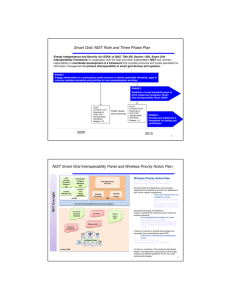
Master_Thesis_Proposal_v3_2
advertisement

Master Thesis Proposal SIMULATION AND ANALYSIS OF WIRELESS MESH NETWORK IN ADVANCED METERING INFRASTRUCTURE PHILIP HUYNH 1. COMMITTEE MEMBERS AND SIGNATURES Approved by Date __________________________________ Advisor: Dr. EDWARD CHOW _____________ __________________________________ Committee member: Dr. JUGAL KALITA _____________ __________________________________ Committee member: Dr. RORY LEWIS _____________ 2. INTRODUCTION MOTIVATIONS GROWING THE NEED FOR SMART GRID A Smart Grid [1] delivers electricity from suppliers to consumers using two-way digital technology to control appliances at consumers' homes to save energy, reduce cost and increase reliability and transparency. Such a modernized electricity network is being promoted by many governments as a way of addressing energy independence, global warming and emergency resilience issues. The potential of Smart Grid and its market benefits are essential for achieving energy efficiency and maintaining the competitive state of utility services. Data collection, monitoring and control, data analysis and information communication infrastructure enables Smart Grid solutions that cost-effectively protect revenues today, while laying the foundations for future services ADVANCED METERING INFRASTRUCTUR (AMI) Government agencies and utilities are turning toward Advanced Metering Infrastructure (AMI) [2] systems as part of larger Smart Grid initiatives to meet these challenges. AMI extends current Advanced Meter Reading (AMR) technology by providing two way meter communications, allowing commands to be sent toward the home for multiple purposes, including “time-of-use” pricing information, demand-response actions, or remote service disconnects. Wireless technologies are critical elements of the Neighborhood Area Network (NAN); aggregating a mesh configuration of up to thousands of meters for back haul to the utility’s IT headquarters [4]. WIRELESS MESH NETWORK AS AN OPTION FOR THE AMI’S COMMUNICATION NETWORK A Wireless Mesh Network (WMN) [3] is a communications network made up of radio nodes organized in a mesh topology. Wireless mesh networks often consist of mesh clients, mesh routers and gateways. The mesh clients are often laptops, cell phones and other wireless devices while the mesh routers forward traffic to and from the gateways which may but need not connect to the Internet. A mesh network is reliable and offers redundancy. When one node can no longer operate, the rest of the nodes can still communicate with each other, directly or through one or more intermediate nodes. Wireless mesh networks can be implemented with various wireless technology including 802.11 [23], 802.16 [24], cellular technologies or combinations of more than one type. When used as the backbone of an AMI solution, wireless mesh networking enables twoway intelligent networked communications with smart meters that enables command and control for value added services like demand response and demand side management, besides meter reading. In [5], Wireless Mesh Network technology expands the technology of electrical grids by adding components such as self-managing and self-healing mesh networking, intelligent meters, and bridging to Home Area Networks (HAN) for connectivity with energy consuming appliances. Smart meters communicate in near real-time with the utility, providing detailed usage data while also receiving and displaying Time-Of-Use (TOU) pricing information, and offering other on-demand abilities such as remote connect/disconnect, unrestricted monitoring and control, etc. These capabilities provide customers with the precise data needed for tailoring consumption and minimizing energy expenses while helping balance overall network demand. When WMNs are used in the AMI, they can provide the following features [5]: Low cost of management and maintenance - WMNs are self-organizing and require no manual address/route/channel assignments. It is simple to manage thousands or millions of devices resulting in the lowest total cost of ownership. Scalability, flexibility and lower costs - WMNs are self-organizing and allow true scalability. Nodes and Gateways are easily added at a very low cost with: o No limitation on number of hops o No network address configuration o No managed hierarchical architecture o No hard limitation on number of Nodes per Gateway Robust security – WMNs have the security standards that allows all communications in AMI are protected by mutual device authentication and derived per-session keys using high bit rate AES encryption. This hardened security approach allows for authentication as well as confidentiality and integrity protection in each communication exchange between every pair of network devices – Smart meters, Relays, or Wireless Gateways. CONTRIBUTIONS The main purpose of the thesis is answering the question: Whether the Wireless Mesh Network is a good option for the Advanced Metering Infrastructure? The thesis will focus on the simulation and analysis of WMN in term of network scalability, network performance and network security [18], which are the important requirements for the design of the AMI’s communication network [5]. The trade-off between the Scalability and Performance, as well as the Security of the proposed network model will be discussed. Therefore, this thesis can serve as a baseline for the network designer or decision makers for the communication network of AMI. APPROACH This thesis presents the potential benefits of WMNs in terms of network scalability, network capacity and network security. Suggest a Hybrid WMN architecture for the AMI’s communication network The communication network of AMI should be a Metropolitan Area Network [13] to coverage a wide area such as a city, or town [2]. We suggest a network model that uses the Hybrid WMN architecture [14]. The hybrid WMN architecture is scalable; and the multiradio multi-channel technique can be used in the WMN to increase the network performance [19]. For the simulation, we use the WiMAX technology for the backhaul network and the Wi-Fi technology for the local mesh network [13]. We also discuss about the security of the given network model. Propose a simulation scenario We propose an AMI application scenario for researching on the given network model. In the simulation scenario, we research the performance of the communication network. We also need to experience the trade-off between the network performance and the scalability by changing the parameters of network model such as number of hops, or client nodes; the distance between the base station and subscriber station or mesh routers. For network traffic generation, we build an AMI application called SmartGridSim that run on top of the Networking (Internet) Layer [25]. SmartGridSim simulates the process of exchanging data between the AMI’s Meter Reading Collector and the Smart Meters through the communication network. Simulate and analyze the results Then, we simulate the proposed network scenario with a set of pre-defined parameters. The simulation results are analyzed to understand the network performance, and the trade-off between the scalability and the performance. 3. BACKGOUND 3.1. SMART GRID (SG) In [1], a smart grid delivers electricity from suppliers to consumers using two-way digital technology to control appliances at consumers' homes to save energy, reduce cost and increase reliability and transparency. Such a modernized electricity network is being promoted by many governments as a way of addressing energy independence, global warming and emergency resilience issues. A smart grid includes an intelligent monitoring system that keeps track of all electricity flowing in the system. It also incorporates the use of superconductive transmission lines for less power loss, as well as the capability of integrating alternative sources of electricity such as solar and wind. When power is least expensive a smart grid could turn on selected home appliances such as washing machines or factory processes that can run at arbitrary hours. At peak times it could turn off selected appliances to reduce demand. Goals In principle, the smart grid is a simple upgrade of 20th century power grids which generally "broadcast" power from a few central power generators to a large number of users, to instead be capable of routing power in more optimal ways to respond to a very wide range of conditions, and to charge a premium to those that use energy at peak hours. Peak curtailment/leveling and time of use pricing To reduce demand during the high cost peak usage periods, communications and metering technologies inform smart devices in the home and business when energy demand is high and track how much electricity is used and when it is used. To motivate them to cut back use and perform what is called peak curtailment or peak leveling, prices of electricity are increased during high demand periods, and decreased during low demand periods. It is thought that consumers and businesses will tend to consume less during high demand periods if it is possible for consumers and consumer devices to be aware of the high price premium for using electricity at peak periods, this could mean cooking dinner at 9pm instead of 5pm. When businesses and consumers see a direct economic benefit of not having to pay double for the same energy use to become more energy efficient, the theory is that they will include energy cost of operation into their consumer device and building construction decisions. Essential for renewable energy Supporters of renewable energy favor smarter grids, because most renewable energy sources are intermittent in nature, depending on natural phenomena (the sun and the wind) to generate power. Thus, any type of power infrastructure using a significant portion of intermittent renewable energy resources must have means of effectively reducing electrical demand by "load shedding" in the event that the natural phenomena necessary to generate power do not occur. By increasing electricity prices exactly when the desired natural phenomena are not present, consumers will, in theory, decrease consumption. However this means prices are unpredictable and literally vary with the weather, at least to the distribution utility. Platform for advanced services As with other industries, use of robust two-way communications, advanced sensors, and distributed computing technology will improve the efficiency, reliability and safety of power delivery and use. It also opens up the potential for entirely new services or improvements on existing ones, such as fire monitoring and alarms that can shut off power, make phone calls to emergency services and etc… Problem definition The major driving forces to modernize current power grids can be divided in four, general categories. Increasing reliability, efficiency and safety of the power grid. Enabling decentralized power generation so homes can be both an energy client and supplier (provide consumers with interactive tool to manage energy usage). Flexibility of power consumption at the client’s side to allow