard 168.there are various types of blogs, and each differs in the way___ is delivered or writen media format device *content 169. A tylical blog combines text ,images, and ____ to orther blogs, webpages, and other media related to its topic connection *links posts comments 170.A graphics ____ produces images and designs. A word processor produces texts series box *package parcel. 171.small computers that can read the cards are ___ in ambulances and in hospital emergency rooms *installed put in set up patched 172.the biggest problem is making sure that people ___ their cards at all times hang take hold *carry 173. One of most important steps in computing technology in the coming years is _____ to be a return to mechanical methods. *likely similar alike unlikely 174. The ____ of using a micro-machine to deliver drugs is getting a bit closer to more sci-fi applications. view *idea opinion concept 175. Swallowing an ant-sized machine to cure you or putting one inside some failed machinery seems_ a really good idea. similar likely *like same 176. Some drawing programs can produce _____ draws in PostScript directly. text files print outs documents *pictures 177. Using ____ reality headsets and gloves, doctors and medical students will be able to experiment with new procedures on simulated patients than real ones. *virtual fake unreal untrue 178. Smart clothes which ____ their thermal properties depending on the weather. modify vary *change convert 179. Since we are already ____ with the notion of an internal pacemaker for the heart, including a chip or two may not seem all that astonishing. acquainted known *familiar informal 180. A mor commom implant would be a chip to ____ visual signals. *correct check modif fix 181. Shoppers will be albe to scan down virtual supermarket asisles on their PC and ___ on to whatever they want. put take rely *click 182. ____ is a set of programs used to detectm, identify, and remove viruses from a system. virus protection *anti-virus program data protection data security 183. A computer - graphics system basically ____ a computer to store and manipulate images. composes of *obtains consists of A & C are correct 184. Preexisting images on paper can ___ into the computer through the use of scanners, digitizers, or digital cameras. *be scanned pushed made put into 185. Programmers ussually ___ alot mor than just write the program code. work make write *do 186. The disigners sometimes use____ to show the sequence of logical steps in a program. maps *diagrams plans tree-flows 187. A (n) ______ in a computer program is often called a bug and the processes of finding and fixing them is known as debugging. *error mistake fault false 188. When your computer has fiddiculties, the processor ____ the priority of the action and stops what it is doing at an appropriate time to deal with the problem. processes gets *determines executes 189. When your computer has difficulties, the processor ____ the priority of the action and stops what it is doing ai an appropriate time to deal with the problem. *is made up of is combined is consist of is kept of 190. The CPU sends a message to the user after it saves its ____ status in a special area of memory. chosen particular permanent *current 191. There are ____ areas of computing and the students are likely to be able to suggest very recentn developments. speeding *fast-moving falling on-going 192. Computing is changing and developing at a very fast ____ around the word in every field. trend face *pace increase 193. It is already necessary for young people to have some computing____ if they want to find a job in the companies nowadays. *skills Bprograms capabilities materials 194. Miniature computers may be used to ____ our health and the use of computer controlled body implants is likely to develop to some extent. determind monitor provide *calculate 195. All study and most jobs in the future will require computer ____ . programs communication literal *literacy 196. Communication through networks will ____ teachers from paperwork. *liberate freedom increase improve 197. Computers _____ continue to become faster, cheaper, and mor efficient. will likely to is likely to *are likely to going to likely to 198. Speech recognition will make a big ____ in computing and will ineviably encourage a lot more people to use computers in everyday situations. *change Damage Loss develop 199. It is difficult to find a good time to buy a computer because they are always___. being repaired being sold being changed *being improved 200.Because___can develop in computer systems, it is important to keep copies of valuable data by using a backup system. mistakes *faults changes developments 201.Viruses are programs that have been written to make a computer behave in a(n)___way. right effective impressive *unexpected 202. Plain text email messages cannot contain a virus, but viruses can be___email attachments. *carried in carried out carriedwith carried of 203. Viruses have a tendency to ___themselves, and often attach themselves to other programs. coppy eather copy or replicate is correct replicate *both copy replicate are correct 204. It is common for a user to have a virus program on their disk without___it. aware of *being aware of wareness of knowledge of 205.