Workware™ Service Definition
Version: 1.0
ian.carter
© Copyright AOM International 2016
Confidentiality: Restricted
Page 1 of 20
CONTENTS
Service Overview - Functional ........................................................................ 5
Introduction............................................................................................................................ 5
Workware ............................................................................................................................... 5
About Workware............................................................................................................................................ 5
Summary of Functionality .............................................................................................................................. 6
Service Overview – Non functional ................................................................ 8
Application Security ............................................................................................................... 8
Authentication ............................................................................................................................................... 8
Role based security ........................................................................................................................................ 9
SQL injection attack ....................................................................................................................................... 9
Session management ..................................................................................................................................... 9
Development and technology ................................................................................................ 9
Data Integrity.......................................................................................................................... 9
Secure communications ................................................................................................................................. 9
Separation of client data .............................................................................................................................. 10
Security Overview ................................................................................................................ 10
Data Centres ................................................................................................................................................ 10
Firewalls ....................................................................................................................................................... 10
Physical security ........................................................................................................................................... 10
Servers ......................................................................................................................................................... 10
Monitoring and network protection ............................................................................................................ 11
Penetration testing ...................................................................................................................................... 11
Software Releases/Roadmap ............................................................................................... 11
Technical Requirements ............................................................................... 11
Information Assurance................................................................................. 12
Back-up/Restore and Disaster Recovery ...................................................... 12
Backups ................................................................................................................................ 12
Disaster Recovery ................................................................................................................. 13
DR Technology overview .............................................................................................................................. 13
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 2 of 20
On-boarding and Off-boarding processes ..................................................... 13
On-boarding ......................................................................................................................... 13
Off-boarding ......................................................................................................................... 13
Data restoration / service migration ............................................................ 13
Data Restoration .......................................................................................................................................... 13
Service Migration ......................................................................................................................................... 14
Service management ................................................................................... 14
Account Management .......................................................................................................... 14
Service Monitoring ............................................................................................................... 14
Service Desk ......................................................................................................................... 14
Hours of support .......................................................................................................................................... 14
Service Levels ....................................................................................................................... 14
Support ........................................................................................................................................................ 14
Availability .................................................................................................................................................... 15
Service constraints ....................................................................................... 15
Maintenance windows ................................................................................................................................. 15
Service exclusions ........................................................................................................................................ 15
Service Level Penalty Regime ....................................................................... 15
Consumer Responsibilities ........................................................................... 16
Pricing.......................................................................................................... 17
VAT ....................................................................................................................................... 17
Indexation ................................................................................................... 17
Trial Service ................................................................................................. 18
Ordering and Invoicing Process .................................................................... 18
Termination Terms ...................................................................................... 18
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 3 of 20
VERSION HISTORY
Version
Created/Updated by
Reviewed by
Comments
1.0
RS, IC, ML, ME
ME
Initial Version
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 4 of 20
Service Overview - Functional
Introduction
AOM is an innovative approach to operations management, focusing front-line managers and their staff on the
achievement of quality and service levels at the optimum cost. AOM transforms the typical top-down, datadriven, command-and-control management style into a collaborative, method-driven, bottom-up culture,
where good decisions are made daily at the heart of the operation.
Primarily, AOM drives fundamental and lasting change in management behaviours. It achieves this by
concentrating on three aspects: Method, Skills and Tools. These are introduced to your organisation through a
structured 12–16 week implementation programme.
Workware supports the introduction of this management method by providing full-cycle support for capacity
planning and operational performance reporting.
Through the collection of workload and performance data, and through the use of Workware’s planning and
reporting capabilities, Workware helps users to:
Forecast future work loads
Plan how to meet the demand of future workloads.
Identify opportunities for when additional activities can take place.
Monitor and improve the performance of individuals, teams and departments.
Continuously improve through review actual performance against plan performance.
Review performance and workload trends to help identify future resourcing requirements and
improvement initiatives.
Workware is a web-based application that is provided by AOMi on a software-as-a-service basis. Users need
only have internet access via a supported web-browser.
