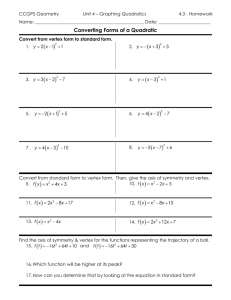
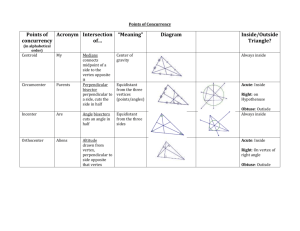
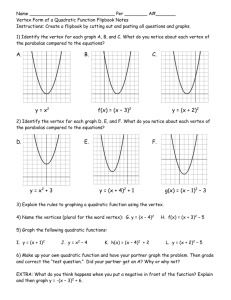
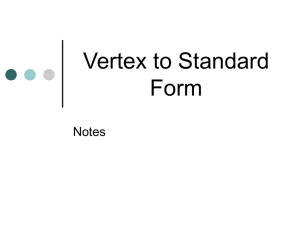
pptx-file
advertisement

Link Reversal Algorithms
Jennifer L. Welch
DISC 2014 Tutorial
What is Link Reversal?
Distributed algorithm design technique
Used in solutions for a variety of problems
routing, leader election, mutual exclusion,
scheduling, resource allocation,…
Model problem as a directed graph and
reverse the direction of links appropriately
Use local knowledge to decide which links
to reverse
1
Outline
1.
2.
3.
4.
5.
6.
Routing in a Graph: Correctness
Routing in a Graph: Complexity
Routing and Leader Election in a
Distributed System
Mutual Exclusion in a Distributed System
Scheduling in a Graph
Resource Allocation in a Distributed
System
2
Section 1
ROUTING IN A GRAPH:
CORRECTNESS
3
Routing
[Gafni & Bertsekas 1981]
Undirected
connected graph
represents
communication
topology of a system
Unique destination
node
D
1
2
3
4
5
6
4
Routing
[Gafni & Bertsekas 1981]
Assign virtual directions to
the graph edges (links) s.t.
if nodes forward messages
over the links, they reach the
destination
Directed version of the
graph (orientation) must
be acyclic
have destination as only sink
Thus every node has path
to destination.
D
1
2
3
4
5
6
5
Mending Routes
What happens if some edges go away?
Might need to change the virtual directions on
some remaining edges (reverse some links)
More generally, starting with an arbitrary
directed graph, each vertex should decide
independently which of its incident links to
reverse
6
Mending Routes Example
D
1
2
3
4
5
6
7
Sinks
A vertex with no outgoing links is a sink.
The property of being a sink can be
detected locally.
A sink can then reverse some incident links
Basis of several algorithms…
8
Full Reversal Routing Algorithm
Input:
directed graph G with destination
vertex D
Let S(G) be set of sinks in G other than D
while S(G) is nonempty do
reverse every link incident on a vertex in S(G)
G now refers to resulting directed graph
9
Full Reversal (FR) Routing Example
D
D
D
1
2
3
1
2
3
1
2
3
4
5
6
4
5
6
4
5
6
D
D
1
2
3
4
5
6
D
1
2
3
1
2
3
4
5
6
4
5
6
10
Why Does FR Terminate?
Suppose it does not.
Let W be vertices that take infinitely many
steps
x
nonempty since it includes D
Consider neighboring vertices w in W, x in X
D
nonempty by assumption
Let X be vertices that take finitely many
steps
X
(stop)
exist since graph is connected
Consider first step by w after last step by x:
link is w g x and stays that way forever.
Then w cannot take any more steps,
contradiction.
w
W
(don’t
stop)
11
Why is FR Correct?
Assume input graph is acyclic.
Acyclicity is preserved at each iteration:
Any new cycle introduced must include a vertex that
just took a step, but such a vertex is now a source
(has no incoming links)
When FR terminates, no vertex, except possibly D, is a
sink.
A DAG must have at least one sink:
if no sink, then a cycle can be constructed
Thus output graph is acyclic and D is the unique sink.