supplier selection (enables distributed generation, solar, wind, and biomass). Increase GDP by creating more new, green-collar energy jobs related to renewable energy industry manufacturing, plug-in electric vehicles, solar panel and wind turbine generation, energy conservation construction. Smart grid functions Before examining particular technologies, a proposal can be understood in terms of what it is being required to do. The governments and utilities funding development of grid modernization have defined the functions required for smart grids. According to the United States Department of Energy's Modern Grid Initiative report, a modern smart grid must: Be able to heal itself Motivate consumers to actively participate in operations of the grid Resist attack Provide higher quality power that will save money wasted from outages Accommodate all generation and storage options Enable electricity markets to flourish Run more efficiently Enable higher penetration of intermittent power generation sources Self-healing Using real-time information from embedded sensors and automated controls to anticipate, detect, and respond to system problems, a smart grid can automatically avoid or mitigate power outages, power quality problems, and service disruptions. As applied to distribution networks, there is no such thing as a "self healing" network. If there is a failure of an overhead power line, given that these tend to operate on a radial basis (for the most part) there is an inevitable loss of power. In the case of urban/city networks that for the most part are fed using underground cables, networks can be designed (through the use of interconnected topologies) such that failure of one part of the network will result in no loss of supply to end users. A fine example of an interconnected network using zoned protection is that of the Merseyside and North Wales Electricity Board (MANWEB). It is envisioned that the smart grid will likely have a control system that analyzes its performance using distributed, autonomous reinforcement learning controllers that have learned successful strategies to govern the behavior of the grid in the face of an ever changing environment such as equipment failures. Such a system might be used to control electronic switches that are tied to multiple substations with varying costs of generation and reliability. Consumer participation A smart grid is, in essence, an attempt to require consumers to change their behavior around variable electric rates or to pay vastly increased rates for the privilege of reliable electrical service during high-demand conditions. Historically, the intelligence of the grid in North America has been demonstrated by the utilities operating it in the spirit of public service and shared responsibility, ensuring constant availability of electricity at a constant price, day in and day out, in the face of any and all hazards and changing conditions. A smart grid incorporates consumer equipment and behavior in grid design, operation, and communication. This enables consumers to better control (or be controlled by) “smart appliances” and “intelligent equipment” in homes and businesses, interconnecting energy management systems in “smart buildings” and enabling consumers to better manage energy use and reduce energy costs. Advanced communications capabilities equip customers with tools to exploit real-time electricity pricing, incentive-based load reduction signals, or emergency load reduction signals. The real-time, two-way communications available in a smart grid will enable consumers to be compensated for their efforts to save energy and to sell energy back to the grid through net-metering. By enabling distributed generation resources like residential solar panels, small wind and plug-in hybrid, smart grid will spark a revolution in the energy industry by allowing small players like individual homes and small businesses to sell power to their neighbors or back to the grid. The same will hold true for larger commercial businesses that have renewable or back-up power systems that can provide power for a price during peak demand events, typically in the summer when air condition units place a strain on the grid. Resist attack Smart grid technologies better identify and respond to man-made or natural disruptions. Real-time information enables grid operators to isolate affected areas and redirect power flows around damaged facilities. One of the most important issues of resist attack is the smart monitoring of power grids, which is the basis of control and management of smart grids to avoid or mitigate the system-wide disruptions like blackouts. The traditional monitoring is based on weighted least square (WLS) which is very weak and prone to fail when gross errors (including topology errors, measurement errors or parameter errors) are present. New technology of state monitor is needed to achieve the goals of the smart grids. High quality power Outages and power quality issues cost US businesses more than $100 billion on average each year. It is asserted that assuring more stable power provided by smart grid technologies will reduce downtime and prevent such high losses. Accommodate generation options As smart grids continue to support traditional power loads they also seamlessly interconnect fuel cells, renewable, micro turbines, and other distributed generation technologies at local and regional levels. Integration of small-scale, localized, or on-site power generation allows residential, commercial, and industrial customers to self-generate and sell excess power to the grid with minimal technical or regulatory barriers. This also improves reliability and power quality, reduces electricity costs, and offers more customer choice. Enable electricity market Significant increases in bulk transmission capacity will require improvements in transmission grid management. Such improvements are aimed at creating an open marketplace where alternative energy sources from geographically distant locations can easily be sold to customers wherever they are located. Intelligence in distribution grids will enable small producers to generate and sell electricity at the local level using alternative sources such as rooftop-mounted photo voltaic panels, small-scale wind turbines, and micro hydro generators. Without the additional intelligence provided by sensors and software designed to react instantaneously to imbalances caused by intermittent sources, such distributed generation can degrade system quality. Optimize assets A smart grid can optimize capital assets while minimizing operations and maintenance costs. Optimized power flows reduce waste and maximize use of lowest-cost generation resources. Harmonizing local distribution with interregional energy flows and transmission traffic improves use of existing grid assets and reduces grid congestion and bottlenecks, which can ultimately produce consumer savings. Enable high penetration of intermittent generation sources Climate change and environmental concerns will increase the amount of renewable energy resources. These are for the most part intermittent in nature. Smart Grid technologies will enable power systems to operate with larger amounts of such energy resources since they enable both the suppliers and consumers to compensate for such intermittency. Features Existing and planned implementations of smart grids provide a wide range of features to perform the required functions. Load adjustment The total load connected to the power grid can vary significantly over time. Although the total load is the sum of many individual choices of the clients, the overall load is not a stable, slow varying, average power consumption. Imagine the increment of the load if a popular television program starts and millions of televisions will draw current instantly. Traditionally, to respond to a rapid increase in power consumption, faster than the start-up time of a large generator, some spare generators are put on a dissipative standby mode. A smart grid may warn all individual television sets, or another larger customer, to reduce the load temporarily (to allow time to start up a larger generator) or continuously (in the case of limited resources). Using mathematical prediction algorithms it is possible to predict how many standby generators need to be used, to reach a certain failure rate. In the traditional grid, the failure rate can only be reduced at the cost of more standby generators. In a smart grid, the load reduction by even a small portion of the clients may eliminate the problem. Demand response support Demand response support allows generators and loads to interact in an automated fashion in real time, coordinating demand to flatten spikes. Eliminating the fraction of demand that occurs in these spikes eliminates the cost of adding reserve generators, cuts wear and tear and extends the life of equipment, and allows users to cut their energy bills by telling low priority devices to use energy only when it is cheapest. Currently, power grid systems have varying degrees of communication within control systems for their high value assets, such as in generating plants, transmission lines, substations and major energy users. In general information flows one way, from the users and the loads they control back to the utilities. The utilities attempt to meet the demand and succeed or fail to varying degrees (brownout, rolling blackout, uncontrolled blackout). The total amount of power demand by the users can have a very wide probability distribution which requires spare generating plants in standby mode to respond to the rapidly changing power usage. This one-way flow of information is expensive; the last 10% of generating capacity may be required as little as 1% of the time, and brownouts and outages can be costly to consumers. Greater resilience to loading Although multiple routes are touted as a feature of the smart grid, the old grid also featured multiple routes. Initial power lines in the grid were built using a radial model, later connectivity was guaranteed via multiple routes, referred to as a network structure. However, this created a new problem: if the current flow or related effects across the network exceed the limits of any particular network element, it could fail, and the current would be shunted to other network elements, which eventually may fail also, causing a domino effect. A technique to prevent this is load shedding by rolling blackout or voltage reduction (brownout). Decentralization of power generation Another element of fault tolerance of smart grids is decentralized power generation. Distributed generation allows individual consumers to generate power onsite, using whatever generation method they find appropriate. This allows individual loads to tailor their generation directly to their load, making them independent from grid power failures. Classic grids were designed for one-way flow of electricity, but if a local sub-network generates more power than it is consuming, the reverse flow can raise safety and reliability issues. A smart grid can manage these situations. Price signaling to consumers