elc200day5
advertisement

ELC 200 Day 5
ELECTRONIC COMMERCE
From Vision to Fulfillment
Third Edition
Elias M. Awad
© 2007 Prentice-Hall, Inc
1-1
Agenda
• Questions??
• Assignment 1 DUE
– 3 MIA
• Assignment 2 is posted
– Due February 17th
• Quiz 1 on Friday the 13th
– Chap 1 & 2 from text
– 50 min time limit,
– 20 M/C @ 4 points each
– 4 short essays @ 5 points each
– 1 extra credit @ five points on History of Web browsers
• Discussion on Internet Architecture
© 2007 Prentice-Hall, Inc
1-2
Internet Architecture
ELECTRONIC COMMERCE
From Vision to Fulfillment
Third Edition
Elias M. Awad
© 2007 Prentice-Hall, Inc
1-3
The focus of this chapter is on
several learning objectives
• Types of networks required to conduct ecommerce
• The technical backbone behind accessing
information on Web sites
• How information is transferred between a
customer’s browser and a Web site on the Internet
• How a message is handled in transit on the
Internet
• Hardware and software requirements to support a
Web site for e-commerce
• Factors to consider in designing and managing
networks
© 2007 Prentice-Hall, Inc
1-4
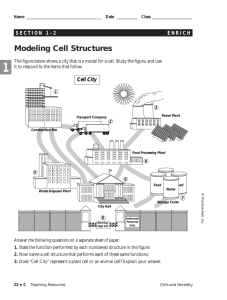
Building Blocks of Electronic
Commerce
© 2007 Prentice-Hall, Inc
1-5
Internet Basics
• The Internet is a network of networks
– Network is any-to-any communications
• Each station on the network has a unique address (much
like a phone number) called an IP address
• Routers and switches forward traffic between network
segments
• Protocols are rules that govern the way a network operates:
– How data travel in packets
– How electrical signals represent data on a network cable
© 2007 Prentice-Hall, Inc
1-6
What Is a (computer) Network?
• A connection between at least two computers for
the purpose of sharing resources
• All networks are based on the concept of sharing
– Why connect if you don’t share?
© 2007 Prentice-Hall, Inc
1-7
Types of Networks
• Peer-to-Peer Networks are the linking of several
PCs so that each acts as a peer, sharing and
exchanging information without the need for a
centralized server
• Client / Server Networks are a cluster of
computers (called clients) connected to one or
more servers to form a network
© 2007 Prentice-Hall, Inc
1-8
Peer-to-Peer Networks
• Computers are linked together as equals
• No centralized server or control
• Any computer can share its resources with any
other computer on the same network in any way
and whenever it chooses
• Users are network administrators in that they
control access to the resources residing on their
own computer
• Can result in institutionalized chaos, and security
can be a problem
© 2007 Prentice-Hall, Inc
1-9
Peer-to-Peer Networks (cont'd)
• Setup usually connects fewer than 10 computer
• As the number of users increases, the peer-topeer environment becomes impractical
• Most common
– AppleTalk
– NetBios
© 2007 Prentice-Hall, Inc
1-10
Basic Peer-to-Peer Network
© 2007 Prentice-Hall, Inc
1-11
Pros and Cons of Peer-to-Peer
Network
© 2007 Prentice-Hall, Inc
1-12
Client/Server Networks
• A server is simply a special-purpose
computer designed to address a
client’s requests
• A client is any computer or workstation
connected to the server within a
network
• All programs or applications reside on
the server
• The client downloads software and/or
data from the server
• When the client finishes data may be
uploaded back to the server
© 2007 Prentice-Hall, Inc
1-13
Client/Server Network
© 2007 Prentice-Hall, Inc
1-14
Pros and Cons of Client/Server
Network
© 2007 Prentice-Hall, Inc
1-15
IP Addresses
• A Web site’s address includes the name of the
host computer’s link the Web site resides on
• Each host is identified by a unique host number
(called an IP address) and by a name that is easier
to remember than the number