Workware
About Workware
Workware is a SaaS-delivered application that supports the introduction of the AOM management method by
providing full-cycle support for capacity planning and operational performance reporting. Workware is used by
major organisations from Financial Services to the Public sector.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 5 of 20
Summary of Functionality
System Area
Administration
Worklog (production
data capture)
Description of Functionality
Workware provides Administration functions which allow users to configure
and maintain the application via the user-interface. This functionality
includes:
Creation of tasks, teams, departments and other objects
Maintenance of relationships between objects (organisation
hierarchy, team-task associations, etc)
User account and user-role management
System-wide configuration options
The Worklog section of the application provides the capability to capture
production data, including:
Volumes of Work Received - per task
Volumes of work outstanding (Work In Progress [WIP]) – per task
Staff-member work records:
o Volumes of work completed – per task
o Time spent on non core activities – per task
o Downtime (e.g. sick leave) – per category
o Working time data (working hours, annual leave,
loaned/borrow time, flexitime, overtime)
o Quality sample sizes and checking results – per task
o Service standard adherence results – per task
A number of methods of collecting the above data are provided by
Workware:
Manual keying, either on behalf of a whole team or individuals
entering their own data
Spreadsheet upload – either individually or for the full team
Import from Workware Connect – data can be loaded directly to the
Worklog from any source system via the Workware Connect
integration tool
Import from Workware RTM – data can be loaded to the Workware
Worklog directly from the Workware RTM module.
The Worklog allows descriptive notes to be attached to any item of data.
These notes can be used to explain features or anomalies of the data. The
notes are visible in the Worklog section of the application and are also shown
in all reports where the data item is shown.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 6 of 20
System Area
Planning
Control
Description of Functionality
The Workware planning tool, provides the ability for users to create capacity
plans for any team or organisational entity (department, business unit,
division, etc). The planning tool allows users to:
Forecast/plan all variables necessary for capacity planning:
o Volumes of core work (received, planned for processing,
outstanding)
o Time to be spent on non core work
o Resource availability and effectiveness
Analyse historic data held in Workware to assist with forecasting
Balance the capacity plan – i.e. ensure that the planned work
matches the available resource capacity
Plan for a wide range of time horizons as required by the business
Aggregate plans from lower levels of the organisation hierarchy to
create plans for higher levels in the hierarchy
Automatically create plans based on planning assumptions saved in
an existing plan
Provide daily work plans for individual staff members
The Control section of Workware provides a range of reports which allow
managers to analyse planned work output/performance against actual
output/performance. The reports provide a range of different presentations
of this data from visual dashboards to detailed data-sheets.
Features of all of the reports in this section include:
Can be run for any level of the organisation hierarchy (from staff
member through to the highest level of the organisation)
Extensive drill-down functions allowing users to query the data at a
more detailed level (e.g. expand a report category to view the data
by task)
A wide range of user-defined parameters to determine the scope of
the report
Printing and export to Microsoft Excel
The ability to add/review explanatory notes placed against any data
item
All data can be shown in a range of reporting units relevant to the
data type. For example all data relating to Core Work can be seen
as volumes or time (hours/minutes/FTE) based the task’s defined
standard-time
Charting tools allow users to create charts from any data shown in
the reports.
The reports include data of the following types:
Core Task work-flow data – received, processed, outstanding
Diverted (non core work) time
Resources consumed – contracted hours, annual leave,
loan/borrow, overtime, temporary staff, flexitime, etc
Performance – productivity, utilisation, complex productivity, total
productivity, error rate, service performance
All of the above data is provided as planned and actual figures
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 7 of 20
System Area
Report
Description of Functionality
The Report section of the application provides reports on a variety of
Workware data. Whilst the Control section provides reports which compare
planned data against actual data, the Report section focuses only on actual
data.
Production reports provide flexible (any time period, any organisational level)
access to all production data recorded in the Workware Worklog. The
features of the Control reports (above) also apply to these reports.
Skills reports allow managers to record the skills of their team members
against the tasks recorded in Workware.
Notes reports allow users to query the database of descriptive notes which
can be recorded via the Worklog or in any report.
Miscellaneous Features
Export facilities allow all of the data in a production report to be extracted
into Microsoft XL for further analysis.
Workware features an extensive online help system which includes content
on both the use of Workware and also background on the AOM
methodology.
Service Overview – Non functional
Application Security
Authentication
Workware uses Database authentication, where user details are verified against the user’s credentials stored
in the database. Passwords requirements are:
Length must be between 8 and 15 characters
Must contain at least one of each of; lower case letters, upper case letters, numbers and nonalphanumeric characters
In addition, password functionality also includes:
Password entry is masked at logon
Force password change at logon function when creating or maintaining user account
User password expiry notification
Password history, preventing users from reusing passwords
Configurable password aging.
