Slide
advertisement
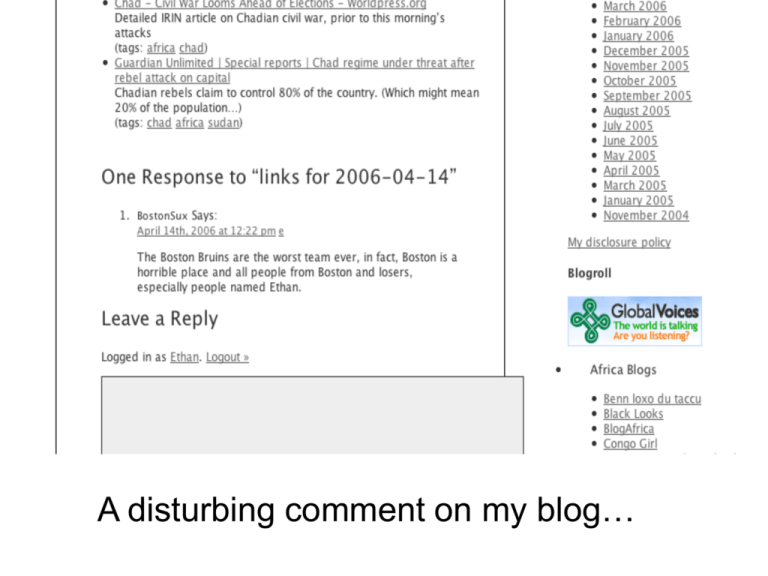
A disturbing comment on my blog… Who is sux@boston.com? IP: 128.100.171.22 sux@boston.com posted from this IP! So what’s an IP? An address. Every computer connected to the Internet has one, or shares one. Four numbers - each 0-255, separated by periods: 128.100.171.22 Try typing “66.233.167.99” into a web browser. You get… 66.233.167.99 is the IP address of one of the thousands of computers that run Google’s website. Easier to remember “google.com”, huh? Every computer on the Internet has an IP address or shares one. Everything transmitted on the Internet - an email, a webpage, a picture, a sound file - is made up of one or more “packets” of data. These packets have a header, a payload and, sometimes, a footer. The header includes the IP address of the computer sending a packet, and the IP address of the computer receiving it. When you type 66.233.167.99 into your browser, you send a set of packets to a Google computer, asking it to send some packets back to your IP address. Your browser assembles those packets into the Google homepage. So what’s my IP address? 151.203.155.73. Or was that 192.168.0.103? Network Address Translation lets 254 computers share one IP address! Who is 128.100.171.22? No - whois 128.100.171.22! One of 65,536 IP addresses at U Toronto… “Dear Russ, which of your users thinks Boston sucks?” nslookup at kloth.net haxor.citizenlab.com! whois contacts the authority responsible for assigning IP addresses and asks who has been assigned the IP address you’re curious about. nslookup uses the domain name system the system that associates the names of computers connected to the Internet to IP addresses - to tell you what domain names are associated with an IP address. Aha! Nart works for Citizen Lab! Allowing me to craft an appropriate response… Other possible outcomes: - IP address was from a shared or publicly accessible computer. Result: no way to know who made the post without a record of users. - IP address was from an ISP via dialup, DSL or cable modem. Result: ISP may have records of which user had the IP, but won’t release except under subpoena. - IP address was a proxy or anonymizer, designed to hide the poster’s identity. Result: Proxy operator may - or may not - have records of the real IP. IP address is a lousy identifier. What happens if Google says “Hello, Ethan here’s your new gmail” when it sees a request from 151.203.155.73? Anyone in my house can read my mail. And when my ISP gives me a new IP, someone else is very confused to be greeted as Ethan. Unfortunately, IPs get treated like unique identifiers often… because we don’t have other options. I can’t get information from an ISP about who has a particular IP… But governments can. Security online is about protecting and obscuring your IP address. If you don’t protect your identity, prepare to have your computers seized… Deleting & Wiping files • When files are deleted the name is removed from the disk and the space is marked as available for new data • As long as no data is written to that space the original file can be recovered • A little experiment – A file called secretfiles.doc was created in “My Documents” – It was “deleted” and sent to the Recycle bin – The Recycle bin was emptied Undelete Wiping • Wiping utilities overwrite data with garbage • The greater the number of overwrite passes it makes the more difficult it is to recover the data Dpeft boe djqifst: voefstuboejoh fodszqujpo Dpeft boe djqifst: Codes and ciphers: voefstuboejoh fodszqujpo understanding encryption Codes and ciphers: Add to each letter: 1 Dpeft boe djqifst: “Add to each letter” - algorithm “1” - secret key A very weak form of encryption… A better cipher + -+-+-+ -+-+-+ 1 234512 345123 B zhpydt zmkicu Realworld ciphers use complex, multipart algorithms and LONG keys. Algorithms are public - keys are secret. An encrypted file… Encrypted Storage • A lot of utilities, a nice one for Windows is BestCrypt (http://www.jetico.com/) • It creates an additional drive letter that you need to enter a password to access Encrypted Storage Encrypted Storage Encrypted Storage • Any files you place in the BestCrypt drive are encrypted • When you unmount the drive, the drive letter disappears Remote Backup • Store files on a remote server • Allows