12
Pair Algorithm
easy to argue
Can implement FR by having each vertex v keep
an ordered pair (c,v), the height (or vertex label)
of vertex v
c is an integer counter that can be incremented
v is the id of vertex v
View link between v and u as being directed
from vertex with larger height to vertex with
smaller height (compare pairs lexicographically)
If v is a sink then v sets c to be 1 larger than
maximum counter of all v’s neighbors
13
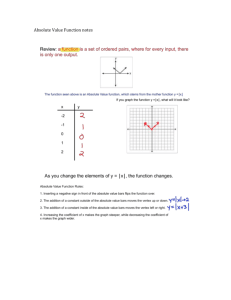
Pair Algorithm Example
(1,0)
0
1
2
(0,1)
(2,1)
(0,2)
3
(2,3)
14
Pair Algorithm Example
(1,0)
0
1
2
(0,1)
(2,1)
(0,2)
(3,2)
3
(2,3)
15
Pair Algorithm Example
(1,0)
0
1
2
(0,1)
(2,1)
(0,2)
(3,2)
3
(2,3)
16
Partial Reversal Routing
Algorithm
Try to avoid repeated reversals of the
same link.
Vertices keep track of which incident links
have been reversed recently.
Link (u,v) is reversed by v iff the link has
not been reversed by u since the last
iteration in which v took a step.
17
Partial Reversal (PR) Routing
Example
D
D
D
1
2
3
1
2
3
1
2
3
4
5
6
4
5
6
4
5
6
D
D
1
2
3
4
5
6
D
1
2
3
1
2
3
4
5
6
4
5
6
18
Why is PR Correct?
Termination can be
proved similarly as for
FR: difference is that it
might take two steps by
w after last step by x
until link is w g x .
X
(stop)
D
x
w
W
(don’t
stop)
19
Why is PR Correct?
Preservation of acyclicity is more involved,
deferred to later.
Alternate geometric proof due to Radeva
and
Lynch 2011
20
Triple Algorithm
Can implement PR by having each vertex v keep an
ordered triple (a,b,v), the height (or vertex label) of
vertex v
not so easy to argue
a and b are integer counters
v is the id of vertex v
View link between v and u as being directed from vertex
with larger height to vertex with smaller height
(compare triples lexicographically)
If v is a sink then v
sets a to be 1 greater than smallest a of all its neighbors
sets b to be 1 less than smallest b of all its neighbors with new
value of a (if none, then leave b alone)
21
Triple Algorithm Example
(0,1,0)
0
1
(0,0,1)
(1,0,1)
2
(0,0,2)
3
(0,2,3)
22
Triple Algorithm Example
(0,1,0)
0
1
(0,0,1)
(1,0,1)
2
(0,0,2)
(1,-1,2)
3
(0,2,3)
23
Triple Algorithm Example
(0,1,0)
0
1
(0,0,1)
(1,0,1)
2
(0,0,2)
(1,-1,2)
3
(0,2,3)
24
General Vertex Label Algorithm
Generalization of Pair and Triple algorithms
Assign a label to each vertex s.t.
labels are from a totally ordered, countably infinite
set
new label for a sink depends only on old labels for the
sink and its neighbors
sequence of labels taken on by a vertex increases
without bound
25
Correctness of General Vertex
Label Algorithm
Termination: Similar to the
arguments for LR and PR.
Difference is that it might take
several steps by w after last
step by x until link is w g x.
However it will happen
because w’s label increases
without bound and eventually
is larger than x’s final label.
X
(stop)
D
x
w
W
(don’t
stop)
26
Correctness of General Vertex
Label Algorithm
Acyclicity is preserved because labels are
from a totally ordered set
27
Relationship Between
Algorithms
FR
PR
Pair Algorithm
Triple Algorithm
General Vertex Label Algorithm
28
Binary Link Labels Routing
[Charron-Bost et al. 2013]
Alternate way to implement and generalize FR and PR
Instead of unbounded vertex labels, apply binary link
labels to input DAG
link directions are independent of labels (in contrast to
algorithms using vertex labels)
Algorithm for a sink:
if at least one incident link is labeled 0, then reverse all
incident links labeled 0 and flip labels on all incident links
if no incident link is labeled 0, then reverse all incident links
but change no labels
29
Binary Link Labels Example
0
1
1
0
1
2
0
3
30
Binary Link Labels Example
0
1
1
0
1
2
0
3
31
Binary Link Labels Example
0
1
1
0
0
2
1
3
32
Why is BLL Correct?
Termination can be
proved very similarly to
termination for PR.
Takes 1 or 2 steps until link
X
(stop)
D
x
is w g x.
w
W
(don’t
stop)
33
Why is BLL Correct?
What about acyclicity preservation?
