PHPC Presentation
advertisement

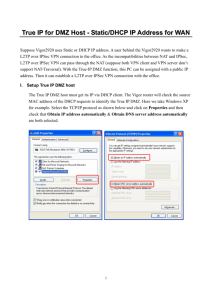
A Cold Fusion Programmers Guide to Secure Networking By: Jeremy Brodie, Sr. Developer 12500 Fair Lakes Circle, Suite 150 Farifax, VA 703.815.2500 www.edgewater.com Overview Server Environment Best Practices NAT/Firewalls IP Environment Email/Spam/Black Hole Lists 2 Why Bother (Care)? Networking provides the communication allowing your applications to be accessible Do it wrong and you place your company and your applications at risk Possible Legal Risks? - Documented legal cases of organizations sued for poor security - Can affect your organization’s/department’s reputation - Can affect any/all Internet projects 3 Typical Environment Three-tired environment - Production - Staging - Development Source Control (Development) Email Relay Server for CF Mail Several Servers Networked Together 4 Typical Environment Typical Environment Diagram Router Firewall Internet DMZ Database Server Internal Email Server Network Server JRUN Server w/ Cold Fusion DNS Server 5 Development Env. Network Environment Your Corporate Network Will Have Many of These Components Your network may include the following items as well One or more switches to facilitate communication within the DMZ or Internal Zones Diagram Overview Network Address Translation within the Firewall Port blocking within the Firewall Load Balancers (for high traffic sites) Storage Area Network Internal DNS Challenge Often several employees/ departments will control the functioning of these network areas. Each will have their own areas of expertise. As a developer, you need to balance their technical concerns with the business requirements of your application. 6 Diagram Technical Overview Networking Definitions Internal - Workstations - File and Print Servers - Outbound communication with outside. Can pull information from DMZ computers DMZ or Production - Location of Servers (web, database, mail) Hosted - Location of some production application. Communication with network available through FTP and programs such as Terminal Services 7 Network Address Translation Definitions Business Challenge Provide communication to servers via a nonroutable IP address Use Non-Routeable Addresses to communicate behind the firewall - Internal and DMZ networks are on separate subnets - Example: 192.168.10.3 for a DMZ Server Example: 192.168.100.3 for a Workstation on the Internal network Addresses Reserved for Internet networking Prevent Outsiders from Knowing the True Address of Servers. - Servers will have non-routable addresses only. NAT Table provides reference Only Exposes to Outside servers needing Exposing 8 Routing Table Example 192.168.100.2 192.168.100.3 192.168.100.4 192.168.100.5 9 64.23.122.2 64.32.122.3 65.32.122.4 65.32.122.5 NAT: In Practice Packet arrives with IP address Business Challenge Prevent outsiders from reaching internal network resources. Firewall asks for location of DNS to translate name Firewall translates IP address acceptable list located in DMZ Reality Check Insiders need to have access to corporate resources on the road. A VPN solution allows specified laptops to have access to Internal resources. Server IP address contain NonRoutable IP address only Internal users access NAT through Internal DNS server containing nonroutable IP information. 10 NAT: Other Tools Things to Know All internal machines communicate via Non-routable IP address configured by DHCP Business Challenge With a limited pool of Internal addresses, allow employees to access resources on the Internet. DHCP uses Internal DNS to locate router Internal DNS acts as a gateway between the Internal and DNZ networks Set up DHCP, or a dynamic pool of internal address with right to access resources outside the Firewall. Resources RFC 1631 (http://www.faqs.org/rfcs/rfc1631.html) NAT Overview (http://computer.howstuffworks.com/nat1.ht m) 11 Email Spam: Risks and Challanges The Challenge CFMAIL Requires a Relay Server Business Challenge You need to send email to external customers using your application. You don’t want to spam, however. Spam is a huge problem on the open Internet Technology NAT can be used to specify who relays and who does not - 30-50% of all traffic is spam - Spammers use unethical methods to send email - Spam/Virus link? - Legal Liability? Black hole list can prevent your email from being routed to the right place 12 Successful CFMAIL Goals of System Business Challenge Provide the ability to use CFMAIL for external applications, while preventing spammers from having access to Mail servers. Factoid The new versions of Outlook do not by default allow customer to see HTML email. Spammers were using external pictures to validate email addresses. Goal 1: Prevent Outsiders from using Email Server. If not blocked then black hole list could shut down entire subnet Goal 2: Only allow Cold Fusion Server to send out Email Goal 3: Use an Opt –in Mail list collected from your site to send public email Resources 13 The Black Hole List What is a Black Hole List Email ends up in a black hole: It gets sent out, but customers never receive email Reasons Why Black hole lists allow administrators to block email from known places. Employees could be liable if they did not filter. Used by spam filters to reduce the flow of spam to inboxes Administrator subscribed Factoid Although the MAPS RBL allows users to be removed, some systems do not have a way to be removed from a list. If you receive a new IP block, check to see if it has been listed. Resources Realtime Black Hole List (http://www.mailabuse.org) Spamcop (http://www.spamcop.net) 14 Example in IIS Router Business Solution Only internal servers can relay. Since mail server accepts only Internal addresses, one must be located in the DMZ to relay. Separate server allows corporate email server never to relay Firewall Internet IIS Web/ Mail Server 192.168.10.6 Only allows 192.168.10.5 and other DMZ servers to relay 15 JRUN Server w/ Cold Fusion 192.168.10.5 SQL Server 192.168.10.7 Solution for Sending CFMAIL Create a Win-Win Situation Use a separate server for relaying mail from applications Results Successfully deliver CFMAIL to your customers. - Opt-In Lists One way of ensuring successful mail is through the use of Opt-in Maillists. In this case, you specifically ask for the permission of the person before sending out email from an application. New regulations require companies to only send out email for public applications using this method. Relay server only accepts internal IP addresses from DMZ siubnet Emails are logged by Cold Fusion Corporate email server never relays Configure corporate server to allow HTML email only from Internal Applications External Emails Should be Reviewed With Privacy Policy in Mind - 16 Should be Opt-in list only Should be text only for external customers Other Points Communication is the number one reasons why projects fail - The stakes are often higher for the System admins that your project - IT pros are naturally conservative outside their boundaries. IT is the one saying “no” Your organization requires better communication or an improved process - The implementation boundary is stretched What are your experiences? 17