ProSafe Smart Wireless Switch
WFS709TP
Section 1: Course Introduction
© .1996-2006 NETGEAR® . All rights reserved
2
Course Description
» This course will cover product specifications, product features,
hardware installation and software administration of the
WFS709TP ProSafe Smart Wireless Switch.
» The course is intended for L1, L2, L3 technical support engineers,
VARs and sales.
© .1996-2006 NETGEAR® . All rights reserved
3
Course Prerequisites
» Students should have a basic understanding of OSI reference
model and be familiar with 802.11 standard.
» Understanding of 802.1Q and DHCP will be very helpful.
© .1996-2006 NETGEAR® . All rights reserved
4
Course Objectives
» Upon successful completion of this course, students will be able
to answer questions about hardware specifications and features
of the wireless switch and the light wireless access points.
» Students will be able to physically install the hardware, initialize
the wireless switch for management, provision access points to
be managed by the wireless switch, use RF planning tool to plan
WLAN deployment and configure their wireless network.
© .1996-2006 NETGEAR® . All rights reserved
5
Course Agenda
»
»
»
»
»
»
»
»
Section 1: Course Introduction
Section 2: Product Information
Section 3: Product Features
Section 4: Competitive Information
Section 5: Pre-install / Site Survey
Section 6: Hardware Installation
Section 7: Software Installation
Section 8: Software configuration
• RF Planning
• Guest Access
• Multiple controller and Redundancy
• IDS
» Section 9: Testing the completed installation
» Section 10: Troubleshooting
© .1996-2006 NETGEAR® . All rights reserved
6
Section 2: Product Information
© .1996-2006 NETGEAR® . All rights reserved
7
Product Description
» The WFS709TP ProSafe Smart Wireless switch is a full-featured
wireless switch that centrally manages NETGEAR light access
points.
» It provides wireless mobility, security and converged services for
both wired and wireless users.
© .1996-2006 NETGEAR® . All rights reserved
8
Design and Architecture
» WFS709TP uses “thin APs”. There is very little functionality
included in the AP.
» WFS709TP work with WGL102 and WAGL102 or WG102 and
WAG102 converted with new firmware. Once converted to “thin
AP” firmware, WG102/WAG102 cannot be restore back to
standalone AP.
© .1996-2006 NETGEAR® . All rights reserved
9
Section 3: Product features
© .1996-2006 NETGEAR® . All rights reserved
10
Features Overview
» Controlled up to 16 access points
» 8 Fast Ethernet ports with PoE support. 802.3af compliance 48VDC with
maximum aggregate power draw of 100W
» Gigabit Ethernet ports: One 10/100/1000Base-T
» One serial console port
» Centralized management and monitoring of wireless infrastructure
» Built-in RF Planning tool
» Wireless intrusion detection and protection
» Advanced security features such as 802.1x that support EAP-PEAP, EAPTLS, EAP-TTLS; 802.11i, MAC address authentication, captive-portal
» 802.1Q VLAN
» Layer-3 routing
© .1996-2006 NETGEAR® . All rights reserved
11
Wireless LAN Security and Control Features
»
»
»
»
»
»
»
»
»
»
»
802.11i security (WFA certified WPA2 and WPA)
802.1x user and machine authentication
EAP-PEAP, EAP-TLS, and EAP-TTLS support
802.11i PMK caching for fastroaming applications
EAP offload for AAA server scalability and survivability
Stateful 802.1x authentication for standalone APs
MAC address, SSID and locationbased authentication
Multi-SSID support for operation of multiple WLANs
SSID-based RADIUS server selection
Secure AP control and management over IPSEC or GRE
Simultaneous centralized and distributed WLAN support
© .1996-2006 NETGEAR® . All rights reserved
12
Identity-Based Security Features
» Wired and wireless user authentication
» Captive portal; 802.1x and MAC address authentication
» Username, IP Address, MAC address and encryption key binding
for strong network identity creation
» Per-packet identity verification to prevent impersonation
» RADIUS and LDAP based AAA server support
» Internal user DB for AAA server failover protection
» Per-user session accounting for usage auditing
» Configurable acceptable use policies for guest access
© .1996-2006 NETGEAR® . All rights reserved
13
Convergence Features
»
»
»
»
»
»
»
»
»
»
»
»
Voice and data on a single SSID for convergence devices
Flow-based QoS using Voice Flow Classification (VFC)
SIP, Spectralink SVP, Cisco SCCP and Vocera ALG
Strict priority queuing for over-the-air QoS
DiffServ marking and 802.1p support for network QoS
On-hook and off-hook
VoIP client detection VoIP call admission control (CAC) using VFC
Call reservation thresholds for mobile VoIP calls
Voice-aware RF management for ensuring voice quality
Fast-roaming support for ensuring voice quality
SIP early media and ring tone generation (RFC 3960)
Per-user and per-role rate limits (Bandwidth contracts)
© .1996-2006 NETGEAR® . All rights reserved
14
IntelliFi Radio Management Features
»
»
»
»
»
»
»
Automatic channel and power settings for controlled APs
Simultaneous air monitoring and end user services
Self-healing coverage based on dynamic RF conditions
Dense deployment options for capacity optimizations
AP load balancing based on number of users
Coverage hole and RF interference detection
802.11h support for radar detection and avoidance
© .1996-2006 NETGEAR® . All rights reserved
15
Wireless Intrusion Protection Features
» Integration with wireless infrastructure
» Simultaneous or dedicated monitoring capabilities
» Rogue AP detection and built-in location visualization
© .1996-2006 NETGEAR® . All rights reserved
16
Networking features
»
»
»
»
»
»
»
»
L2 and L3 switching over the air and over the wire
VLAN pooling for easy, scalable network designs
VLAN mobility for seamless L2 roaming
Proxy mobile IP and proxy DHCP for L3 roaming
Built-in DHCP server and DHCP relay
VRRP-based N+I controller redundancy (L2)
AP provisioning-based N+I controller redundancy (L3)
802.1d Spanning Tree Protocol
© .1996-2006 NETGEAR® . All rights reserved
17
Wireless switch management features
»
»
»
»
»
»
»
»
»
RF planning and AP deployment toolkit
Centralized AP provisioning and image management
Live coverage and visualization heat maps
Detailed statistics visualization for monitoring
Remote packet capture for RF troubleshooting
Interoperable with Ethereal®, Airopeek and AirMagnet© analyzers
Multi-controllers configuration and management
Location visualization and device tracking
System-wide event collection and reporting
© .1996-2006 NETGEAR® . All rights reserved
18
Wireless switch administration features
» Web-based user interface access over HTTP and HTTPS
» Quickstart screens for easy controller configuration
» Restricted CLI access using console, disabled by default CLI
access, SSH and telnet console
» Role-based access control for restricted admin access
» Authentication access via RADIUS, LDAP or internal DB
» SNMPv3 and SNMPv2 for controller monitoring
» Standard MIBS and private enterprise MIBS
» Detailed message logs with syslog event notification
© .1996-2006 NETGEAR® . All rights reserved
19
Section 4 Competitive Information
© .1996-2006 NETGEAR® . All rights reserved
20
Section 5 Pre-Installation; Site Survey
© .1996-2006 NETGEAR® . All rights reserved
21
Package Contents
»
»
»
»
»
»
»
»
WFS709TP wireless switch
Power adapter cord
Four 12-24 screws for attaching the switch to an equipment rack
RS-232 serial cable with RJ-45 male connectors and serial
adapter to connect the serial cable to a terminal or PC with a DB-9
serial port
Ethernet cable
Resource CD
Warranty and Support Card
Quick Install Guide
© .1996-2006 NETGEAR® . All rights reserved
22
Unpacking the hardware
» Check the contents of the boxes to make sure that all items are
presents before beginning the installation.
• 1. Place the container on a clean flat surface and cut all straps
securing the container.
• 2. Unpack the hardware from the boxes.
• 3. Remove all packing material.
• 4. Make sure that all items are present. If any item is found
missing or damaged, contact local NETGEAR reseller for
replacement.
• 5. Inspect the products and accessories for damage .Report any
damage immediately.
© .1996-2006 NETGEAR® . All rights reserved
23
Site Requirements
» Reliable power
• Make sure the electrical outlet is compatible with the WFS709TP
»
»
»
»
Power consumption: 170W maximum
AC input voltage: 90-132VAC, 180-264VAC, auto-sensing
AC input current: 4A@110VAC
AC input frequency: 47-63Hz
• Power cord must be rated to 10 A and must conform to grounded electrical
standard in the country in which the WFS709TP operates.
• Use of a power line conditioner or UPS can decrease or mitigate problems caused
by power services fluctuations. Make sure that the output of any power shaping
device is compatible with the WFS709TP power supply.