___are temporary storage areas for instructions or data .They work under the direction of the control unit. *Registers Floppies Storage devices main memory 206.___is the standard set of rules for communicating over the Internet. *Transmission control protocol/Internet protocol internet address instructions ID 207.Popular network___include Unix,Novell Netware,and Microsoft Windows NT. microprocessors *operating systems word processors programming languages 208.A___is a group of parallel wires which earn electrical signals between different parts of the computer route signal *bus hub 209.The___is a bidirectional bus.It carries data and instructions from the memory to the CPU and form the CPU to memory. *Only data bus is correct both data bus and address bus are correct address bus neither data bus nor address bus is correct 210.Using built-in camera,you can make___to other 3G mobile phones and see yourself and other person you�re talking to on the screen. audio *video calls calls photos 211.If both card and PIN are valid, the ATM will proceed to___money to the customers. take get *dispense withdraw 212. A hacker is a person who___a network�s privacy *invades helps protect secure 213. We are the world leading___of digital camera for professional photographers. *manufacturer manufacturing manufacture manufactured 214. Ascreen___enlarger text and graphics on the screen,increasing legibility. zoom monitor *magnifier camera 215.A___has a screen and a keyboard that transcribes spoken voice as text; it�s ideal for deaf people. microphone recording touch-screen *text-phone 216. When a disk is formatted, its surface is divided into concentric cireles know as___. rings *tracks circular round 217. The set of all weblogs on the internet is called___. blogsphere blogging blogs *blogosphere 218.The Apple I Phone combines three products � a mobile phone, a widescreen iPod,and an internet device � into one small___device. *handheld hand hold handling handheled 219. To capture sounds in digital format and play them back, modern PCs contain a___card. sppeaker recorder *sound mouse 220.Text with links, which takes you to other Webpages, is called___ super link link connection *hyperlink 221. A CD___is a program that extracts music tracks from audio CDs to file on your hard disk. recorder *ripper player editor 222.The technique used to play sound and video files as a continuous stream while they are downloading is called___ *streaming ripping extracting playing 223. Compressed music can be played with an MP3___ stramer ripper *player recorder 224. Concert and other events are broadcast over the web in a process called___. blog cast *webcast weblog webpage 225. Graphics programs have a ___that enables you to draw,paint and edit images on the computer. *toolbox tool menu toolbar paint box 226. Bitmaps, or___are stored as a series of tiny dots are called pixels. vector graphics *raster graphic images animations 227. The basic elements used to construct graphical objects are called___;they include lines, curcles,polygons and text. attributes instructions features *primitives 228. Line objects can have different kinds of___, such as thickness, colour, etc. *attributes instructions features primitives 229.CAD designers often start a project by making a___, a drawing showing the edges and vertices of a 3-D model. wire frame *wireframe wireframing 230.In image-editing programs,___are special effects that can be applied to pictures including drop shadows,textures, distortions,etc. *Filters Rendering Wireframe Translating 231.___is the process of combining multiple images together to form one final image. Translating Rotating Remdering *Compositing 232. Gnofract 4D is a program that allows you to create___. fractals amazing *amazing fractals amazed fractals fractals amazed 233. The only language a PC can directly excute is___,which consistsof 1s and 0s. *machine code programming instruction high-level 234__refers to the technologies and applications that integrate different media: text,graphics,sound,video and animation. Smart device Modem *multimedia virtual reality 235.___represent images as mathematical formulae, so they can be changed or scaled without losing quality. *Vector graphics Raster graphics Animation Drawing 236.___adds textures to each surface, abd generates realistic reflections,shadows and highlights Rotating Compositing black *white 237.Crackers,or___-hat hackers, are computer criminals who use technology to perform a variety of crimes. red green *black white 238.