Depends on initial labeling:
0
3
0
1
1
0
2
3
1
1
1
2
0
0
0
0
34
Conditions on Initial Labeling
All labels are the same
all 1’s => Full Reversal
all 0’s => Partial Reversal
Every vertex has all incoming links labeled
the same (“uniform” labeling)
Both of the above are special cases of a
more general condition that is necessary
and sufficient for preserving acyclicity
35
Relationship Between
Algorithms Revisited
Binary Link Label Algorithm
FR
PR
Pair Algorithm
Triple Algorithm
General Vertex Label Algorithm
36
Section 2
ROUTING IN A GRAPH:
COMPLEXITY
37
What About Complexity?
Busch et al. (2003,2005) initiated study of
the performance of link reversal routing
Work complexity of a vertex:
number of steps taken by the
vertex
Global work complexity: sum
of work complexity of all
vertices
38
Worst-Case Work Complexity
Bounds [Busch et al.]
bad vertex:
has no (directed) path to dest.
Pair algorithm (Full Reversal):
for every input, global work complexity is
O(n2), where n is number of initial bad vertices
for every n, there exists an input with n bad
vertices with global work complexity Ω(n2)
Triple algorithm (~Partial Reversal):
same
as Pair algorithm (if appropriately
initialized)
39
Exact Work Complexity Bounds
A more fine-grained question:
Given any
input graph and any vertex in that graph,
exactly how many steps does that vertex
take?
Busch et al. answered this question for FR.
Charron-Bost et al. answered this question
for BLL (as long as labeling satisfies
Acyclicity Condition): includes FR and PR.
40
Definitions
Let C = <v1, v2, …, vk> be a chain in the labeled input
DAG (series of vertices s.t. either (vi,vi+1) or (vi+1,vi) is
a link).
r: number of links that are labeled 1 and rightway
((vi,vi+1) is a link, i.e., directed away from D)
s: number of occurrences of vertices s.t. the two
adjacent links are incoming and labeled 0
Res: 1 if last link in X is labeled 0 and rightway, else 0
41
Example of Definitions
0
1
1
2
0
1
3
8
0
D
4
1
7
1
6
0
1
5
For chain <D,7,6,5>: r = 1, s = 0, Res = 1
For chain <D,1,2,3,4,5>: r = 2, s = 1, Res = 0
42
Grouping the Vertices
D is set of all vertices with an incoming link labeled 0
and either an incoming link labeled 1 or an outgoing
link
S is all other vertices (all incoming links, if any, labeled 1
or a sink with all links labeled 0)
0
1
group S
0
0
1
1
0
group D
1
0
1
0
43
BLL Work Complexity
Theorem: The work complexity of vertex v is
min{r(C) + s(C) + Res(C) : C is a chain from D to v}
if v is in S
min{2r(C) + 2s(C) + Res(C) : C is a chain from D to v}
if v is in D
Proof is by showing how different combinations of r,
s, and Res are either invariant or increase by certain
amounts throughout execution until a chain
becomes a path from v to D.
44
Work Complexity for FR
Recall: The work complexity of vertex v is
min{r(C) + s(C) + Res(C) : C is a chain from D to v} if v is in S
min{2r(C) + 2s(C) + Res(C) : C is a chain from D to v} if v is in D
For FR (all labels are 1), all vertices are in S, s(C) = 0, and
Res(C) = 0. Thus formula becomes
minimum, over all chains from D to v, of number of links in the
chain that are directed away from D
Worst-case graph for global work complexity:
D12…n
vertex i has work complexity i
global work complexity then is Θ(n2)
45
Work Complexity for PR
For PR (all labels are 0 initially), work complexity
of vertex v is
min, over all D-to-v chains, of s + Res if v is a sink or a
source initially
min, over all D-to-v chains, of 2s + Res if v is neither a
sink nor a source initially
Worst-case graph for global work complexity:
D123…n
work complexity of vertex i is Θ(i)
global work complexity is Θ(n2)
46
Comparing FR and PR
Looking at worst-case global work complexity shows no
difference – both are quadratic in number of bad vertices
Can use game theory to show some meaningful
differences (Charron-Bost et al. 2013)
Consider class of uniform labelings: for each vertex, all
incoming links have the same binary label
A vertex’s choice of initial label for its incoming links can
be viewed as its strategy in a game
Should v play
0
0
v
0
or
1
1
v
?