In many countries, including Belgium, the Netherlands and the UK, the electric utilities have installed double tariff electricity meters in many homes to encourage people to use their electric power during night time or weekends, when the overall demand from industry is very low. During off-peak time the price is reduced significantly, primarily for heating storage radiators or heat pumps with a high thermal mass, but also for domestic appliances. This idea will be further explored in a smart grid, where the price could be changing in seconds and electric equipment is given methods to react on that. Also, personal preferences of customers, for example to use only green energy, can be incorporated in such a power grid. Technology The bulk of smart grid technologies are already used in other applications such as manufacturing and telecommunications and are being adapted for use in grid operations. In general, smart grid technology can be grouped into five key areas: Integrated communications Some communications are up to date, but are not uniform because they have been developed in an incremental fashion and not fully integrated. In most cases, data is being collected via modem rather than direct network connection. Areas for improvement include: substation automation, demand response, distribution automation, supervisory control and data acquisition (SCADA), energy management systems, wireless mesh networks and other technologies, power-line carrier communications, and fiber-optics. Integrated communications will allow for real-time control, information and data exchange to optimize system reliability, asset utilization, and security. Sensing and measurement Core duties are evaluating congestion and grid stability, monitoring equipment health, energy theft prevention, and control strategies support. Technologies include: advanced microprocessor meters (smart meter) and meter reading equipment, wide-area monitoring systems, dynamic line rating (typically based on online readings by Distributed temperature sensing combined with Real time thermal rating (RTTR) systems), electromagnetic signature measurement/analysis, time-of-use and real-time pricing tools, advanced switches and cables, backscatter radio technology, and Digital protective relays. Smart meters A smart grid replaces analog mechanical meters with digital meters that record usage in real time. Smart meters are similar to Advanced Metering Infrastructure meters and provide a communication path extending from generation plants to electrical outlets (smart socket) and other smart grid-enabled devices. By customer option, such devices can shut down during times of peak demand. Phasor measurement units High speed sensors called PMUs distributed throughout their network can be used to monitor power quality and in some cases respond automatically to them. Phasors are representations of the waveforms of alternating current, which ideally in real-time, are identical everywhere on the network and conform to the most desirable shape. In the 1980s, it was realized that the clock pulses from global positioning system (GPS) satellites could be used for very precise time measurements in the grid. With large numbers of PMUs and the ability to compare shapes from alternating current readings everywhere on the grid, research suggests that automated systems will be able to revolutionize the management of power systems by responding to system conditions in a rapid, dynamic fashion. A Wide-Area Measurement Systems (WAMS) is a network of PMUS that can provide realtime monitoring on a regional and national scale. Many in the power systems engineering community believe that the Northeast blackout of 2003 would have been contained to a much smaller area if a wide area phasor measurement network was in place. Advanced Components Innovations in superconductivity, fault tolerance, storage, power electronics, and diagnostics components are changing fundamental abilities and characteristics of grids. Technologies within these broad R&D categories include: flexible alternating current transmission system devices, high voltage direct current, first and second generation superconducting wire, high temperature superconducting cable, distributed energy generation and storage devices, composite conductors, and “intelligent” appliances. Advanced control Power system automation enables rapid diagnosis of and precise solutions to specific grid disruptions or outages. These technologies rely on and contribute to each of the other four key areas. Three technology categories for advanced control methods are: distributed intelligent agents (control systems), analytical tools (software algorithms and high-speed computers), and operational applications (SCADA, substation automation, demand response, etc). Using artificial intelligence programming techniques, Fujian power grid in China created a wide area protection system that is rapidly able to accurately calculate a control strategy and execute it. The Voltage Stability Monitoring & Control (VSMC) software uses a sensitivity-based successive linear programming method to reliably determine the optimal control solution. Improved interfaces and decision support Information systems reduce complexity. Operators and managers have tools to effectively and efficiently operate a grid with an increasing number of variables. Technologies include visualization techniques that reduce large quantities of data into easily understood visual formats, software systems that provide multiple options when systems operator actions are required, and simulators for operational training and “what-if” analysis. Standards and groups IEC TC57 has created a family of international standards that can be used as part of the smart grid. These standards include IEC61850 which is an architecture for substation automation, and IEC 61970/61968 — the Common Information Model (CIM). The CIM provides for common semantics to be used for turning data into information. MultiSpeak has created a specification that supports distribution functionality of the smart grid. MultiSpeak has a robust set of integration definitions that supports nearly all of the software interfaces necessary for a distribution utility or for the distribution portion of a vertically integrated utility. MultiSpeak integration is defined using extensible markup language (XML) and web services. The IEEE has created a standard to support synchrophasors — C37.118. A User Group that discusses and supports real world experience of the standards used in smart grids is the UCA International User Group. There is a Utility Task Group within LonMark International, which deals with smart grid related issues. There is a growing trend towards the use of TCP/IP technology as a common communication platform for Smart Meter applications, so that utilities can deploy multiple communication systems, while using IP technology as a common management platform. IEEE P2030 is an IEEE project developing a "Draft Guide for Smart Grid Interoperability of Energy Technology and Information Technology Operation with the Electric Power System (EPS), and End-Use Applications and Loads". NIST has included ITU-T G.hn as one of the "Standards Identified for Implementation" for the Smart Grid "for which it believed there was strong stakeholder consensus". G.hn is standard for high-speed communications over power lines, phone lines and coaxial cables. OASIS EnergyInterop – is an OASIS technical committee developing XML standards for energy interoperation. Its starting point is the California OpenADR standard. 3.2. ADVANCED METERING INFRASTRUCTURE (AMI) In [2], AMI is not a single technology, but rather an integration of many technologies that provides an intelligent connection between consumers and system operators. AMI gives consumers the information they need to make intelligent decisions, the ability to execute those decisions and a variety of choices leading to substantial benefits they do not currently enjoy. In addition, system operators are able to greatly improve consumer service by refining utility operating and asset management processes based on AMI data. Through the integration of multiple technologies (such as smart metering, home area networks, integrated communications, data management applications, and standardized software interfaces) with existing utility operations and asset management processes, AMI provides an essential link between the grid, consumers and their loads, and generation and storage resources. Such a link is a fundamental requirement of a Modern Grid. How does AMI support the vision for the Modern Grid? Initially, Automated Meter Reading (AMR) technologies were deployed to reduce costs and improve the accuracy of meter reads. A growing understanding of the benefits of two-way interactions between system operators, consumers and their loads and resources led to the evolution of AMR into AMI. The vision of the Modern Grid’s seven principal characteristics further reinforces the need for AMI: Motivation and inclusion of the consumer is enabled by AMI technologies that provide the fundamental link between the consumer and the grid. Generation and storage options distributed at consumer locations can be monitored and controlled through AMI technologies. Markets are enabled by connecting the consumer to the grid through AMI and permitting them to actively participate, either as load that is directly responsive to price signals, or as part of load resources that can be bid into various types of markets. AMI smart meters equipped with Power Quality (PQ) monitoring capabilities enable more rapid detection, diagnosis and resolution of PQ problems. AMI enables a more distributed operating model that reduces the vulnerability of the grid to terrorist attacks. AMI provides for self healing by helping outage management systems detect and locate failures more quickly and accurately. It can also provide a ubiquitous distributed communications infrastructure having excess capacity that can be used to accelerate the deployment of advanced distribution operations equipment and applications. AMI data provides the granularity and timeliness of information needed to greatly improve asset management and operations. What is AMI? AMI is not a single technology implementation, but rather a fully configured infrastructure that must be integrated into existing and new utility processes and applications. This infrastructure includes home network systems, including communicating thermostats and other in-home controls, smart meters, communication networks from the meters to local data concentrators, back-haul communications networks to corporate data centers, meter data management systems (MDMS) and, finally, data integration into existing and new software application platforms. Additionally, AMI provides a very “intelligent” step toward modernizing the entire power system. Figure 4 below graphically describes the AMI technologies and how they interface: At the consumer level, smart meters communicate consumption data to both the user and the service provider. Smart meters communicate with in-home displays to