you to recover your files if something happens • You can remove sensitive files from you computer, and retrieve them at a later time Martus.org • Martus is a software tool that allows users to create “bulletins”, uploading them at the earliest opportunity, and storing them on redundant servers located around the world Martus.org • Records are encrypted, stored securely at a remote site, backed up to multiple locations and protected by a unique password. • After a bulletin has been designated as final by the user, it cannot be altered, ensuring that even an unauthorized user who may have obtained access cannot delete the group's records. Some bad passwords: “fluffy” - Pet’s name (guessable) “010473” - Dates (guessable) “solitaire” - common words (vulnerable) Dictionary attacks - take every word in a dictionary. Encrypt them. See if any one matches the password. If so, you’re in! Better password: fluffy010473 Even better: fluFFY0104&# VGY&BHU* Not very easy to remember… VGY&BHU* Very easy to remember… possibly too easy 99bob@TW “Ninety nine bottles of beer on the wall” The longer the better Mix of letters, numbers, symbols UPPER and lowercase MiXeD BUT A good password is memorable without writing it down. A written password is a broken password. If you can only remember one password, use PasswordSafe or PasswordGorilla… Surveillance & Locations • Low-tech (security camera placed at a cyber-cafe) • Local (software on a specific PC, e.g. keystroke logger) • Network/ISP • Internet backbone / Int’l gateway PC: Key Stroke Logger • Hardware or Software that logs all key strokes • Intercepts passwords • Log files can be transmitted to remote location Packet Sniffing • Intercept network traffic • Protocol Analysis (HTTP vs. SMTP) • Optionally, search for specific strings (keywords, names, email addresses) What Filtering Looks Like Filtering: Where and How • DNS filtering • IP filtering • URL filtering Filtering • Detecting Filtering – Sometimes an error is just an error – How can we tell? • Responding to Filtering – Knowing how a site is filtered is extremely important Block Pages • Confirms a block • May contain category information • May indicate tech used • View-Source: – <ISUTAG filter="sf" url="http://www.playboy.com/" > – <ISUTAG filter="local" url="http://www.islah.tv/"> HTTP Headers • May identify filtering tech – Iran: NEDA GET http://www.emrooz.ws/ HTTP/1.1 HTTP/1.x 403 Forbidden X-Squid-Error: ERR_SCC_SMARTFILTER_DENIED • 404 or 403 – Distinguish between errors • 302: Check Redirects – UzSciNet GET http:// forum.ferghana.ru / HTTP/1.1 HTTP/1.x 301 Moved Permanently Location: http://ferghana.ru/ • 200: Blockpage? – Server header is good indicator Network Interrogation • Tools: – Traceroute – TCP Traceroute – Packet Sniffer Key Questions • • • • Is the site filtered for sure? Is there an indication why it is filtered? When is it time to sound the alarm? When is it time to activate your circumvention strategy? Circumvention Strategies • Push strategies: content delivered to users. • Pull strategies: enables users to access content. Get to know your users • Context and location of users • Spectrum from casual to committed • Servicing Users – Sign-up profiles – Email list • Identify users that want continued information – Interactivity – Updates Info Management • There will be windows of opportunity: it takes time for a site to be filtered • Information you make public can be discovered by those who filter • Develop responses to filtering that relate to your users Responses • • • • Communication Strategy Mirroring Strategy Syndication Strategy Circumvention Strategy Communications • Sustain communication with users – Email – IM, Chat, SMS • Advertise new locations – E.g. Google Ads Mirroring • Register multiple domain names • Obtain accounts on several ISPs • Have a technical mirroring solution ready Our clever db trick… Syndication • CC/GPL for syndication options • RSS – Third-party aggregators – RSS emailer – RSS mirrors • P2P Responses Circumvention Simple Circumvention • Sometimes it’s a simple as removing “www” from the domain name • Or accessing the IP directly or through an alternate domain name • Or using the Google cache Two Types of Users • Providers: non-filtered locations • Users: censored locations • Successful circumvention relies