Security audits
advertisement

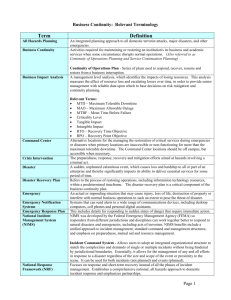
Security audits Today’s talk Security audits Penetration testing as a component of Security auditing Different types of information systems security accreditation organizations Certifications available Introduction Definition Purpose of security audits Domain specific audit Application security Network security Business continuity planning (BCP)/Disaster recovery (DR) Physical (Environmental) security/personnel Employee vetting procedures Security Policy The ‘Bible’ of the organization Contents Bad policies are worse than none at all Policy should be changes for any additions to the infrastructure Generally the Information Security policy is expected to be reviewed annually Application Security This domain only comes into picture when the third party is providing an application or using an web application developed by another company. Detailed enumeration of the development process: Ex: Whether SDLC was followed while development Access controls in place. Network Security Network diagram – firewall infrastructure used , most preferably multi tier firewall. Segregation between the application server and database server. Either logically or physically. Usage of removable media, access to file upload sites and personal email Ability to disable antivirus Server hardening and change management procedures. Penetration Testing Is a focused effort on penetrating the system Penetration testing vs Vulnerability scanning Expected to be done annually Business continuity/DR Business continuity – Pre planned procedure to ensure continuation of operations in the case of a disaster. BCP simulation test. (Time to recover) Disaster recovery - reactive approach in case of a disaster Availability of a cold site ,hot site and a warm site Physical Security/Personnel Very critical since humans are involved Controls can be placed for systems but very difficult to implement for humans Social engineering Importance of educating even the facilities staff Employee Vetting Includes Background verification ,criminal check Credit reference Adherence and education of the information security policy and other policies such as clear desk policy Guidelines PCI-DSS : Payment card Industry Data security standards – organizations that handle cardholder information. SSAE 16 : Reporting on controls at a service organization ISO 27001 Certification for data centers : Security management standard that specifies security management best practices and comprehensive security controls. Certifications ISO/IEC 27001 lead auditor certification Certifiied Information systems auditor certification (CISA) by ISACA.