make consumers more aware of their energy usage. Going further, electric pricing information supplied by the service provider enables load control devices like smart thermostats to modulate electric demand, based on pre-established consumer price preferences. More advanced customers deploy distributed energy resources (DER) based on these economic signals. And consumer portals process the AMI data in ways that enable more intelligent energy consumption decisions, even providing interactive services like prepayment. The service provider (utility) employs existing, enhanced or new back office systems that collect and analyze AMI data to help optimize operations, economics and consumer service. For example, AMI provides immediate feedback on consumer outages and power quality, enabling the service provider to rapidly address grid deficiencies. And AMI’s bidirectional communications infrastructure also supports grid automation at the station and circuit level. The vast amount of new data flowing from AMI allows improved management of utility assets as well as better planning of asset maintenance, additions and replacements. The resulting more efficient and reliable grid is one of AMI’s many benefits. What are the technology options for AMI? An AMI system is comprised of a number of technologies and applications that have been integrated to perform as one: • Smart meters • Wide-area communications infrastructure • Home (local) area networks (HANs) • Meter Data Management Systems (MDMS) • Operational Gateways Smart Meters Conventional electromechanical meters served as the utility cash register for most of its history. At the residential level, these meters simply recorded the total energy consumed over a period of time – typically a month. Smart meters are solid state programmable devices that perform many more functions, including most or all of the following: • Time-based pricing • Consumption data for consumer and utility • Net metering • Loss of power (and restoration) notification • Remote turns on / turns off operations • Load limiting for “bad pay” or demand response purposes • Energy prepayment • Power quality monitoring • Tamper and energy theft detection • Communications with other intelligent devices in the home And a smart meter is a green meter because it enables the demand response that can lead to emissions and carbon reductions. It facilitates greater energy efficiency since information feedback alone has been shown to cause consumers to reduce usage. Communications Infrastructure The AMI communications infrastructure supports continuous interaction between the utility, the consumer and the controllable electrical load. It must employ open bidirectional communication standards, yet be highly secure. It has the potential to also serve as the foundation for a multitude of modern grid functions beyond AMI. Various architectures can be employed, with one of the most common being local concentrators that collect data from groups of meters and transmit that data to a central server via a backhaul channel. Various media can be considered to provide part or all of this architecture: • Power Line Carrier (PLC) • Broadband over power lines (BPL) • Copper or optical fiber • Wireless (Radio frequency), either centralized or a distributed mesh • Internet • Combinations of the above Future inclusion of smart grid applications and potential consumer services should be considered when determining communication bandwidth requirements. Home Area Networks (HAN) A HAN interfaces with a consumer portal to link smart meters to controllable electrical devices. Its energy management functions may include: • In-home displays so the consumer always knows what energy is being used and what it is costing • Responsiveness to price signals based on consumer-entered preferences • Set points that limit utility or local control actions to a consumer specified band • Control of loads without continuing consumer involvement • Consumer over-ride capability The HAN/consumer portal provides a smart interface to the market by acting as the consumer’s “agent.” It can also support new value added services such as security monitoring. A HAN may be implemented in a number of ways, with the consumer portal located in any of several possible devices including the meter itself, the neighborhood collector, a standalone utility-supplied gateway or even within customer-supplied equipment. Operational Gateways AMI interfaces with many system-side applications (see MDMS above) to support: Advanced Distribution Operations (ADO) Distribution Management System with advanced sensors (including PQ data from AMI meters) Advanced Outage Management (real-time outage information from AMI meters) DER Operations (using Watt and VAR data from AMI meters) Distribution automation (including Volt/VAR optimization and fault location, isolation, sectionalization and restoration (FLISR)) Distribution Geographic Information System Application of AMI communications infrastructure for: o Micro-grid operations (AC and DC) o Hi-speed information processing o Advanced protection and control o Advanced grid components for distribution Advanced Transmission Operations (ATO) Substation Automation Hi-speed information processing Advanced protection and control (including distribution control to improve transmission conditions) Modeling, simulation and visualization tools Advanced regional operational applications Electricity Markets Advanced Asset Management (AAM) AMI data will support AAM in the following areas: System operating information Asset “health” information Operations to optimize asset utilization T&D planning Condition-based maintenance Engineering design and construction Consumer service Work and resource management Modeling and simulation 3.3. WIRELESS MESH NETWORK In [3], Wireless Mesh Network (WMN) is a highly promising technology and it plays an important role in the next generation wireless mobile network. WMNs have emerged as important architectures for the future wireless communications. WMNs consist of mesh routers and mesh clients, and could be independently implemented or integrated with other communication systems such as the conventional cellular systems. In addition, WMN are dynamic self-organized, self-healed, and self-configured, and enable quick deployment, easy maintenance, low cost, high scalability and reliable service. WMN is an ad-hoc network extension and is becoming an important mode complimentary to the infrastructure based wireless networks because they can enhance network capacity, connectivity and resilience. We can define a WMN as a network that has a network topology of either a partial or full mesh topology. In practice, WMNs are characterized by static wireless relay nodes which provide a distributed infrastructure for client nodes over a partial mesh topology. Due to the presence of partial mesh topology, a WMN utilizes multi-hop relaying like other ad hoc wireless networks. Important Issues in Wireless Mesh Networks In this section we discuss important aspects that must be taken into account in wireless mesh networks, such as the throughput capacity, scalability, fairness, reliability and robustness, and resource management [14]. Theoretical Throughput Capacity In data communication systems, throughput is defined as the number of bits, or characters (data) per unit of time that is delivered over a wired or wireless medium. As an example, we could say that throughput is the amount of data per second passing through a wire connecting two computers. Then, the total network capacity is the maximum throughput of a node or communication link. In WMNs, one of its big limitations is the network capacity. The theoretical upper limit of every node throughput capacity is asymptotically limited by (1/√n) where n is the number of nodes in the network. Therefore, increasing the number of nodes, the throughput capacity per node becomes unacceptably low. In general, the throughput capacity achievable in a WMN is proportional to the (W × n−1/d) where d is the dimension of the network and W is the total bandwidth. One approach to improve the throughput capacity is the use of multiple radio and fine tuned protocols. WMN nodes have a more limited throughput capacity in a single-channel system than in a multi-channel system. Moreover, other factors contribute to the throughput degradation such as characteristics of MAC protocol, the hidden terminal problem, the exposed node problem, and the error rate in the wireless channel; which have more effect in a singlechannel system. Scalability When the coverage area increases to serve more users, multi-hop networking suffers from the scalability issue. This is because in the multi-hop WMNs throughput enhancement and coverage extension are two contradictory goals. On one hand, the multi-hop communications can extend the coverage area to lower the total infrastructure cost. On the other hand, as the number of hops increases, the repeatedly relayed traffic will exhaust the radio resource. In the meanwhile, the throughput will sharply degrade due to the increase of collisions from a large number of users. Therefore it becomes an important and challenging issue to design a scalable wireless mesh network, so that the coverage of a WMN can be extended without sacrificing the system overall throughput [19]. Resource Management Resource management means the efficient management of network resources such as energy, bandwidth, interfaces, and storage. For example, if we consider a node with two interfaces, one low-power node and another regular one, then the WMN can use efficiently the energy resources. The overall power consumption, even in idle mode, depends very much on the type of interface. Therefore, in an IEEE 802.11-based WMN with limited energy reserve, an additional low-power and low data rate interface can be used to carry out-of-band signaling information to control the high-power and high-data rate data interface. Bandwidth resources can also be managed better in a multi-radio environment. For example, the load balancing across multiple interfaces could avoid a channel to get very congested and therefore a possible bottleneck. In addition, the bandwidth of each interface could be aggregated to obtain a high effective data rate. Finally, in such a bandwidth aggregation mechanism (bandwidth striping), dynamic packet scheduling can be utilized to obtain an even better performance. Fairness Fairness, from the MAC perspective, can be achieved if the MAC protocol does not present preference for any single node when multiple nodes are trying to access the same channel. Then, we can say that the bandwidth is shared fairly. WMN single-radio nodes also face high throughput unfairness. We say that a network has high throughput fairness if all nodes get equal throughput under similar conditions of source traffic and network load. WMNs show high throughput unfairness among the contending traffic flows especially when CSMA/CA-based MAC protocols are employed for contention resolution. Three important properties associated with CSMA/CA-based MAC protocols, when used in a WMN environment