© 2007 Prentice-Hall, Inc
1-16
IP Address Arithmetic
•
An IP address consists of 32 binary digits or bits (zeros and ones)
•
Divide the 32 bits into 4 groups of 8 bits called a byte, or octet
•
Each octet represents a decimal value from 0 through 255
•
Write the four decimal values separated by dots
•
191.170.64.12 - computer friendly, but not human friendly
•
Every host on the Internet has a host number
•
My address (use scientific calculator in Windows XP)
– 130.111.66.240
– 10000010.01101111.01000010.11110000
– 10000010011011110100001011110000
© 2007 Prentice-Hall, Inc
1-17
Networks and Numbers
• Host number divided into two parts
– Network part - 2 octets
– Local part - 2 octets
{
{
University of Virginia host number
191 . 170 . 64 . 12
network
part
local
part
– All UVa addresses begin with 191 . 170
• UMS is 130.111
– 64 identifies a subnet at UVa
– 12 is the machine on the subnet
© 2007 Prentice-Hall, Inc
1-18
Networks and Sizes
• Networks are classified in three sizes:
–
–
–
–
Class A (large)
Class B (medium)
Class C (small)
Class D is a multicast network
• The initial bits of the IP address tells the size of
the network host
© 2007 Prentice-Hall, Inc
1-19
IP Address Classes
# of networks
# Hosts / network
total
Class A
126
16,777,214
2,113,928,964
Class B
16,382
65,534
1,073,577,988
Class C
2,097,150
254
532,676,100
3,720,183,052
© 2007 Prentice-Hall, Inc
1-20
Class A Networks
• A host is in a Class A network if the first bit of the first
octet is 0
0 xxxxxxx
• Class A network host number format
NNN.LLL.LLL.LLL
NNN = network part
LLL = local part
• There are 7 bits left in the first octet for network host
number - 126 Class A networks (27)
– This part in the text is wrong also!
• The remaining three octets are for the local host id on the
network - 16 million local hosts (224 )
© 2007 Prentice-Hall, Inc
1-21
Class B Networks
• A host is in a Class B network if the first two bits of the
first octet are 10
10 xxxxxx
• Class B network host number format
NNN.NNN.LLL.LLL
NNN = network part
LLL = local part
• There are 14 bits left in the first two octets for network host
number - 16000 Class B networks (214)
• The remaining two octets are for the local host id on the
network - 65000 local hosts (216 )
© 2007 Prentice-Hall, Inc
1-22
Class C Networks
• A host is in a Class C network if the first three
bits of the first octet are 110
110 xxxxx
• Class C network host number format
NNN.NNN.NNN.LLL NNN = network part
LLL = local part
• There are 21 bits left in the first three octets for
network host number - 2 million Class C networks
(221)
• The remaining one octet is for the local host id on
the network - 254 local hosts (28 )
– [Note: 28 = 256, however, two of the local host
ids are reserved]
© 2007 Prentice-Hall, Inc
1-23
Class D Networks
• A host is in a Class D network if the first four
bits of the first octet are 1110
1110 xxxx
• Used for multicasting
• The packet goes to all hosts on that subnet.
© 2007 Prentice-Hall, Inc
1-24
Network Class Example
• UVa network host number is 191.170.0.0
• Binary representation for the 191 is
•
10111111
•
First two bits are 10 Class B network
• UVa is a class B network
– 65,000 possible hosts in UVa network (216)
© 2007 Prentice-Hall, Inc
1-25
Network Class Example
• UMS network host number is 130.111.0.0
• Binary representation for the 130 is
•
10000010
•
First two bits are 10 Class B network
• UMS is a class B network
– 65,000 possible hosts in UMS network (216)
© 2007 Prentice-Hall, Inc
1-26
Host Naming
• A host name is an Internet address consisting of
text labels separated by dots
• Host name is people friendly
• Host names used instead of IP addresses or host
numbers
– Wouldn’t it be great if the phone system
worked this way?
• Why doesn;t it?