1
47
Comparing FR and PR with
Game Theory
Compare FR and PR among all uniform labelings
(every vertex initially has all its incoming links
with same label)
Global work complexity of FR can be larger than
optimal (w.r.t. all uniform labelings) by a factor
of Θ(n)
Global work complexity of PR is never more than
twice the optimal
Thus PR is a safer bet than than FR w.r.t. global
work complexity
48
Time Complexity
Time complexity is number of iterations in greedy
execution (all sinks take step in each iteration)
Busch et al. (2003, 2005) observed that time
complexity cannot exceed global work
complexity
Thus O(n2) iterations for both pair (FR) and triple (~PR)
algorithms
Busch et al. also showed graphs on which pair
(FR) and triple (~PR) algorithms require Ω(n2)
iterations
49
Time Complexity
Charron-Bost et al. (2011) derived an exact formula
for the last iteration in which any vertex takes a
step in any graph for BLL…
50
FR Time Complexity:
Recurrence for Work
Let Wi(t) be number of steps vertex i has taken by iteration t
Identify a recurrence relation for Wi(t) based on understanding how
vertex i and its neighbors take turns being sinks:
0
o
0
o
0
o
0
o
0
o
1
o
1
o
1
1
1
1
1
1
2
o
2
1
2
1
2
2
2
2
3
o
3
o
3
1
3
1
3
2
t=0
Wi(t+1) = min{Wj(t)+1,Wk(t) :
j is initially incoming to i,
t = 2 k is initially outgoing from i}
t=1
t=3
t=4
51
Linear Recurrence
Wi(t+1) = min{Wj(t)+1,Wk(t) :
j is initially incoming to i,
k is initially outgoing from i}
This recurrence is linear in the min-plus algebra
Represent system of equations as a matrix A
W(t+1) = A W(t) = At O (O is all-zero vector)
Classical duality arguments give us an expression
for the time vector using max-plus algebra
Formula for time complexity of general BLL is
rather technical
52
FR Time Complexity Formula
Theorem: For every bad vertex v, termination time
of v is
1 + max{len(C): C is chain ending at v with r = σv – 1}
where σv is the work complexity of v
Worst-case graph for global time complexity:
n
D
1
2
n-1
n/2
vertex n/2 has work complexity n/2;
consider chain that goes around the loop
counter-clockwise n/2-1 times starting and
ending at n/2: has r = n/2-1 and length Θ(n2)
n/2+3
n/2+1
n/2+2
53
BLL Time Complexity
What about other link labelings?
Transform to FR!
In more detail: for every labeled input graph G
(satisfying the Acyclicity Condition), construct
another graph T(G) s.t.
for every execution of BLL on G, there is a
“corresponding” execution of FR on T(G)
time complexities of relevant vertices in the
corresponding executions are the same
54
Idea of Transformation
If a vertex v is initially in the category D (a sink with some
links labeled 0 and some labeled 1, or not a sink with an
incoming link labeled 0), then its incident links are
partitioned into two sets:
all links in one set reverse at odd-numbered steps by v
all links in the other set reverse at even-numbered steps by v
Transformation replaces each vertex in D with two
vertices, one corresponding to odd steps by v and the
other to even steps, and inserts appropriate links
Vertices initially in category S reverse all their links at
every step they take, which is already FR-like behavior
55
Example of LR->FR
Transformation
0
1
1
0
LR input
0
FR input
Yellow vertex in graph on left is in D, so it is replaced
with two vertices in graph on right
56
PR Time Complexity
Theorem: For every vertex v with no path to D
originally, termination time of v is
1 + max{len(C): C is a chain ending at v with s + Res = σv – 1}
if v is a sink or a source initially
1 + max{len(C): C is a chain ending at v with 2s + Res = σv – 1}
otherwise
Worst-case graph for global time complexity:
D 1 2 3 … n/2 n/2+1 … n
Vertex n/2 has work complexity n/2. Consider chain that starts at n/2, ends
at n/2, and goes back and forth between n/2 and n making (n-2)/4 round
trips. 2s+Res for this chain is n/2-1, and length is Θ(n2).
57
FR vs. PR Again
On chain on previous slide, PR has
quadratic time complexity.
But FR on that chain has linear time
complexity
in fact, FR has linear time complexity on any
tree
On chain on previous slide, PR has
(slightly) better global work complexity
than FR.