are: (i) information asymmetry, (ii) location dependent contention, and (iii) half-duplex character of single-channel systems. Information asymmetry is caused by the lack of information at certain nodes, but also having excessive information may also contribute to throughput unfairness. For example, when a node is exposed to two flows, its Network Allocation Vector (NAV) is always set and therefore abstains from transmitting. In addition, the half-duplex property of a single-interface system is another property that causes high throughput unfairness in a single-radio WMN. Due to the half-duplex characteristics, no node can simultaneously receive and transmit over the network. Reliability and Robustness WMNs improve the reliability and robustness of communication. The partial mesh topology in a WMN provides high reliability and path diversity against node and link failures. Multi-Radio WMNs (MR-WMN) provide the most important advantage for robustness in communication diversity. For example, in wireless systems channel errors can be very high compared to wired networks; therefore, graceful degradation of communication quality during high channel errors is necessary. The use of multiple radio interfaces allows frequency diversity; therefore instead of having a full loss of connectivity, we achieve graceful degradation. Moreover, MRWMNs can use appropriate radio switching modules to achieve fault tolerance in communication either by switching the radios, channels, or by using multiple radios simultaneously. Security Security is a major issue in both wired and wireless networks. In a wired network, the transmission medium can be physically secured, and access to the network as well. On the other hand, in a wireless network, security is more difficult to implement, since the transmission medium is open to anyone within the geographical range of a transmitter. In recent years, many security schemes have been proposed for Ad hoc wireless networks that can also be applicable to WMNs. However, these schemes are not good enough to be implemented in real scenarios. Moreover, because the difference in infrastructure between Ad hoc and WMN, some proposed solutions for the first are ineffective for the later. In order to better understand the security issue, we need to learn what attacks exist. Attacks can be seen from a general perspective as active and passive attacks, and from the network layer, specifically with respect to routing protocols. In active attacks, information is injected into the network by replicating, modifying or deleting exchanged data. On the other hand, in passive attacks, one subtype is passive eavesdropping, where the attacker intents to discover nodes information by listening to ongoing traffic. From the routing perspective, there are several specific attacks targeting the operation of a routing protocol. 1. Location Disclosure: It happens when the attacker tries to obtain network information such as the location of a node, or the network structure. 2. Black Hole: In this attack, false routing advertising is injected in such a way that the attacker is able to capture most packets from other nodes with the purpose of eavesdropping, or perform denial of service by dropping all received packets. 3. Replay: In replay attack, previously captured routing traffic is sent back into the network to target new routes. 4. Wormhole: This attack requires two malicious nodes where one node captures routing traffic, and sends it to the other malicious node. Then, the second node can send back selective information to the network. 5. Blackmail: Here, the attacker can fabricate a list to block nodes and inject it into the network. This attack targets routing protocols that block malicious nodes by sending a black list of offenders to legitimate nodes. 6. Denial of Service: This attack has two types: a) Routing table overflow, and b) Sleep deprivation torture. In the first type, the attacker floods the network with bogus route creation packets in order to prevent the correct creation of routing information, and to consume resources of nodes. In Sleep deprivation torture, the attacker sends diverse routing information to a specific node in order to make it consume its batteries because of the constant routing processing. 7. Routing Table Poisoning: In this attack, the routing table is affected by receiving modified messages or fabricated signaling traffic in order to create false entries in the routing tables of participating nodes. Thus, routes may not be optimal, or routing loops, and bottlenecks are produced. Since most important attacks are identified, the research community is constantly addressing the security issue by proposing new routing protocols using three different means or the a combination of them: 1) symmetric cryptography, 2) asymmetric cryptography, and 3) reputation systems. Proposed routing protocols include the following: • Authenticated Routing for Ad hoc Networks (ARAN) • ARIADNE: A Secure On-Demand Routing Protocol for Ad Hoc Networks. • Detecting and Correcting Malicious Data (DCMD) • Secure Ad hoc on demand Distance Vector (SAODV) • Secure Efficient Distance Vector Routing for Mobile Wireless Ad Hoc Networks (SEAD) • Secure Link State routing Protocol (SLSP) • Secure Position Aided Ad hoc Routing (SPAAR) • WATCHDOG-PATHRATER • Ad hoc on demand Distance Vector (AODV-SEC) • Building secure routing out of an Incomplete Set of Secure associations (BISS) • PACKET-LEASHES • Vehicle Ad hoc network Reputation System (VARS) • EndairALoc Other approaches at the link layer implement mechanisms based on cryptography to address authorization and privacy on radio links. In addition, the IEEE 802.11 standard considers Wired Equivalent Privacy (WEP) to provide security in wireless networks. WEP supports data encryption and integrity by using a secret key shared by all devices of a WLAN, or a pair-wise secret key shared by only two communicating devices. Wireless Mesh Network Architectures Based on its network topology, a WMN can be classified into three types: flat WMN, Hierarchical WMN, and Hybrid WMN. We briefly discuss these categories in the following sub-sections. Flat Wireless Mesh Network In a flat WMN, the network is formed by nodes that are both clients and routers. Here, each node is at the same level as that of its peers. The wireless client nodes coordinate among themselves to provide routing, network configuration, services, and other applications. This architecture is similar to an ad hoc wireless network and it is the simplest type among the three WMN architectures. One of its advantages is its simplicity, and its disadvantages include lack of network scalability and high resource constraints. Hierarchical Wireless Mesh Network In a hierarchical WMN, the network has multiple tiers or levels where the WMN client nodes form the lowest tier in the hierarchy. These client nodes can communicate with a WMN backbone network formed by WMN routers. In most cases, the WMN router nodes are dedicated nodes that form a WMN backbone network. This means that the backbone nodes may not be a source or final destination of data traffic like the WMN client nodes. The responsibility to self-organize, self-heal, and maintain the backbone network is provided for the WMN routers, some of which in the backbone network may have external connections to other resources such as the Internet, and other servers in a wired network, then such nodes are called gateway nodes. Hybrid Wireless Mesh Networks Hybrid WMNs are a special case of hierarchical WMNs where the WMN utilizes other wireless networks for communication. For example, Hybrid WMN uses other infrastructure-based WMNs such as cellular networks, WiMAX networks, or satellite networks. These hybrid WMNs may use multiple technologies for both WMN backbone and back haul. Since the growth of WMNs depends heavily on how it works with other existing wireless networking solutions, this architecture becomes very important in the development of WMNs. STANDARDS The current and increasing interest in wireless mesh technologies has led to the creation of Working Groups (WG) as part of the standardization activities. In these WGs, the Study groups (SG) or Task groups (TG) are in charge of develop mesh functionality for Wireless Local Area Networks (IEEE 802.11s), Wireless Personal Area Networks (IEEE 802.15.5), and Wireless Metropolitan Area Networks (IEEE 802.16). In this section, we describe these standards and their goals as clear objectives that remark the current needs and trends of wireless mesh networks. IEEE 802.11s In September 2003, IEEE formed the 802.11s SG which, in July 2004, became the “Extended Service Set (ESS) Mesh Networking” or 802.11s Task Group (TGs), and it is the most advanced group of the 802.11 WG. The current objective of this TG is to apply mesh technology to WLANs by defining a Wireless Distribution System (WDS) used to build a wireless infrastructure with MAC-layer broadcast/multicast support in addition to the unicast transmissions. The TG should produce a protocol that specifies the installation, configuration, and operation of WLAN mesh. Moreover, the specification should include the extensions in topology formation to make the WLAN mesh self-configure and self-organized, and support for multi-channel, and multi-radio devices. At the MAC layer, a selection path protocol should be incorporated, instead of assigning the routing task to the network layer. The WLAN Mesh architecture comprises the following IEEE 802.11 based elements: • Mesh Points (MP) which supports (fully or partially) mesh relay functions, and implement operations such as channel selection, neighbor discovery, and forming and association with neighbors. Additionally, MPs communicate with their neighbors and forward traffic on behalf of other MPs. • Wireless Distribution System (WDS) which is a collection of MPs, and serves similarly to a Distribution System (DS) in a WLAN. • Mesh Access Point (MAP) which is a MP but acts as an AP as well. Therefore, MAPs can operate in a WLAM Mesh or as part of legacy IEEE 802.11 modes. • Mesh Portals (MPP) are another kind of MP that allows the interconnection of multiple WLAN meshes to form a network of mesh networks. Moreover, MPP can function as bridges or gateways to connect to other wired or wireless networks in the DS. Wi-Fi Security Security is an important issue in wireless network. Since Wi-Fi is a wireless technology, it is also vulnerable to security threats. Anybody with a wireless adapter can access the network within the coverage area. Wired Equivalent Privacy (WEP) was used previously for securing the wireless access network, but it has many vulnerabilities and currently Wi-Fi network use different technology for its security. Wi-Fi Protected Access (WPA): WPA is an improved and interoperable security mechanism which addressed all known vulnerabilities of the WEP protocol. It adds user authentication and increases the level of encryption which ensures that user’s data is protected and only authorized users are accessing the network. For encrypting the data WPA uses temporal key integrity protocol (TKIP). Wi-Fi Protected Access 2 (WPA2): WPA2 is an updated version of WPA which ensures higher level of security. It uses Advance Encryption Standard (AES) algorithm for encrypting the data. National Institute of Standard and Technology (NIST) defines two versions of WPA2, WPA2 enterprise and WPA2 personal. In WPA2 enterprise, server verifies the network users and WPA2 personal is protected by assigning a password. Extensible Authentication protocol (Extended EAP): This technology further improves the WPA and WPA2. It also ensures higher degree of interoperability between the enterprise and personal user. IEEE 802.15.5 In May 2004, the IEEE 802.15 WG formed the Task Group 5 (TG5) with the objective of developing a standard for Wireless Personal Area Networks (WPAN) further divided into low rate mesh WPAN and high rate mesh WPAN. Mesh WPANs are small closed wireless networks with a flat hierarchy which generally do not have an Internet gateway, or APs. For TG5, there are two types of applications: a) low-rate applications such as sensor networks, and b) high-rate applications such as control and maintenance applications, and multimedia applications. TG5 develops a single “WPAN Mesh” document for both types of applications, but separate them when necessary. TG5 shall provide specifications for an architectural framework for interoperable, stable, and scalable wireless mesh topologies for WPAN devices. The current TG5 proposal defines a tree based approach named Adaptive Robust Tree (ART) which considers a mesh tree routing approach, multicasting, and key pre-distribution. In ART, each node maintains an ART Table (ARTT) to track the tree branches through assigned addresses. ART also defines three phases: 1. Initialization or configuration phase. The ART tree is established while nodes joint the network. Additionally, this phase considers two stages: • Association. Nodes gradually joint the network starting in the root node of the tree. • Address assigning. When the tree is complete, nodes indicate the number of addresses they need, and finally all nodes have an ARTT built. 2. Operation phase. Nodes start sending and receiving data. Also, reconfiguration may take place if more nodes joint the network. 3. Recovery phase. It starts when network is broken for link failures or routing node failures. In recovery phase only parts of the tree can be reconstructed while other parts are still operating correctly. In this manner, the repair and recovery may not need to reassign addresses to nodes. On top of the ART, a meshed ART (MART) is formed in such a way that root nodes are connected one to another. Therefore, root nodes treat each other as child or leaf node in the local routing tree. In this way, these nodes decide on which neighbor to choose as next hop by using the tree previously formed. IEEE 802.16 In 1999, the IEEE established the IEEE 802.16 WG on Broadband Wireless Access Standards which aims to develop recommended practices and standards to support the development and deployment of broadband wireless metropolitan area networks (WMAN). The official name for the IEEE 802.16 family of standards is Wireless MAN, but the industry named it as “Worldwide Interoperability for Microwave Access” (WiMAX) which basically, standardizes the physical (PHY) layer and MAC sub-layer. Currently, various amendments are in progress, such as the case of IEEE 802.16j amendment for Multi-hop Relay Specification. Then, the TGj was formed in March 2006 to work on Wireless Relay Networks (WRN) which bases on master-slave architecture. In IEEE 802.16j, a Base Station (BS) functions as an AP, and controls the WMAN. Subscriber Stations (SS) are wireless nodes that synchronize to the BS and other neighboring SSs in order to exchange frames via the central BS, and forward data on request of its BS. Also, IEEE 802.16j improves previous IEEE 802.16 standards by introducing relay stations (RSs) which incorporates BS functionalities to extend the coverage area by relaying traffic between a SS and a BS or between other RSs or between an RS and a BS. There are three types of RSs: 1. Fixed Relay Station (FRS) which does not have mobility. 2. Nomadic Relay Station (NRS) which has fixed location for periods comparable to a user session. 3. Mobile Relay Station (MRS) that forwards data even when being in motion. Due to the increased interests, and low cost of WMN, 802.16j is more likely to be successfully deployed in the market. The FRS concept offers the possibility to cheaply increase the range of BS. WiMAX Security IEEE 802.16 standard clearly describes the security issues for fixed and mobile WiMAX network. It also shows how to secure the physical and MAC layer. In this security mechanism, security sub-layer is responsible for authentication and encryption processes and privacy and key management protocol (PKM) is responsible for user privacy from theft of services. This security sub-layer use authenticated key management protocol where BS is responsible for distributing keying data to the SS. On the whole, WiMAX security architecture deals with all of the basic wireless security requirements like authentication, authorization, access control, data integrity and privacy. 3.4. NETWORK SIMULATION Simulation is one of the most widely used quantitative approaches to decision making. It is a method for learning about a real system by experimenting with a model that represents the system. The simulation model contains the mathematical expressions and logical relationships that describe how to compute the value of the outputs given the values of the inputs. Any simulation model has two inputs: controllable inputs and probabilistic inputs. Simulation is not an optimization technique. It is a method that can be used to describe or predict how a system will operate given certain choices for the controllable inputs and randomly generated values for the probabilistic inputs. In computer network research, network simulation is a technique where a program simulates the behavior of a network. The program performs this simulation either by calculating the interaction between the different virtual network entities (hosts/routers, data links, packets, etc) using mathematical formulas, or actually capturing and playing back network parameters from a real production network. Using this input, the behavior of the network and the various applications and services it supports can be observed in a test lab. Various attributes of the environment can also be modified in a controlled manner to asses these behaviors under different conditions. When a simulation program is used in conjunction with live applications and services in order to observe end-to-end performance to the user desktop, this technique is also referred to as network emulation. Network simulators are used to predict the behavior of networks and applications under different situations. Researchers use network simulators to see how their protocols would behave if deployed. It is typical to use a network simulator to test routing protocols, MAC (Medium Access Control) protocols, transport protocols, applications etc. Companies use simulators to design their networks and/or applications to get a feel for how they will perform under current or projected real-world conditions. The simulator (or network simulator) is the program in charge of calculating how the network would behave. They may be distributed in source form (software) or provided in the form of a hardware appliance. Users can then customize the simulator to fulfill their specific analysis needs. Properties of a network simulator, which can be used as well for categorizing criteria, may be the following: • Operating system that is running on. The most often case is Linux, FreeBSD or some sort of UNIX but also Solaris, Mac, Windows, HP-UX, MS, MS-dos can be met. • Availability of source code. A simulator can be distributed with its source code for any user interested in further development of the application. • Free of any charge or not. Although an open source simulator most of the times means free of charge the opposite is not always true. It can be distributed for free but no code available. • • • • Discrete event or continuous time/space modeling. Most of the computer network simulators use discrete event modeling which is most appropriate for representing networks. Software development environment (framework) or install and ready to go package. Broad range of networks, protocols, network components, etc. covered or specific for e.g. wireless networks, ATM protocol, transport layer, etc. Simulation, emulation software or both. Simulation s/w simulates offline a network, real or imaginary, that all of its entities are virtually operating in the model. Emulation s/w makes use of both parts of a real network (servers, PCs, links) and virtual parts (entities). Thus emulation must, at least partially, operate online with a real network in order to be fed from it with its required inputs. The following network simulators presented in this paper are: NS-2, and NCTUns. NS-2 (Network Simulator 2) NS2 is open source simulation software that is part of a research project, called VINT, funded by DARPA. The aim of VINT is to build a network simulator that will allow the study of scale and protocol interaction in the context of current and future network protocols. VINT is a collaborative project involving USC/ISI, Xerox PARC, LBNL, and UC Berkeley. NS2 is a discreet event simulator targeted at networking research and provides substantial support for simulation of routing, multicast protocols and IP protocols, such as UDP, TCP, RTP and SRM over wired and wireless (local and satellite) networks. It has many advantages that make it a useful tool, such as support for multiple protocols and the capability of graphically detailing network traffic. Additionally, NS2 supports several algorithms in routing and queuing. LAN routing and broadcasts are part of routing algorithms. Queuing algorithms include fair queuing, deficit round-robin and FIFO. NS2 is available on several platforms such as FreeBSD, Linux, SunOS and Solaris. NS2 also builds and runs under Windows. NS is written in C++. The package provides a compiled class hierarchy of objects written in C++ and an interpreted class hierarchy of objects written in OTcl (MIT's object extension to Tcl - Tool Command Language) which are closely related to the compiled ones. The user creates new objects through the OTcl interpreter. New objects are closely mirrored by a corresponding object in the compiled hierarchy. Tcl procedures are used to provide flexible and powerful control over the simulation (start and stop events, network failure, statistic gathering and network configuration). The Tcl interpreter has been extended (OTcl) with commands to create the networks topology of links and nodes and the agents associated with nodes. The simulation is configured, controlled and operated through the use of interfaces provided by the OTcl class Simulator. The class provides procedures to create and manage the topology, to initialize the packet format and to choose the scheduler. It stores