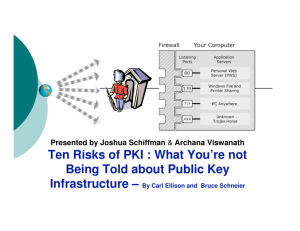
Public Key Infrastructure
advertisement

Public Key Infrastructure July 2011 Topics The need of PKI Trust Model PKI Structures CA types PGP Public Key Distribution issue Public Key cryptography solves the problem of Confidentiality, Integrity Authenticity Non-repudiation But how to ensure the public key is not faked? Eve creates a pair of keys (private/public) and tells everyone that the public key he generated belongs to Alice People send confidential stuff to Alice Alice cannot read (missing of the private key) Eve reads Alice’s messages 3 PKI PKI is a group of solutions for key distribution problems and other issues: Key generation Certificate generation, revocation, validation Managing trust Using Certificates 4 How to Verify a Public Key? Two approaches: Before using anyone public key: Meet to get the right one Have the public key sent in storage device using registered mail (if you trust registered mail) You can use the telephone (if you trust the telephone) Contact someone already trust to certify that the key really belongs to real owner By checking for a trusted digital signature on the key That’s were certificates play a role 5 Topics The need of PKI Trust Model PKI Structures CA types PGP Trust Models Web-of-Trust P2P model for key certification based on friends and friends of friends Individuals digitally sign each other keys You trust implicitly keys signed by some of your friends Used by “Pretty Good Privacy” (PGP) Trusted Authority + Path of Trust (CAs) A trusted agent who certifies public keys for general use Everyone trusts the root Certificate Authority (Verisign, Thawte, BT etc.) CA digitally signs keys of anyone having checked their credentials by traditional methods CA may even nominate others to be CAs 7 CA model (Trust model) Root Certificate CA Certificate Server Cert. 8 Server Cert. CA Certificate Server Cert. Server Cert. Web of Trust model B A Alice Bob D C 9 Trust Models Issues Web-of-trust Time-consuming, requires lots of work Works well in small or high connected worlds How to verify a public key from someone who don’t know before Certification authorities “big brothers” that everyone must trust Simpler model to deploy 10 A Fully Functional PKI Certification authority Certificate repository Certificate revocation Key backup and recovery Automatic key update Key history management Cross-certification Support for non-repudiation Time stamping Client software 11 Topics The need of PKI Trust Model PKI Structures CA types PGP PKI Major Parts PKI is a system that uses public-key encryption and digital certificates to achieve secure Internet services. There are 4 major parts in PKI. 13 Certification Authority (CA) A directory Service Services, Web servers Business Users PKI Structure Certification Authority Directory services Public/Private Keys User 14 Services, Webservers Storing Certificates and Keys Certificates need to be stored so that interested users can obtain them Keys need to be stored for data recovery purposes This weakens the system, but is a necessity This is a function of most certificate servers offer This is not an issue. Certificates are “public” Those servers are also responsible for issuing, revoking, signing etc. of certs But this requires the certificate server to generate the key pairs 15 Example (wrong) User generates a key pair Priv Public key is submitted to CA for certification pub pub DS Cert Certificate is sent to the user Certification Server 16 Example (Good) This model allows key recovery CA generates a key pair User request a certificate to CA pub Priv CA generates certificate pub Private Key and Certificate are sent to the user Certification Server 17 DS Cert SSL with PKI Server authentication is necessary for a web client to identify the web site it is communicating with To use SSL, a special type of digital certificate – “Server