Svr2012InstallWeek03
advertisement

Week 3
Objectives
• Manage User Accounts
• Manage Group Accounts
• Manage Computer Accounts
• Delegation
• Use Commandline Tools and Windows PowerShell
for AD DS Administration
• Performe Bulk Operations with Windows
PowerShell
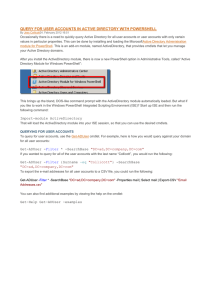
AD DS Administration Tools
To manage AD DS objects, you can use the following
graphical tools:
• Active Directory Administration snap-ins
• Active Directory Administrative Center
You can also use the following command-line tools:
• Active Directory module in Windows PowerShell
• Directory Service commands
Creating User Profiles
Group Types
• Distribution groups
• Used only with email applications
• Not security-enabled (no SID);
cannot be given permissions
• Security groups
• Security principal with an SID;
can be given permissions
• Can also be email-enabled
Group Scopes
Group scope
Members from
same domain
Members
from
domain in
same forest
Members
from trusted
external
domain
Can be
assigned
permissions to
resources
Local
U, C,
GG, DLG, UG
and local users
U, C,
GG, UG
U, C,
GG
On the local
computer only
Domain
Local
U, C,
GG, DLG, UG
U, C,
GG, UG
U, C,
GG
Anywhere in the
domain
Universal
U, C,
GG, UG
U, C,
GG, UG
N/A
Anywhere in the
forest
Global
U, C,
GG
N/A
N/A
Anywhere in the
domain or a
trusted domain
U
C
GG
User
Computer
Global Group
DLG
UG
Domain Local Group
Universal Group
Implementing Group Management
I
Identities
Users or computers,
which are members of
G
Global groups
Which collect members
based on members’ roles,
which are members of
DL Domain local groups
Which provide management
such as resource access,
which are
A
Assigned access to a resource
In a multi domain forest, it is
IGUDLA, where U is Universal
Sales
(Global Group)
Auditors
(Global Group)
ACL_Sales_Read
(Domain Local Group)
Default Groups
• Carefully manage the default groups that provide
administrative privileges, because these groups:
Typically have broader privileges than are necessary for
most delegated environments
• Often apply protection to their members
•
Group
Location
Enterprise Admins
Users container of the forest root domain
Schema Admins
Users container of the forest root domain
Administrators
Built-in container of each domain
Domain Admins
Users container of each domain
Server Operators
Built-in container of each domain
Account Operators
Built-in container of each domain
Backup Operators
Built-in container of each domain
Print Operators
Built-in container of each domain
Special Identities
• Special identities:
Are groups for which membership is controlled by the
operating system
• Can be used by the Windows Server operating system to
provide access to resources:
•
•
•
Based on the type of authentication or connection
Not based on the user account
• Important special identities include:
Anonymous Logon
• Authenticated Users
• Everyone
• Interactive
• Network
•
Specifying the Location of Computer Accounts
• Best practice is to create OUs for
computer objects
Servers
• Typically subdivided by server role
• Client computers
• Typically subdivided by region
•
• Divide OUs:
By administration
• To facilitate configuration with Group
Policy
•
Computer Accounts and Secure Channels
• Computers have accounts
sAMAccountName and password
• Used to create a secure channel between the computer and a
domain controller
•
• Scenarios where a secure channel can be broken
Reinstalling a computer, even with same name, generates a
new SID and password
• Restoring a computer from an old backup, or rolling back a
computer to an old snapshot
• Computer and domain disagree about what the password is
•
Resetting the Secure Channel
• Do not remove a computer from the domain and
rejoin
•
This process creates a new account, resulting in new SID
and lost group memberships
• Options for resetting the secure channel:
• Active Directory Users and Computers
• DSMod.exe
• NetDom.exe
• NLTest.exe
• Windows PowerShell
Effective AD DS Permissions
Permissions assigned to users and groups accumulate
Best practice is to assign permissions to groups, not to
individual users
In the event of conflicts:
• Deny permissions override Allow permissions
• Explicit permissions override Inherited permissions
• Explicit Allow overrides Inherited Deny
To evaluate effective permissions, you can use:
• The Effective Permissions tab
• Manual analysis
What Are DS Commands?
Windows Server 2012 includes command-line tools
that are suitable for use in scripts
• Examples
• To modify the department of a user account, type:
Dsmod user "cn=Joe Healy,ou=Managers,
dc=adatum,dc=com" –dept IT
•
To display the email of a user account, type:
Dsget user "cn=Joe Healy,ou=Managers,
dc=adatum,dc=com" –email
•
To delete a user account, type:
Dsrm "cn=Joe Healy,ou=Managers,dc=adatum,dc=com"
•
To create a new user account, type:
Dsadd user "cn=Joe Healy,ou=Managers,dc=adatum,dc=com"
What Is Csvde?
Export
csvde.exe
filename.csv
Import
Use csvde to export objects to a .csv file:
• -f filename
• -d RootDN
• -p SearchScope
• -r Filter
• -l ListOfAtrributes
Use csvde to create objects from a .csv file:
csvde –i –f filename –k
AD DS
What Is Ldifde?
