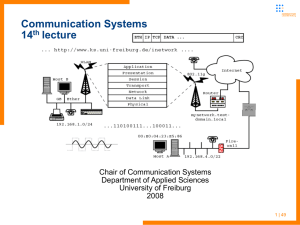
Network Access Control
advertisement

A Secure Network for All Team Excel Requirements Business • Add visitor, customer, and competitor access • Use non-company laptops onto corporate network for internet and internal application use • Visitor access to internet, VPN • Wireless access Security • • • • Protect corporate IP Principle of least privilege Patch and anti-virus required Wireless access to internal network prohibited Challenge = How? Access required Pros Risks Employees •Physical •Internet •Intranet •Corporate Applications •Standard builds •Regular patches •Updated Anti-Virus •Physical access to most areas Visitors (frequent, short meetings) •Physical •Internet •Wireless access •External access only •Escort required •Unfiltered access to internet •No login •Wireless security Contractors (Few days to 1 year) •Physical •Internet •Corporate Applications •NDA required •Easy to control application access •Login created for access •Access typically same as employee Customers and/or Competitors (Regularly on-site for specific projects) •Physical •Internet •Some internal applications •Non-standard builds •Limited ability to control •Login created for access •Considerable access to building •Intentional or unintentional disclosure Risks • Physical access to multiple networks • Protection of Intellectual Property • Introduction of Malware • Unintentional access to corporate data and applications • Blocking of valid users • Difficult for support staff to understand who can access what Are you at risk? Anyone with a requirement to protect corporate intellectual property or privacy data: • Government • Healthcare • Research • Engineering • Many more Technology Pro Con Electronic badge •Limits access to buildings and certain rooms •Auditing is available •Once in a building, access is open to most areas •Physical access to network available in empty offices, etc LDAP login •Limits access to domain •Occurs after network access is granted •DHCP address granted to anyone Active Directory groups •Allows or restricts access to specific applications •Easy to maintain •Auditing available •Can be easy to get added to a group Separate networks •Limits access to subnet and specific IP’s and ports •May require additional authentication •Requires additional infrastructure •Firewall rules can be complex Network Access Control •Prevents access to network without authentication •Policy-based access can limit access anywhere at a site •Cost •Complex support •Blocking valid users Encryption •Prevents reading data even if disclosed •Requires infrastructure •Support issues Summary • How do you prevent disclosure to those with physical access? • How do you grant access to some while limiting access to others? • How can you do it without re-designing your network? • How can you meet the business requirements without giving away the corporate secrets? Solution: Week 10 Questions?