Virtual Active Networks
advertisement

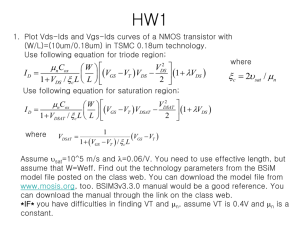
Virtual Active Networks Gong Su Mar. 9, 2000 Network Computing Models Traditional: end-to-end, Client-server software at end nodes The network is but a packet-transport wire Emerging: edge-to-edge Application services/components deployed at edge nodes Examples: web proxies, firewalls, QoS/bandwidth brokers… Applications need to interact with network resources & topology Configure resources to provide appropriate service Adapt to availability and performance of network components VAN: Middleware for Edge-Computing VAN is a middleware architecture that enables applications to Configure network topology Allocate node and link resources A Driving Example A web caching application needs… Coverage for certain network area Connectivity among caching service components Resources to move cached contents Solution: requests a VAN that provides Coverage: spans a ring between AS1, AS2, AS4, and AS5 Resources: provides at least 1mbps for all connections Reliability: prohibits more than 2 virtual links from traversing the same physical link Physical network Virtual spec. A 1mbps B 1mbps D Logical hierarchy AS1 D C AS2 1mbps 1mbps C A B D C Mapping by VAN AS5 B A AS4 AS3 VAN Contributions Enable applications to configure network Acquire distributed node and link resources Algorithm that maps VAN specification to physical resources Deadlock-free VAN resource provisioning protocol Recover from underlying network failure Protocol that preserves VAN service semantics under failures VAN Service Arch Components VAN Local Manager (VLM) Manages local node resources Supports deadlock-free VAN provisioning Monitors & reports resource status VAN Domain Server (VDS) Provides VAN services to application VAN provisioning Resource acquisition Performance monitoring Manages VAN to recover from physical network failure Active node with VLM AS3 AS1 D C AS2 VDS VDS AS5 B A AS4 VDS administrative domain Specification Mapping Heuristic mapping algorithm Sort VNs and PNs by degree; map VN to PN by degree-order Mark all PL without enough bandwidth for the VLs as infeasible Each PL has a “mapped-onto” counter, initially 0 pick a VL and map it to a physical path with lowest maximum counter among all PLs traversed After each VL is mapped, increment counter and subtract available bandwidth for each PL; mark a PL infeasible as appropriate Repeat until all VLs are mapped A 1mbps AS1 D B 1mbps D C AS2 1mbps 1mbps AS3 0 1 2 0 1 0 1 1 0 C AS5 B 0 1 A AS4 Resource Acquisition Protocol Acquires node and link resources Deadlock among competing VANs for shared resources can occur because Intra-domain: VDS – VLM Inter-domain: VDS – VLM and VDS – VDS One VAN is built in many domains distributedly Many VANs are built in many domains simultaneously Example VDS1 and VDS2 build VAN1 and VAN2 in domain A respectively VDS3 and VDS4 build VAN1 and VAN2 in domain B respectively VAN1 preempts VAN2 in domain A VAN2 preempts VAN1 in domain B B A VDS2 VDS1 VAN1 VLM1 VAN2 VDS3 VDS4 VAN1 VAN2 VLM2 Deadlock Prevention Protocol B A How does the solution work Assign “weight” to VNs and VLs Each VDS computes a “Progress Index” (PI), indicating “how much” a VAN has been built PIs are globally synchronized and used as the priority for preemption when conflict 1 VDS’es happens request resource VDS2 VAN1:3 6 VLM notifies VDS’es with the arbitration decision VLM2 VAN2:6 VLM1 B 4 A 3 VDS2 1 2 2 3 4 1 VDS4 VDS3 VDS1 2 VLM detects conflict and initiates arbitration 5 VDS’es ack arbitration request VAN2:2 VAN1:7 3 VDS broadcasts to all other VDS’es requesting global PI Other VDS’es ack sync request 4 synchronization VDS4 VDS3 VDS1 VLM2 VLM1 B A VDS4 VDS3 VDS1 VDS2 5 6 6 VLM1 5 VLM2 Failure Recovery When a physical link fails, the VLs it carries must be restored First try Local repair Find an alternative path with adequate resources between the two disconnected AS’es Fast, and preserve original topology But May violate reliability constraint Alternative path may not exist Example Physical link between 2 and 3 goes down Alternative path goes through 2, 1, 4, and 3 2 1 Physical link Virtual link 3 4 5 6 2 1 Reliability violation 3 4 5 6 Failure Recovery: Global Repair Local repair may violate reliability constraints or it may not be able to find an alternative path Global repair Computes substitute VL based on global topology and resource information Reconstruct topology when local repair cannot; guarantee reliability constraint But Computationally expensive Communication delay between root VDS and local VDS’es Example Substitute VL computed between 5 and 6, replacing the VL going VDS1 through 2, 1,VDS1 4, and 3 2 2 1 1 Physical link 3 4 Virtual link 5 VDS2 VDS3 6 3 4 VDS3 5 VDS2 6 Schedule End of Spring 2000 Efficiently obtain global topology and resource information Summer 2000 (first half) Heuristics for virtual specification to physical network mapping with constraints Summer 2000 (second half) Algorithm for computing dynamic priority (PI) and analyze conflict resolution protocol Fall 2000 (first half) Efficient local repair mechanism (study MPLS fast rerouting, ATM self-healing, etc.) Fall 2000 (second half) Incremental global repair mechanism