Export
ldifde.exe
filename.ldif
Import
AD DS
Use ldifde to export objects to a LDIF file:
• -f filename
• -d RootDN
• -r Filter
• -p SearchScope
• -l ListOfAttributes
• -o ListOfAttributes
Use ldifde to create, modify, or delete objects:
ldifde –i –f filename –k
Using Windows PowerShell Cmdlets to
Manage User Accounts
Cmdlet
New-ADUser
Set-ADUser
Remove-ADUser
Set-ADAccountPassword
Set-ADAccountExpiration
Unlock-ADAccount
Enable-ADAccount
Disable-ADAccount
Description
Creates user accounts
Modifies properties of user accounts
Deletes user accounts
Resets the password of a user account
Modifies the expiration date of a user account
Unlocks a user account after it has become
locked after too many incorrect login attempts
Enables a user account
Disables a user account
New-ADUser "Sten Faerch" –AccountPassword (Read-Host
–AsSecureString "Enter password") -Department IT
Using Windows PowerShell Cmdlets to
Manage Groups
Cmdlet
Description
New-ADGroup
Set-ADGroup
Get-ADGroup
Remove-ADGroup
Add-ADGroupMember
Get-ADGroupMember
Remove-ADGroupMember
Add-ADPrincipalGroupMembership
Get-ADPrincipalGroupMembership
Creates new groups
Modifies properties of groups
Displays properties of groups
Deletes groups
Adds members to groups
Displays membership of groups
Removes members from groups
Adds group membership to objects
Displays group membership of objects
Remove-ADPrincipalGroupMembership
Removes group membership from an object
New-ADGroup –Name "CustomerManagement" –Path
"ou=managers,dc=adatum,dc=com" –GroupScope Global
–GroupCategory Security
Add-ADGroupMember CustomerManagement –Members "Joe"
Using Windows PowerShell Cmdlets to
Manage Computer Accounts
Cmdlet
Description
New-ADComputer
Set-ADComputer
Creates new computer accounts
Modifies properties of computer
accounts
Get-ADComputer
Displays properties of computer
accounts
Remove-ADComputer
Deletes computer accounts
Test-ComputerSecureChannel
Verifies or repairs the trust relationship
between a computer and the domain
Reset-ComputerMachinePassword Resets the password for a computer
account
New-ADComputer –Name LON-SVR8 -Path
"ou=marketing,dc=adatum,dc=com" -Enabled $true
Test-ComputerSecureChannel -Repair
Using Windows PowerShell Cmdlets to
Manage OUs
Cmdlet
Description
New-ADOrganizationalUnit
Set-ADOrganizationalUnit
Creates organizational units
Modifies properties of organizational
units
Views properties of organizational units
Deletes organizational units
Creates organizational units
Get-ADOrganizationalUnit
Remove-ADOrganizationalUnit
New-ADOrganizationalUnit
Set-ADOrganizationalUnit
Get-ADOrganizationalUnit
Modifies properties of organizational
units
Views properties of organizational units
New-ADOrganizationalUnit –Name Sales
–Path "ou=marketing,dc=adatum,dc=com"
–ProtectedFromAccidentalDeletion $true
What Are Bulk Operations?
• A bulk operation is a single action that changes
multiple objects
• The process for performing a bulk operation is:
1. Define a query
2. Modify the objects defined by the query
• You can perform bulk operations by using:
• Graphical tools
• Command-line tools
• Scripts
Querying Objects with Windows PowerShell
Show all the properties for a user account:
Parameter
Description
Get
ADUser Administrator
Properties
*
SearchBase
Defines the AD DS path
to begin searching.
SearchScope
Defines
at what level
SearchBase aOU
search
should
Show
all the user
accounts
inbelow
the the
Marketing
and
all be
itsperformed.
subcontainers:
ResultSetSize
Defines how many objects to return in response to a query.
Properties
Defines which object properties to return and display.
Get ADUser –Filter * SearchBase
"ou=Marketing,dc=adatum,dc=com" SearchScope subtree
Operator
Description
-ne
Not equal to
Show all of the user accounts with a last logon date older than
-eq
Equal to
a specific date:
Less than
Get ADUser -lt
Filter {lastlogondate
lt "January 1, 2012"}
-le
Less than or equal to
-gtuser accounts
Greater
Show all of the
in than
the Marketing department that
-ge date older
Greater
equal to date:
have a last logon
thanthan
a or
specific
-like
Uses wildcards for pattern matching
Get ADUser Filter {(lastlogondate lt "January 1, 2012") and
(department eq "Marketing")}
Modifying Objects with Windows PowerShell
Use the pipe character ( | ) to pass a list of objects to a
cmdlet for further processing
Get -ADUser -Filter {company -notlike "*"} |
Set-ADUser -Company "A. Datum"
Get -ADUser -Filter {lastlogondate -lt "January 1,
2012"} | Disable-ADAccount
Get Content C:\users.txt | Disable ADAccountGet
Content C:\users.txt | Disable ADAccount
Working with CSV Files
The first line of a .csv file defines the names of the
columns
FirstName,LastName,Department
Greg,Guzik,IT
Robin,Young,Research
Qiong,Wu,Marketing
A foreach loop processes the contents of a .csv that
have been imported into a variable
$users=Import-CSV C:\users.csv
Foreach ($i in $users) {
Write-Host "The first name is:" $i.FirstName
}