Document
advertisement
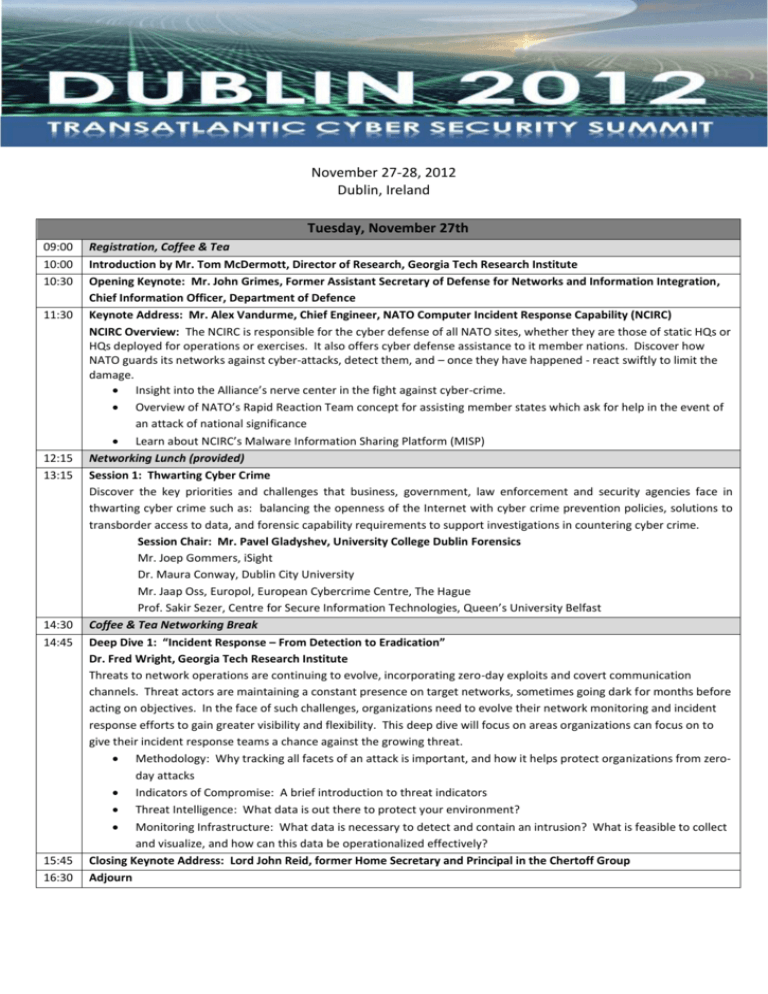
November 27-28, 2012 Dublin, Ireland Tuesday, November 27th 09:00 10:00 10:30 11:30 12:15 13:15 14:30 14:45 15:45 16:30 Registration, Coffee & Tea Introduction by Mr. Tom McDermott, Director of Research, Georgia Tech Research Institute Opening Keynote: Mr. John Grimes, Former Assistant Secretary of Defense for Networks and Information Integration, Chief Information Officer, Department of Defence Keynote Address: Mr. Alex Vandurme, Chief Engineer, NATO Computer Incident Response Capability (NCIRC) NCIRC Overview: The NCIRC is responsible for the cyber defense of all NATO sites, whether they are those of static HQs or HQs deployed for operations or exercises. It also offers cyber defense assistance to it member nations. Discover how NATO guards its networks against cyber-attacks, detect them, and – once they have happened - react swiftly to limit the damage. Insight into the Alliance’s nerve center in the fight against cyber-crime. Overview of NATO’s Rapid Reaction Team concept for assisting member states which ask for help in the event of an attack of national significance Learn about NCIRC’s Malware Information Sharing Platform (MISP) Networking Lunch (provided) Session 1: Thwarting Cyber Crime Discover the key priorities and challenges that business, government, law enforcement and security agencies face in thwarting cyber crime such as: balancing the openness of the Internet with cyber crime prevention policies, solutions to transborder access to data, and forensic capability requirements to support investigations in countering cyber crime. Session Chair: Mr. Pavel Gladyshev, University College Dublin Forensics Mr. Joep Gommers, iSight Dr. Maura Conway, Dublin City University Mr. Jaap Oss, Europol, European Cybercrime Centre, The Hague Prof. Sakir Sezer, Centre for Secure Information Technologies, Queen’s University Belfast Coffee & Tea Networking Break Deep Dive 1: “Incident Response – From Detection to Eradication” Dr. Fred Wright, Georgia Tech Research Institute Threats to network operations are continuing to evolve, incorporating zero-day exploits and covert communication channels. Threat actors are maintaining a constant presence on target networks, sometimes going dark for months before acting on objectives. In the face of such challenges, organizations need to evolve their network monitoring and incident response efforts to gain greater visibility and flexibility. This deep dive will focus on areas organizations can focus on to give their incident response teams a chance against the growing threat. Methodology: Why tracking all facets of an attack is important, and how it helps protect organizations from zeroday attacks Indicators of Compromise: A brief introduction to threat indicators Threat Intelligence: What data is out there to protect your environment? Monitoring Infrastructure: What data is necessary to detect and contain an intrusion? What is feasible to collect and visualize, and how can this data be operationalized effectively? Closing Keynote Address: Lord John Reid, former Home Secretary and Principal in the Chertoff Group Adjourn Wednesday, November 28th 08:30 09:00 15:45 Networking Breakfast (provided) Opening Keynote: Dr. Robert J. Elder, USAF Lt General (Ret.), Research Professor, George Mason University “Alternative Approaches to Leverage Cyberspace for National Security” Session 2: International Collaboration and Information Sharing This session discusses the key international challenges affecting cooperation and coordination of cyber policy and solutions. Understand how fostering strong