Unsuccessful logon attempts are also recorded.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 8 of 20
Role based security
The Workware application has a granular role based security system, which allows user account permissions to
be controlled down to the functional activity level. The organisational span (teams and departments) with
which the user can interact is also controlled by the role-based security. Workware security settings are
automatically inherited by RTM and AOM Analytics, Workware provides a predefined set of roles and clients
can configure these and further roles as and when required.
SQL injection attack
All free form text fields within Workware have SQL injection attack detection and rejection functionality. This
functionality was developed by AOMi using recommendations from Microsoft.
Session management
Workware uses IIS to provide session security management, with each having its own individual timeout
limitation.
Workware will timeout unused or abandoned sessions. This timeout period can be configured at the system
level.
Development and technology
AOMi has been developing the Workware software in-house for over 10 years. Initially starting as a complex
spread sheet it soon developed to a ‘Thick Client’ version (2.5) before moving to a web enabled application in
2005 (v5.0) using SQL2000 and .NET 1.1.
In 2006 Workware moved to SQL2005 and .NET 2 (v5.1). In 2010 AOMi released Workware 5.2 which was
accompanied by a move to SQL2008 and IIS 6. Like previous versions, Workware 5.2 exploits the .NET 2
framework.
AOMi’s policy is to keep Workware technologically relevant in the market place and where appropriate use the
latest technology to deliver a positive user experience. As such, Workware 5.3 (released in February 2013)
uses updated versions of the core technology, namely .NET 4, IIS7 and SQL2008, all running on Windows Sever
2008 64bit.
The Service is delivered over the web (or dedicated network if required) and accessed via standard browser
technology using open standards.
Data Integrity
Secure communications
Workware SaaS uses Comodo Elite 2048 bit SSL certificates, with 128/256 bit SSL
certificates; RSA with 2048 bit exchange to provide secure HTTP (HTTPS) communication.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 9 of 20
SaaS applications can only be accessed when using HTTPS.
Separation of client data
Although clients share physical servers, their data is held within separate databases. In addition, each client
has their own installation of the application, with its own client specific URL.
Security Overview
Data Centres
AOMi uses two geographically disperse lights-out Class 3 Data Centres (DC). The Primary DC is dedicated to
Workware Production/Live environments with the Secondary DC hosting User Acceptance Testing (UAT) and
Disaster Recovery.
The two DCs are connected via a dedicated Advanced Encryption Standard (AES) encrypted 100Megabit
Multiprotocol Label Switching (MPLS) link.
The Production DC is PCI DSS (Payment Card Industry Data Security Standard) certified.
Firewalls
Each DC has a dedicated pair of managed Juniper SSG 140 firewalls in a High Availability configuration which
provides external access to the Workware servers and network, as well as internal and inter DC zoning.
Physical security
DCs are physically manned and monitored 24x7 by on-site internal and external CCTV, with remote video
recording. Vehicle access is via intercom and electronic security gates. Access to the DC is via access control
card.
Access to the DCs is by advanced agreement only and is restricted to named authorised personnel only.
The AOMi SaaS environment is physically separated from other DC clients by a floor to ceiling cage, with card
access providing a barrier to unauthorised access. Access to cages, for hands-on support, is restricted to DC
authorised employees or authorised repair agents. Proximity access control is used to restrict movement
within the DC to authorised areas only.
Servers
All servers are supplied by Hewlett-Packard (hp) and are covered by the DC provider, as an hp authorised
repair agent, on a 2 hour call-to-fix contract.
Database servers utilise local mirrored discs for installation of the Operating System and SQL, with fibre
connection to a Storage Area Network (SAN) for database logs, tables, indexes and backups. Web servers also
utilise local mirrored discs.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 10 of 20
All servers have access to multiple Network Interface Cards (NICs) to separate internet network traffic from
internal backup and management traffic.
Servers are covered by Symantec anti-virus, with centralised definitions management and patched to the latest
Microsoft security advisory within 48 hours of successful installation and test into the UAT environment.
Servers are hardened at the point of build in line with Microsoft best practice, with services and ports
reviewed again at the point of server commissioning for production use.