» Cool, non-condensing ventilation
• Operating temperature: 0 to 40C Storage temperature 0 to 50C
• Humidity: 5% to 95% (non-condensing)
• Altitude: up to 10,000 feet
» Ample space
• For proper air circulation, leave at least 10cm clearance for the vents on the left
and right side of the chassis.
» Limited electromagnetic interference
• For best operation, keep the WFS709TP and all cords and cables at 0.7 meters
from fluorescent lighting fixtures, and 2 meters from photocopiers, radio
transmitters, electric generators and other source of strong electromagnetic
interferences.
© .1996-2006 NETGEAR® . All rights reserved
24
Deployment recommendations
» AP Deployment
• Whatever makes sense from a cabling perspective
• AP configuration is the same in either case
• AP don’t care if they are directly or indirectly attached
» Controller Deployment
• Follow the database
• Deploy controllers close to the terminus of user data
• Typically this is the data center.
© .1996-2006 NETGEAR® . All rights reserved
25
Section 6: Hardware Installation
© .1996-2006 NETGEAR® . All rights reserved
26
Front and rear panel
© .1996-2006 NETGEAR® . All rights reserved
27
1. System LED
© .1996-2006 NETGEAR® . All rights reserved
28
2. Eight Fast Ethernet ports
» A. Link LED
» B. PoE LED
» C. Access point status.
• Red (Solid) – AP on this port has failed (highest precedence)
• Red (Flashing) – An air-monitor on this port has detected an unsecure AP.
• Green (flashing) – An air monitor on this port has detected interference. The
interfering device has been detected by your valid APs, but has no wired presence on
your network.
• Amber (solid) – Load balancing is enabled on this port, or an AP has reached the
maximum number of clients it is configured to support.
• Green (solid) – All detected APs on this port are operating as expected.
• Off – No AP is detected on this port.
© .1996-2006 NETGEAR® . All rights reserved
29
3. Gigabit Uplink port
» The gigabit interface is not user-replaceable. Do not remove the
port cover plate.
© .1996-2006 NETGEAR® . All rights reserved
30
4. Serial port
» The port support RS-232 cable with RJ-45 connector.
» WFS709TP only support limited CLI access. No enable mode
access to CLI.
© .1996-2006 NETGEAR® . All rights reserved
31
Mounting the chassis
» Make sure that your rack environment meets the installation
requirements.
» Position the chassis in the equipment rack and align the
brackets’ mounting holes with the corresponding holes in the
rack frame.
» Use a Phillips or cross-head screwdriver to secure the chassis to
the rack with two 12-24 screws for each mounting bracket.
© .1996-2006 NETGEAR® . All rights reserved
32
Verifying the installation
» 1. Check the Power LED lights solid green immediately upon
power up and remains solid green during and after boot.
» 2. Check the fans to verify they are working.
» 3. Connect appropriate network cable.
» 4. Perform the initial software setup.
© .1996-2006 NETGEAR® . All rights reserved
33
Section 7: Software Installation/Update Process
© .1996-2006 NETGEAR® . All rights reserved
34
Initialize the switch for management
» Two methods to initialize the switch for management
• Using Web GUI – default IP address192.168.0.250
• Using serial console port
© .1996-2006 NETGEAR® . All rights reserved
35
Initialization – Web GUI
Default IP address – 192.168.0.250
© .1996-2006 NETGEAR® . All rights reserved
36
Initialization – Serial port
© .1996-2006 NETGEAR® . All rights reserved
37
Factory default reset
» Bring up the console and on the hyper-terminal type the following
commands
• Reboot the box and hit enter when you see “Hit any key to stop
autoboot” on the console.
• On the cpboot prompt enter
» cpboot > setenv cfgfile foo
» cpboot >saveenv
» boot
• The system will reset to factory default and when it boot up it will
go to the initial setup screen.
© .1996-2006 NETGEAR® . All rights reserved
38
Provisioning access point
» How access point communicate to the wireless switch?
© .1996-2006 NETGEAR® . All rights reserved
39
AP Communications to controller
» AP is attached to any switch port. AP is powered on and receives
DHCP address (or statically assigned).
» AP find the address of WFS709TP (DNS or broadcast).
» AP boot image from controller and create a PAPI (UDP 8211)
connection to controller. AP authenticates to controller and
creates a GRE tunnel between AP and controller.
» All client communicates to the AP are encapsulated in the GRE
tunnel and forwarded to the controller.
© .1996-2006 NETGEAR® . All rights reserved
40
AP boot sequence
» AP learn location ID from bootrom
» AP sends out DHCP request for IP address
» If DHCP response includes vendor option 43 (masterip), AP will use this
for master IP address. Netgear APs identify themselves with a vendor
class identifier set to NetgearAP in their DHCP request.
» If no vendor option specified, AP send “ADP” packet to multicast group
224.0.82.11.
» If no response to multicast ADP, AP sends “ADP” packet as L2/L3
broadcast.
» If no response, AP sends DNS query to server given by DHCP for
hostname “netgear-master”. AP will use this for Master IP address.
» AP sends messages to controller with its location ID.
» If needed, AP sends TFTP request to controller and downloads OS
image.
» Based on the AP’s location ID, the current controller may take control of
this AP or direct it to another controller.
» AP authenticates to controller and establishes GRE tunnel.
© .1996-2006 NETGEAR® . All rights reserved
41
Location ID
» Uniquely identifies APs
» Location ID indicates:
• Building
• Floor
• Specific AP
• [Building number].[Floor number].[AP number]
• [1-255].[1-255].[1-65536]
• For example, 1.1.1 (Building 1, 1st Floor, AP #1)
» Zero(0) is a wildcard:
• 1.0.0 – All AP in building 1
• 1.1.0 – All AP in building 1, 1st Floor)
© .1996-2006 NETGEAR® . All rights reserved
42
Unprovisioned AP
© .1996-2006 NETGEAR® . All rights reserved
43
Provision new access point
© .1996-2006 NETGEAR® . All rights reserved
44
Provision new access points
» Two methods to provision new access point
• Access point installation wizard
• Manual provisioning
© .1996-2006 NETGEAR® . All rights reserved
45
Provision AP
Configuration->Basic->Access Point Installation Wizard
© .1996-2006 NETGEAR® . All rights reserved
46
Access Point Installation Wizard
© .1996-2006 NETGEAR® . All rights reserved
47
Access Point Installation Wizard
© .1996-2006 NETGEAR® . All rights reserved
48
Access Point Installation Wizard
© .1996-2006 NETGEAR® . All rights reserved
49
Access Point Installation Wizard
© .1996-2006 NETGEAR® . All rights reserved
50
Access Point Installation Wizard
© .1996-2006 NETGEAR® . All rights reserved
51
Provision AP – manual
Maintenance->WLAN->Program AP
© .1996-2006 NETGEAR® . All rights reserved
52
Lab one – Initialize the wireless switch
© .1996-2006 NETGEAR® . All rights reserved
53
Lab two – Provision access point
© .1996-2006 NETGEAR® . All rights reserved
54
Section 8: Software Setup / Configuration
© .1996-2006 NETGEAR® . All rights reserved
55
Software Configuration
»
»
»
»
RF Planning
Guess Access
IDS – rogue AP detection and containment
Multiple controller and redundancy
© .1996-2006 NETGEAR® . All rights reserved
56
RF Planning
© .1996-2006 NETGEAR® . All rights reserved
57
RF Plan
» Use RF Plan as an initial tool to place APs
» RF Plan makes many assumptions and does not factor in building
construction materials (walls, doors, furniture, etc)
» Works well for typical office environments
» After installation, turn on ARM
» Update RF Plan with actual AP locations
© .1996-2006 NETGEAR® . All rights reserved
58
Pre-installation activities
» You will
• Create floor plan files to use for post-installation RF Plan use
» RF Plan will
• Provide number of AP/AM you will need for each floor/building
• Derive recommended location for AP/AM on the floor plans
© .1996-2006 NETGEAR® . All rights reserved
59
Required Information for RF Plan
»
»
»
»
»
»
Building (drawing) dimensions
Protocols (802.11a/g)
AP types
Desired data rate
Desired monitoring rate for Air Monitors
Floor maps in JPEG format
• Maximum 2048x2048 pixels
© .1996-2006 NETGEAR® . All rights reserved
60
Importing Floor Plans
Step 1 – Edit floor plan in a graphics editor
Step 3 – Scale pixels
per feet (or meters) against
known dimension
Step 2 – Move mouse to bottom right of image to measure picture (not Bldg) width
and height in pixels
© .1996-2006 NETGEAR® . All rights reserved
61
Sizing Floor Plans
Step 4 – Save floor
image File as JPG
Step 5 – Calculate image dimensions:
• Calculating pixels per feet (or meters)
against a known dimension
• Use that value to calculate dimensions
of JPG image width and length in feet
or meters
© .1996-2006 NETGEAR® . All rights reserved
62
Importing Floor Plans Best Practice
» Make sure the image is scaled. If image is not scaled and
proportional, triangulation and heat-map calculation will be
flawed.
