Unit 07 - Assignment Checklist
advertisement

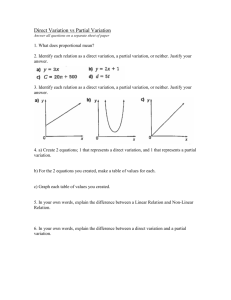
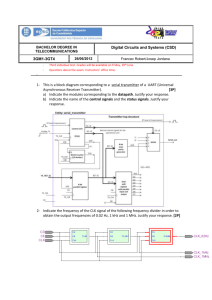
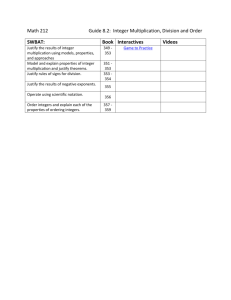
Enderoth School OCR Cambridge TEC (Certificate/Diploma) in IT Unit 07 - Computer Network Systems Student Name: Daniel McGinley Grade Awarded by: STR Date Awarded: __________ Grade: PASS/MERIT/DISTINCTION Unit 07 - Assignment Checklist - 11-12-2013 TASKS & LEVEL ACTIVITIES Feedback LO1 - Know types of network systems and protocols Task 1 (P1.1) Task 2 (M1.1) Task 3 (P1.2) Task 4 (P1.3) Task 5 (M1.2) Task 6 (P1.4) Task 7 (M1.3) Task 8 (P1.5) Task 9 (M1.4) Task 10 (P1.6) Task 11 (M1.5) Task 12 (P1.7) Task 13 (P1.8) Task 14 (P1.9) Describe the 3 different types of networks Describe how information is transferred around the system in terms of information flow Suggest and justify a network system type and workstation purchase that will suit the needs of your client and describe the benefits and drawbacks of this network Describe with examples WAN information transfer technologies. ATM X.25 and Frame Relay MPLS Describe how the 5 different network topologies work and how they transfer information Star Ring Bus Mesh Tree Suggest and justify a network topology for your client and describe the benefits and drawbacks of this topology Describe how the 2 different network access methods work and how they transfer information CSMA Token Passing Suggest and justify the benefits and drawbacks of the internal network access methods for the client and users Describe how the 2 different network access methods work and how they transfer information (HARDWARE) TCP/IP Peer to Peer Suggest and justify the benefits and drawbacks of the external network access methods for the client and users Describe what a Client Server network is and the technical hardware necessary to provide internal and external access Suggest and justify the benefits and drawbacks of operating a Client Server network for the client and users Describe the technologies behind the Network Layer Protocols • Discuss the advantages and disadvantages of each Protocol within a school environment TCP/IP Appletalk UDP 802 Standards FDDI Describe what the following network connections are - Bluetooth, Wi-Fi and 3G/4G Outline the factors affecting range and speed of wireless connections within a school environment WIFI Bluetooth 3g and 4g Describe what the functions are for the following application layers - DNS, DHCP, HTTP, FTP and SMTP Outline the practical applications used within a school environment DNS DHCP HTTP FTP SMTP LO2 - Understand the key components used in networking Task 1 (P2.1) Task 2 (M1.6) Task 3 (P2.2) Task 4 (M1.7) Task 5 (M1.8) Task 6 (P2.3) Task 7 (M1.9) Task 8 (P2.4) Task 9 (M1.10) Task 10 (P2.5) Page 1 of 3 Describe the practicalities of Base and Thin client workstations. • Outline the benefits and drawbacks of the different forms of networked workstations Suggest and justify a network setup for your client and focus on the benefits and drawbacks Describe the functions and uses of the different servers Print Server Mail Server File Server Proxy Server Web Server Suggest and justify the network setup of server(s) for your client and focus on the benefits and drawbacks Suggest and justify the network setup of hardware component(s) for your client and focus on the benefits and drawbacks Network Connection Motherboard Hard Drives Memory Processor Power Supply Describe the purposes, features and functions of a NIC, Router, Switch and Wireless Access Point Network Interface Cards – Router Switch Wireless Access Point - WAP NIC Suggest and justify the network setup of interconnection device(s) for your client and focus on the benefits and drawbacks Describe what a Leased and Dedicated Line connection is Suggest and justify the type of line connection for your client and focus on the benefits and drawbacks Describe the different kinds of Connections and Cabling within a Networking Environment © Enderoth • • • Task 11 (M1.11) Task 12 (M1.12) Coaxial Category 5e and 6 Fibre Optic BNC Connector Task 14 (P2.6) Task 15 (M1.14) Task 16 (P2.7) Task 17 (M1.15) Twisted Pair STP UPT RJ45 Connector Wireless Mobile Technology Suggest and justify the type(s) of Connections and Cabling methods your client would require within their network setup and focus on the benefits and drawbacks Suggest and justify the type of Network Operating System (Microsoft Server versus Novell Netware) your client would require within their network setup and focus on the benefits and drawbacks Windows NT Server Task 13 (M1.13) • • • Novell NetWare Mac OSX Linux Suggest and justify the alternative Commercial Systems your client would require within their network setup and focus on the benefits and drawbacks Describe the different forms of Software used for a Network Operating System File Sharing Security Directory Network Support Suggest and justify the type(s) of Software your client would require within their network setup and focus on the benefits and drawbacks Describe the importance of the different forms of protections used within a Networking Environment Suggest and justify the type(s) of protection measures your client would require within their network setup and focus on the benefits and drawbacks LO3 - Know the services provided by network systems Task 1 (P5.1) Describe the facility and importance of Directory Services within a network environment. Account Management Authentication Management Active Directory DNS Task 2 (M3.1) Describe the need for implementation of these Directory Services within a Primary School System in terms of security, Data Protection and ease of student use. Task 3 (D2.1) Within your PowerPoint, evaluate the Directory Services need your business needs to take to secure their Networks. Task 4 (P5.2) Describe the Range of Communication Services available to companies and the potential benefits of monitoring and controlling access to these. Task 5 (M3.2) Describe