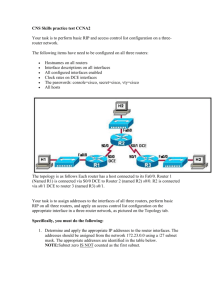
- Home - KSU Faculty Member websites
advertisement

Module 10 Routing Fundamentals and Subnetting Version 3.0 1 Routable Protocols • A protocol is a set of rules that determines how computers communicate with each other across networks • A protocol describes the following: – The format that a message must conform to – The way in which computers must exchange a message within the context of a particular activity Version 3.0 2 Routed Protocols • A routed protocol allows the router to forward data between nodes on different networks. – it must have the ability to assign a network number and a host number to each individual device • These protocols also require a network mask (subnet mask) in order to differentiate between the network and host portion of the address. Version 3.0 3 Routable Protocols Version 3.0 4 Encapsulation Process Data Segments Packets Frames Bits Version 3.0 5 Transport Layer Version 3.0 6 Internet Protocol (IP) • The Internet Protocol (IP) is the most widely used network-addressing scheme • IP is a connectionless, unreliable, best-effort delivery protocol • IP does not verify that the data reaches its destination; this function is handled by the upper layer protocols Version 3.0 7 IP • Data is encapsulated into packets, also known as datagrams at the network layer of the OSI model. Version 3.0 8 Connection-Oriented vs. Connectionless Networks • Connectionless Networks – Often referred to as packet-switched processes – IP Protocol – Internet • Connection-Oriented Networks – Often referred to as circuit-switched processes – A connection with the recipient is first established, and then data transfer begins – TCP adds Layer 4, connection-oriented reliability services to IP Version 3.0 9 Network Layer • Routing is an OSI Layer 3 function • Routing is the process of finding the most efficient path from one device to another • The primary device that performs the routing process is the router Version 3.0 10 Routers • A router is a network layer device that uses one or more routing metrics to determine the optimal path along which network traffic should be forwarded • Routers make logical decisions regarding the best path for the delivery of data Version 3.0 Routing metrics are values used in determining the advantage of one route over another 11 Routers • The encapsulation and de-encapsulation process occurs each time a packet transfers through a router • This process breaks up the data stream into segments, adds the appropriate headers and trailers then transmits the data. The deencapsulation process is the opposite process, removing the headers and trailers, then recombining the data into a seamless stream Version 3.0 12 Routing versus Switching • Switching occurs at Layer 2 of the OSI model • Routing occurs at Layer 3 • The Layer 2 switch can only recognize its own local MAC addresses and cannot handle Layer 3 IP addresses • A Layer 2 switch interconnects segments belonging to same logical network or subnetwork Version 3.0 13 Routing versus Switching Version 3.0 14 Routing versus Switching • Each computer and router interface maintains an ARP table for Layer 2 communication. The ARP table is only effective for the broadcast domain (or LAN) that it is connected to. • The router also maintains a routing table that allows it to route data outside of the broadcast domain • Each ARP table contains an IP-MAC address pair Version 3.0 15 Routing versus Switching • The Layer 2 switch can only recognize its own local MAC addresses and cannot handle Layer 3 IP addresses • When a host has data for a non-local IP address, it sends the frame to the closest router also known as its default gateway • The host uses the MAC address of the router as the destination MAC address Version 3.0 16 Routing versus Switching • Another difference between switched and routed networks is switched networks do not block broadcasts • Routers block LAN broadcasts • Because routers block broadcasts, routers also provide a higher level of security and bandwidth control than switches Version 3.0 17 Subnetting • Subnetting provides manageability, enables the network administrator to provide broadcast containment, and low-level security on the LAN. • Subnet addresses include the Class A, Class B, and Class C network portion, plus a subnet field and a host field. The subnet field and the host field are created from the original host portion of the major IP address. • A LAN is seen as a single network with no knowledge of the internal network structure. This view of the network keeps the routing tables small and efficient. Version 3.0 18 Subnet Mask • The subnet mask gives the router the information required to determine in which network and subnet a particular host resides • The subnet octet or octets are determined by adding the position value of the bits that were borrowed. If three bits were borrowed, the mask for a Class C address would be 255.255.255.224. • This mask may also be represented, in the slash format, as /27. The number following the slash is the total number of bits that were used for the network and subnetwork portion. Version 3.0 19 Subnetting Formula • Number of usable subnets equals two to the power of the assigned subnet bits or borrowed bits, minus two (reserved addresses for subnetwork id and subnetwork broadcast) 2 power of borrowed bits –2 = usable subnets 23 = 8 - 2 = 6 usable subnets • Number of usable hosts equals two to the power of the bits remaining, minus two (reserved addresses for subnet id and subnet broadcast) 2 power of remaining host bits –2 = usable hosts 25 = 32 – 2 = 30 usable hosts per subnet Version 3.0 20 ANDing Process • Routers use subnet masks to determine the home subnetwork for individual nodes. This process is referred to as logical ANDing. • ANDing is a binary process by which the router calculates the subnetwork ID for an incoming packet. Version 3.0 21