on meeting the needs of both users. Determining Needs and Capacity • • • • • • Bandwidth User location Level of technical expertise Trusted contacts Potential penalty Full disclosure Public vs. Private • Public – Zero Trust – Could be blocked • Private – Trusted contact – Low circulation Not Anonymous • If plaintext, the content of the session can be easily intercepted and analyzed by an intermediary such as an Internet Service Provider (ISP) Public Systems Web-based Proxies • • • • • • • http://www.anonymizer.com/ http://www.unipeak.com/ http://www.anonymouse.ws/ http://www.proxyweb.net/ http://www.guardster.com/ http://www.webwarper.net/ http://www.proxify.com/ • http://www.the-cloak.com/ “Open” Proxy Servers • • • • http://www.samair.ru/proxy/ http://www.antiproxy.com/ http://tools.rosinstrument.com/proxy/ http://www.multiproxy.org/ • http://www.publicproxyservers.com/ Modify Browser Setting “Open” Proxy Servers • Not secure, traffic is in plain text • Not anonymous, proxy owner can intercept all traffic • Often just misconfigured servers that are not intended for public use Private Key encryption: - Fast - Secure - Strength proportional to key length Works great for protecting my files. But what if I want to send a secret message to you? The problem: Key distribution. Conventional encryption is symmetric: “cipher” “djqifs” key “cipher” key Public encryption is not symmetric: “cipher” “cgaone” Key A “cipher” Key B You can encode a message with Key A, but Key A is useless for decoding it. Weird! Key A = public key. Key B = private key. In conventional encryption, I send a message to the recipient in a locked box. Sender Recipient Both of us have the key, and both of us can open the box. In public key encryption, the recipient first sends me an unlocked box to which only she has the key. I lock my message inside and send the box to her… Recipient Once I’ve locked the message in the box, I can’t read it, as I don’t have the key! It’s safe for the recipient to send me a lock, as the lock doesn’t allow me to unlock a locked box. (Weird.) Why is it safe to send a credit card number over the internet? When you request an https:// site, that site sends your browser a public key - an unlocked box. Your browser encrypts your information so only that site can read it. Signed Certificates • A Certification Authority (CA) digitally signs each certificate issued • Each browser contains a list of CAs to be trusted • When the SSL handshake occurs, the browser verifies that the server certificate was issued by a trusted CA • If the CA is not trusted, a warning will appear Man-In-The-Middle Attack Private Circumventors • Leverages personal relations of trust • Web-based circumventor on SSL-enabled webserver • Circumvention & security is the focus, not anonymity or privacy Civisec & Psiphon • Psiphon is an encrypted webserver + webbased proxy • It is designed for personal use, based on the circle of trust model • It is private and decentralized Psipon • Users in non-censored countries download the software • The location is shared with users your personally know and trust in censored countries • The user in the censored country does not have to download any software Redundancy • The circle of trust is based on social networks • This model can be optionally extended for redundancy Extending Trust • Pro – Redundancy – Larger user base • Con – Increases chance of infiltration – Increases chance of blocking Anonymous Communications Systems • Anonymity is protected from: – ISP – Circumvention system – Content server • Examples – Java Anonymous Proxy – TOR Explaining Tor Downsides of Tor • - slow • dangerous if you’re the only one using it • Hard to use? We tend to treat email like it was private. It’s not. In the US, if your employer provides your email, he is permitted to read it. Many do. The administrator of your mail system can read your unencrypted email. How well do you trust your sysadmin? The sysadmin on the receiving end? If anyone is sniffing packets on your network, they can read all unencrypted traffic - including email. Ask your sysadmin if they support IMAPS or POPS. Most do, and most will thank you for using it. When using web-based mail, use services that use https. Try this - https://gmail.google.com Even with https, the email is still vulnerable