© 2007 Prentice-Hall, Inc
1-27
Zones and Domain Names
• An Internet name is decoded from right to left
• Zone name is the last (rightmost) part of a domain name
preceded by a dot, specifying the type of domain name
• Zones are classified in two ways:
– Three-letter zone names
– Two-letter zone names
• Domain name is a Web address that contains two or more
word groups separated by periods
• www.virginia.com => domain name
.com => zone
© 2007 Prentice-Hall, Inc
1-28
Sample Zone Names
© 2007 Prentice-Hall, Inc
1-29
Common Geographical Two-Letter Zone
http://www.iana.org/root-whois/index.html
Names
za = South Africa
kn = St Kitts
jm = Jamaica
pl = Poland
br = Brazil
cs = Serbia & Montenegro
hr = Croatia
© 2007 Prentice-Hall, Inc
1-30
How to Pick a Domain Name
• Pointer for picking domain names
– If you sell bricks, pick a domain name containing a word
like brick
– Consider name length and ease of remembering the
name
– Hyphens to force search engines to see keywords in
your domain name
– Make sure the domain name is easy for Web users to
remember and find
– The domain name should suggest the nature of your
product or service
– The domain name should serve as a trademark
– The domain name should be free of legal conflicts
© 2007 Prentice-Hall, Inc
1-31
Some memorable Internet names
• Good names
– Amazon.com
– Ebay.com
– Yahoo.com
– Google.com
– Alibaba.com
– Hotmail.com
– qwerty.com
• Bad names
– Yadayada.com
– Doggles.com
– ePet.com
– Teacherstalk.com
– “anything”online.com
– llanfairpwllgwyngyllgogerychwyr
ndrobwyllllantysiliogogogoch.com
– Close to an existing name
• Gooogle.com
• Goggle.com
© 2007 Prentice-Hall, Inc
1-32
How to Register a Domain
Name
• Check if the domain name you propose has been
taken
• www.FasterWhois.com
• http://www.networksolutions.com/whois/index.jsp
• One of the most popular and reliable registration
sites is www.internic.net/alpha.html
– I use www.godaddy.com and
www.networksolutions.com
© 2007 Prentice-Hall, Inc
1-33
Packets and Protocols
• All data sent through the Internet are sent as packets
• A packet is a sequence of bits that carries identifying
information for transmitting the data as well as the data
itself
• A single packet contains a header to keep track of the actual
data it carries
• Packets range in size from 100 bytes to 2,000 bytes
• Messages that are larger than the standard packet size are
split into a series of packets for transmission
© 2007 Prentice-Hall, Inc
1-34
Packets and Internet Protocols
• Protocols are pieces of software that run on every node or
computer and allow every pair of computers to
communicate directly without having to know much about
each other, except for the IP address
• Protocols govern communication between peer processes
on different systems
• Differing client browser and Web server
• Protocols used in connection with the Internet include many
functions and the TCP/IP protocol suite
© 2007 Prentice-Hall, Inc
1-35
Packet Switching
• The way data are exchanged between two
communicating computers
• Divides data into packets (datagrams), which also
contain control information like Internet
addresses of the source and destination
computers
• Packet switching makes it possible to enable
multiple communicating computers to share the
network efficiently, quickly, and accurately
© 2007 Prentice-Hall, Inc
1-36
OSI Reference Model
• Application Layer
• Presentation Layer
• Session Layer
• Transport Layer
• Network (Internet) Layer
• Data Link Layer
• Physical Layer
© 2007 Prentice-Hall, Inc
1-37
OSI Reference Model - (cont’d)
• A seven-layer model that defines the basic
network functions
• Each layer handles a different portion of the
communications process with specific network
functions
© 2007 Prentice-Hall, Inc
1-38
ISO 7-layer Model
Node A
Node B
Layer 7
Application
Messages
Layer 7
Application
User applications
FTP, email, browser, etc.
Layer 6
Presentation
Messages
Layer 6
Presentation
Data translation
MIME, encryption, etc.
Layer 5
Session
Messages
Layer 5
Session
Session management
Dialog management, security
Layer 4
Transport
Messages
Layer 4
Transport
End-to-End control
Error correction (TCP)
Layer 3
Network
Packets
Layer 3
Network
Manages data transfer
Message routing (IP)
Layer 2
Data Link
Frames
Layer 2
Data Link
Link management
MAC, physical addressing
Level 1
Physical
Physical hardware
Media, signal transmission
Level 1
Physical
Bits on physical
medium
© 2007 Prentice-Hall, Inc
1-39
Application Layer
• Communicates with the actual application in use
• Standards at the application layer specify how two
application programs should communicate
– The main standard hypertext transfer protocol (HTTP)
– Hypertext markup language (HTML) is a standard set of
codes representing text or graphics
• The application layer is where the user begins to do
something useful
• Simple network management protocol (SNMP) is a protocol
that controls network devices at the application layer
• Domain naming service (DNS) is software that converts IP
addresses into easy-to-remember names for the user
© 2007 Prentice-Hall, Inc
1-40
Presentation and Session Layers
• Presentation Layer
– The network’s translator
– Converts data into a format for network
transmission and converts incoming data into a
format the receiving application can
understand
• Session Layer
– Facilitates a “session” between two parties to
communicate across a network
– Keeps track of the status of the exchange and
ensures that only designated parties are
allowed to participate
– Enforces security protocols
© 2007 Prentice-Hall, Inc
1-41
Transport Layer
• Manages the transmission or flow of data between two
computers or across a network
• Manages the data flow is by segmenting data into multiple
packets