» Leave some border to help triangulate WiFi devices to just
outside the building.
» For building with multiple floors, the rectangle size needs to
cover the same exact dimensions. For buildings with floors are
different shapes/dimension, it’s critical that the cropped area be
the same square footage for all floors and that the floors be
anchored against something such as elevator shafts.
© .1996-2006 NETGEAR® . All rights reserved
63
RF Plan – Create New building
Click Plan, then New Building
© .1996-2006 NETGEAR® . All rights reserved
64
RF Plan – Default Overview
Click Building Dimension
© .1996-2006 NETGEAR® . All rights reserved
65
RF Plan – Set building dimension
The inter floor height is used by RF Plan to allow APs on one floor to service users
on adjacent floors. If you do not wish RF Plan to factor in adjacent floors, set this
value to be very large (300).
© .1996-2006 NETGEAR® . All rights reserved
66
RF Plan – AP modeling spec.
Which bands to support? Which APs will be used?
These settings are on a per-building basis. If you have a mix of AP
types, choose the most common one.
© .1996-2006 NETGEAR® . All rights reserved
67
RF Plan
» Coverage
• Coverage is typically based on WLAN transmit rate
» Desired speed rate define estimated minimum connect speed
» The higher the rate, the smaller the coverage area, more APs required
» Capacity-based coverage is recommended for high capacity conference
or training rooms.
» Customer coverage is for deployments where the AP count is already
known
» Overlap
• 100% (Low) – best for open spaces – warehouses, etc.
• 150% (Medium) – best for office spaces
• 200% (High) – offer twice the minimum AP, high redundancy/performance
and dense deployments.
• Custom – allow specific overlap. Many office spaces work well with 120%
overlap.
© .1996-2006 NETGEAR® . All rights reserved
68
RF Plan – AM Modeling Parameters
Decide on AM coverage rates
Coverage rates for AMs refer to the rate at which an AM can
capture packets and will tell RF Plan how close to place AMs to
one another. If you will be using AMs purely for IDS purposes, use
the lowest rate values for the a and b/g radio.
© .1996-2006 NETGEAR® . All rights reserved
69
RF Plan – Building Planning
Click “Add New Floor”, then “Edit floor”
Browse to JPEG image and click “Apply”
© .1996-2006 NETGEAR® . All rights reserved
70
Edit Floor – Import Floor Plan
© .1996-2006 NETGEAR® . All rights reserved
71
RF Planning – Enlarge/Reduce Floor image
The zoom control enlarge or reduce
the floor image.
© .1996-2006 NETGEAR® . All rights reserved
72
RF Planning – Delete existing AP in plan
Delete and clear to start with
a clean deployment
© .1996-2006 NETGEAR® . All rights reserved
73
AP Planning - Initialize
Clicking on initialize will cause the RF
plan to place AP on the map. Clicking on
“Start” cause RF Plan to optimize the
placement of the APs.
If you wish to add more AP than what RF
Plan recommend, DO NOT click initialize
again. This will reset the drawing to the
recommended and erase any manually
added AP.
© .1996-2006 NETGEAR® . All rights reserved
74
AP Planning - Start
© .1996-2006 NETGEAR® . All rights reserved
75
AP Planning – Assign AP Name
» Use AP names
that help identify
and locate the
APs.
» Define channel
and power
settings to
override auto
settings.
» Use note session
for comments.
© .1996-2006 NETGEAR® . All rights reserved
76
AM Planning
© .1996-2006 NETGEAR® . All rights reserved
77
New area
» “Don’t care” area tell RF Plan to not deploy AP in that area, and
that you don’t care if there is RF coverage in that space or not.
» “Don’t Deploy” area tell RF Plan to not place APs in that area but
that you do want as much RF coverage in that area as possible.
© .1996-2006 NETGEAR® . All rights reserved
78
AP Planning – New Area
© .1996-2006 NETGEAR® . All rights reserved
79
AP Planning – New Area
Drag and drop the area to
desired location
© .1996-2006 NETGEAR® . All rights reserved
80
AP Planning – New Area
After drag and drop the
area into desired location,
click initialize and start to
re-calculate.
© .1996-2006 NETGEAR® . All rights reserved
81
Optimize AP locations
• Drag and drop APs as needed (conference rooms, hallways, etc)
• Avoid metal and non-RF friendly obstacles
• New APs can be manually added if needed.
© .1996-2006 NETGEAR® . All rights reserved
82
Save Plan Information
Review and save the RF Plan
• Verify the building information, AP and AM count and coverage rates
• Save the building info
© .1996-2006 NETGEAR® . All rights reserved
83
RF Plan – Exporting Plan
» Used to back up and
move RF Plan Info
» Export/Import
between controllers
or between offline
version and
controller
» Click on include
images if any images
are present
» Multiple buildings
can be saved into a
single RF Plan
Export file
© .1996-2006 NETGEAR® . All rights reserved
84
RF Plan - Deployed
To see the heat map, enable
ARM and let it run for a
few minutes.
© .1996-2006 NETGEAR® . All rights reserved
85
Lab three – Use RF Plan to create plan
© .1996-2006 NETGEAR® . All rights reserved
86
RF Management
© .1996-2006 NETGEAR® . All rights reserved
87
Post-installation Activities
» Review dynamic heat maps and validate
coverage
» Track location of WLAN devices such as
clients, Interfering and Rogue APs
© .1996-2006 NETGEAR® . All rights reserved
88
Dynamic Heat Maps
• Near real-time view of RF
coverage and interference
• Information reported by
APs and AMs
• Helps identify coverage
holes and interference
© .1996-2006 NETGEAR® . All rights reserved
89
Location Tracking
(continued)
Two Web UI options to locate APs and clients
1. Monitor
•
Viewing client/AP info and clicking on “Locate”
2. RF Plan
•
Performing a search for a specific client wireless
MAC or AP BSSID
© .1996-2006 NETGEAR® . All rights reserved
90
Location Tracking: Monitor
• Monitor -> Switch -> Clients/APs
• Select and click Locate button
• At least three devices must be on the same
channel to triangulate a device (AP or AM)
© .1996-2006 NETGEAR® . All rights reserved
91
Location Tracking: Monitor
(continued)
• Click Locate to show
either contour shapes
(shown here) and/or
rings
• “Keep data for” should
be set to maximum of
10 minutes for best
results
• The more APs/AMs on
same channel as the
device the better the
result will be
© .1996-2006 NETGEAR® . All rights reserved
92
Location Tracking: MAC
Copy client MAC address or AP BSSID from Web
UI screen or from CLI
© .1996-2006 NETGEAR® . All rights reserved
93
Location Tracking: MAC
(continued)
Use the MAC/BSSID to select the device
© .1996-2006 NETGEAR® . All rights reserved
94
Location Tracking: MAC
(continued)
• Use “Add Device” to enter
the device MAC address
• Click OK to locate
© .1996-2006 NETGEAR® . All rights reserved
95
Calibration
» Active calibration allows the switch to learn which APs and AMs
are in rage of each other and adjust their channel and power
settings for optimum performance.
» Purpose:
• To learn and implement optimal channel plan.
• To learn and implement optimal power level plan.
© .1996-2006 NETGEAR® . All rights reserved
96
Adaptive Radio Management (ARM)
» Adaptive Radio Management is a real time dynamic calibration
mechanism.
» ARM allow each AP to figure out its own best channel and power
settings.
» ARM, if enabled, is a continuous process. It allows the system to
detect changes in the RF and to dynamically react to maintain the
most optimized RF system possible.