58
Section 3
ROUTING AND LEADER ELECTION
IN A DISTRIBUTED SYSTEM
59
From Graph to Distributed
System
To adapt previous ideas to a distributed system:
Node (processor) is a vertex
Communication channel is an edge (link)
Issues to be overcome:
Neighboring nodes need to communicate to agree on
which way the link between them should be directed:
delays and losses
Topology can change due to movement and failures;
might not always be connected
60
Routing in a Dynamic System
In any execution that experiences a finite
number of topology changes, after the last
topology change:
every node in same connected component as
D (destination) should have a path to D
every node not in the same component as D
should stop trying to find a route to D or
forward a message to D
61
What’s Wrong with FR?
3
1
3
2
1
2
D
D
3
3
1
2
D
1
2
D
62
TORA
[Park & Corson 1997]
Modify the generalized algorithm of Gafni & Bertsekas
using increasing vertex labels
Vertex labels, or heights, are 5-tuples
one entry is current time: Temporally Ordered Routing
Algorithm
Every node in same connected component as D
eventually has a path to D in the directed version of the
communication graph induced by the heights
Clever use of additional entries in the heights allows
node to tell when they are partitioned from D and should
stop participating
63
Heights in TORA
reference level
delta
[ t , oid , r , d , i ]
time this
ref. level
was started
id of node
originating
this ref.
level
reflection
bit
orders
nodes with
same ref.
level
id of node,
breaks ties
64
TORA Overview
Route Creation:
use standard spanning
tree construction ideas to set ref levels to
(0,0,0) and deltas to distances from D
Route Maintenance and Partition
Detection: see next slide
Route Erasure: When partition is
detected, flood “clear” messages
throughout component
65
TORA Route Maintenance
If node i loses last outgoing link:
due to a link failure (Case Generate):
set ref level to (current time, i, 0), a full reversal
due to a height change and
nbrs don’t have same ref level (Case Propagate):
nbrs have same ref level with r = 0 (Case Reflect):
adopt max ref level and set d to effect a partial reversal
adopt new ref level, set r to 1, set d to 0 (full reversal)
nbrs have same ref level with r = 1 and oid = i (Case Detect):
Partition! Start process of erasing routes.
66
TORA Example – Partition
D
1
5
2
3
D
4
1
2
Generate
5
3
4
Propagate
Propagate
Reflect
D
5
Reflect
1
D
5
D
2
3
4
5
Propagate
1
2
3
4
1
2
3
4
Propagate
Detect
67
TORA Discussion
Works best with perfectly synchronized clocks
How to prove correctness?
Gafni & Bertsekas result does not directly apply
because of asynchronous delay in updating neighbors
about new heights
Other issues remain: partition detection, route
creation, route erasure
Can be adapted to solve leader election: when
partition is detected, elect a new leader! (Cf.
Ingram et al. 2013)
68
Section 4
MUTUAL EXCLUSION IN A
DISTRIBUTED SYSTEM
69
Link Reversal for Mutual
Exclusion [Snepscheut 1987]
Goal: no-lockout mutual exclusion in a message-passing
system with a tree communication topology
Solution: Pass around a unique “token” message.
70
Link Reversal for Mutual
Exclusion [Snepscheut 1987]
impose logical directions on communication channels s.t.
token holder is unique sink
when a node has the token, it can enter critical section
When node needs the token, it sends “request” message
on its unique outgoing link – toward token holder
When a node receives a request, it remembers it in a FIFO
queue and forwards it toward the token-holder (if not
already waiting)
when token holder responds to a request, it forwards the
token to the neighbor at the head of the queue, and
reverses direction of that link
71
From a Tree to a DAG
For a general communication topology, the
previous algorithm can be run on a spanning tree
overlay of the graph.
However, this does not take advantage of the
redundancy offered by additional links.
Instead, direct all links in the graph:
request message can be forwarded on any outgoing
link
when a node receives the token, all its outgoing links
are reversed, to make it a sink
72
From a Tree to a DAG
73
Related Work
Naimi and Trehel 1987:
analyzed expected
message complexity
Raymond 1989: gave fault-tolerant
extension
Dhamdhere and Kulkarni 1994: considered
dynamic topogies
Walter et al. 2001: handled dynamic
topologies by adding vertex labels
74
Section 5
SCHEDULING IN A GRAPH
75
Scheduling in a Graph
[Barbosa & Gafni 1989]
What happens when the Full Reversal routing
algorithm is executed without a destination?
