COS 338_day20
advertisement
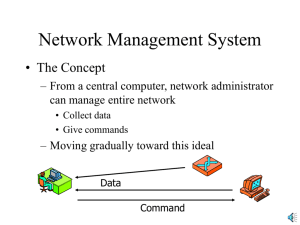
COS 338 Day 20 DAY 19 Agenda Assignment 6 Due Lab 7 due next Monday Assignment 7 Posted Due Dec 1 Capstone Progress reports due Exam 3 on November 21 Chap 8&9, open book, open notes, 60 min, 25 M/c questions. Quiz can be taken from anywhere. Availability, time and password will be sent via WebCT e-mail Today we will do discuss network management 2 Network Management Chapter 10 Copyright 2004 Prentice-Hall Panko’s Business Data Networks and Telecommunications, 5th edition Cost Figure 10-1: Network Demand Versus Budget Trends Money/ Demand User Demand Budget Time 5 Figure 10-2: Cost Issues The Importance of Costs Exploding demand Slow budget growth Falling hardware costs help, but software costs fall more slowly, and labor costs are rising Select the least expensive technology that will fully meet user needs 6 Figure 10-2: Cost Issues Non-Technology Costs Labor costs High, and unit labor costs are rising over time Rising Health Care costs are also a factor Often dominate total costs Carrier fees Recurring contractual charges 7 Figure 10-2: Cost Issues Total Cost of Ownership Fully configured cost of hardware Base price plus necessary options Often much higher than base price Fully configured cost of software Initial installation costs Vendor setup costs IT and end-user labor 8 Figure 10-2: Cost Issues Total Cost of Ownership Ongoing costs Upgrades Labor costs often exceed all other costs Immature products have very high labor costs Total cost of ownership (TCO): total of all costs over life span 9 Figure 10-3: Multiyear Cost Analysis: Total Cost of Ownership (TCO) Year 1 Year 2 Year 3 Year 4 $200,000 15,000 15,000 15,000 245,000 85,000 9,000 9,000 9,000 112,000 $100,000 10,000 10,000 10,000 130,000 Software Options 50,000 10,000 10,000 10,000 Technology Subtotal 435,000 44,000 44,000 44,000 567,000 Base Hardware Hardware Options Base Software Total 80,000 10 Figure 10-3: Multiyear Cost Analysis: Total Cost of Ownership (TCO) Year 1 Year 2 Year 3 Year 4 Total Planning and Development 75,000 75,000 Implementation 50,000 50,000 Ongoing IT Labor Ongoing User Labor Labor Subtotal Total 100,000 75,000 75,000 75,000 325,000 50,000 25,000 25,000 25,000 125,000 275,000 100,000 100,000 100,000 575,000 710,000 144,000 144,000 144,000 1,142,000 Note: The total cost of ownership is $1,142,000. 11 Network Simulation Figure 10-4: Network Simulation Simulation Build a model, study its implications More economical to simulate network alternatives than to build them Opnet GURU is a Simulation tool 13 Figure 10-4: Network Simulation What is: the existing situation Net 1 Net 4 Utilization in Peak Hour 95% Net 2 Net 3 Too high! Net 5 Net 6 14 Figure 10-4: Network Simulation What-if: See the Impact of a Change Net 1 Net 4 Added Router Net 2 Net 3 Added Link Est. Utilization in Peak Hour 70% Net 5 Net 6 15 Figure 10-4: Network Simulation Simulation Purposes Comparing alternatives to select the best one Base case and sensitivity analysis to see what will happen if the values of variables were varied over a range (+ or –- a certain amount) Anticipating problems, such as bottlenecks Planning for growth, to anticipate areas where more capacity is needed 16 Figure 10-4: Network Simulation Before the Simulation, Collect Data Data must be good Otherwise, GIGO (garbage in, garbage out) Collect data on the current network Forecast growth 17 Figure 10-4: Network Simulation The Process (Based on OPNET IT Guru) Add nodes to the simulation work area (clients, servers, switches, routers, etc.) Specify the topology with transmission lines (including line speeds) Configure the nodes and transmission lines (IP Time-to-Live value, etc.) Add applications, which generate traffic data 18 Figure 10-4: Network Simulation The Process Run the simulation for some simulated period of time Examine the output to determine implications Validate the simulation (compare with reality if possible to see if it is