© .1996-2006 NETGEAR® . All rights reserved
97
Enable ARM
Configuration->Advanced->WAN->RADIO
Enable ARM Scanning with single band
© .1996-2006 NETGEAR® . All rights reserved
98
How ARM works
» APs constantly scan other channels during dead intervals
» AP analyzes BSSIDs and interference seen on current and other
channels
» AP reports back to controller when a better channel is found
» “Better” is defined as “least number of APs seen on a channel”
or “better SNR statistics”
» Controller analyzes reports from APs and make calculations
based on known WLAN topology database
» If controller finds no conflicts, it will instruct AP to move to the
new channel
» Dampening factor prevents channel “flapping”
© .1996-2006 NETGEAR® . All rights reserved
99
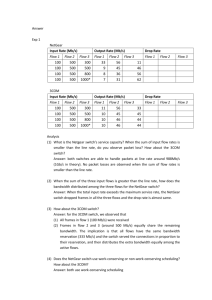
Power Level adjustment
» Radio power levels are adjustable between 0 and 4
» 4 is the highest
» Calibration will automatically set the power level to avoid interference
with other APs
» Power levels will be dynamically adjusted to fill in holes is an AP fails
B/G Radio
A Radio
Level
dB
mW
Level
dB
mW
0
0
1
1
0
1
1
11
13
2
9
8
2
14
25
3
12
16
3
17
50
4
15
32
4
20
100
5
18
63
© .1996-2006 NETGEAR® . All rights reserved
100
Channel Selection
» APs operate most efficiently when they are the only AP on the
channel
» Calibration will automatically assign channels to each AP to
minimize interference
» Only channel approved by the appropriate country regulations
will be assigned
» For example, in North America this is
• 802.11b/g = 1, 6, 11
• 802.11a = 36, 40, 44, 48, 52, 56, 60, 64, 149, 153, 157, 161
© .1996-2006 NETGEAR® . All rights reserved
101
Before Calibration
•All .11a radios on
channel 36
•All .11g radios on
channel 1
•All power levels
at 50%
© .1996-2006 NETGEAR® . All rights reserved
102
After Calibration
•Network learns
optimal channel
plan to avoid
interference
•Learns optimal
power levels to
avoid coverage
holes
© .1996-2006 NETGEAR® . All rights reserved
103
ARM assignment options
» Disabled
• Disables ARM calibration and reverts AP back to default channel
and power settings
» Single band
• Enable the AP to change channels, in same band, and transmit
power
» Multi band
• Not supported (for future use)
» Maintain
• Cause AP to hold last used channel and power settings. Useful for
customers concerned with APs changing channel/power during
user.
© .1996-2006 NETGEAR® . All rights reserved
104
ARM Options
» ARM Scanning
• Enable ARM scanning
» ARM Client Aware
• Prevent AP from changing channel if clients are associated.
» ARM Rogue AP Aware
• If no other APs are on the same channel as the rogue or no AM
are available the AP can change channel to contain a rogue. An
AP can always contain a rogue on the same channel.
» ARM VoIP Aware
• Pause ARM scanning when a VoIP call is detected (SIP, SCCP,
SVP, Vocera)
» ARM Multi Band Scan
• Allows APs to scan across bands for Rogue detection.
© .1996-2006 NETGEAR® . All rights reserved
105
Air Monitor
Turn an AP into Air monitor
© .1996-2006 NETGEAR® . All rights reserved
106
RF Management
Calibration
© .1996-2006 NETGEAR® . All rights reserved
107
RF Management
Calibration
© .1996-2006 NETGEAR® . All rights reserved
108
RF Management
Calibration
© .1996-2006 NETGEAR® . All rights reserved
109
RF Management
Optimization – Self Healing
© .1996-2006 NETGEAR® . All rights reserved
110
RF Management
Optimization – Load Balancing
© .1996-2006 NETGEAR® . All rights reserved
111
RF Management
Protection - DoS Protection
© .1996-2006 NETGEAR® . All rights reserved
112
RF Management
Monitoring – Coverage hole detection
© .1996-2006 NETGEAR® . All rights reserved
113
RF Management
Monitoring – Interference detection
© .1996-2006 NETGEAR® . All rights reserved
114
RF Management
Monitoring – Event Thresholds
© .1996-2006 NETGEAR® . All rights reserved
115
RF Management
Monitoring - Advanced
© .1996-2006 NETGEAR® . All rights reserved
116
Encryption and Authentication
© .1996-2006 NETGEAR® . All rights reserved
117
Module Overview
» Authentication
•
•
•
•
SSID
MAC
Captive Portal
802.1x
» Encryption
• Layer 2 vs. Layer 3
» Wireless security protocols
• WPA
• 802.11i/WPA 2.0
© .1996-2006 NETGEAR® . All rights reserved
118
Security Overview
Wireless security standards and protocols fall into
3 categories:
» Encryption
• Ensures privacy of data transmitted through the air
• Can be done at Layer 2 (WEP, TKIP, AES)
» Authentication
• Ensures that only authorized users with proper credentials
are allowed to use the network
• Authentication methods include EAP, captive portal.
» Access Control
• Provides a policy enforcement structure to control the traffic
of authorized users, including networks, bandwidth, time of
day, and protocols
© .1996-2006 NETGEAR® . All rights reserved
119
Authentication
Authentication Overview
Information Security has 3 goals:
• Confidentiality
• Integrity
• Availability
» Authentication assists with confidentiality and
integrity
» Ensures “you are who you say you are”
» Necessary for both client and network/server
© .1996-2006 NETGEAR® . All rights reserved
121
Authentication Methods
(continued)
• WFS709TP supports a variety of authentication
methods.
• Authentication methods are configured at:
• Configuration -> Security -> Authentication Methods
© .1996-2006 NETGEAR® . All rights reserved
122
Authentication Methods
(continued)
» Authentication methods are used by the
WFS709TP to authenticate to wireless access.
© .1996-2006 NETGEAR® . All rights reserved
123
Authentication Methods
» SSID
» MAC
» Captive Portal
» 802.1x
• EAP
© .1996-2006 NETGEAR® . All rights reserved
124
SSID Authentication
» A user can be authenticated simply by associating
with a given SSID
» A policy is created such that anyone associating with
a given SSID is granted certain permissions
» Weak encryption offerings (WEP), and high
administrative overhead (creating a separate SSID for
each user group) make SSID a poor choice
» No real security value
© .1996-2006 NETGEAR® . All rights reserved
125
SSID Authentication Configuration
© .1996-2006 NETGEAR® . All rights reserved
126
SSID Authentication Configuration
(continued)
© .1996-2006 NETGEAR® . All rights reserved
127
MAC Authentication
» A user’s MAC address can be used to establish Identity
» However, MAC addresses can be spoofed by an attacker
» Useful for devices that cannot run authentication software
(handheld scanners, printers, etc)
© .1996-2006 NETGEAR® . All rights reserved
128
MAC Authentication
© .1996-2006 NETGEAR® . All rights reserved
(continued)
129
Internal Database
» Built in on the controller
» Simple authentication option
» Can be used with PEAP-offload
© .1996-2006 NETGEAR® . All rights reserved
130
Internal Database
© .1996-2006 NETGEAR® . All rights reserved
(continued)
131
Captive Portal
» Web-based authentication method (SSL)
» Enabled by default
» Typically found in Public Hotspots,
Universities
» User associates (open or static WEP),
receives IP address.
» Launches web browser, forced to
authentication web page
» May authenticate against internal or external
server
» Can also be used with Sygate On Demand
Agent (SODA) for client integrity
» After successful authentication, Role
assigned
132
© .1996-2006 NETGEAR® . All rights reserved
Captive Portal
© .1996-2006 NETGEAR® . All rights reserved
(continued)
133
Captive Portal Login
© .1996-2006 NETGEAR® . All rights reserved
134
Customized Captive Portal
© .1996-2006 NETGEAR® . All rights reserved
135
802.1x
» Standard protocol for authenticating user *prior* to
granting access to L2 media
» Utilizes EAP (Extensible Authentication Protocol)
• Evolved from PPP, used for wired network authentication -
unencrypted
• Several types of “Wireless” EAP
»
»
»
»
Cisco LEAP
EAP-TLS
PEAP
EAP-TTLS
• These sub-types intended for use on untrusted networks such as
wireless
© .1996-2006 NETGEAR® . All rights reserved
136
EAP Definitions
Supplicant: client station
Authenticator: WFS709TP
Authentication Server: RADIUS Server
© .1996-2006 NETGEAR® . All rights reserved
137
EAP Overview
1. Supplicant communicates with authentication server through
the authenticator
2. Authenticator reformats 802.1x to RADIUS and forwards to
Authentication Server
3. EAP exchange happens between supplicant and authentication
server
4. On success, server delivers EAP Success via RADIUS message
5. Details often hidden from authenticator
6. The WFS709TP is EAP agnostic
© .1996-2006 NETGEAR® . All rights reserved
138
EAP Exchange
EAP Exchange
(Controller used as pass-through doesn’t have to know EAP type)
Trusted
Network
802.11 a/b/g
Secured Link
Client
© .1996-2006 NETGEAR® . All rights reserved
WFS709TP
Authentication
Server
139
802.1x Process
802.1x Access Control – Sequence of events
Request Identity
Response credentials
Authentication Server
Authenticator
Client
Response Identity
Response Identity (anonymous)
PEAP Start
Certificate
Client Key exchange
Cert. verification
Request credentials
Success
© .1996-2006 NETGEAR® . All rights reserved
140
EAP Flavors
LEAP
» Cisco proprietary
» Dynamic WEP
» Has been broken. Not recommended for current deployment
EAP-FAST
» Cisco proprietary
» Uses a PSK in phase 0 to obtain a PAC file, PAC is used as credentials
on network
» Subject to man in the middle attacks; poor Windows AD integration
EAP-TLS (EAP with Transport Layer Security)
»
»
»
»
RFC 2716 - based on SSL
Uses both client and server certificates
Provides for mutual authentication
Supported by Windows 2000, XP, 3rd party clients
© .1996-2006 NETGEAR® . All rights reserved
141
EAP Flavors
(continued)
EAP-PEAP
»
»
»
»
Based on TLS
Hides EAP exchange
Requires both server and client authentication
Developed by Microsoft, Cisco and RSA Security
EAP-MD5
» Early implementation of EAP using only MD5 hash with no encryption
» Rarely used
EAP-TTLS
» Similar to PEAP, but allows for any EAP authentication protocol
» Requires 3rd party client
» Developed by Funk Software
© .1996-2006 NETGEAR® . All rights reserved
142
802.1x Configuration
© .1996-2006 NETGEAR® . All rights reserved
143
PEAP-Offload
EAP Exchange
Trusted
Network
802.11 a/b/g
Secured Link
Client
NAS
Authentication
Server
© .1996-2006 NETGEAR® . All rights reserved
144
PEAP Offload
(continued)
802.1x termaination
© .1996-2006 NETGEAR® . All rights reserved
145
Encryption
WEP
» Wired Equivalent Privacy
» Based on RC4 stream cipher
» Part of 1997 802.11 specification
» WEP was defeated in 2000
» Keys made up of 24-bit Initialization Vector
(IV) and either a 40-bit or 104-bit key
» Usually statically configured on both AP and
client
• Makes key rotations difficult
• Can be dynamically assigned through 802.1x - LEAP
© .1996-2006 NETGEAR® . All rights reserved
147
WEP (cont.)
