1.) Open the pcap file in wireshark to get an idea of the capture. The
advertisement
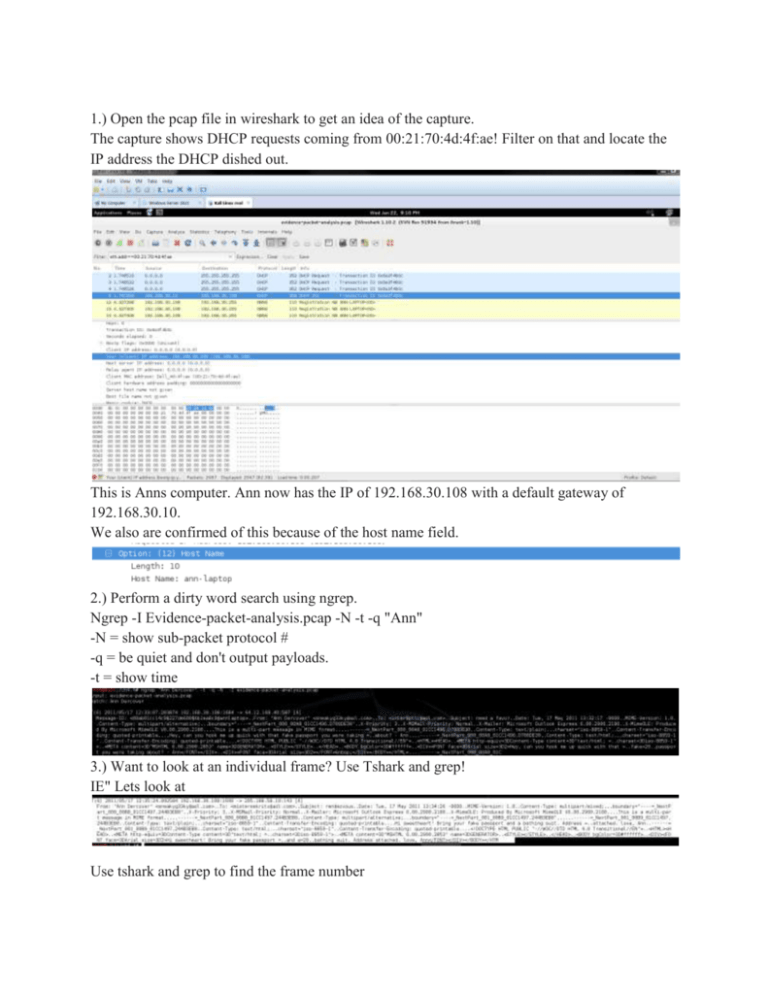
1.) Open the pcap file in wireshark to get an idea of the capture. The capture shows DHCP requests coming from 00:21:70:4d:4f:ae! Filter on that and locate the IP address the DHCP dished out. This is Anns computer. Ann now has the IP of 192.168.30.108 with a default gateway of 192.168.30.10. We also are confirmed of this because of the host name field. 2.) Perform a dirty word search using ngrep. Ngrep -I Evidence-packet-analysis.pcap -N -t -q "Ann" -N = show sub-packet protocol # -q = be quiet and don't output payloads. -t = show time 3.) Want to look at an individual frame? Use Tshark and grep! IE" Lets look at Use tshark and grep to find the frame number Now use tshark to print that frame 4.) Let's look more at the output of the ngrep search. The results show 7 frames. The results of this show that there were 7 frames that had matches to "Ann Dercover" and that that 3 of them went over SMTP (port 587). Four frames went over port 143, which is assigned to the Internet Message Access Protocol (IMAP) which is used to retrieve e-mail. 5.) Let's get the stream of the SMTP messages from tshark I am taking anything from Ann's laptop that matches SMTP or IMAP. 6.) Wireshark time! Open that new pcap and follow the TCP stream of the first frame to reveal information about Anns mail client. We see that her login information right under AUTH LOGIN... but that information is in base 64. Let's decode it! Here’s Ann’s username: $ echo "c25lYWt5ZzMza3k =" | base64 -d sneakyg33ky Here’s her password: $ echo "czAwcGVyczNrcjF0" | base64 -d s00pers3kr1t We also see Ann's message recipient... inter0ptlc@aol.com Looking more at the stream we also get the Subject of "need a favor" and the message containing " Hey, can you hook me up quick with that fake passport you were taking = about? - Ann" 7.) Keep following TCP streams... there are several e-mails that Ann sent... filter by tcp.port==587 and view a few of them! Using the results from your ngrep.... you have times/dates of the several times "Ann Decrover" matched... follow the TCP stream on those packets! Reveals 3 main e-mails. 8.) Looking at the 3rd e-mail... Ann says that a location is attached for her lover to meet her. This flow is between ports 1689 and 587. Here is the last result from the ngrep that was ran in step 2... This shows that ann send something with an attachment! This stream is between ports 143 and 1690. Let's use tcpflow on this steam and get some information about it. " # less 192.168.030.108.01689-064.012.168.040.00587" reveals the e-mail that was sent. 9.) The e-mail said there was an attachment... let's get it... manually! Looking in bless we can see the name of the file that was sent by Ann. immediately after that filename= field is the attachment. Cut all the junk before the "UEsD" ASCII field out! Also cut the junk starting at offset 0x4513a. Note: the garbage at the beginning ends at offset 0x73c. Cut that junk out and save. I saved mine as "carvedstream". We have to remove the line breaks in this carved attachment. The book uses the command "fromdos" and this requires the "tofrodos" package to be installed.. apt-get or yum that thing! #apt-get install tofrodos tofrodos converts text files between DOS and Unix formats GOT HER! ------------------------------------------Other ways to carve that would be easier? Tail like in the last one??? hmmm...