I.e., every vertex in the graph does a reversal when it
is a sink
Call this algorithm FRND (FR with No
Destination).
When a vertex is a sink, it is said to be scheduled:
can take some action with the guarantee that
none of its neighbors are scheduled at the same
time.
76
Behavior of FRND
Claim: FRND maintains acyclicity.
Same proof as for FR.
Claim: Every vertex is a sink infinitely often.
By Claim 1, at each iteration there is at least one sink,
so FRND never terminates.
If some vertices take finitely many steps and some
take infinitely many, then use same argument as for
showing FR terminates to get a contradiction.
Thus every vertex is scheduled infinitely
often.
77
FRND Example
0
1
2
3
4
5
0
1
2
3
4
5
0
1
2
3
4
5
0
1
2
3
4
5
0
1
2
3
4
5
0
1
2
3
4
5
78
Behavior of FRND
Claim:
In the greedy execution of FRND
from an initial DAG, eventually the pattern
of sinks becomes periodic.
Let G1, G2,… be the sequence of
graph states
in the execution. Since finite number of
vertices, Gi = Gj for some i and j.
Thus Gi+1 = Gj+1, etc.
Note: every vertex appears at least once in
every period.
79
Q&A about FRND
How long until the execution becomes periodic?
At most polynomial number of iterations [Malka &
Rajsbaum 1991]
How long is the period?
At least 2 iterations, since neighbors cannot be sinks
simultaneously
Can be as bad as exponential [Malka et al. 1993]
How “fair” is the period?
every vertex takes same number of steps…
80
Period is Fair
Claim 1: Difference in total number of steps
taken by u and v at any iteration is at most the
distance between them.
Proof is by induction on the distance.
Claim 2: Every vertex takes same number of
steps in the period.
Suppose u appears a times and v appears b times with
b > a. After k-th execution of the period, u has taken
ka steps and v has taken kb steps. Eventually kb – ka
exceeds the distance between u and v, contradicting
Claim 1.
81
Multiplicity and Concurrency
Multiplicity of the period is the number of
times that each vertex takes a step in the
period.
Concurrency is ratio of multiplicity m to
the period length p, i.e., m/p.
Concurrency is fraction of iterations during
which any given vertex takes steps.
at most 1/2
at least 1/n
82
Multiplicity and Concurrency
Multiplicity of the period is the number of
times that each vertex takes a step in the
period.
Concurrency is ratio of multiplicity m to
the period length p, i.e., m/p.
Concurrency is fraction of iterations during
which any given vertex takes steps.
at most 1/2
at least 1/n
83
Concurrency Example
Period length is 5
multiplicity is 2
concurrency is 2/5
84
Exact Expression for Concurrency
Claim 1:
For any initial orientation of a
tree, the greedy execution of FRND
reaches a periodic orientation with length
2 and multiplicity 1, so concurrency = 1/2.
Claim 2: For any periodic orientation G of a
non-tree graph, the concurrency is equal
to the minimum, over all (simple) circuits k
in G, of the fraction of links in k that are
right-way.
85
Choosing a Good Initial
Orientation
For trees, the initial orientation is unimportant:
they all lead to a period with concurrency 1/2
For non-trees, the initial orientation can make a
big difference to the concurrency:
consider a ring of n vertices, where n is even
if initially there is just 1 sink, there will never be more
than 1 sink in any orientation: concurrency is 1/n
if initially every other vertex is a sink, vertices keep
alternating: concurrency is 1/2
Unfortunately, determining the best orientation
is NP-complete!
86
Section 6
RESOURCE ALLOCATION IN A
DISTRIBUTED SYSTEM
87
Resource Allocation in a
Distributed System [Chandy & Misra 1984]
Dining philosophers (or resource allocation)
problem is a generalization of the mutual
exclusion problem:
conflict graph: vertices correspond to the nodes,
edge between I and j means I and j compete for
exclusive access to a resource
Ensure exclusion: no two neighbors in the conflict
graph are in their critical sections simultaneously
Ensure fairness: every node requesting access to its
critical section eventually is granted access
88
First Solution
Use FRND on the conflict graph: when a vertex
is a sink, it can enter its critical section
Every vertex is a sink infinitely often
no two neighbors are sinks simultaneously
Issues:
How to adapt FRND to asynchronous message
passing?
Why bother a node that is not interested in entering
its critical section?