» Static WEP vulnerabilities include:
• No privacy between users - same keys
• Weak IV’s lead to linear key discovery
• No authentication mechanism
• Vulnerable to Man-in-the-Middle/replay attacks
» Dynamic WEP an improvement
• Keys generated by authentication server through 802.1x -
unique to each user
• Keys rotated periodically
• Keys still able to be attacked directly, just takes longer
© .1996-2006 NETGEAR® . All rights reserved
148
WPA/TKIP
» WPA (Wi-Fi Protected Access) is an industrysponsored interim security standard
• Subset of 802.11i RSN (Robust Security Network)
• Dramatic improvement over WEP
» WPA consists of 2 parts:
• 802.1x Authentication
• TKIP encryption (Temporal Key Integrity Protocol)
» TKIP
• Provides per-packet key mixing, strong MIC (Message Integrity
Check), extended IV, and a re-keying mechanism
• Based on RC4 - only requires a software upgrade for most
devices
• Can use a Pre-Shared Key (PSK) like WEP or dynamic keys
through 802.1x (recommended)
© .1996-2006 NETGEAR® . All rights reserved
149
WPA Disadvantages
Major drawbacks of WPA include:
• Backwards-compatibility limits crypto operations
» Encryption is still ultimately based on RC4, as is WEP/TKIP
» Not FIPS-certified or approved for US government use
• WPA designed as an interim solution before 802.11i
• Not compatible with pure 802.11i/RSN environments
© .1996-2006 NETGEAR® . All rights reserved
150
802.11i/Wi-Fi Protected Access 2.0
» Amendment to the original 802.11 standard
» Specifies security mechanisms for wireless networks (Wi-Fi)
Major 802.11i components include:
» 802.1X for authentication
» RSN for keeping track of associations
» AES-based CCMP encryption
» Four-way authentication handshake
© .1996-2006 NETGEAR® . All rights reserved
151
xSec
xSec enjoys all of the same security benefits as
802.11i with the addition of higher levels of
encryption and FIP compliancy
» xSec functionality is same as 802.11i with:
• Wired and wireless functionality
• Higher encryption levels
Major xSec components are:
•
•
•
•
802.1X for authentication
RSN for keeping track of associations
AES-CBC-256 and HMAC-SHA1
Four-way authentication handshake
© .1996-2006 NETGEAR® . All rights reserved
152
Configuring 802.1x/802.11i
© .1996-2006 NETGEAR® . All rights reserved
153
Wireless Security Best Practices
• Use WPA or WPA2 wherever possible
• Migrate to full 802.11i as drivers and equipment allow
• Leverage firewall policies to protect legacy networks
• Pure Windows environments: use EAP-PEAP
• Pure Windows rollouts with existing PKI: TLS is an
option for greater security
• Always validate server certificate to prevent man in the
middle attacks
© .1996-2006 NETGEAR® . All rights reserved
154
EAP Methods Comparison
MD5
TLS
TTLS
PEAP
LEAP
FAST
Client-side
authentication/certificate
required
No
Yes
No
No
No
No (PAC)
Server-side
authentication/certificate
required
No
Yes
Yes
Yes
No
No (PAC)
Authentication method
One-way
Mutual
Mutual
Mutual
Mutual
Mutual
Deployment complexity
Low
High
Moderate
Moderate
Moderate
Moderate
to high
Security strength
Low
Highest
High
High
Low
Medium
to high
Feature/Benefit
© .1996-2006 NETGEAR® . All rights reserved
155
WFS709TP RADIUS Compatibility
MD5
TLS
TTLS
PEAP
LEAP
FAST
Cisco ACS 3.2 and higher
Yes
Yes
No
Yes
Yes
Yes
Microsoft IAS
Yes
Yes
No
Yes
No
No
Funk Steel Belted
RADIUS
Yes
Yes
Yes
Yes
Yes
Yes
InfoBlox
Yes
Yes
No
Yes
Yes
No
FreeRADIUS
Yes
Yes
No
Yes
Yes
No
Radiator
Yes
Yes
Yes
Yes
Yes
No
RADIUS Server
© .1996-2006 NETGEAR® . All rights reserved
156
Lab four
Create SSID and test client association
© .1996-2006 NETGEAR® . All rights reserved
157
Guest Access
© .1996-2006 NETGEAR® . All rights reserved
158
Guest Access
» Guess access can be created from the Basic or Advanced
configuration menu.
© .1996-2006 NETGEAR® . All rights reserved
159
Guest Access
Configuration->Basic->WLAN
© .1996-2006 NETGEAR® . All rights reserved
160
Guest Access
Configuration->Advanced
» 1. Add user to internal database for authentication
» 2. Create guest SSID
» 3. Enable Captive Portal
© .1996-2006 NETGEAR® . All rights reserved
161
Add guest user to internal database
Configuration->Advanced->Security->AAA Servers
© .1996-2006 NETGEAR® . All rights reserved
162
Create Guest SSID
Configuration->Advanced->WAN->Network
© .1996-2006 NETGEAR® . All rights reserved
163
Enable Captive portal
Configuration->Advanced->Security->Authentication->Captive Portal
Enter guest SSID
© .1996-2006 NETGEAR® . All rights reserved
164
Captive Portal Login
DNS must be operational to access the captive portal page
© .1996-2006 NETGEAR® . All rights reserved
165
Captive Portal Authenticated
© .1996-2006 NETGEAR® . All rights reserved
166
Authenticated guest
© .1996-2006 NETGEAR® . All rights reserved
167
Lab five – Create guess login and captive portal
© .1996-2006 NETGEAR® . All rights reserved
168
Multiple VLAN/ESSID support
© .1996-2006 NETGEAR® . All rights reserved
169
Scenario
»
»
»
»
Two VLANs: Corp, Guest
DHCP provided by Layer3 switch
Two ESSID: Corp, Guest
Guest ESSID not allow to access
Corp but allow to access Internet
Internet
NETGEARTM
Cable/DSL VPN Router
PWR TEST
INTERNET
LNK
ACT
LOCAL
1
2
3
4
5
6
7
8
MODELFV318
100
LNK/ACT
Router
TM 24 PORT
10/100 Mbps Fast Ethernet Switch
100Mbps
1
12
Link FDX
Green = Rx/Tx, Yellow = Collision
100Mbps
24
13
Green = Rx/Tx,Yellow = Collision
NETGEAR
1
Bay Networks
13
Power
MODELFS524
12
Normal / Uplink
Layer3 switch
24
VLAN Trunk
NETGEARTM
Cable/DSL
VPN Router
INTERNET
PWR
TEST
LNK
ACT
LOCAL
1
2
3
4
5
6
7
8
MODELFV 318
100
LNK/ACT
WFS709TP
NETGEAR
Internet Access Firewall Router
PWR TEST
INTERNET
LNK
ACT
LOCAL
1
2
3
4
100
LNK/ACT
MODELFR314
NETGEAR
Internet Access Firewall Router
PWR TEST
INTERNET
LNK
ACT
LOCAL
1
2
3
4
100
LNK/ACT
MODELFR314
Access Point
© .1996-2006 NETGEAR® . All rights reserved
170
Multiple VLAN/ESSID
»
»
»
»
»
»
»
