LAN
advertisement

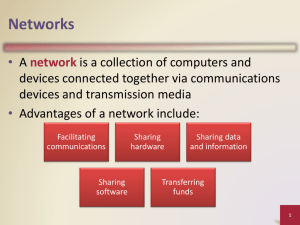
Information Technology in Theory By Pelin Aksoy and Laura DeNardis Chapter 11 Local Area Networks Objectives • Gain familiarity with the most popular types of local area networks (LANs), with a focus on Ethernet • Understand LAN design characteristics, including topology, access mechanism, physical transmission media, and equipment Information Technology in Theory 2 Objectives (continued) • Explain what a frame format is and what purpose it serves in LANs • Define the functions of LAN operating systems • Understand the technical architecture of Wi-Fi Information Technology in Theory 3 Network Categories • • • • • Local area networks (LANs) Wide area networks (WANs) Personal area networks (PANs) Metropolitan area networks (MANs) Campus area networks (CANs) • Storage area networks (SANs) Information Technology in Theory 4 Defining LANs • LAN—a network that spans a confined geographical distance, such as a building or home • WAN—a network that spans a larger geographical area, such as a city, nation, or the world at large Information Technology in Theory 5 Resources Accessed via LANs Information Technology in Theory 6 LAN Design Characteristics • • • • • Physical topology Logical topology Access control and LAN switching LAN physical media and equipment LAN operating systems Information Technology in Theory 7 Physical Topology • A LAN’s physical topology refers to how the multiple devices (often called network nodes) are physically connected to each other – Star – Ring – Star-Wired Ring – Bus Information Technology in Theory 8 Star Topology Information Technology in Theory 9 Ring Topology Information Technology in Theory 10 Star-Wired Ring Topology Information Technology in Theory 11 Bus Topology Information Technology in Theory 12 Logical Topology • While the physical topology describes how network nodes are connected within the LAN, the logical topology dictates how information flows among the nodes • Common logical topologies for LANs – Bus – Ring – Star Information Technology in Theory 13 Access Control and LAN Switching • Access control mechanism – A procedure that specifies and enforces rules for when each device may transmit or receive information over a network – Token passing – CSMA/CD – CSMA/CA Information Technology in Theory 14 Token Passing • Uses a deterministic access method • Each node communicates only during its specified turn • A token, which is just a signal that comprises a specific bit pattern, is transmitted from one device to the next in a sequential pattern • When a device receives this signal, it “possesses the token,” meaning it may transmit information Information Technology in Theory 15 CSMA/CD • CSMA/CD is nondeterministic – Any device may transmit information at any given moment, provided that no signals are already being transmitted over the LAN • A node preparing to transmit information first “listens” to the network to determine whether transmissions are occurring • The node starts to transmit only if it detects that the network is free of transmissions Information Technology in Theory 16 CSMA/CA • In some LANs, such as wireless LANs, collisions cannot be detected • Using CSMA/CA, a node that has information to transmit first listens to the network to see if another node is transmitting • If the network is idle, it sends a “request to send” (RTS) packet to other nodes • The other nodes can then send a “clear to send” (CTS) packet, alerting the transmitting node that it is free to send data Information Technology in Theory 17 Gigabit LAN Switches Information Technology in Theory 18 LAN Switching Information Technology in Theory 19 LAN Physical Media and Equipment • • • • • • Network interface controller Transmission media Wiring hubs High-speed switches Routers Servers Information Technology in Theory 20 Network Interface Controller • Built into the computer’s motherboard • Basically a small card with a couple of integrated circuits and other electronic components • Provides the physical interface to a network medium or wireless LAN and supports an addressing system that is critical to the LAN’s operation Information Technology in Theory 21 Transmission Media • The most common LAN transmission media are free space, fiber-optic cable, twisted pair, or some combination • Many LANs connect devices using a combination of twisted pair cable and fiberoptic cable • WLANs use radio frequency communications rather than fiber-optic cable or copper cable Information Technology in Theory 22 LAN Operating Systems • Software • Sometimes called a network operating system (NOS) or a server operating system • Some computer operating systems, like UNIX, Linux, and Windows NT have built-in networking features • Other software, like Novell’s Netware, has specifically been designed as a LAN operating system Information Technology in Theory 23 LAN Operating Systems (continued) • Manage and control networked access to LAN resources such as