internally references to each element of the topology. The user creates the topology using OTcl through the use of the standalone classes node and link that provide a few simple primitives. The function of a node is to receive a packet, to examine it and map it to the relevant outgoing interfaces. A node is composed of simpler classifier objects. Each classifier in a node performs a particular function, looking at a specific portion of the packet and forwarding it to the next classifier. Agents are another type of components of a node: those model endpoints of the network where packets are fed or consumed. Users create new sources or sinks from the class Agent. NS currently supports various TCP agents, CBR, UDP, and others protocols, including RTP, RTCP, SRM. There is no mention of ATM protocols. Links are characterized in terms of delay and bandwidth. They are built from a sequence of connector objects. The data structure representing a link is composed by a queue of connector objects, its head, the type of link, the ttl (time to live), and an object that processes link drops. Connectors receive packet, perform a function, and send the packet to the next connector or to the drop object. Various kinds of links are supported, e.g. point-to-point, broadcast, wireless. The output buffers attached to a link in a “real” router in a network are modeled by queues. In NS, queues are considered as part of a link. NS allows the simulation of various queuing and packet scheduling disciplines. C++ classes provided include drop-tail (FIFO) queuing, Random Early Detection (RED) buffer management, CBQ (priority and roundrobin), Weighted Fair Queuing (WFQ), Stochastic Fair Queuing (SFQ) and Deficit RoundRobin (DRR). Traffic generation in NS looks rather basic in the current implementation. For the purpose of TCP, only FTP and Telnet traffic can be generated; otherwise, NS provides an exponential on/off distribution and it allows generating traffic according to a trace file. In order to analyze results, NS provides classes to trace each individual packet as it arrives, departs or is dropped, and to record any kind of counts, applied on all packets or a perflow basis. The trace can be set or unset as desired by the user. The user has to specify the routing strategy (static, dynamic) and protocol to be used. This is done with a procedure in the class simulator. Supported routing features include asymmetric routing, multipath routing, Distance Vector algorithm, multicast routing. Other features of NS include error models where the unit could be packet, bit or time based, and mathematical classes for the approximation of continuous integration by discrete sums and for random number generation. In order to verify some aspects of the protocol to be simulated, NS includes some validation tests distributed with the simulator. Νs as well includes capabilities to make the simulation topologies dynamic although this latest point is still somewhat experimental. The simulation engine is extensible, configurable and programmable. The current implementation is single-threaded (only one event in execution at any given time). It does not support partial execution of events nor pre-emption. Events are described by a firing time and a handler function. The type of event scheduler used to drive the simulation can be chosen among the four presently available: a simple linked-list (default), heap, calendar queue, and a special type called real-time. Each one is implemented using a different data structure. The simple linked-list scheduler provides a list of events kept in time-order, from the earliest to the latest. This requires scanning the list to find the appropriate entry upon insertion or deletion. The entry at the head is always executed first. Entries with the same simulated time are extracted according to their order in the list. The heap scheduler code is borrowed from the MARS-2.0 simulator (that itself borrowed the code from MIT'S NETSIM). This implementation is superior to the linked list scheduler when the number of events is large. In the calendar queue scheduler implementation, events with the same “month/day” of multiples “year” are recorded in one “day”. The real-time scheduler is still under development and is currently a subclass of the list scheduler. It is well suited when events arrive with a relatively slow rate. Execution of events should occur in real time. NS has scaling constraints in terms of storage requirements of the routing tables: each node maintains a route to all other nodes in the network, resulting in aggregate memory. This grows with the number of nodes in the network. VINT proposes to replace NS's flat addressing conventions by implementing efficient hierarchical routing table look-ups in the nodes objects. NS represents an underlying transmission link and its corresponding scheduling and queuing algorithms in a single object, but the VINT simulation framework will require their separation in order to flexibly combine different scheduling algorithms with different underlying link technologies. In the current implementation of NS, each module that implements a scheduling discipline need be changed when adding modules to support a new link type. Another modification is the performance improvement to the event scheduler. The linear search insertion algorithm should be replaced with a heap or a calendar queue. Coexistent scheduling algorithms can be derived from base class abstraction and are easily implemented in NS due to its C++ implementation. A graphical interface of NS2 to setup network simulations is NAM that supports a drag-anddrop user interface. Nam is a Tcl/TK based animation tool for viewing network simulation traces and real world packet traces. It supports topology layout, packet level animation, and various data inspection tools. Nam began at LBL. It has evolved substantially over the past few years. The Nam development effort was an ongoing collaboration with the VINT project. Currently, it is being developed at ISI as part of the SAMAN and Conser projects. For the study of protocol interaction and behavior at significantly larger scale, the simulator will provide two levels of abstraction. The detailed level simulator is the one currently built. It allows a fine abstraction of the distinct modules of the simulation and will later include an emulation interface that will allow incorporating a real network node as a component of the simulation. The session level simulator will give a coarse-grain abstraction. Data packets will be represented by flows instead of individual packets. This will reduce the number of events and state required, at the cost of lost detail in the simulation. As an instance, instead of tracing each packet through each router and link, the simulator only calculate the time for that packet to be received by the sink according to the path used. The project also hopes to apply parallel network simulation techniques because the limits of a single-processor computational power will necessarily be stressed. The project will implement a distributed version of the simulator. NCTUns The NCTUns is a high-fidelity and extensible network simulator and emulator capable of simulating various protocols used in both wired and wireless IP networks. Its core technology is based on the novel kernel re-entering methodology invented by Prof. S.Y. Wang when he was pursuing his Ph.D. degree at Harvard University. Due to this novel methodology, NCTUns provides many unique advantages that cannot be easily achieved by traditional network simulators such as ns-2 and OPNET. Figure 4.1 Screenshot of topology editor The NCTUns network simulator and emulator has many useful features listed below: It can be used as an emulator. An external host in the real world can exchange packets (e.g., set up a TCP connection) with nodes (e.g., host, router, or mobile station) in a network simulated by NCTUns. Two external hosts in the real world can also exchange their packets via a network simulated by NCTUns. This feature is very useful as the function and performance of real-world devices can be tested under various simulated network conditions. It directly uses the real-life Linux’s TCP/IP protocol stack to generate high-fidelity simulation results. By using a novel kernel re-entering simulation methodology, a real-life UNIX (e.g., Linux) kernel’s protocol stack can be directly used to generate high-fidelity simulation results. It can use any real-life existing or to-be-developed UNIX application program as a traffic generator program without any modification. Any real-life program can be run on a simulated network to generate network traffic. This enables a researcher to test the functionality and performance of a distributed application or system under various network conditions. Another important advantage of this feature is that application programs developed during simulation studies can be directly moved to and used on real- world UNIX machines after simulation studies are finished. This eliminates the time and effort required to port a simulation prototype to a real-world implementation if traditional network simulators are used. It can use any real-life UNIX network configuration and monitoring tools. For example, the UNIX route, ifconfig, netstat, tcpdump, traceroute commands can be run on a simulated network to configure or monitor the simulated network. Its setup and usage of a simulated network and application programs are exactly the same as those used in real-world IP networks. For example, each layer-3 interface has an IP address assigned to it and application programs directly use these IP addresses to communicate with each other. For this reason, any person who is familiar with real-world IP networks can easily learn and operate NCTUns in a few minutes. For the same reason, NCTUns can be used as an educational tool to teach students how to configure and operate a real-world network. It simulates many different and new types of networks. The supported types include Ethernet-based fixed Internet, IEEE 802.11(b) wireless LANs, mobile ad hoc (sensor) networks, GPRS cellular networks, optical networks (including both circuit-switching and busrt-switching networks), IEEE 802.11(b) dual-radio wireless mesh networks, IEEE 802.11(e) QoS wireless LANs, Tactical and active mobile ad hoc networks, and 3dB beamwidth 60-degree and 90-degree directional antennas. It simulates various networking devices. For example, Ethernet hubs, switches, routers, hosts, IEEE 802.11 (b) wireless stations and access points, WAN (for purposely delaying/dropping/reordering packets), obstacle (block/attenuate wireless signal, block mobile nodes’ movement, block mobile nodes’ views), GPRS base station, GPRS phone, GPRS GGSN, GPRS SGSN, optical circuit switch, optical burst switch, QoS DiffServ interior and boundary routers, IEEE 802.11(b) dual-radio wireless mesh access point, IEEE 802.11(e) QoS access points and mobile stations, etc. It simulates various protocols. For example, IEEE 802.3 CSMA/CD MAC, IEEE 802.11 (b) CSMA/CA MAC, IEEE 802.11(e) QoS MAC, IEEE 802.11(b) wireless mesh network routing