___is one kind of crimes using e-mails or websites that look like those of real organizations. Abusing *Phishing Piracy Spyware 239. Looking at web pages can be called �navigating the web� but is more commonly called___. *surfing the net skiing the net swimming the net going to the net 240. A file which is copied from the internet into your computer is called___. an upload *a download a load a buffer 241. Designs and drawings in websites are usually called web___. pictured images illustrations *graphics 242.Websites with sounds and/or video clips and/or animations have___content. *multimedia many-media mixed-media various 243.A program that adds functions to a browser(eg Shock wave) is called a___. plug plugged-in *plug-in plugging 244.A website which can only be viewed by authorized people has___access. reduced small wrong *restricted 245.Internet users who like cyber-shopping should get a digital___,an electronic identity card. *certificate paper cash signature 246.Private network use a software and/or hardware mechanism called a___to block unauthorized traffic from the Internet. anti-virus *firewall interface lock 247.You can download___from the Net; this type of software is available free of charge but protected by copy right. pirate freeware software *plug-in 248.Afer creating DTP files on the computer, most people often take their files to___,a company that specializes in printing. advertising a gency software producer *distributor service bureau 249.If you click on a___link,you can jump to another screen with more information about a particular subject. super link hypermedia *hypertext supertext 250.MP3 is short for MPEG audio layer 3, a standard format that___audio files *compresses depresses opens views 251.___is a form of wnriched multimedia which allows an interactive and dynamic linking od visual and audio elements. Hypertext Hyperlink *Hypermedia Interactive games 252.___is a technique for playing sound and video files while they are downloading. *Streaming Recording Ripping Compressing 253.___is a special program which converts the source program into machine code � the only language understood by the processor. Flowchart Debugging Machine code *Compiler 254.Geographic information system (GIS) allow___to create detailed maps. *carto graphers map designers programmers photographers 255.In education, it is used in presentations and ___training courses. based computer *computer-based computerized computing 256. In____, users interact with a simulated world. practical the Internet *virtual reality multimedia 257. Some kinds of browsers allow you to disable or delete___, a small file placed on the hard drive by web servers so that they can recognize the PC once visited them. plug-in programs alerts *cookies freeware 258. The activity happening on the internet like harassment or abuse, mainly in the chat rooms or newsgroups is called___. piracy cyber-stalking phishing *spreading 259. ___ involes adding paint, colour and filters to drawing and designs. Wireframing Compositing Rotating *Texturing 260. Video and audio components are decompressed using separate___, a formula used for decomposing components of a data stream. algebra angle *algorithm algae 261. To find the webpage you want, you have to click on a webpage___ or enter a URL into a browser. browser *hyperlink sever domain name 262. ___is used for creating and editing webpages. image editor presentation program graphics *website editor 263. JPEG is the most common type of___ used for storing image data on the web. *compression decompression composition component 264. The company uses___ techniques to decode ( or decipher ) secret data. *decryption decompression compression encryption 1.Compiled Java code can run on most computers because there are Java interpreters, known as________ for most operating systems. A. Java ME B. Java applet C. Java Script *D. Java Virtual Machines 2.The Java Virtual Machine includes an option just-in-time compiler that dynamically compiles bytecodeinto _____as an alternative to interpreting one bytecode instruction at a time. *A. executable code B. digits C. java D. binary code 3.Flash files, traditionally called____, have a .swf file extension. *A. Flash movies B. The Jman applet C. The LandRover applet D.Adobe Flash 4.A competitor of Java is Adobe Flash technology,which supports graphics, a scripting language called____, and the streaming of audio and video. A. Flash files *B. Action Script C. Adobe Flash D. Flash movies 5.The Java language began to attract serious attention from____ *A. the Internet community B. Wi-Fi C. platforms D.the Internet connection . 6.Today, Java is a hot technology that runs on multiple____, including smart cards, embedded devices,mobile phones and computers. A. animations B. screens *C. platforms D. moving texts 7.An_____ clock applet displays the time according to the web user�s computer and lets you set the colors and style of the hands and numbers. *A. analogue B. digital C. computer D. synchronized 8.Java was designed to have the �clock and feel� of the C+ + language, but it is simpler to use than C + and enforces a/an____ programming model. *A. object-oriented B. multi-threaded C. single-threaded D.B & C are correct 9.Duke, an animated character, is the_____of the Java language. A. logo *B. mascot C. statue D.slogan 10.The original name of____ was Oak, which was named after the tree outside the window of James Gosling, one of the engineers at Sun Microsystems. A. Java B. the Java language C. the Java application *D. All are correct 11.Java applets let you watch_____characters on web pages. *A, animated B. object-oriented C. compiled