1. Setup VLAN and trunk port on switch.
2. Configure DHCP pools (switch / WFS709TP / DHCP server)
3. Create trunk port on WFS709TP
4. Create VLAN on WFS709TP
5. Define ESSID with associated VLAN on WFS709TP.
6. Create ACL on switch.
7. Create static routes on router for internal subnets.
© .1996-2006 NETGEAR® . All rights reserved
171
Create Trunk port on wireless controller
Enable trunk port and allow all VLAN
© .1996-2006 NETGEAR® . All rights reserved
172
Create VLAN on wireless controller
© .1996-2006 NETGEAR® . All rights reserved
173
Define ESSID associated with VLAN
Assign VLAN to ESSID
© .1996-2006 NETGEAR® . All rights reserved
174
Lab six – Multiple BSSID with VLAN and guess access
© .1996-2006 NETGEAR® . All rights reserved
175
IDS
© .1996-2006 NETGEAR® . All rights reserved
176
Overview
• Threats and countermeasures
» WLAN Discovery
•
Active/Passive
» DoS Attacks
» Surveillance
» Impersonation/Man-in-the-Middle
» Intrusion
•
Client-Client
• Client-Network
» Rogue Detection and Containment
© .1996-2006 NETGEAR® . All rights reserved
177
Probing/Network Discovery
» Probing not an “attack”, but may precede an attack
» Often, probes are people looking for free access (War Driving)
» Can be active or passive
© .1996-2006 NETGEAR® . All rights reserved
178
Passive Probe Detection and Prevention
» Behavior
• Station listens for AP beacons
• Most operating systems perform this by default and present the user
with a list of “available networks”
» Detection
• Impossible to detect - station is not transmitting
• Enabling hidden SSIDs will stop AP beacons but monitoring legitimate
traffic will reveal SSID
• May discourage the casual War Driver
© .1996-2006 NETGEAR® . All rights reserved
179
Active Probe Detection and Prevention
» Behavior
• Station transmits probe-request frame with a null ESSID (Broadcast
BSSID, empty ESSID)
• APs receiving this request will send a probe response indicating their
SSID and other capabilities
» Detection
• Some tools (Netstumbler, Wellenreiter) may be detected through
signature analysis
• Disabling broadcast probe response will prevent Aps from responding
to active probes
• SSID will still be revealed through monitoring legitimate traffic
© .1996-2006 NETGEAR® . All rights reserved
180
Probing Event Reports
© .1996-2006 NETGEAR® . All rights reserved
181
Denial of Service Attacks
Two types of Denial of Service (DoS) attacks:
• Layer 1
• Layer 2
© .1996-2006 NETGEAR® . All rights reserved
182
Layer 1 Jamming Attacks
» Involves sending sufficient RF noise to
drown out any 802.11 communication
» Illegal in most countries – but difficult to
enforce because the jammer can be hard
to find
» YDI “DoS-in-a-box” costs $695
© .1996-2006 NETGEAR® . All rights reserved
183
Layer 1 Jamming Detection
» Aruba Air Monitors and APs constantly measure signal-to-noise ratio (SNR)
» Interference Detection logs can be correlated to detect a jamming attack in
progress
» If SNR drops below a certain threshold on a single channel, ARM will be able to
react and move to a new channel
» If SNR drops below a certain threshold across a wider spectrum, the
administrator can be automatically notified that a jamming attack is taking
place
© .1996-2006 NETGEAR® . All rights reserved
184
Interference Detection
© .1996-2006 NETGEAR® . All rights reserved
185
Layer 2 Attacks
» DoS Attacks that work within the 802.11 protocol framework
» Examples include associate/disassociate attacks, authenticate/deauthenticate
attacks, network overload attacks, and NIC firmware flaws
» An attacker may try to disconnect clients from an AP by sending deauthenticate or disassociate frames with a spoofed source address. This often
signals an attempted man-in-the-middle attack
» In the US, these attacks are not prohibited by the FCC, but are covered by other
information security laws (Communications Act of 1934)
© .1996-2006 NETGEAR® . All rights reserved
186
L2 Client Attack
»
»
»
»
Enable “Station DoS Prevention” (stm sta-dos-prevention)
Generates a security event
Quarantines the station from the network for [sta-dos-block-time] seconds.
Prevents a man-in-the-middle attack from taking place.
© .1996-2006 NETGEAR® . All rights reserved
187
L2 AP Attack
» Ignores attacks against the AP with DoS protection enabled (stm dosprevention).
» Switch will ignore all disassociate/deauthenticate frames.
» Idle stations age out according to sta-ageout-interval parameter
© .1996-2006 NETGEAR® . All rights reserved
188
DoS Protection
© .1996-2006 NETGEAR® . All rights reserved
189
Layer 2 Event Reporting
© .1996-2006 NETGEAR® . All rights reserved
190
Other Layer 2 Attacks
» EAP Start Floods
• An attacker may try to overwhelm the authentication server in an 802.1x
network by sending EAP handshake floods
» WFS709TP will detect this as a rate anomaly
» FakeAP
• An attacker may run a tool such as “FakeAP” that generates a large
number of beacons with different BSSIDs
» Tool was developed for stress-testing wireless networks and
to confuse War Drivers by making clients think there are a
large number of APs – same tool can be used as a DoS
attack
» WFS709TP will detect FakeAP and generate a security
event
© .1996-2006 NETGEAR® . All rights reserved
191
Other Layer 2 Attacks
(continued)
» Association Floods
• An attacker may try to fill an AP’s association table using association or
authentication floods
» Rate anomaly detection will sense an abnormally high
number of associate/authenticate frames coming from the
same physical location
» Stations that associate but send no data will be aged out
after 30 seconds
» Probe Floods
• An attacker may send a high number of probe request frames to
consume resources on the AP
» Rate anomaly detection will sense and report this
© .1996-2006 NETGEAR® . All rights reserved
192
Surveillance
» The nature of Wi-Fi makes surveillance easy – all that is required is an
802.11 NIC and software to decode frames
» Surveillance leads to exposure of sensitive information, network
topology information, addressing, client information, and in some cases,
authentication information
© .1996-2006 NETGEAR® . All rights reserved
193
Preventing Surveillance
» Strong encryption is the key to defeating surveillance
» Static WEP is NOT strong encryption
• WEP is sufficient to discourage the casual War Driver and cause them
to go elsewhere
• WEP can be broken in as little as 4 hours on a busy network just
through monitoring alone – active attacks (like “reinj.c”) can break it in
30-60 minutes
» Use WPA 1.0 with dynamic TKIP for now, and WPA 2.0/802.11i when
equipment supports it.
• If this is not possible, at a minimum use dynamic WEP and a strongly
encrypted L3 VPN
© .1996-2006 NETGEAR® . All rights reserved
194
A Note on Cracking WEP
» WEP is broken, but is better than no encryption at all
» Deploying an Aruba network significantly reduces an attacker’s ability to
crack WEP
• WEP cracking tools (Airsnort, WEPcrack) rely on packets with weak
initialization vectors (IVs) in order to conduct analysis
• Aruba controllers will not generate packets with weak IVs – thus all
downstream packets will be unusable for cracking purposes
• Clients will still generate weak IVs – some percentage of client traffic
will contain packets with weak IVs
• A determined attacker will eventually crack the WEP key – though it
may take weeks using client traffic alone
© .1996-2006 NETGEAR® . All rights reserved
195
Impersonation Attacks
» Pretending to be someone you are not
• Could be a client impersonating another client
• Could be a client impersonating an AP
• Could be an AP configured with your enterprise SSID
© .1996-2006 NETGEAR® . All rights reserved
196
Impersonation Attacks
» In order for an impersonation attack to succeed in a useful way, the
attacker must have already cracked the Layer 2 encryption key
• Moral of this story: Don’t use static WEP
• If WEP is required, use dynamic WEP with 1-minute re-keying intervals
• If you must use static WEP, supplement it with a L3 VPN technology such
as IPSEC or PPTP
© .1996-2006 NETGEAR® . All rights reserved
197
Client Impersonation Attacks
»
»
»
Client impersonation attacks involve taking the MAC address and/or IP
address of a valid wireless station
End goal: Gain access to the network while appearing to be an authenticated
and valid user
Three types possible:
1) Use DoS attack to remove valid station from the network.