Monitoring and network protection
The SaaS environment is monitored to identify threshold breaches, such as memory, CPU, disc utilisation and
backup progress. Any breaches are reported back to AOMi Support for action.
The DC provider uses a combination of logical and physical network segregation to prevent client services from
impacting one another. The DC provider also utilises MessageLabs services to prevent virus, spam, mobile code
and other forms of malware from entering the network.
In addition, an Active Directory is utilised to ensure all users are authenticated onto the network.
Penetration testing
To ensure the SaaS environment delivers the required level of security, AOMi undertakes regular independent
internal and external penetration testing, with any security gaps dealt with as part of AOMi’s ISO27001/ISMS
Management Committee.
External penetration testing is conducted annually.
Software Releases/Roadmap
AOMi has a policy of continual product enhancement and development. This typically culminates in 2 to 3
major software releases a year. AOMi are happy to share the product roadmap with clients when requested.
All software updates to the service (major functional releases and maintenance releases) are supported by
release notes and user guidance documentation which provide details of new, modified and depreciated
functionality.
Technical Requirements
The service is provided for use in Web browser environment. Supported browsers include:
Microsoft Internet Explorer version 6 or above (Workware v.5.2 and above) supported. Microsoft Internet
Explorer version 8 or above is recommended.
Google Chrome
Mozilla Firefox
Safari
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 11 of 20
Other browsers may be able to access the service.
AOMi applications do not install any software on the desktop environment (other than a temporary cookie for
session management), nor do they use ActiveX components. However, they do require the activation of popups for a client-specific URL.
Workware requires a PDF reader to be installed on the user’s PC to facilitate printing of reports. Additionally,
Workware includes functionality to export and import data in Microsoft Excel format. To utilise this data,
Microsoft Excel needs to be installed.
Information Assurance
The Service is not currently accredited but the security controls for the service target "PGA IL1/2".
Back-up/Restore and Disaster Recovery
Backups
Backups are taken in three forms:
1.
System backups
A daily incremental backup is taken every day and appended to a weekly full backup. Backups are held on
a local disc based backup library which is then replicated to a secondary data centre.
These backups are retained for 10 days.
2.
Database backups
Database extracts are taken daily and stored on the local server. These are then backed up via the system
backup (see above).
3.
Log shipping
SQL database logs are transferred on an hourly basis from the Production database servers to database
servers in the Secondary DC. These logs are then ‘replayed’, recreating the Production database in the
Secondary DC. This reduces the potential data loss timescale from 24 to 1 hour.
More details on Log Shipping can be found at http://msdn.microsoft.com/en-us/library/ms187103.aspx.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 12 of 20
Disaster Recovery
DR Technology overview
AOMi operates Primary and Secondary UK-based data
centres (DCs). The Secondary DC, operates as a DR location.
The two DCs are geographically separated by a distance of
90 miles and are connected via a dedicated 100Mbit
encrypted link to prove a dedicated high speed connection
between them.
The Secondary DC has identical security to that of the
Primary DC. The secondary DC contains standby application
and database servers which will utilised in the event of a DR
invocation. Application code updates are released to both
DCs and the databases are kept synchronised using the backup and log-shipping methods described above.
More details of AOMi’s DR invocation criteria and processes can be provided on request.
On-boarding and Off-boarding processes
On-boarding
Computer based training modules are provided to help users with the use of the Workware system. Additional
support is available from our Service Desk.
Data requiring migration onto the Workware system can be entered manually into the system, or through the
use of Excel templates provided by the system.
Off-boarding
Billing for the service is based upon the number of FTE’s that the client is actively managing using the software.
Therefore clients can simply stop using the service when they choose.
Any data that is held within the service can be provided to the client on request in the form of data extracts.
Removal of client data and information from the service will be performed by AOMi within 7 days of receipt of
a written request or after six months of non-usage.
Data restoration / service migration
Data Restoration
We provide a full data back-up and restoration facility as a standard part of the service, in the event of any
failure of the service during operation, and can offer a range of back-up and restore options.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 13 of 20
Service Migration
To support you migrating on and off the service, we have a standard service On-boarding and Off-boarding
facility, which is described more fully in the section above (on-boarding and off-boarding process)
Service management
Account Management
Each client is assigned a named Account Manager who will schedule service level review meetings on a regular
basis and also be the nominated contact for post-implementation strategic support.
Service Monitoring
Each client implementation of the service is subject to 24x7x365 monitoring to ensure that the service is
operating and available within agreed service levels.