D.interpreted 12.Java does have______: Microsoft�s C# and Adobe Flash. *A. competitors B. applets C. platforms D.A & B are correct 13.A person who knows a lot about Information Technology and is employed to give advice about it to customers and other people is a/an_____. . A.webmaster *B.IT consultant C. DTP operator D. network administrator 14.A person who uses page layout software to prepare electronic files for publication is callled a/an_____ . A.webmaster B. IT consultant *C. DTP operator D. network administrator 15.We call a person who manages the hardware and software that comprise a network a/an____ . A. DTP operator B. IT consultant C. DTP operator *D. network administrator 16.A person who is responsible for creating, managing and maintaining one or more webservers or websites is called a/an_____ . *A. webmaster B. IT consultant C. DTP operator D. network administrator 17.A person who writes applications programs (computer programs designed to be used for a particular purpose, e.g. wordprocessors, spreadsheets or database programs) is called a/an____ . A.IT manager *C. applications programmer B.system programmer D. help-desk troubleshooter 18.A person who specializes in writing systems software (a program or set of programs that are used to control the basic functions of a computer system, e.g. operating system programs) is a/an____ . A,IT manager C. applications programmer *B.system programmer D. help-desk troubleshooter 19.A person who manages projects, technology and people. He is also responsible for developing and implementing computer software that supports the operations of the business is called a/an_____ . *A . I T manager C. applications programmer U system programmer D. help-desk troubleshooter 20.We call a person who works as part of telephone service that helps users solve problems that occur on computer systems a/an____ A.IT manager C. applications programmer B.system programmer D*. help-desk troubleshooter 21.A fault in a machine, especially in a computer system or program is a____ . *A. bug B. debug C. blog D. troubleshoot 22._____is the technique of detecting and correcting errors which may occur in programs. A. Bugging B. Bug C. Debugger *D. Debugging 23._____refers to the transmission of signals over a distance for the purpose of communication. *A. Telecommunications B. teletext C. mobile phone D. Internet 24.VoIP stands for Voice over Internet Protocol, a system which lets you make phone calls using the____ instead of the regular phone line. A. telecommunications B. teletext C. mobile phone *D. Internet 25.With a Wi-Fi phone, you are using the Internet, so the calls are free or at least cheaper than using a(n)_____ . A. telecommunications B. message *C. mobile phone D. Internet 26.Spit, or spam over internet telephony, means that our phones could be blocked with unwanted voice_____ . A.telecommunications *B. messages C. mobile phones D. Internet 27.Thanks to telecommunications, people can now work at home and communicative with their office by computer and telephone. This is called____ . A. teletext *B. teleworking C. telemarketing D. call centre 28_____ .is the process of selling goods and services over the phone. A. Teletext B. Teleworking *C. Telemarketing D. Call centre 29. A___ has the ability to handle a considerable volume of calls at the same time. A. teletext B. teleworking C. telemarketing *D. call centre 30._____ is a system for giving written information on many subjects, such as news, sport results, share prices and weather forecasts, by television. *A. Teletext B. Teleworking C. Telemarketing D. Call centre 31._____ is/are transmitted by devices such as the telephone, radio, television, satellite or computer network. A. Information B. Data C. Signal *D. All are correct 32. A___ is a being that a part robot, part human. *A. cyborg B. robotics C. nanobots D. android 33._____ is a machine that sends and receives documents in an electronic form along telephone wires and then prints them. A. Teletext B. Set-top box *C. Fax D. BlackBerry 34.The Passport, the latest model of__ A. mobile phone B.set-top box C. wearable computer *D. BlackBerry , is officially released on September 24,2014. 35.A device that changes a digital television signal into a form which can be seen on an ordinary television is called a_____ . A. teletext *B. set-top box C. fax D. BlackBerry 36.____ is a machine in or outside a bank from which you can get money from your bank account using a special plastic card. A. Cashpoint B. Cash machine C. Cash dispenser *D. All are correct 37_ ___ cover a large geographic area, like a country or even multiple countries. A. LANs B. Intranets C. PANs *D. WANs 38.