correct) What-if analysis Application performance analysis (OPNET ACE) 19 Figure 10-5: OPNET IT Guru Node Template 20 Figure 10-6: Configuring a Frame Relay CIR 21 Figure 10-7: Configured Simulation Model 22 Figure 10-8: What-If Analysis 23 IP Subnetting Figure 10-9: IP Subnetting Step Description 1 Total size of IP address (bits) 2 Size of network part assigned to firm (bits) 16 8 3 Remaining bits for firm to assign 16 24 4 Selected subnet/host part sizes (bits) 32 8/8 6/10 12/12 8/16 A firm is given its network size; it chooses its subnet size. Total is 32 bits, so big subnet size gives many subnets but few hosts. 25 Figure 10-9: IP Subnetting Step Description 5 Possible number of subnets (2^N-2) 254 62 4,094 254 (2^8-2) (2^6-2) (2^12-2) (2^8-2) 6 Possible number of hosts 254 1,022 4,094 65,534 per subnet (2^N-2) (2^8-2) (2^10-2) (2^12-2) (2^16-2) Subnet Calculator http://www.solarwinds.net/free/ 26 27 Directory Servers Store corporate information Hierarchical organization of content LDAP standard to access directory servers Figure 10-10: Hierarchical Directory Server Name Space Directory Server with Hierarchical Object Structure LDAP Request: Get e-mail.Brown.faculty. University of Waikiki (O) CN=Waikiki business.waikiki Astronomy Business (OU) (OU) LDAP Response: Brown@waikiki.edu O=organization OU=organizational unit CN=common name LDAP=Lightweight Directory Access Protocol CprSci (OU) Staff Faculty Routers Chun Brown Ochoa CN Brown E-Mail Ext Brown@waikiki.edu x6782 29 Configuring Routers Needed to set up new routers Needed to change operation of old routers Time consuming and an important skill Figure 10-11: Cisco Internetwork Operating System (IOS) Command Line Interface (CLI) Command Comment Router>enable[Enter] Router> is the prompt. The “>” shows that the user is in non-privileged mode. Enables privileged mode so that user can take supervisory actions. User must enter the enable secret. All commands end with [Enter]. Enter is not shown in subsequent commands. 31 Figure 10-11: Cisco Internetwork Operating System (IOS) Command Line Interface (CLI) Command Comment Router#hostname julia Prompt changes to “#” to indicate that user is in privileged mode. User gives the router a name, julia. julia#config t Enter configuration mode. The t is an abbreviation for terminal. 32 Figure 10-11: Cisco Internetwork Operating System (IOS) Command Line Interface (CLI) Command Comment julia(config)#int e0 Prompt changes to julia(config) to indicate that the user is in configuration mode. User wishes to configure Ethernet interface 0. (Router has two Ethernet interfaces, 0 and 1.) julia(config-if)#ip address 10.5.0.6 255.255.0.0 User gives the interface an IP address and a subnet mask. (Every router interface must have a separate IP address.) The subnet is 5. 33 Figure 10-11: Cisco Internetwork Operating System (IOS) Command Line Interface (CLI) Command Comment julia(config-if)#no shutdown This is an odd one. The command to shut down an interface is “shutdown”. Correspondingly, “no shutdown” turns the interface on. julia(config-if)# Ctrl-Z User types Ctrl-Z (the key combination, not the letters) to end the configuration of e0. julia(config)#int s1 User wishes to configure serial interface 1. (Router has two serial interfaces, 0 and 1.) 34 Figure 10-11: Cisco Internetwork Operating System (IOS) Command Line Interface (CLI) Command Comment julia(config-if)#ip address 10.6.0.1 255.255.0.0 User gives the interface an IP address and subnet mask. The subnet is 6. julia(config-if)#no shutdown Turns on s1. julia(config-if)# Ctrl-Z Ends the configuration of s1. julia# router rip Enables the Router Initiation Protocol (RIP) routing protocol. 