Service Desk
AOMi’s service desk is available to named contacts within the client. Service /requests can be submitted by
either telephone, email or directly via the Service and Relationship Management (SRM) ticketing system.
Hours of support
The service desk operates between 08:30 and 18:00 Monday to Friday excluding all UK public holidays.
AOMi operates an out-of-hours support number for Priority 1 & 2 calls.
Service Levels
Support
Severity
Priority 1
Definition
Support
Availability
M-F
0830Out of
1800
Hours
Initial response/
request for
information
Temporary
workaround
1 Hour
24 Hours
30 Business
Days
Yes
Yes
2 Hours
48 Hours
60 Business
Days
Yes
Yes
Permanent fix
Major Impact
Complete loss of service or
performance over a sustained period
is such that the tool is rendered
unusable.
No workaround available
Priority 2
High Impact or critical
Majority of users are unable to use
some aspects of functionality.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 14 of 20
A workaround may be available
although performance may be
degraded or functionality limited
Priority 3
Medium Impact or non-critical
Any defect where a workaround is
available, but is not Major or High
impact
Priority 4
24 Hours
Reasonable and
agreed between
parties
Reasonable and
agreed
between
parties
Yes
No
48 Hours
Reasonable and
agreed between
parties
Reasonable and
agreed
between
parties
Yes
No
Low Impact or Change Request
Non-functional defects that do not
prevent use of the tool. Also Service
or Change requests.
Availability
The availability target for the service is 99.8%.
Service constraints
Maintenance windows
Whilst every effort is made to ensure the constant availability of the service, certain maintenance activities,
such as software upgrades, may occasionally require a short period of outage.
The service architecture enables this to be managed on a client-specific basis and therefore maintenance
windows will always be scheduled in advance at a mutually agreed time which will typically be out of core
working hours or, in the case of 24 hour operations, at the time of least business impact.
Service exclusions
Performance or accessibility issues generated by the client’s infrastructure.
Web browser compatibility and configuration issues.
Issues caused as a result of client’s policies to web pop-ups, java or use of 3rd party plug-ins
Service Level Penalty Regime
1.
Unless the parties agree to the contrary, AOMi will only face liability for not meeting service levels in
relation to non delivery of Permanent fixes for defects at Priority Levels 1 & 2 (defined in Service Level section
above).
2.
Where AOMi is found to be at fault for loss of service or functionality:
2.1. In relation to a complete loss of service (Priority 1 Defect), Client shall receive a 100% reduction in their
licence fee for the period exceeding the timeframe for service restoration.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 15 of 20
2.2. In relation to a significant loss of service functionality (Priority 2 Defect), Client shall receive a 50%
reduction in their licence fee for the period exceeding the timeframe for service restoration.
3.
For fee rebates amounting to more than 1 working day, the fee reduction will be calculated back to a
daily rate by dividing the monthly licence price per FTE by the number of working days in that particular
month. The discount will then be applied to the number of FTE impacted multiplied by the number of days.
For example, where 100 FTE are subject to complete loss of service for 10 days and the Client is paying £15 per
FTE per month (20 working days), the calculation would be as follows: 100% of £15 divided by 20 days
multiplied by 10 days multiplied by 100FTE, so £750 in total.
4.
For fee payments of less than 1 working day, the fee reduction will be calculated back to an hourly rate
by dividing the monthly fee per FTE by the number of working days in the particular month divided by the
number of hours in the Client’s standard business day. The discount will then be applied to the number of FTE
impacted multiplied by the number of hours affected.
5.
Where a fee reduction is agreed with a Client, this shall only apply:
5.1.
In relation to the number of FTE impacted by the Defect;
5.2.
Where responsibility for fixing the Defect resides with AOMi; and,
5.3. The affected Client has made reasonable efforts to provide all necessary information and assistance as
reasonably required by AOMi and has not unduly caused AOMi delay in implementing a Permanent fix, e.g.
Client has answered queries raised by AOMi in a timely manner, so that solution can be finalised and deployed.
Consumer Responsibilities
Contractual responsibilities of the consumer are defined in the standard Terms and Conditions. Additionally, in
order to help AOMi maintain its commitment to providing outstanding customer service, clients are expected
to:
Nominate named contacts who are responsible for providing 1st level support internally to the client
Log support incidents with AOMi support via these named individuals.