the need for monitoring Communication Services within a Primary School System in terms of security, Data Protection and filtered student use. Task 6 (D2.2) Within your PowerPoint, evaluate the procedures your organisations should take to secure their Communication Systems. Account Management Account Management Task 7 (P5.3) Task 8 (M3.3) Task 9 (D2.3) Task 10 (P5.4) Task 11 (M3.4) Task 12 (D2.4) Task 13 (P5.5) Task 14 (M3.5) Task 15 (P5.6) Task 16 (M3.6) Task 17 (D2.5) Task 18 (P5.7) Task 19 (M3.7) Task 20 (P5.8) Task 21 (M3.8) Task 22 (D2.6) Email Remote Desktop Email Remote Desktop Email Remote Desktop Authentication Management Authentication Management IRC IRC IRC Active Directory Active Directory Discussion Boards Social Networking Discussion Boards Social Networking Discussion Boards Social Networking DNS DNS Remote Access File Transfer Remote Access File Transfer Email File Transfer Describe the Process and Benefits to companies of configuring File Sharing management services. Describe the circumstances in which File Sharing management takes place with a school environment. Within your PowerPoint, evaluate the procedures your organisations should take to secure their student information if instigating file sharing rights. Describe the need for Databases, Web and Proxy Services on a system to ensure consistent functionality. Describe the circumstances in which Application Management takes place with a school environment. Within your PowerPoint, evaluate the procedures your organisations should take to secure their Application Software if instigating student management rights. Describe the need for sharing devices on a system to ensure consistent availability. Describe the circumstances in which Device Sharing Management takes place with a school environment. Describe the need for Storage Space allocation and management on a system to ensure consistent functionality. Describe the circumstances in which Storage Management takes place with a school environment. Within your PowerPoint, evaluate the Storage Space needs of your organisations and the procedures that should be taken to allocate required student and department space. Describe the facility of VOIP and Mobile Working within a Networking environment. Describe the circumstances in which VOIP and Mobile Working takes place with a school environment. Describe the Policies of Authentication and the benefits of setting these access rights. Describe the circumstances in which Authentification Rights takes place with a school environment. Within your Client’s system, describe the different Access and Authentification Rights between Students and Staff and discuss the need for this security measure. LO4 - Be able to make networked systems secure Page 2 of 3 © Enderoth Task 01 (P6.1) State why Passwords are essential to Network systems with examples of the risks and give examples of strong and weak passwords. Task 02 (P6.2) State the policy of Access Control Lists and Permission Rights on files, folders and programs and state the need to secure these right within a school environment. Task 03 (P6.3) Describe the importance and method of restoring files on a network and give examples related to your Client of the need to generate a Policy of Recovery. Task 04 (P6.4) Describe Encryption and Encryption Keys and state how secure this method might be in securing the data within a school environment. Task 05 (P6.5) Describe the different technologies that exist in biometrics and analyse their relative value within your Clients Network. Task 06 (P6.6) State the different methods of physical security available and for your client, state the possible benefits and implications of these security measures. Task 07 (P6.7) Describe the two different kinds of firewalls available for Networks and explain the need for your Client to maintain this protection. Task 08 (P6.8) Describe with examples Spyware, Adware and Malware and describe how your company can minimise the threat of each of these. Task 09 (P6.9) Describe the different types of risks that exist to information storage and describe to your client and the level of risk they pose. Task 10 (P6.10) Describe what an Antivirus program is and in detail describe the precautions your client should take to protect their network. Task 11 (P6.11) State and explain the different Software methods of detecting an intruder and state the need for your Client to manage the network needs through software and vigilance. Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Service Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Loss of Business Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Increased Costs Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality Confidentiality System Integrity System Integrity System Integrity System Integrity System Integrity System Integrity System Integrity System Integrity System Integrity System Integrity System Integrity Evaluate the current levels of security the school will need to prepare for in order to maintain a degree of security. Task 12 (D2.7) Task 13 (P6.12) Task 14 (P6.12) Task 15 (P6.12) Task 16 (P6.12) Task 17 (P6.12) Page 3 of 3 Passwords Authorisation Levels of Risk Security Issues Backing up and restoring Intrusion Detection Systems Encryption Biometrics Antivirus Software Physical Security Create a guide that demonstrates to a new user with network rights the stages of installing and configuring a Virus Checker and Firewall protections. Create a guide that demonstrates to a new user with network rights the stages of configuring a new User Account. Within this guide that demonstrates to a new user with network rights the stages of configuring the TCP/IP setting to connect to an existing network. Within this guide that demonstrates to a new user with network rights the stages of configuring Pop3 and SMTP Mail services. Within this guide that demonstrates to a new user with network rights the stages of configuring a Network Printer. © Enderoth