protocol, learning bridge protocol, spanning tree protocol, IP, Mobile IP, Diffserv (QoS), RIP, OSPF, UDP, TCP, RTP/RTCP/SDP, HTTP, FTP, Telnet, etc. It simulates a network quickly. By combining the kernel re-entering methodology with the discrete-event simulation methodology, a simulation job can be finished quickly. It generates repeatable simulation results. If the user fixes the random number seed for a simulation case, the simulation results of a case are the same across different simulation runs even if there are some other activities (e.g., disk I/O) occurring on the simulation machine. It provides a highly-integrated and professional GUI environment. This GUI can help a user (1) draw network topologies, (2) configure the protocol modules used inside a node, (3) specify the moving paths of mobile nodes, (4) plot network performance graphs, (5) playing back the animation of a logged packet transfer trace, etc. All these operations can be easily and intuitively done with the GUI. Its simulation engine adopts an open-system architecture and is open source. By using a set of module APIs provided by the simulation engine, a protocol developer can easily implement his (her) protocol and integrate it into the simulation engine. NCTUns uses a simple but effective syntax to describe the settings and configurations of a simulation job. These descriptions are generated by the GUI and stored in a suite of files. Normally the GUI will automatically transfer these files to the simulation engine for execution. However, if a researcher wants to try his (her) novel device or network configurations that the current GUI does not support, he (she) can totally bypass the GUI and generate the suite of description files by himself (herself) using any text editor (or script program). The non-GUIgenerated suite of files can then be manually fed to the simulation engine for execution. It supports remote and concurrent simulations. NCTUns adopts a distributed architecture. The GUI and simulation engine are separately implemented and use the client-server model to communicate. Therefore, a remote user using the GUI program can remotely submit his (her) simulation job to a server running the simulation engine. The server will run the submitted simulation job and later return the results back to the remote GUI program for analyses. This scheme can easily support the cluster computing model in which multiple simulation jobs are performed in parallel on different server machines. This can increase the total simulation throughput. It provides complete and high-quality documentations. The GUI user manual has 118 pages while the protocol developer manual has 320 pages. NCTUns also provides over 50 example simulation cases and their demo video clips to help a user easily understand how to run up a simulation case. Figure 4.2 Screenshot of performance monitor It is continuously supported, maintained, and improved. New functions and network types are continuously added to NCTUns to enhance its function, speed, and capability. For example, WiMAX wireless networks (including PMP and mesh modes) and GEO satellite networks are being under development and will be released in NCTUns 4.0.12 4. THESIS PLAN 4.1 TASKS 4.1.1 Work flow ---------------------------------------------------------------------------------------------------------------------RESEARCH STEPS BASELINES TIME ---------------------------------------------------------------------------------------------------------------------Research Smart Grid – AMI AMI Knowledge Fall-2009 Research WMN Wireless Mesh Network Knowledge Fall-2009 Propose the AMI’s Communication Network architecture: Hybrid WMN (WiMAX, Wi-Fi) Simulation Scenario Spring-2010 SmartGridSim Simulate Integrated WMN in AMI context Conclusions Spring-2010 Simulation based network performance analysis Trade-off between network scalability and network performance Spring-2010 4.1.2 Already Complete • Research Smart Grid, and AMI • Research Wireless Mesh Networks • Research network Simulator Software: NCTUns 6.0 and NS-2 4.1.3. In Progress • Propose the AMI’s communication network model: uses Hybrid WMN architecture. The backhaul network uses WiMAX. The local mesh network uses Wi-Fi. Scenario: The Integrated Wireless Mesh Network as a Communication Network for AMI. The AMI has three components that are Meter Reading Collector, Wireless Mesh (WM) Communication Network, and Wi-Fi (WF) Smart Meter. The Meter Reading Collector component accesses the WF Smart Meter’s reading via the WM Communication Network. Wi-Fi Smart Meter WM Communication Network Meter Reading Collector Basically, the WM Communication Network component provides the data transportation services. The requests and responses from Meter Reading Collector component and Wi-Fi Smart Meter component will be delivered by the using to the transportation services of WM Communication Network component. The WM Communication Network component has three layers of network services like the first three layers of the OSI model: Networking Layer (Internet Protocol: w/ multi-hop routing) Data Link Layer Physical Layer The WM Communication Network is an integrated Wireless Mesh Network (WMN), which uses Wi-Fi and WiMAX technologies. The WM Communication Network has the WiMAX Base Station, the WiMAX/Wi-Fi Gateway, and Wi-Fi Dual Band Mesh Routers. (More detailed information about the functionality of these components can be found in the included documents) The above Design has been implemented in the NCTUns 6.0 Network simulation software. The background picture is a portion of the Colorado Springs city map which has been extracted from the Google map. The distance between the WiMAX base station and the Subscriber Station (WiMAX/Wi-Fi Gateway) is about 600m. The distance between two Wi-Fi Dual Band Routers in the same cluster is 200m. 4.1.4. Future • Develop and implement SmartGridSim application, a network application that will simulate the process of data transmission between the Meter Reading Collector (MRC) and the Smart Meters (SM). As a part of the simulation scenario, the SmartGridSim will run on top of the NCTUns Network simulation, so that we can record and analysis the performance of the communication network. SmartGridSim has two programs. One runs at the Meter Reading Collector, and called Communication Server (CS). Other one runs at the Smart Meter and called Communication Terminal (CT). The traffic pattern is the requests that are issued from the CS to CT. Communication Terminal (Wi-Fi Smart Meter) 2. Response WM Communication Network Communication Server (Meter Reading Collector) 1. Request For example, the usage scenario of the SmartGridSim is as following: • • • 1. Communication Server (CS) is started with the arguments such as “IP address of the target Smart Meter”, “Number of times to read”, “Number of bytes to read” 2. Communication Terminal (CT) is started with arguments such as “Number of bytes to send”. 3. As the end of the running, the output from the programs will be such as the following: Output by the CS: o Total of time spent to collect data from the meters o Total number of data request times (1 times per meter) o Total number of times (successful data collection) o Total number of times (fail data collection) Output by the CT: o Total number of times responded to MRC request Simulate the network scenario with different values of parameters such as number of hops, client nodes (or Smart meters), Wireless link bandwidth, distance between WiMAX base station and subscriber station. Analyze the simulation results: o Evaluate the network performance measures such as throughput, delay o Trade-off between Scalability and Performance Write the thesis report 4.2 DELIVERABLES • The SmartGridSim application that simulates the process of Meter Reading Collection. The application runs on top of the NCTUns 6.0 network simulation for the analyzing of network performance and scalability. • The thesis report documents the technologies of wireless mesh networks, proposed network architecture, network model, simulation scenario, and various simulation parameters such as simulation area, radio models, number of Hops, distances between mesh routers, number of client nodes, MAC protocols, routing protocols. We also discuss about the trade-off between the network scalability and performance, as well as the security of the proposed network model. REFERENCES [1] “Smart Grid”, http://en.wikipedia.org/wiki/Smart_grid [2] “Advanced Metering infrastructure NETL”, AMI White paper final 021108.pdf [3] “Wireless Mesh Network”, http://en.wikipedia.org/wiki/Wireless_mesh_network [4] “AMI & AMR”, http://www.ember.com/applications_amr.html [5] “Smart AMI Network Solutions Enable the Smart Grid”, http://www.electricenergyonline.com/?page=show_article&mag=55&article=395 [6] “Design and Implementation of a network simulation system”, Jae-Won Choi and Kwang-Hui Lee, http://nsl.csie.nctu.edu.tw/NCTUnsReferences/KoreaSimulator.pdf [7] “Network Traffic Simulation”, http://en.wikipedia.org/wiki/Network_traffic_simulation [8] “Home Networking with Zigbee”, Mikhail Galeev http://www.embedded.com/columns/technicalinsights/18902431?printable=true [9] “Tree-based Wireless Mesh Network Architecture: Topology Analysis”, S. Waharte and R. Boutaba, University of Waterloo, School of Computer Science [10] “Wireless Mesh Network”, Department of Computer Science University of California, Davis [11] “Getting Started with ZigBee and IEEE 802.15.4”, Copyright © 2004–2008, Daintree Networks Inc [12] “The Protocol Developer Manual for the NCTUns 6.0”, Network and System Laboratory, Department of Computer Science, National Chiao Tung University, Taiwan 2010. [13] “Understanding Wi-Fi and WiMAX as Metro-Access Solutions”, Intel Corporation, 2004 [14] “Wireless Mesh Networks: Performance Analysis and Enhancements”, Omar VillavicencioCalderon, University of Puerto Rico 2008. [15] “Why WiMAX”, Mark Norris, Adrian Golds, http://www.intercai.co.uk/library/pdf/WhyWiMAX-Paper-v1-2%20_3_.pdf [16] WiMAX community, http://www.wimax.com [17] “How Wi-Fi works”, http://computer.howstuffworks.com/wireless-network1.htm [18] “Chapter 1. Challenges and Issues in Designing Architectures and Protocols for Wireless Mesh Networks”, V. C. Gungor, E. Natalizior, P. Pace, S. Avallone, Book “Wireless Mesh Network: Architecture and Protocols” by Ekram Hossain , Kin Kwong Leung, Springer 2008. [19] “Chapter 2. Architectures and Deployment Strategies for Wireless Mesh Networks”, J. –H. Huang, L. -C. Wang, C. -J. Chang, Book “Wireless Mesh Network: Architecture and Protocols” by Ekram Hossain , Kin Kwong Leung, Springer 2008. [20] The Network Simulator Ns-2, http://www.isi.edu/nsnam/ns/ [21] NCTUns 6.0 Network Simulator and Emulator, http://nsl.csie.nctu.edu.tw/nctuns.html [22] “Throughput Considerations for Wireless Networks”, Wi4Net, http://www.wi4net.com/Brochures/WhitePaper/Throughput%20Considerations%20for%20Wireless%20 Networks%20Feb10.pdf [23] “IEEE 802.11”, http://en.wikipedia.org/wiki/IEEE_802.11 [24] “IEEE 802.16”, http://en.wikipedia.org/wiki/IEEE_802.16 [25] “OSI Model”, http://en.wikipedia.org/wiki/OSI_model