Ethernet
advertisement

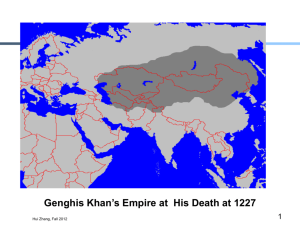
15-441 Computer Networks Ethernet I Professor Hui Zhang hzhang@cs.cmu.edu 1 Aloha Network 2 Hui Zhang Original Ethernet 3 Hui Zhang High Level View 4 Goal: share a communication medium among multiple hosts connected to it Problem: arbitrate between connected hosts Solution goals: High resource utilization Avoid starvation Simplicity (non-decentralized algorithms) Hui Zhang Medium Access Protocols Channel partitioning Divide channel into smaller “pieces” (e.g., time slots, frequency) Allocate a piece to node for exclusive use Random access Allow collisions “recover” from collisions Taking-turns 5 Tightly coordinate shared access to avoid collisions Hui Zhang Random Access Protocols Transmit at full channel data rate R. No a priori coordination among nodes Two or more transmitting nodes -> “collision”, Random access MAC protocol specifies: 6 When node has packet to send How to detect collisions How to recover from collisions Examples of random access MAC protocols: Aloha Slotted ALOHA CSMA and CSMA/CD Hui Zhang Aloha Nodes sends the message when it has data to send. If it receives an ack, it considers the transmission completed, otherwise it retransmits after a random delay. Simple, distributed protocol, but not very efficient 8 Central Computer 18% maximum utilization Slotted Aloha: more efficient. Reduces chances of collision 37% maximum utilization Hui Zhang Slotted Aloha Time is divided into equal size slots (= packet transmission time) Node with new arriving pkt: transmit at beginning of next slot If collision: retransmit pkt in future slots with probability p, until successful. Success (S), Collision (C), Empty (E) slots 9 Hui Zhang CSMA/CD Broadcast technology host host host host host host host host hub 10 Carrier-sense multiple access with collision detection (CSMA/CD). MA = multiple access CS = carrier sense CD = collision detection Hui Zhang CSMA/CD Algorithm Sense for carrier. If carrier present, wait until carrier ends. 11 Sending would force a collision and waste time Send packet and sense for collision. If no collision detected, consider packet delivered. Otherwise, abort immediately, perform “exponential back off” and send packet again. Start to send at a random time picked from an interval Length of the interval increases with every retransmission Hui Zhang Collision Detection B C Time A 12 Hui Zhang Collision Detection: Implications All nodes must be able to detect the collision. B C Any node can be sender The implication is that either we must have a short wires, or long packets. A Or a combination of both Can calculate length/distance based on transmission rate and propagation speed. Messy: propagation speed is mediadependent, low-level protocol details, .. Minimum packet size is 64 bytes – Cable length ~256 bit times 13 Example: maximum coax cable length is 2.5 km Hui Zhang CSMA/CD: Some Details 14 When a sender detects a collision, it sends a “jam signal”. Make sure that all nodes are aware of the collision Length of the jam signal is 32 bit times Exponential backoff operates in multiples of 512 bit times. Longer than a roundtrip time Guarantees that nodes that back off longer will notice the earlier retransmission before starting to send Hui Zhang Ethernet Frame Format 8 6 6 2 Preamble Dest Source Type 15 Data Pad CRC Preamble marks the beginning of the frame. 4 Also provides clock synchronization Source and destination are 48 bit IEEE MAC addresses. Flat address space Hardwired into the network interface Type field is a demultiplexing field. What network layer (layer 3) should receive this packet? Is actually a length field in the 802.3 standard CRC for error checking. Hui Zhang Minimum Packet Size 16 Why put a minimum packet size? Give a host enough time to detect collisions In Ethernet, minimum packet size = 64 bytes (two 6-byte addresses, 2-byte type, 4-byte CRC, and 46 bytes of data) If host has less than 46 bytes to send, the adaptor pads (adds) bytes to make it 46 bytes What is the relationship between minimum packet size and the length of the LAN? Hui Zhang Minimum Packet Size (more) Host 1 a) Time = t; Host 1 starts to send frame Host 2 propagation delay (d) Host 1 b) Time = t + d; Host 2 starts to send a frame just before it hears from host 1’s frame c) Time = t + 2*d; Host 1 hears Host 2’s frame detects collision Host 2 propagation delay (d) Host 1 Host 2 propagation delay (d) LAN length = (min_frame_size)*(light_speed)/(2*bandwidth) = = (8*64b)*(2*108mps)/(2*107 bps) = 5.12 km 17 Hui Zhang Ethernet Physical Layer 10Base2 standard based on thin coax. Thick coax no longer used Nodes are connected using thin coax cables and “T” connectors in a bus topology 18 host host host Host 10-BaseT uses twisted pair and hubs. host Hub acts as a concentrator The two designs have the same protocol properties. Key: electrical connectivity between all nodes Deployment is different host host host host Hub Hui Zhang Ethernet Technologies: 10Base2 19 10: 10Mbps; 2: under 200 meters max cable length Thin coaxial cable in a bus topology Repeaters used to connect up to multiple segments Repeater repeats bits it hears on one interface to its other interfaces: physical layer device only! Hui Zhang 10BaseT and 100BaseT 20 10/100 Mbps rate; later called “fast ethernet” T stands for Twisted Pair Hub to which nodes are connected by twisted pair, thus “star topology” Hui Zhang 802.3u Fast Ethernet Apply original CSMA/CD medium access protocol at 100Mbps Must change either minimum frame or maximum diameter: change diameter Requires 2 UTP5 pairs (4B5B) or 4 UTP3 pairs (8B6T) or 1 fiber pair No more “shared wire” connectivity. 21 Hubs and switches only 4B/5B encoding Hui Zhang Gbit Ethernet 22 Use standard Ethernet frame format Allows for point-to-point links and shared broadcast channels In shared mode, CSMA/CD is used; short distances between nodes to be efficient Uses hubs, called here “Buffered Distributors” Full-Duplex at 1 Gbps for point-to-point links Hui Zhang Traditional IEEE 802 Networks: MAC in the LAN and MAN Ethernet defined as IEEE 802.3. 23 Not quite identical The IEEE 802.* set of standards defines a common framing and addressing format for LAN protocols. Simplifies interoperability Addresses are 48 bit strings, with no structure 802.3 (Ethernet) 802.5 (Token ring) 802.X (Token bus) 802.6 (Distributed queue dual bus) 802.11 (Wireless) Hui Zhang LAN Properties Exploit physical proximity. Typically there is a limitation on the physical distance between the nodes, for example, – to collect collisions in a contention based network – to limit the overhead introduced by token passing or slot reservations 24 Relies on single administrative control and some level of trust. Broadcasting packets to everybody and hoping everybody (other than the receiver) will ignore the packet Token passing protocols assume everybody plays by the rules Hui Zhang Why Ethernet? Easy to manage. You plug in the host and it basically works No configuration at the datalink layer Broadcast-based. In part explains the easy management Some of the LAN protocols (e.g. ARP) rely on broadcast – Networking would be harder without ARP Not having natural broadcast capabilities adds complexity to a LAN – Example: ATM 25 Drawbacks. Broadcast-based: limits bandwidth since each packets consumes the bandwidth of the entire network Distance Hui Zhang 802.3z Gigabit Ethernet Same frame format and size as Ethernet. Full duplex point-to-point links in the backbone are likely the most common use. 26 This is what makes it Ethernet Added flow control to deal with congestion Choice of a range of fiber and copper transmission media. Defining “jumbo frames” for higher efficiency. Hui Zhang