35 Figure 10-11: Cisco Internetwork Operating System (IOS) Command Line Interface (CLI) Command Comment julia#disable Takes user back to non-privileged mode. This prevents anyone getting access to the terminal from making administrative changes to the router. julia> 36 Network Management Utilities Figure 10-12: Network Management Utilities Network management utilities are programs to help network managers administer the network Security Management tools can be used to make attacks Policies should limit these tools to certain employees and for certain purposes Firewalls block many network management tools to avoid attacks 38 Figure 10-12: Network Management Utilities Host Diagnostic Tools Network Setup Wizard works most of the time; need tools if it does not Testing the connection Open a connection to a website using a browser Ping a host to see if latency is acceptable 39 Figure 10-12: Network Management Utilities Host Diagnostic Tools Loopback testing and ipconfig/winipconfig Go to the command line Ping 127.0.0.1. This is the loopback interface (you ping yourself) For detailed information: ipconfig /all or winipconfig (older versions of Windows) 40 Figure 10-12: Network Management Utilities Host Diagnostic Tools Checking the NIC in Windows XP Right click on a connection and select Properties Under the name of the NIC, hit the Configuration button The dialog box that appears will show you the status of the NIC It also offers a Troubleshooting wizard if the NIC is not working 41 Figure 10-13: NIC Configuration Dialog Box 42 Figure 10-12: Network Management Utilities Host Diagnostic Tools Packet capture and display programs Capture data on individual packets Allows extremely detailed traffic analysis Look at individual packet data and summaries WinDUMP is a popular packet capture and display program on Windows 43 Figure 10-12: Network Management Utilities Command prompt>tcpdump www2.pukanui.com 7:50.10.500020 10.0.5.3.62030 > www2.pukanui.com.http: S 800000050:800000050(0) win 4086 <mss1460> 7:50.10.500020 is the time 10.0.5.3.62030 is the source host (62030 is the port number) www2.pukanui.com.http is the destination host (HTTP) WinDUMP from Ch. 8a 44 Figure 10-12: Network Management Utilities 7:50.10.500020 10.0.5.3.62030 > www2.pukanui.com.http: S 800000050:800000050(0) win 4086 <mss1460> S indicates that the SYN flag is set 800000050:800000050(0) Seq No and length Win 4086 is the window size (for flow control) <mss1460> is the option for maximum segment size (size of the TCP data field) WinDUMP from Ch. 8a 45 Figure 10-12: Network Management Utilities 7:50.10.500030 www2.pukanui.com.http > 10.0.5.3.62030 : S 300000030:300000030(0) ack 800000051 win 8760 <mss1460> SYN/ACK from the webserver 7:50.10.500040 10.0.5.3.62030 > www2.pukanui.com.http: . ack 1 win 4086 ACK to finish 3-way open WinDUMP from Ch. 8a 46 Figure 10-12: Network Management Utilities 7:50.10.500050 10.0.5.3.62030 > www2.pukanui.com.http: P 1:100(100) 7:50.10.500060 www2.pukanui.com.http > 10.0.5.3.62030 : . ack 101 win 9000 7:50.10.500070 www2.pukanui.com.http > 10.0.5.3.62030 : . 1:1000(999) 7:50.10.500080 10.0.5.3.62030 > www2.pukanui.com.http: . ack 1001 win 4086 WinDUMP from Ch. 8a 47 Figure 10-12: Network Management Utilities Host Diagnostic Tools Traffic summarization Shows statistical data on traffic going into and out of the host EtherPeek is a popular commercial traffic summarization program 48 Figure 10-14: EtherPeek Packet Capture and Summarization Program 49 Figure 10-12: Network Management Utilities Host Diagnostic Tools Connection analysis At the command line, Netstat shows active connections This can identify problem connections Spyware running on Port 3290 50 Figure 10-12: Network Management Utilities Route Analysis Tools To test the route to another host Ping tests gives the latency of a whole route Tracert gives latencies to router along the path Ping 275 ms 250 ms Tracert 25 ms 75 ms 225 ms 150 ms (Problem?) 