Data_Link_layer_part1.PPT
advertisement

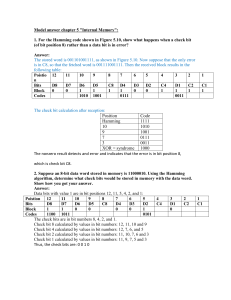
COMPUTER NETWORKS Ms. Mrinmoyee Mukherjee Assistant Professor St. Francis Institute of Technology, Mount Poinsur, S.V.P Road, Borivli (west), Mumbai- 400103 DATA LINK LAYER MAIN TASK OF DLL 1. Transfer data from the network layer of one machine to the network layer of another machine 2. Converts the raw bit streams of physical layer into groups of bits called as ‘FRAMES’ SERVICES PROVIDED BY DLL ??Why do we require any kind of control 1. Frame Synchronization- The beginning and end of data block should be recognizable 2. Flow Control-The sender should not send frames at a rate faster than the receiver can receive and process them 3. Error Control- Any bit error introduced by the transmission system should be corrected 4. Addressing- On a multipoint link, the identity of the sender and receiver must be specified 5. Reliable delivery between adjacent nodes The services can be provided througha. Unacknowledged Connectionless Service b. Acknowledged Connectionless Service c. Acknowledged Connection-oriented Service SERVICES PROVIDED BY DLL Placement of the data link protocol. FRAMING BY DLL Translates the physical layer raw bit stream into discrete units called frames. ?? How can the receiver detect frame boundary…i.e the start and end of a frame There are basically three methods of framing 1. Length Character Count 2. Bit Stuffing 3. Byte Stuffing (Character Stuffing Protocol) LENGTH COUNT BIT STUFFING.. (FIG1) BIT STUFFING (FIG 2) BYTE STUFFING (FIG 2) ERROR DETECTION AND CORRECTION TYPES OF ERROR (A) Single bit error (A) Burst Errors ERROR DETECTION vs CORRECTION Detection1.We are only interested in looking if any error has occurred or not. The simple answer to this question is YES/NO 2.We are not even interested in knowing the number of corrupted bits Correction1. We need to know the exact no of bits that are corrupted. 2. The number of errors and size of message are important factors. 3. We also need to know the location of corrupted bits. ERROR DETECTION vs CORRECTION Errors in the received frames are detected by means of – 1. Parity Check and CRC (Cyclic Redundancy Check). 2. In both scenario, few extra bits are sent along with actual data to confirm that bits received at other end are same as they were sent. If the checks at receiver’s end fails, the bits are corrupted. In digital world, error correction can be done in two ways1. Backward Error Correction: When the receiver detects an error in the data received, it requests back the sender to retransmit the data unit. 2. Forward Error Correction: When the receiver detects some error in the data received, it uses an error-correcting code, which helps it to autorecover and correct some kinds of errors. LINEAR BLOCK CODES 1. In BLOCK CODES , message is divided into blocks of ‘k bits’ called as data words. 2. ‘r ‘ redundant bits are added to it to get n=r+k 3. With k bits it is possible to get 2𝑘 datawords 4. With n bits it is possible to get 2𝑛 codewords 5. Since n>k , the number of possible code-words is always larger than the no of possible data-words. 6. The block coding process is one-to-one- the same data-word is always encoded as the same code-word 7. This means that we have (2𝑛 - 2𝑘 ) code-words that are not used. 8. We call this code-words invalid or illegal. 9. The trick in error detection is the existence of these code-words. 10.If the receiver receives an invalid code word, it indicates that the data was corrupted during transmission Almost all block codes used today belong to a subset called linear block codes. A linear block code is a code in which the exclusive OR (addition modulo-2) of two valid code-words creates another valid codeword. 10. BLOCK CODESHow can errors be detected using block codes1. If the receiver has a list of valid code-words. 