printers, files, applications, and messaging services • Provide security by managing user directories, monitoring remote LAN access, and incorporating encryption and other security features • Provide network management, including diagnostic tools Information Technology in Theory 24 LAN Types • • • • Information Technology in Theory Ethernet Token ring FDDI Wireless LANs 25 LAN Characteristics • • • • • • • • • Shared or switched access method Topology (ring, bus, star) Medium (twisted pair, free space, fiber) Speed, distance Cost Performance, mobility Manageability Number of devices supported Frame format Information Technology in Theory 26 Ethernet LANs • Originally developed in 1976 by Bob Metcalfe at Xerox’s Palo Alto Research Center (PARC) • IEEE 802.3 standard • Commonly implemented over free space, twisted pair cable, or fiber-optic cable Information Technology in Theory 27 10/100-Mbps Switch Information Technology in Theory 28 Ethernet Frame Format Information Technology in Theory 29 Token Ring and FDDI • Not as popular as Ethernet • Token Ring – Ring configuration – Token passing access method • FDDI – Dual ring configuration – Fiber – Token passing access method Information Technology in Theory 30 Token Structure Information Technology in Theory 31 Token Ring Network Information Technology in Theory 32 Token Ring Frame Format Information Technology in Theory 33 FDDI LAN Information Technology in Theory 34 Wireless LANs • WLAN: wireless local area network • Use radio-frequency signals, rather than light or electricity over cables, to connect users within a limited geographical range Information Technology in Theory 35 Wi-Fi • Predominant WLAN implementation is known as Wi-Fi (wireless fidelity) • A catchy designation indicating that a product complies with the IEEE’s 802.11 wireless Ethernet specifications • Uses a carrier radio frequency in the unlicensed 2.4-GHz or 5-GHz range Information Technology in Theory 36 WLAN Standards • IEEE 802.11a—Wireless technology operating at a frequency of 5 GHz with a maximum data rate of 54 Mbps • IEEE 802.11b—Wi-Fi wireless technology operating at a frequency of 2.4 GHz with a maximum data rate of 11 Mbps • IEEE 802.11g—Backward compatible with 802.11b, operating at a frequency of 2.4 GHz and a maximum data rate of 54 Mbps Information Technology in Theory 37 WLAN Standards (continued) • IEEE 802.11i—Standards for wireless security mechanisms • IEEE 802.15—Known as WPAN, or wireless personal area networks • IEEE 802.16—WiMAX, an emerging technology that seeks to provide high-speed wireless access over much longer distances than implementations of the IEEE 802.11 standards Information Technology in Theory 38 Personal WLANs • A home-based wireless LAN uses a wireless access point (WAP) – A device that connects wireless computers to a wired network to enable high-speed Internet access and other services • Laptops with an installed wireless adapter then communicate with the WAP over the 2.4-GHz or 5-GHz frequency range Information Technology in Theory 39 Home LAN Implementation Information Technology in Theory 40 Business WLAN Implementation Information Technology in Theory 41 WLAN Advantages • Mobility • Flexibility Information Technology in Theory 42 WLAN Disadvantages • Security • Range limitations • Bandwidth • Manageability Information Technology in Theory 43 Municipal Broadband Wireless • Some cities and municipalities offer public Internet access via Wi-Fi network access points in parks, libraries, and other public locations • These networks are driven by economic, political, and technical factors Information Technology in Theory 44 Summary • A network shares information using a set of hardware and software designed to interconnect multiple computers, communication devices, and other types of devices • Categorizing networks is somewhat arbitrary, but in the networking industry, the most common categories are local area networks (LANs) and wide area networks (WANs) Information Technology in Theory 45 Summary (continued) • LANs are networks that span a relatively small geographical area, such as the floor of an office or a house; LANs interconnect local computing resources and provide WAN access • WANs are networks that span a large geographical area such as a city, a country, or the world at large – The Internet is the most important example of a WAN – Chapter 12 discusses WANs in detail Information Technology in Theory 46 Summary (continued) • Some design characteristics of LANs include topology (such as bus, star, and ring), access method (such as CSMA/CD, CSMA/CA, or token passing), and type of medium (wireless, fiber, twisted pair) • Ethernet, including switched Ethernet, has become the most prevalent type of local area network • Some wireless local area networks (WLANs) include the IEEE 802.11b and IEEE 80211g standards, more commonly called Wi-Fi – WLANs have great advantages, including mobility and flexibility, but they also present security challenges Information Technology in Theory 47