51 Figure 10-12: Network Management Utilities Network Mapping Tools To understand how the network is organized Discovering IP addresses with active devices Fingerprinting them to determine their operating system (client, server, or router) A popular network mapping program is Nmap (Figure 10-4) 52 Figure 10-12: Network Management Utilities IP Range to Scan Type of Scan Identified Host and Open Ports 53 Figure 10-16: Simple Network Management Protocol (SNMP) Simple Network Management Protocol (SNMP) Standard for managing remote devices in a network Collects information from remote devices to give the network administrator an overview of the network Optionally, allows the network administrator to reconfigure remote devices Potential for strong labor cost savings 54 Figure 10-16: Simple Network Management Protocol (SNMP) Network Management Software (Manager) Managed Device Manager manages multiple managed devices from a central location RMON Probe 55 Figure 10-16: Simple Network Management Protocol (SNMP) Network Management Software (Manager) Network Management Agent (Agent), Objects Network Management Agent (Agent), Objects Manager talks to an network management agent on each managed device RMON Probe 56 Figure 10-16: Simple Network Management Protocol (SNMP) Network Management Software (Manager) Network Management Agent (Agent), Objects Network Management Agent (Agent), Objects RMON (remote monitoring) probe is a special agent that collects data about multiple devices in a region of in the network. It is like a local manager that can be queried by the main manager. RMON Probe 57 Figure 10-16: Simple Network Management Protocol (SNMP) Network Management Software (Manager) Management Information Base (MIB) Management Information Base (MIB) MIB stores data about devices. MIB on manager stores all. MIB on device stores local information Management Information Base (MIB) RMON Probe 58 Figure 10-16: Simple Network Management Protocol (SNMP) Network Management Software (Manager) Management Information Base (MIB) Simple Network Management Protocol (SNMP) Management Information Base (MIB) Command (Get, Set, etc.) Response Management Information Base (MIB) Trap RMON Probe 59 Figure 10-17: SNMP Object Model SNMP Object Model Management Information Base (MIB) The MIB database schema Defines objects (parameters) about which information is stored for each managed device SNMP System Objects System name System description System contact person System uptime (since last reboot) 60 Figure 10-17: SNMP Object Model SNMP IP Objects Management Information Base (MIB) Forwarding (for routers). Yes if forwarding (routing), No if not Subnet mask Default time to live Traffic statistics Number of discards because of resource limitations 61 Figure 10-17: SNMP Object Model SNMP IP Objects (Continued) Management Information Base (MIB) Number of discards because could not find route Number of rows in routing table Rows discarded because of lack of space Individual row data in the routing table 62 Figure 10-17: SNMP Object Model SNMP TCP Objects Management Information Base (MIB) Maximum / minimum retransmission time Maximum number of TCP connections allowed Opens / failed connections / resets Segments sent Segments retransmitted Errors in incoming segments No open port errors Data on individual connections (sockets, states) 63 Figure 10-17: SNMP Object Model SNMP UDP Objects Error: no application on requested port Traffic statistics Management Information Base (MIB) SNMP ICMP Objects Number of errors of various types 64 Figure 10-17: SNMP Object Model Management Information Base (MIB) SNMP Interface Objects (One per Port) Type (e.g., 69 is 100Base-FX; 71 is 802.11) Status: up / down / testing Speed MTU (maximum transmission unit—the maximum packet size) Traffic statistics: octets, unicast / broadcast / multicast packets Errors: discards, unknown protocols, etc. 65 Remote Switch and Router Management Figure 10-12: Network Management Utilities Remote Switch and Router Management Telnet Web interfaces SSH TFTP Saves money compared to traveling to device 67 Figure 10-18: Telnet, Web Management, SSH, and TFTP Telnet Remotely log into managed device as a dumb terminal Poor security Weak password authentication Passwords are sent in the clear, making them vulnerable to sniffers No encryption of traffic 68 Figure 10-18: Telnet, Web Management, SSH, and TFTP Web Interfaces Managed device contains a webserver Administrator connects to the managed device with a browser Can use SSL/TLS but typically does not 69 Figure 10-18: Telnet, Web Management, SSH, and TFTP SSH Secure shell protocol Similar to Telnet but highly secure Widely installed on Unix computers (including Linux computers) Software must be added to Windows devices 70 Figure 10-18: Telnet, Web Management, SSH, and TFTP TFTP Trivial File Transfer Protocol Similar to file transfer program but simpler Simple enough to implement on switches and routers Often used to download configurations to a switch or router from a server 71 Figure 10-18: Telnet, Web Management, SSH, and TFTP TFTP No password is needed Can be used by hackers to download attack programs Poor security makes TFTP very dangerous 72 Traffic Management Figure 10-19: Traffic Management Methods Traffic Management Capacity is expensive; it must be used wisely Especially in WANs 74 Figure 10-19: Traffic Management Methods Traditional Approaches Overprovisioning In Ethernet, install much more capacity than is needed most of the time This is wasteful of capacity Does not require much ongoing management labor 75 Figure 10-19: Traffic Management Methods Traditional Approaches Priority In Ethernet, assign priority to applications based on sensitivity to latency In momentary periods of congestion, send highpriority frames through Substantial ongoing management labor 76 Figure 10-19: Traffic Management Methods Traditional Approaches QoS Reservations In ATM, reserve capacity on each switch and transmission line for an application Allows strong QoS guarantees for voice traffic Highly labor-intensive Data gets the scraps—capacity that is not reserved for voice 77 Figure 10-19: Traffic Management Methods Traffic Shaping The Concept Control traffic coming into the network at access switches Filter out unwanted applications Give a maximum percentage of traffic to other applications 78 Figure 10-19: Traffic Management Methods Traffic Shaping Advantages and Disadvantages Traffic shaping alone reduces traffic coming into the network to control costs Very highly labor intensive Creates political battles (as do priority and QoS reservations to a lesser degree) 79 Topics Covered Topics Covered Cost Exploding demand, slow budget growth Hardware, software, labor costs Fully-configured hardware versus base prices Total cost of ownership: cost over entire life cycle Network Simulation Model the network on a computer Explore alternatives Cheaper than building alternatives 81 Topics Covered IP Subnet Planning Organization is given its network part Divides remaining bits of IP address into subnet and host part Must balance number of subnets with hosts per subnet Directory Servers Hierarchical data storage LDAP 82 Topics Covered Configuring Routers Time-consuming; important skill Cisco IOS is the dominant router operating system Command-line interface (CLI) Network Management Utilities Both network managers and hackers love them Host diagnostic tools. Is the connection working? 127.0.0.1 Windows XP: Connection Properties 83 Topics Covered Network Management Utilities Packet capture and display programs Traffic summarization program (Etherpeek) Netstat to show active connections Route analysis: Ping and Tracert Network mapping tools (nmap) 84 Topics Covered Simple Network Management Protocol (SNMP) Manager, managed devices, agents Get and set commands MIB RMON probe SNMP object model (MIB schema) 85 Topics Covered Remote Switch and Management Utilities Saves money compared to traveling to device Telnet Web interfaces SSH TFTP 86 Topics Covered Traffic Management Capacity is expensive on WANs Overprovisioning is too wasteful on WANs Priority is good but expensive to manage QoS reservations only allow strong guarantees for some services; rest get the scraps Traffic shaping: only select certain type of traffic Drop certain traffic or limit it to a certain amount 87