2. The original code-word has changed to an invalid one. CENTRAL CONCEPTS-Hamming Distance 1. The HAMMING DISTANCE between the two words (of the same size) is the number of differences between the corresponding bits. 2. The hamming distance between the two words x and y is : d=(x,y) CENTRAL CONCEPTS-Hamming Distance 1. If the hamming distance between the sent and received code-word is not zero, the code-word has been corrupted during transmission. 2. The hamming distance can easily be found if we apply XOR operations on the two words and count the number of 1s in the result CENTRAL CONCEPTS-Minimum Hamming Distance 1. The minimum hamming distance is the smallest hamming distance between all possible pairs in a set of words. It is denoted by 𝑑𝑚𝑖𝑛 CENTRAL CONCEPTS-Relationships scheme is denoted as C (n, k) and must have a 𝑑𝑚𝑖𝑛 2. To guarantee detection up to ‘s ‘ errors, the minimum hamming distance in the block code must be 𝑑𝑚𝑖𝑛 =s+1 3. To guarantee correction up to ‘t ‘ errors, the minimum hamming distance in the block code must be 𝑑𝑚𝑖𝑛 =2t+1 4. In a Linear Block Code, the minimum hamming distance is the no of 1s in the non-zero valid code-word with the smallest number of 1s. In the above example dmin =3 1. A coding DATAWORD CODEWORD 00 00000 01 01011 10 10101 11 11110 Type-1:Simple Parity Check Code 1. A simple parity check code is a single bit error detecting code in which n=k+1 and 𝑑𝑚𝑖𝑛 =2 2. The single bit appended to the data-word to get the code-word is called the ‘Parity Bit’. 3. The value of the parity bit is selected such that the number of 1’s in the code-word is ‘even’ 4. This code can only detect a single bit error. It cannot correct errors Simple Parity Check Code Simple Parity Check Code-Encoding and Decoding 1. Encoding is done by using modulo-2 addition on all the 4 bits of the data word to get the parity bit 2. 𝑟0 = a3+a2+a1+a0 (modulo-2) 3. In decoding the modulo-2 addition is done on the entire code-word (including the parity) 4. The resultant bit is called ‘syndrome’ 5. If s=0 means that there are even number of ones i.e. The code-word is correct 6. S=1, it means that there are odd number of 1s i.e the code-word has an error 7. If two bits are changed error may not be detected 8. Simple parity check code can detect odd number of errors 10. Table 10.3 Simple parity-check code C(5, 4) Example Let us look at some transmission scenarios. Assume the sender sends the dataword 1011. The codeword created from this dataword is 10111, which is sent to the receiver. We examine five cases: 1. No error occurs; the received codeword is 10111. The syndrome is 0. The dataword 1011 is created. 2. One single-bit error changes a1 . The received codeword is 10011. The syndrome is 1. No dataword is created. 3. One single-bit error changes r0 . The received codeword is 10110. The syndrome is 1. No dataword is created. 10. Example (continued) 4. An error changes r0 and a second error changes a3 . The received codeword is 00110. The syndrome is 0. The dataword 0011 is created at the receiver. Note that here the dataword is wrongly created due to the syndrome value. 5. Three bits—a3, a2, and a1—are changed by errors. The received codeword is 01011. The syndrome is 1. The dataword is not created. This shows that the simple parity check, guaranteed to detect one single error, can also find any odd number of errors. 10. Type-2:2-D Parity Check Code CHECKSUM METHOD (SENDER) CYCLIC REDUNDANCY CHECK 1. One of the most powerful and commonly used error detecting codes. 1. Given a m bit block of bit sequence, the sender generates an n bit sequence, known as Frame Check sequence (FCS), so that the resulting frame consisting of m+n bits is exactly divisible by some predetermined number. 1. The receiver divides the incoming frame, by that number and if there is no remainder, assumes that there was no error. (show small example on board) CRC-Performance 1. CRC can detect all single bit errors 2. CRC can detect all double-bit errors (more than 3 ones) 3. CRC can detect any odd number of errors(X+1) 4. CRC can detect all burst errors of less than the degree of polynomial 5. CRC detects most of the larger burst errors with high probability