Engage with AOMi to schedule, in a timely manner, upgrades to the service
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 16 of 20
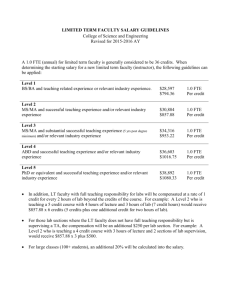
Pricing
The basis for Workware pricing is detailed in the “Workware - Standard Pricing Explanation” document which
forms part of the service catalogue submission. Our standard rate card for software usage involves no
“upfront” licence fees or hardware costs providing the in-scope FTE have access to a computer and web
browser. The cost is therefore entirely linked to use of the software and is invoiced monthly in arrears.
Workware software pricing
No. of FTE
SaaS
pricing*
Min
-
Max
0
-
1,000
£22.50
1,001
-
2,500
£20.10
2,501
-
5,000
£16.20
5,001
-
10,000
£13.20
10,001
-
20,000
£11.50
20,001
+
£10.10
* All prices quoted are per FTE per
month and exclusive of VAT
The unit price is applied to the total FTE managed in Workware (See FTE Calculation section of this document)
across all Contracting Bodies using Workware under the relevant Framework Agreement. All FTE are invoiced
at the same price according to the total FTE managed by Workware. For example:
A single HM Government department commences use of the SaaS software for 500FTE. At the end of
their trial period, they will be charged £11,250 plus VAT each month (500 FTE x £22.50)
Six months later, a second HM Government department commences use of Workware for 1,000 FTE.
At the end of their trial period, they will be charged £20,100 plus VAT each month (1,000 FTE x
£20.10).
Additionally, the first HM Government department will benefit from the growth of overall usage to
1,500 FTE by their monthly charge reducing to £10,050 plus VAT each month (500 FTE x £20.10).
VAT
All pricing included within the tender documents and all other pricing documentation provided by AOMi is
quoted exclusive of VAT which shall be applied at the applicable rate when invoicing.
Indexation
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 17 of 20
Where a call-off agreement between AOMi and a Contracting Body exceeds 12 months, AOMi reserves the
right to index its prices not more than annually (from the date of commencement of the Client’s use of the
service), upon at least 30 days prior notice to Client. Any increase in fees by AOMi shall not be greater than
the rate of UK inflation (RPI) in the period since the charges were previously agreed.
Trial Service
Each new Contracting Body, signing a call-off agreement in respect of the Workware service, and managing
data for more than 100FTE, shall be entitled to 3 calendar months free use of Workware. This Trial period
commences on the date that data is first recorded in Workware. Where a Contracting Body signs multiple calloff agreements, the Trial Period shall only apply to the first call-off agreement signed.”
Ordering and Invoicing Process
Enquiries and orders should be submitted to enquiries@activeops.com or by calling 0118 907 5000 and asking for
the Sales Department.
AOMi will invoice the Client in the amounts and on the basis set out in the proposal with the Client. Where
necessary, VAT will be added at the prevailing rate. Payment terms for all fees, expenses and other sums
payable to AOMi by the Customer are 30 days from the date of invoice.
Termination Terms
Either party shall provide 30 days written notice of any intention to terminate the service. There is no
minimum period unless otherwise agreed for the basis of pricing discounts.
Please refer to our terms and conditions for further information.
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 18 of 20
Version: 1.0
© Copyright AOM International 2016
Confidentiality: Restricted
Page 19 of 20
www.activeops.com
Where this document has been classified as ‘Protected’, ‘Confidential’ or ‘Restricted’, the information contained
within it is confidential and should be treated as such.
This document constitutes the intellectual and proprietary property of AOMi and is protected by intellectual property
laws and international intellectual property treaties.
While the author has made every effort to provide accurate information at the time this document was produced,
neither AOMi nor the author assumes any responsibility for errors or changes that occur after production (unless
explicitly contractually agreed between AOMi and the recipient of this document).
Copyright © 2016 Active Operations Management International LLP (AOMi).
All rights reserved.
Active Operations Management International LLP
Forbury Court
12 Forbury Road
Reading
Berkshire
RG1 1SB
Tel: +44 (0) 118 907 5000
Version: 1.0
© Copyright AOM International 2016
Fax: +44 (0) 118 907 5001
Confidentiality: Restricted
Page 20 of 20