on the server and your hard drive. Enter PGP… Using Thunderbird with OpenGPG Enigmail requires Thunderbird, GPG (a PGP implementation) and the Enigmail package. Using pgp.mit.edu to find a public key. Is the key legit? PGP users “sign” each other’s keys - this verifies that the person using the key is actually the person associated with it. When a PGP-encrypted email arrives, Thunderbird asks you to enter your passphrase to decrypt. Also alerts you to signed mail. Hushmail - PGP made easy (okay, easier.) + + Near-anonymous blogging Tor installed, ready to go… Torpark - torpark.nfshost.com - Tor on a USB key! If you’re concerned that your blog will get you into trouble, blog from an unmonitore d cybercafe, and use Torpark on a USB key. Make sure Tor is working before relying on it. http://serifos.eecs.harvard.edu/cgi-bin/ipaddr.pl?tor=1 When using the web through Tor, your IP address is hidden - you appear to be coming from a different IP. Set up a hushmail account with a name that is not easily linked to you. Why we don’t recommend Hotmail… Or Yahoo! Mail… As long as you sign up via Tor, you’d be okay… But gmail… …and hushmail don’t report your IP in their headers. Still using Tor, and using your new hushmail account, sign up for a Wordpress blog. The process isn’t perfect. Wordpress doesn’t expect you to be using Tor, and chokes occasionally. Ignore the errors and keep going… Wordpress will send an email to your hushmail account. Respond - using Tor - to activate the new blog. Your brand new, highly secure, hosted blog! Using Tor, you can start posting. But one concern remains: Sleepless in Sudan: Aid worker blogging from Darfur, highly critical of Sudanese government. Needs to remain completely anonymous. We know the Khartoum government is watching Sleepless’s blog. We know they can watch all Internet traffic coming out of Sudanese ISPs. Every time something is posted to the blog, there’s a request from a specific IP to a Tor server… Sleepless must be posting through Tor - let’s arrest her! Changing timestamps to prevent timing attacks. Consider putting the date 5-15 minutes ahead of time - the blog will autopublish once you’ve already logged out! To stay anonymous: - Post, email and comment through Tor or another proxy. - Minimize information that could only have come from you. - Post from unmonitored public computers (danger of keystroke logging! ) - Post from your machine (danger that you’re one of very few people using Tor/Proxy!) - Don’t be stupid. Why you should not be anonymous: -Identify yourself and by default, you’re trusted. Conceal yourself and by default, you’re not. - Secrecy leads to speculation - is Salam Pax a CIA agent? An al-Qaeda member? - Need to build your reputation as an anonymous blogger over many posts. - If you can’t blog without being anonymous, be anonymous. If you can, seriously consider blogging in your own name. Why is “Inside PCIJ” the top result for “gloria garci”? How Google works… (sort of) When you search for a term, you get web pages that include that term. They’re ranked by “authority”. “Authority” = popularity = incoming links (adjusted for spam, freshness, link farms) PageRank - algorithm that determines authority of a page… mypagerank.net Rank: 0-10, logarithmic. Yahoo = 9, Google = 10 PCIJ’s blog is a “6” - pretty good! Manila Standard is a “4”. Not so good. PCIJ is 100x more authoritative. How much do we trust Jeff Ooi? Google says Jeff is a “6”! Who links to Jeff? Technorati.com 1794 links from 822 sites, #1,125 in the world! Who links to Jeff… and why? Why we link: - Participate in conversations - Reinforce social ties (blogroll) - Ask for links back to our work If you want links to your blog, link to other blogs. Comment on other blogs. Answer your own comments. Start conversations. Blogpulse.com pubsub.com Tags identify blog content Jordanplanet.net - a national blog aggregator Posts from blogs, blogroll… Virtual communities are also real-world communities. We link to people we know… The Kaybees Kenya’s national blog awards… Clay Shirky - Weblogs and Power laws Popular blogs - 10,000+ incoming links Making friends with the A-List: - Don’t beg. - Know what they write about. - Link before you ask. - At a certain point, bloggers are journalists disclosure of conflicts, transparency about linking.