2) Leave valid client alone, and send packets to the network pretending to be that
client
3) Wait for the valid client to shut down, then assume its MAC address and IP
address
© .1996-2006 NETGEAR® . All rights reserved
198
DoS Client Impersonation
• Use DoS to get them “out of the way” by getting them to associate to
another AP (or a fake AP) on a different channel
» Aruba will quarantine wireless clients following a de-
auth attack
» Air Monitors will detect a non-valid AP using the
SSID of the valid network and will prevent clients
from connecting to it
© .1996-2006 NETGEAR® . All rights reserved
199
Share the Air Client Impersonation
» The “share the air” attack – leaving valid client on the network while
impersonation takes place
• Aruba supports 802.11 sequence number analysis (ids-policy
sequence-check enable) to detect this type of attack
» Possible, though difficult, to overcome sequence number
analysis
• Client itself will often detect this attack, displaying “duplicate IP address”
messages
• TCP cannot be used here – the valid client will receive TCP packets it
does not recognize, and will send a TCP RST
© .1996-2006 NETGEAR® . All rights reserved
200
MAC Address Spoofing Detection
© .1996-2006 NETGEAR® . All rights reserved
201
Off-Air
» Wait for Client
valid clientImpersonation
to shutdown, then impersonate
• Most clients never send a disassociate message when they shut down
– leaving their association ID active in the AP
• An attacker could watch for a client shutdown (NetBIOS sessions
closing, DHCP release, person walking out the front door, etc.) and then
assume the client’s association ID and MAC/IP addresses
• Use of strong encryption will prevent this attack
» WPA (802.1x with TKIP)
» IPSEC/PPTP VPNs
© .1996-2006 NETGEAR® . All rights reserved
202
AP Impersonation Attacks
» AP Impersonation
• Any time an unauthorized device is advertising itself as an AP with a
valid enterprise SSID, Aruba supports the ability to launch a de-auth
attack against this AP
» Air Monitors perform the monitoring function, and
also generate de-auth frames
• This prevents “honey pot” attacks – an attacker sitting outside the
building advertising an enterprise SSID and attempting to lure
enterprise clients to connect with it
» A honey pot attack is normally a prelude to some
other type of attack, such as man-in-the-middle or
client vulnerability probing
© .1996-2006 NETGEAR® . All rights reserved
203
Rogue Detection and Containment
© .1996-2006 NETGEAR® . All rights reserved
204
Rogue APs, Ad-Hoc Networks, and Bridges
» Rogue APs and ad-hoc networks are typically set up by employees who do not
understand the security risks
» Rogue APs represent one of the single largest threats to network security
• A rogue AP in an office, with default configuration parameters, is no different
than an Ethernet jack on the outside of a building
» Ad-Hoc networks can be dangerous because they may turn a PC into a
wireless-wired bridge
• There is no security in an ad-hoc network – anyone can join one
• If the PC is bridging between network interfaces, an ad-hoc network is just like a
rogue AP
» Wireless bridges can expose the network in the same way that rogue APs do
• Bridges are relatively rare
© .1996-2006 NETGEAR® . All rights reserved
205
Ad-Hoc Network and Bridge Detection
» Air Monitors constantly scan the air looking for “deviant topologies”
• Ad-hoc networks transmit all 802.11 frames with the “ToDS” and
“FromDS” bits in the header set to 0
• Wireless bridges transmit all 802.11 frames with the “ToDS” and
“FromDS” bits in the header set to 1
» When an ad-hoc network or wireless bridge is detected, a security event
notification is generated
© .1996-2006 NETGEAR® . All rights reserved
206
Ad-Hoc Network Protection
» Configuration/WLAN Intrusion Detection/Policies/Ad hoc Network
© .1996-2006 NETGEAR® . All rights reserved
207
Rogue AP Detection and Containment
» Aruba supports automatic detection and classification of rogue APs
• APs are first detected on the wireless side as “interfering” – meaning
that they appear in the radio spectrum
• Air Monitors constantly compare MAC addresses between the wireless
and wired sides of the network. If a match is found, a rogue AP is
present
• Rogue APs are automatically shut down through a DoS attack against
them
© .1996-2006 NETGEAR® . All rights reserved
208
Classification
Corporation with WFS709TP
Neighboring
Company or
Public Hotspot
Valid
Interfering
Mobility Controller
Known Interfering
BACKBONE
Parking Lot
© .1996-2006 NETGEAR® . All rights reserved
Rogue
209
Rogue AP Detection
» WFS709TP IDS security event generated
» Syslog message and SNMP trap sent
© .1996-2006 NETGEAR® . All rights reserved
210
Rogue AP Detection
© .1996-2006 NETGEAR® . All rights reserved
211
Locating Rogue APs
Rogue
AP
© .1996-2006 NETGEAR® . All rights reserved
Air Monitors
and/or APs
212
Rogue AP/Station Location
© .1996-2006 NETGEAR® . All rights reserved
213
Rogue AP Configuration
Configuration/WLAN Intrusion Detection/Rogue AP
© .1996-2006 NETGEAR® . All rights reserved
214
Configuring an Air Monitor
» To convert an AP to an AM, you must first create a location describing
the specific AP you wish to convert
» From the Web UI, select:
• Configuration/WLAN/Advanced
• Click “Add” and specify the AP in x.x.x format
• Select the radio to change, click “Air Monitor”, then “Apply”
© .1996-2006 NETGEAR® . All rights reserved
215
IDS Best Practices
» Always start with detection first
• Recommended start:
»
»
»
»
»
Rogue AP detection (on by default)
Ad hoc detection
Fake AP detection
AP impersonation
Signature detection
» Add protection/countermeasures later
• Take time to understand what is triggering events
• Might be legitimate users/devices
» Create baseline prior to threshold setting changes
• Allows for evaluation of usefulness
© .1996-2006 NETGEAR® . All rights reserved
216
Security
Firewall Settings
© .1996-2006 NETGEAR® . All rights reserved
217
RF Policy
© .1996-2006 NETGEAR® . All rights reserved
218
Lab Seven – Rogue AP detection and containment
© .1996-2006 NETGEAR® . All rights reserved
219
Multiple Controller and Redundancy
© .1996-2006 NETGEAR® . All rights reserved
220
Multi controller
» For large multi-site deployments, multiple controllers may be
required.
» WFS709TP uses a Master-Local architecture
• All configuration and management is handled by master controller.
• AP boot either from the master controller or a local controller, and
are assigned to a local controller for processing based on location
ID.
• Only VLANs and other local port attributes configured on local
controller.
© .1996-2006 NETGEAR® . All rights reserved
221
Multi-Controller
(continued)
Master
Local
AP Location 2.0.0
Local Controller IP
Building 2
Building 1
Local
Building 3
GRE Tunnel
© .1996-2006 NETGEAR® . All rights reserved
222
AP Boot Sequence
» During an AP boot, the AP identifies itself to the master controller
with its location ID. The master uses the location ID to determine
where the AP should terminate its GRE tunnel. When using
VRRP, this should be the virtual IP address of the VRRP router.
» On the master controller, tie APs to their local controller by
location ID. This must be done even if AP bootstrap from their
local controller.
» For the local controller, local mode is configured during intial
setup.
» After that, only VLAN and IP information is configured on the
Local controller. Al lother configuration is done on the master.
© .1996-2006 NETGEAR® . All rights reserved
223
Moving to a Multi-Switch Environment
» For a single WLAN configuration, the master switch is the
WFS709TP that controls the RF and security settings of the
WLAN.
» Additional WFS709TP to the same WLA serve as local switches to
the master WFS709TP.
» A local WFS709TP operates independently of the master and
depends on the master only for its security and RF setting.
» The local WFS709TP needs to have connectivity to the master at
all times to ensure that any changes on the master are
propagated to the local WFS709TP.
© .1996-2006 NETGEAR® . All rights reserved
224
Reasons to move to multi-switch environment
» Scaling to include a larger coverage area
» Setting up remote APs
» Network setups requires APs to be redistributed from a single to
multi-switch environment.
© .1996-2006 NETGEAR® . All rights reserved
225
Steps to migrate from single-switch to multi-switch environment
» 1. Configure the role of the local WFS709T to local and specify
the IP address of the master.
» 2. Configuration the layer2/layer3 settings on the local WFS709TP
(VLANs, IP subnets, IP routes).
» 3. Configure as trusted ports the ports the master and local
WFS709TP use to communicate with each other.
» 4. For those APs that need to boot off the local WFS709tp,
configure the LMS IP address to point to the new local
WFS709TP.
» 5. Reboot the APs that are already on the network, so that they
now connect to the local WFS709TP.
© .1996-2006 NETGEAR® . All rights reserved
226
Configuring the local WFS09TP
» Set the mode of the WFS709TP to local.
» Set the master IP address to the IP address of the master
WFS709TP. If master redundancy is enabled on the master, this
address should be the VRRP address for the VLANs instance
corresponding to the IP address of the WFS8709TP.
© .1996-2006 NETGEAR® . All rights reserved
227
Configure the AP for local controller
» Set LMS IP to local controller IP address.