______ is a computer network interconnects computers within a limited area such as a home, school, computer laboratory, or office building. *A. LAN B. Intranet C. PAN D. WAN 39.A computer network typically includes a laptop, a mobile phone and a PDA is called___ A. LAN B. Intranet *C.PAN D. WAN 40.A company network that uses public internet software but makes the website only accessible to employees and authorized users is called____ A.LAN *B. Intranet C.PAN D. WAN 41.According to geographical area criteria,_______are divided into PANs, LANs, MANs and WANs. A .topologies B. architectures C. network protocols *D. networks 42. Networks use different_______. For instance, the Internet uses TCP/IP. A .topology B. architecture *C. network protocols D. geographical area 43.According to the criteria of________ peer-to-peer network. A. topology *B.architecture C.network protocol D. geographical area , networks include client-server network and . 44.There are 3 kinds of_____ *A. topology B.architecture C.network protocol D. geographical area , or layout: bus network, star network and ring network. 45.A wireless network for connecting Wi-Fi hotspots is called______ *A. WiMAX B.satellite C.Bluetooth D. GSM . 46 .____ is the wireless technology that allows devices to communicate over long distances. A. WiMAX *B. Satellite C. Bluetooth D. GSM 47 .____ is the wireless network for mobile phones. A. WiMAX B. Satellite C. Bluetooth *D. GSM 48.Much of the Internet uses high-speed______ A. Wi-Fi hotspot *B. fibre optic cable C. Ethernet cable D. telephone line to send data over long distances. 49.The device that serves as a common connection point for devices in a wireless network is called_______ . A. wired router B.broadband modem C.wireless adapter *D. wireless access point 50.On___topology, all data flows through a central hub, a common connection point for the devices in the network. A. bus B. ring *C. star D. client-server 51. A___ is a device that outputs a video signal to display a video game. A. personal computer B. mobile phone *C. video game console D. portable gaming device 52.Some mobile phone games are programmed to run natively on the chip of____ A. personal computer *B. 3G mobile phones C.video game console D. portable gaming device . 53.Console games are played on_________, such as the Sony PS3 or Microsoft Xbox 360. A. personal computer B. 3G mobile phone *C.video game console D. portable gaming devices 54._________ are played on coin-operated machines, typically installed in restaurants, bars and amusement arcades. A. PC games B.Handheld games *C. Arcade games D. Mobile phone games 55.The Snake series of games had been popular on many Nokia phones since the late 1990s. The Snake is a____ A. PC game B. Handheld game C. Arcade game *D. Mobile phone game 56.Her kid plays___ and plays it at any time. A. PC games *B. handheld games C. arcade games D. mobile phone games on that small machine. He brings that machine to everywhere 57.This____can work with Window XP, but it is faster if you have Window Vista. *A. PC game B. handheld game C. arcade game D. mobile phone game 58._____ allow you to play against other users in other parts of the world using the Internet. A. Arcade games B. Console games C. PC games *D. Massively multiplayer online games 59.To play a______ A. handheld game *B. console game you just need the games controller that came with your machine. C.PC game D. massively multiplayer online game 60._____ is the science of making devices from single atoms and molecules. A. Robotics *B. Nanotechnology C. Expert systems D. Artificial intelligence 61._____ is a computer with electronic parts that are so small that they can only be seen using a microscope. A. Appliance B. Pervasive computing *C. Nanocomputer D. Ubiquitous computing 62.The medical application of nanotechnology is called_____. *A. nanomedicine B. appliance C. expert systems D. biometrics 63._____ are chemical substances or materials that are manufactured and used at a very small scale. A .Nanotube B. Nanotransistor C. expert systems *D. Nanomaterials 64.Nano devices are measured in_____ *A. nanometers B. nanotubes C. nanotransistors D. nanobots . 65.The microscopic robots, built with nanotechnology are called____ A. robotics B. android *C. nanobots D. asimo . 66.Nanomaterials will be made from carbon atoms in the form of____ A. devices B. nanotransistors C. nanobots *D. nanotubes . 67.The science of making intelligent machines and programs is called____ A. robotics B.biometrics C.expert systems *D.Artificial Intelligence 68.The branch of .mechanical engineering, electrical engineering and computer science that deals with thedesign, construction, operation, and application of robots is called___ . *A. robotics B. android c. nanobots D. artificial Intelligence 69.A robot that resembles a human is called____ A. robotics *B. android c. nanobots D. Asimo . 70.In the future, doctors will be using______to diagnose illnesses. A. robotics B. nanobots *c. expert systems D. artificial Intelligence 71.______uses computer technology to identify people based on physical characteristics such as fingerprints,facial features, voice, iris and retina patterns. *A. Biometrics B. Pervasive computing c. Ubiquitous computing D. Nanocomputers 72._____ is the new approach in which computer functions are integrated into everyday life, often in an invisible way. A. Nanocomputers B. Pervasive computing c. Ubiquitous computing *D. B & c are correct 73.In the ideal smart home,______and electronic devices work in sync to keep the house secure. A. nanobots B. nanotransistors c. nanotubes *D.appliances