certificate” is used Get a server certificate from a CA Install a server certificate at the Web server Enable SSL on the Web site 18 Topics The need of PKI Trust Model PKI Structures CA types PGP Single CA A CA that issues certificates to users and systems, but not to other CAs – Easy to build – Easy to maintain – All users trust this CA – Paths have one certificate and one CRL – Doesn’t scale particularly well 20 Hierarchical PKI CAs have a hierarchical relationship (as in a tree) All CAs trust the root CA Root’s is self-signed Root CA certifies its child CAs, and they in turn certify their child CAs, and so on. Easy to establish/verify trust relationship between any two CAs 21 X509 PKI – Approach to Trust Why should I trust a CA? Cross-certification Topics The need of PKI Trust Model PKI Structures CA types PGP Pretty Good Privacy (PGP) Release in June 1991 by Philip Zimmerman (PRZ) PGP is a hybrid cryptosystem that allows user to encrypt and decrypt Use session key “a random generated number from the mouse movement or keystrokes” 24 PGP Public Key Philip R Zimmermann's Public Keys Current DSS/Diffie-Hellman Key: Key fingerprint: 055F C78F 1121 9349 2C4F 37AF C746 3639 B2D7 795E -----BEGIN PGP PUBLIC KEY BLOCK----Version: PGP 7.0.3 mQGiBDpU6CcRBADCT/tGpBu0EHpjd3G11QtkTWYnihZDBdenjYV2EvotgRZAj5h4ewprq1u/zqzGBYpiYL/9j+5XDFcoWF24bzsUmHXsbDSiv+XEyQND1 GUdx4wVcEY5rNjkArX06XuZzObvXFXOvqRj6LskePtw3xLf5uj8jPN0Nf6YKnhfGIHRWQCg/0UAr3hMK6zcA/egvWRGsm9dJecD/18XWekzt5JJeK3febJO/ 3Mwe43O6VNOxmMpGWOYTrhivyOb/ZLgLedqX+MeXHGdGroARZ+kxYq/a9y5jNcivD+EyN+IiNDPD64rl00FNZksx7dijD89PbIULDCtUpps2J0gk5inR+yzi nf+jDyFnn5UEHI2rPFLUbXWHJXJcp0UBACBkzDdesPjEVXZdTRTLk0sfiWEdcBM/5GpNswMlK4A7A6iqJoSNJ4pO5Qq6PYOwDFqGir19WEfoTyHW0kxi pnVbvq4q2vAhSIKOqNEJGxg4DTEKecf3xCdJ0kW8dVSogHDH/c+Q4+RFQq/31aev3HDy20YayxAE94BWIsKkhaMyokAYQQfEQIAIQUCOlTwWwIHABc MgBE/xzIEHSPp6mbdtQCcnbwh33TcYQAKCRDHRjY5std5Xle4AKCh1dqtFxD/BiZMqdP1eZYG8AZgTACfU7VX8NpIaGmdyzVdrSDUo49AJae0IlBoaWx pcCBSLiBaaW1tZXJtYW5uIDxwcnpAbWl0LmVkdT6JAFUEEBECABUFAjpU6CcFCwkIBwMCGQEFGwMAAAAACgkQx0Y2ObLXeV5WUQCfWWfTDHz SezrDawgN2Z4Qb7dHKooAoJyVnm61utdRsdLr2e6QnV5Z0yjjiQBGBBARAgAGBQI6VOkSAAoJEGPLaR3669X8JPcAnim4+Hc0oteQZrNUeuMSuirNVUr 7AKC1WXJI7gwMq0Agz07hQs++POJBMokARgQQEQIABgUCOlcobQAKCRDXjLzlZqdLMVBtAKDa5VPcb6NVH6tVeEDJUv+tBjp6oACeLoNtfbs2rvJkgK DHWEIDmJdgy2GJAD8DBRA6WP4Y8CBzV/QUlSsRAkmdAKC3TfkSSeh+poPFnMfW+/Y/+AAEEpGSUYAAQEAAAEAAQAA/9sAQwAKBwcIBwYKCAgI CwoKCw4YEA4NDQ4dFRYRGCMfJSQiHyIhJis3LyYpNCkhIjBBMTQ5Oz4+PiUuRElDPEg3PT47///EALUQAAIBAwMCBAMFB ………………………………………………………………….. QQEAAABfQECAwAEEQUSITFBBhNRYQcicRQygZk5SVlpeYmZqio6Slpqeoqaqys7S1tre4ubrCw8TFxsfIycrS09TV1tfY2drh4uPk5ebn6Onq8fLz9PX29/j5 +v/EAB8BAAMBAQEBAQEBAQEAAAAAAAABAgMEBQYHCAkKC//EALURAAIBAgQEAwQHBQQEAAECdwABAgMRBAUhMQYSQVEHYXETIjKBCBR CkaGxwQkjM1LwFWJy0QoWJDThJfEXGBkaJicoKSo1Njc4OTpDREVGR0hJSlNUVVZXWFlaY2RlZmdoaWpzdHV2d3h5eoKDhIWGh4iJipKTlJWWl5iZm qKjpKWmp6ipqrKztLW2t7i5usLDxMXGx8jJytLT1NXW19jZ2uLj5OXm5+jp6vLz9PX29/j5+v/aAAwDAQACEQMRAD8A9mooooAKKKKACsjW/Eum6FGTd S7pcfLEv3j/AIfjWV428XHQrf7HY4e/lHXIxEvqfevH7y8lupXmmuJppWOZJC+AD9aly7GkIX1Z3OpfE3Up3K2EUVumcdN7fy/pWLL4415wPM1GWPJyNpK/ 0Fc5btG/Pktkfx7yTVhYAGLsAxbryf5c5rNvzNlG3Q6yz8ZaxEyudQkcZ+7JtYH867PRfG9nfIsd7/o8p/iI+U/4V5EI/IGV+XUGfnHy9iUsiGSa6q6Jew1XpTDJvA AICDACNUV4K2PS6h574Z3NaBsIQe5jkVO48MSohjC6s29CjPhlU79cQIYWmBpuNfwroZ6zltyz6Y2Fm65V0IfvVicR7zvFFCOhahMuk1cr+Qp936OMEq9s LZGxTjClgwrHGS7YpMSZrEC7bpOmERjo4F/n5YmCHJCH8QzCOc9+80gjVEsHiJVABrC8yykjKL5x1V/PSArE4QtMLbkBPGmQYOw8bx6jCHoO43QjUzb qRfBMHZqWVJyoIIZCp+n13XM4+NO/cDVsZ8bjch0LIOyMrT85n24yfXRlP0s7BFjLm59Jjhf4djuJWikJawWETlypAy86OYRRuwCbIyNauBeTKy+avZvF2oL vpwH4UnudpC06/O0jkj2lQpn9EEUw11RwO6sq9zYTwAUyKerN00cbCfyiZl01CIo0btcTO6hQK3c67PaloJ9lVH8/mH7LuqkMLDH5ugkpzmed/8SorfqVkakn e6b4mRySFCBXaVZoKmDHzcH2oSSMhM9exyh6dzi1bGu6JAEwEGBECAAwFAjpU6CcFGwwAAAAACgkQx0Y2ObLXeV7lbQCg+N+fI3bzqF9+fB50J5s FHVHM7hYAn0+9AfDl5ncnr4D7 ReMDlYoIZwRR =Bgy+ -----END PGP PUBLIC KEY BLOCK----- 25