public-private partnerships are a critical element in combatting the continually evolving threat posed by cyber attacks and the role industry and academia can play in creating strong international partnerships. Understand the difficulties in exchanging business and government cyber intelligence and how the outmoded bureaucratic barriers that slow us down can be removed. Session Chair: Mr. Jeff Evans, Georgia Tech Research Institute Mr. Ben Canino, United States Department of Homeland Security Mr. Brian Honan, Irish Reporting and Information Security Service, CERT Mr. Etienne DeBurgh, Financial Services Information Sharing and Analysis Center Mr. Philip Mills, Centre for Secure Information Technologies, Queen’s University Belfast Mr. Slawomir Grzonkowski, Digital Enterprise Research Institute, National University of Ireland Galway Coffee & Tea Networking Break Deep Dive 2: "Malicious Software Analysis and Threat Intelligence Sharing" Mr. Andrew Howard, Georgia Tech Research Institute Malicious code is one of the most common tools in breaching computer networks, despite continued efforts to improve detection and removal. State-sponsored malware has become increasingly difficult to prevent and mitigate due to the use of advanced data-stealing capabilities. Benefit from the opportunity to get the latest innovations on malware forensics and anti-malware techniques. Learn about an approach for community-driven threat intelligence to ensure that actionable intelligence disseminates quickly among organizations, ensuring rapid reaction to increasingly agile threats. This deep dive will: Describe methods for designing and implementing automated malware analysis systems Discuss reasons why building an automated environment is beneficial to any organization's incident response capability Enhance your understanding of technical solutions to anonymous sharing of community-driven threat intelligence Networking Lunch (provided) Keynote Address: Mr. Joe Weiss, Applied Control Solutions, LLC Building the Industrial Control Systems Cyber Security Workforce: The average life of an ICS system is typically about 815 years (INL, 2004) but we all know that individual devices can be out there a great lot longer, and that the chain is as strong as its weakest link… The reality is that most control systems engineers and operations teams have to make do with their legacy workstations and OSs, communications networks and field devices. In this unique session, you will learn about cyber-security risks that affect our world’s infrastructure and perhaps the weakest link in the chain—the lacking ICS cyber security workforce. Session 3: Building the Cyber Workforce Despite new approaches to network design and the latest in automated tools for detecting threats and defending networks, cyber security professionals are outflanked, outgunned, and often outwitted by very sophisticated and unknown enemies. This session discusses what must be done to expand and better prepare a more technically diverse cyber workforce and how leveraging industry, international partnerships, and especially academia is crucial to meeting the challenges of advanced persistent threats. Session Chair: Dr. Robert J. Elder, USAF Lt General (Ret.), Research Professor, George Mason University Mr. Joe Weiss, Applied Control Solutions, LLC Dr. James Breckenridge, Mercyhurst University Lt Col (S) Bryant Springer, US Army, Chief Intel Systems, USAFRICOM Mr. Colm Fagan, Espion Mr. Tahar Kechadi, University College Dublin Forensics Closing Keynote: Dr. Jack Callahan, Office of Naval Research Global 16:30 Adjourn 10:00 11:15 11:30 12:30 13:30 14:30