© .1996-2006 NETGEAR® . All rights reserved
228
Roaming
» Standard 802.11 mobility
• There is no standard protocol for inter-AP handoff
• There is no standard protocol for client-AP handoff
• Client find an AP to associated with, and will hold that association
for as long as possible
• When error rates climb high enough, client will drop association
and look for a new AP
• In a legacy fat-AP network, client had to re-authenticate, get a new
IP address, etc when roaming. All data sessions interrupted.
» Some vendor improved on this, requires proprietary software/clients
© .1996-2006 NETGEAR® . All rights reserved
229
WFS709TP mobility
» Because WFS709TP provides a central management point for
wireless traffic, mobility is seamless
» APs are simply radios – when a client roams from one AP to
another, it only change radios. The wireless switch maintains
state of authentication and encryption
» Ultimately, client still controls mobility
• Client will hang onto an AP as long as it can
• No way to schedule a handoff without client software
© .1996-2006 NETGEAR® . All rights reserved
230
Single Controller Mobility
» When a client roams between APs all mobility
processing is done internally - client retains its IP
address
» Authentication, ACLs, flow classification, state
information is all maintained by the controller
1.1.1
1.1.2
© .1996-2006 NETGEAR® . All rights reserved
L2 Roaming
L3 Roaming
ap location 1.1.0
vlan 100
ap location 1.1.1
vlan 100
ap location 1.1.2
vlan 200
231
Inter-controller mobility
» There are two options for inter-controller mobility
» If controllers are L2 connected, L2 (VLAN mobility) is
recommended.
» If controllers are L3 connected, L3 mobility is recommended.
© .1996-2006 NETGEAR® . All rights reserved
232
Layer 2 Mobility
» If 2 or more controller are layer2 connected, simply trunk all user
VLANs to all controllers in the same site.
» When user roams to another controller, the new controller will
continue to place their traffic on the same VLAN.
© .1996-2006 NETGEAR® . All rights reserved
233
Layer 2 Mobility
ap location 1.0.0
vlan 100
ap location 2.0.0
vlan 200
14, 100, 200
14
100
200
1.1.1
VLAN 100
© .1996-2006 NETGEAR® . All rights reserved
14
100
200
2.1.1
VLAN 100
234
Layer3 Mobility
» L3 mobility should be enabled when controller are separated by
an layer3 network.
» Controllers build mobile-IP tunnels to transmit client traffic to
original controller (home agent).
» When a client roam to an AP controller by different controller, the
new controller (foreign agent) recognizes the client and tunnels
the traffic back to the original controller (home agent).
© .1996-2006 NETGEAR® . All rights reserved
235
Layer 3 Mobility
» L3 mobility should be enabled when controllers are
separated by an L3 network
» Controllers build mobile-IP tunnels to transmit client
traffic to original controller (home agent)
ap location 1.0.0
vlan 100
ap location 2.0.0
vlan 200
L3 Network
14
100
1.1.1
VLAN 100
© .1996-2006 NETGEAR® . All rights reserved
15
200
Mobile IP
2.1.1
VLAN 100
236
Inter-Controller Mobility
1.
2.
3.
4.
Master
Client roams to different
controller (foreign agent)
FA recognizes client
FA builds tunnel to HA
Client’s traffic tunneled
through HA to destination
3
Local
Local
Local
1
© .1996-2006 NETGEAR® . All rights reserved
237
Tunnel Objectives
» Reasons for Mobile IP tunnel:
• IP Addresses are hierarchical - the wired network will still route
traffic to the HA
• Wired-side anti-spoofing rules will not be violated
• Traffic continues through existing Firewall states at HA
© .1996-2006 NETGEAR® . All rights reserved
238
Switch Role
Enable Mobility
© .1996-2006 NETGEAR® . All rights reserved
239
LMS IP
LMS IP
© .1996-2006 NETGEAR® . All rights reserved
240
Multi-controller redundancy
» WFS709TP can be configured in a redundant configuration to
provide fault tolerance in the case of failure.
» Two options:
• Local controller redundancy
• Master controller redundancy
© .1996-2006 NETGEAR® . All rights reserved
241
Local Redundancy
» A pair of WFS709TP with the primary master serving all the APs.
» When the primary master fails, the backup controller take control
of the APs.
» The two WFS709TP must be in the same broadcast domain and
they should have the same firmware version.
© .1996-2006 NETGEAR® . All rights reserved
242
Configuring local controller redundancy
» Collect the VLAN ID on the two WFS709TP that are on the layer2
network and will be used to configure the VRRP instance.
» Decided on a virtual IP.
» Go to Configuration->Switch->VRRP and create a new VRRP
instance.
» Setup the VRRP instance with the proper parameters.
» Configure the APs to terminate their tunnel using the virtual IP.
© .1996-2006 NETGEAR® . All rights reserved
243
VRRP
© .1996-2006 NETGEAR® . All rights reserved
244
VRRP
© .1996-2006 NETGEAR® . All rights reserved
245
VRRP instance for local redundancy
© .1996-2006 NETGEAR® . All rights reserved
246
N + 1 local redundancy
» Master serve as backup of each of the local controller.
© .1996-2006 NETGEAR® . All rights reserved
247
Configure N+1 local redundancy
» Configure the master WFS709TP interface as a trunk port for
VLANs belongs to the #N local controllers.
» The master WFS709TP is set with #N VRRP instance for each
local controller that it is providing redundancy to.
» For each VRRP instance:
» Collect the VLAN ID between the master and local controller.
» Decided on a virtual IP.
» Go to Configuration->Switch->VRRP and create a new VRRP
instance.
» Setup the VRRP instance with the proper parameters, plus:
• Configure the master WFS709TP priority to be 100 and the local
controller to be 110.
• Enable pre-emption.
• Configure master up time or master state tracking with an added
value of 20.
» Configure the APs to terminate their tunnel using the virtual IP.
© .1996-2006 NETGEAR® . All rights reserved
248
Master controller redundancy
»
»
»
»
»
»
WFS709TP can support master controller redundancy
Both WFS709TP are configured as master controllers
Master controllers also support redundancy using VRRP.
Local controllers set master controller IP to VIP
All configuration done on primary master
If master discovery is through DHCP option 43 or through DNS, make
sure they assign the master’s virtual address.
» Besides supporting AP boot sequences, configurations of local
controllers, and mobility support, master controllers can also have APs
terminate traffic on them. If the primary master fails, then the backup
master must take over all responsibilities of the master. Some of these
depend upon database information which is stored in the master. The
backup master need to receive periodical updates from the active to
ensure that it has the latest copy for when it needs to take over the
master duties.
» Database synchronization is configurable in the VRRP setup. You can
also specify how often sync should occur.
© .1996-2006 NETGEAR® . All rights reserved
249
Configure master redundancy
» Collect the VLAN ID on the two WFS709TP that are on the layer2
network and will be used to configure the VRRP instance.
» Decided on a virtual IP.
» Go to Configuration->Switch->VRRP and create a new VRRP
instance.
» Setup the VRRP instance with the proper parameters as local
redundancy except:
• Set the initial prefer master’s priority to 110 and the back to 100.
• Enable pre-emption.
• Configure master up time or master state tracking with an added
value of 20.
» Associate the master VRRP instance with the master WFS709TP
redundancy.
» Configure the APs to terminate their tunnel using the virtual IP.
» The master controller IP need to be set in the local controller.
» The WFS709TP need to be rebooted after the master controller IP
is changed.
250
© 1996-2006 NETGEAR . All rights reserved
.
®
Associate master VRRP ID with the master WFS709TP redundancy
© .1996-2006 NETGEAR® . All rights reserved
251
Section 10: Troubleshooting
© .1996-2006 NETGEAR® . All rights reserved
252
Maintenance
© .1996-2006 NETGEAR® . All rights reserved
253
Maintenace – Reboot Switch
© .1996-2006 NETGEAR® . All rights reserved
254
Maintenance – Clear config
© .1996-2006 NETGEAR® . All rights reserved
255
Maintenance – Synchronize database
© .1996-2006 NETGEAR® . All rights reserved
256
Maintenance – Boot Parameter
© .1996-2006 NETGEAR® . All rights reserved
257
File – Copy File
© .1996-2006 NETGEAR® . All rights reserved
258
File – Copy Crash Files
© .1996-2006 NETGEAR® . All rights reserved
259
File – Copy Log
© .1996-2006 NETGEAR® . All rights reserved
260
Lab Exercise
© .1996-2006 NETGEAR® . All rights reserved
261
Known issues
» 1. Cannot manage wireless controller using IE7 on Vista.
» 2. In some GUI pages, the table width can be longer than the
window size when using resolution lower than 1260x1048
© .1996-2006 NETGEAR® . All rights reserved
262
WFS709TP access
» http://71.140.56.164:8888
» User name: admin
» Password: Netgearwfs709tp
© .1996-2006 NETGEAR® . All rights reserved
263
Q&A
© .1996-2006 NETGEAR® . All rights reserved
264