• Acknowledges successful transmissions and requests
retransmission if packets are damaged or arrive in error
• Breaks the connection when transmission ends
• Standard for the transport layer is the transmission control
protocol (TCP)
© 2007 Prentice-Hall, Inc
1-42
Network (Internet) Layer
• Routes messages across multiple nodes
• Handles network congestion
• Standard for routing packets is the Internet
Protocol (IP)
• Resends lost packets automatically
• Defines how data are subdivided into packets
© 2007 Prentice-Hall, Inc
1-43
Data Link Layer
• The “basement” of the Internet
• Messages at the data link layer are called data
frames the basic unit of Internet traffic
• Another way of sending packets is over an
Ethernet
– Framing and error detection are handled
automatically by Ethernet hardware
– Ethernet broadcasts a message to all the
computers linked to it, but only the computer
with the right address broadcasts an answer
© 2007 Prentice-Hall, Inc
1-44
Physical Layer
• Lowest layer in the journey of a message from
source to destination
• Converts bits into signals for outgoing messages
and signals into bits for incoming messages
© 2007 Prentice-Hall, Inc
1-45
Other Networks
• TCP/IP protocols are not restricted to the Internet
• Companies have found TCP/IP useful for:
– Creating intranets, or internal company
networks
– Forming extranets to connect with vendors and
suppliers and establish shared databases
© 2007 Prentice-Hall, Inc
1-46
Network Cable Types
• Network connectivity means:
– Speed of data transfer
– Network size
– Ease of installation
• There are three types of cable
– Twisted pair
– Optical fiber
– Coaxial
• Wireless technology
© 2007 Prentice-Hall, Inc
1-47
Twisted-Pair Cable
•
Two pairs of insulated wires twisted around each other, even
enclosed in a plastic sheath
•
The most commonly used type of networking cable in the
United States
•
Originally used to connect a telephone to a wall jack
•
Least expensive cable medium
•
Shielded and unshielded twisted pair
– Unshielded twisted-pair (UTP) cabling does not have shielding
against electrical interference
– Shielded twisted-pair (STP) cabling has an electrically
grounded woven copper mesh or aluminum foil wrapped
around each twisted pair and another metal mesh wrapped
around a multiple bundle of wires to reduce electromagnetic
interference
© 2007 Prentice-Hall, Inc
1-48
UTP Cable
© 2007 Prentice-Hall, Inc
1-49
Fiber-Optic Cable
• Uses light rather than voltage to carry data
• Fiber enables digitized light signals to be transmitted more
than 60 miles without being amplified
• Outperforms copper and coaxial media with fewer
transmission losses, lower interference, and higher
bandwidth
• Drawbacks are:
– It is the most expensive of all network media types
– Each segment that transmits incoming and receiving
data must contain an incoming cable and an outgoing
cable
– It requires highly skilled installers and special
connectors
© 2007 Prentice-Hall, Inc
1-50
Optical Fiber
© 2007 Prentice-Hall, Inc
1-51
Optical Fiber
Source: Adapted from Panko, Raymond, Business Data Communications and Networking (3rd ed.), Upper
Saddle River, NJ: Prentice-Hall, 2001, p. 278.
© 2007 Prentice-Hall, Inc
1-52
Fiber Optic Selection Criteria
• Attenuation or delay, the reduction of signal
strength due to gravitational pull
• Dispersion, the time distortion of an optical
signal that results from discrete wave-length
components traveling at different rates
• Mode-field diameter (MFD), the functional
parameter that determines optical performance
when a fiber is coupled to a light source, spliced,
or bent
© 2007 Prentice-Hall, Inc
1-53
Coaxial Cable
• An early version of the way computers were connected to a
network
• The cable in cable TV
• Has a copper core that is much thicker than twisted-pair
cable, so it allows higher data transmission rates over long
distances
• Transmits up to 10 Mbps for a distance of up to 500 meters
• Main drawback is its inflexibility and low security
© 2007 Prentice-Hall, Inc
1-54
Coaxial Cable
© 2007 Prentice-Hall, Inc
1-55
Wireless Technology
• Data communication without physical attachments
• Three types of wireless data transmission technology:
– Microwave transmission is used to connect LANs in
separate buildings that must be within the line of sight of
each other
– Radio technology by radio frequency with no distance
limitations
– Infrared transmission operates at frequencies
approaching the speed of light
© 2007 Prentice-Hall, Inc
1-56
Network Components
• Network Interface Card
– A card installed in a slot in the PC to allow
communication between the PC and other PCs in the
LAN and beyond
– To communicate over a telephone line the PC needs a
modem, a device that converts digital signals into analog
format for outgoing transmission and converts incoming
messages from analog to digital format for computer
processing
• Hubs and Switches
– Hub is a piece of hardware that operates at the OSI
physical layer and acts as a connecting point
– Switch is a piece of hardware that offers a direct
connection to a particular PC
© 2007 Prentice-Hall, Inc
1-57
Network Components (cont'd)
•
Routers
– A piece of hardware that operates at the
OSI Internet layer, linking the network into
little chunks called network segments
– Usually “intelligent” and evaluate the
network traffic and can stop local traffic
from entering and causing congestion
– Make intelligent path choices
– Filter out packets that need not be
received
– Expensive and difficult to operate
•
Gateways
– A special-purpose computer that allows
communication between dissimilar
systems on the network
© 2007 Prentice-Hall, Inc
1-58
Network Design Considerations
STEP 1: Factors to Keep in Mind
• Location - Where will the network be installed?