89
Chandy & Misra’s Solution
Key data structure is precedence graph, directed version
of conflict graph
Precedence graph is represented in a distributed fashion
by having each node keep a variable for each neighbor
indicating who yields to whom
variables are initialized so that precedence graph is acyclic
Each pair of neighbors i and j share a token to ensure
exclusion
if i doesn’t have token when it wants to enter C.S. it sends
request to j
j sends back the token immediately if j is in its remainder section
or if it is in its trying section and i has precedence over j,
otherwise j defers the request from i
90
Chandy & Misra’s Solution
Thus precedence graph is used to arbitrate between
contending neighbors, but otherwise is ignored.
Once i has all its tokens, it enters the C.S.
When i leaves the C.S., it satisfies all deferred requests
and does a full reversal in the precedence graph
91
Correctness Ideas
Management of tokens ensures exclusion.
By starting with an acyclic conflict graph
and only modifying it with full reversal, the
precedence graph is always acyclic:
no deadlock can be caused by a cycle of
nodes
waiting on each other
92
Conclusion
Other applications of link reversal include:
distributed queueing
k-mutual exclusion
publish/subscribe
simulated annealing
graph coloring
neural networks
Appeal of the approach is using local
knowledge to solve global problems
93
Open Questions
Explore consequences of work and time
bounds for BLL on other applications of
link reversal
Discover effects on bounds of distributed
system realities:
message delays
failures
X
ongoing topology changes
94
Acknowledgements
Welch and Walter, “Link Reversal
Algorithms,” Synthesis Lectures on
Distributed Computing Theory #8,
Morgan & Claypool Publishers, 2011.
Editor Nancy Lynch
My collaborators: Bernadette Charron-Bost, Matthias
Fuegger, Antoine Gaillard, Rebecca Ingram, Navneet
Malpani, Mira Radeva, Patrick Shields, Nitin Vaidya, Saira
Viqar, Jennifer Walter, Josef Widder
Funding: National Science Foundation, Texas Higher
Education Coordinating Board
95
References
Barbosa and Gafni, “Concurrency in Heavily Loaded Systems,” ACM TOPLAS
1989.
Busch, Surapaneni and Tirthapura, “Analysis of Link Reversal Routing Algorithms
for Mobile Ad Hoc Networks,” SPAA 2003.
Busch and Tirthapura, “Analysis of Link Reversal Routing Algorithms,” SIAM JOC
2005.
Chandy and Misra, “The Drinking Philosophers Problem,” ACM TOPLAS 1984.
Charron-Bost, Fuegger, Welch and Widder, “Full Reversal Routing as a Linear
Dynamical System,” SIROCCO 2011.
Charron-Bost, Fuegger, Welch and Widder, “Partial is Full,” SIROCCO 2011.
Charron-Bost, Gaillard, Welch and Widder, “Link Reversal Routing with Binary
Link Labels: Work Complexity,” SIAM JOC 2013.
Dhamdere and Kulkarni, “A Token-Based k-Resilient Mutual Exclusion Algorithm
for Distributed Systems,” IPL 1994.
Gafni and Bertsekas, “Distributed Algorithms for Generating Loop-Free Routes in
Networks with Frequently Changing Topology,” IEEE Trans. Comm. 1981.
96
References
Ingram, Radeva, Shields, Viqar, Walter and Welch, “A Leader Election Algorithm
for Dynamic Networks with Causal Clocks,” Distributed Computing 2013.
Malka, Moran and Zaks, “A Lower Bound on the Period Length of a Distributed
Scheduled,” Algorithmica 1993.
Malka and Rajsbaum, “Analysis of Distributed Algorithms Based on Recurrence
Relations”, WDAG 1991.
Naimi and Trehel, “An Improvement of the log n Distributed Algorithm for
Mutual Exclusion,” ICDCS 1987.
Park and Corson, “A Highly Adaptive Distributed Routing Algorithm for Mobile
Wireless Networks,” INFOCOM 1997.
Radeva and Lynch, “Partial Reversal Acyclicity,” PODC 2011.
Raymond, “A Tree-Based Algorithm for Distributed Mutual Exclusion,” ACM
TOCS 1989.
van de Snepscheut, “Fair Mutual Exclusion on a Graph of Processes,” Distributed
Computing 1987.
Walter, Welch and Vaidya, “A Mutual Exclusion Algorithm for Ad Hoc Mobile
97
Networks,” Wireless Networks, 2001.