• Capacity - What is the optimum traffic capacity
of the network?
• Distance Limitations - What is the distance of
the farthest PC to the server?
• Cost - What is the estimated cost of the proposed
network installation?
• Potential Growth - How easily and how well can
the network be scaled to meet growing demands?
• Security - How secure is the proposed network?
© 2007 Prentice-Hall, Inc
1-59
Network Design Considerations
STEP 2: Hardware and Software Considerations
• Hardware Requirements
• Software Requirements
• Disaster Recovery and Fault-Tolerance
Requirements
© 2007 Prentice-Hall, Inc
1-60
Network Design Considerations
SUCCESSFUL INSTALLATION
• Conduct a survey of current technology and
constraints
• Document network requirements
• Decide on the network operating systems
• Decide on the file server hardware platform
• Determine the physical environment and client
support
© 2007 Prentice-Hall, Inc
1-61
Managerial Factors
• Network management tasks:
– Maintain an acceptable level of system
availability
– Assure good response time
– Run the network at optimal capacity
– Route voice and data traffic around the clock
– Enable managers, employees, and customers
to communicate effectively regardless of time,
distance, or location
© 2007 Prentice-Hall, Inc
1-62
Managerial Factors – (cont’d)
• Key components of a typical network management system:
– The manager - the network administrator manages the
network via software loaded on a special workstation
– Managed nodes - the manager monitors nodes or
pieces of software call agents that communicate with the
manager on behalf of the node
– Objects - Ports on the managed node that the agent
represents to the manager
– Management Information Base (MIB) - software that
defines the objects that can exist, based on the initial
design of the database
– Requests and Responses - uses SNMP to allow the
manager and agents to work through pre-established
cycles
© 2007 Prentice-Hall, Inc
1-63
E-Commerce Issues
•
•
•
•
•
•
•
Financial Exposure
IP Exposure
Legal Security
Packet Sniffing
Firewalls
IPSec
Intrusion Detection Systems (IDS)
© 2007 Prentice-Hall, Inc
1-64
Management Implications
•
•
High demand for Technical talent
– Project Management
– Business Knowledge
– Communication Skills
– High Salaries
Retaining Talent
– Constructive & Timely Feedback
– Recognition & Appreciation
– Championing Staff Causes
– Support Employee Career goals
– Match Industry Standards for Salary
© 2007 Prentice-Hall, Inc
1-65
Chapter Summary
• A network is a connection between at least two
computers for the purpose of sharing resources.
• Internet host numbers are divided into two parts: the
network part (first two numbers) and the local part
(second two numbers).
• Messages, invoicing, and other information
transmission on the Internet are made possible by
protocols, standards, and other software that
transmits information via packets through a cable to
its destination.
• The OSI Reference Model is a seven-layer model that
defines the basic network functions.
• The standard for the transport layer is TCP, which is
the most popular standard used on the Internet.
© 2007 Prentice-Hall, Inc
1-66
Chapter Summary (cont'd)
• To communicate over a line, you need a modem, which
converts incoming analog signals into digital signals.
• Several factors need to be considered in designing a
network: location, capacity, distance limitations, cost,
potential growth, and security.
• Factors to be considered in selecting network
architecture include: hardware requirements, software
requirements, disaster recovery and fault-tolerance
requirements, and corporate culture and organizational
factors.
• The main implication of networking for management is
that firms need to have a work environment that
technical people find conducive for long-term
employment and one that promotes a career path for
© 2007 Prentice-Hall, Inc
1-67
qualified employees.