Chapter 6 carlos
advertisement

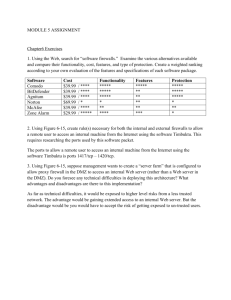
Carlos Giron Information Security Professor Hartunian June 14, 2012 Chapter 6 Review Questions 2&8 Exercise 2 and Case exercises 1&2 2. TCP (Transmission Control Protocol) is the most commonly used protocol on the Internet. The reason for this is because TCP offers error correction. When the TCP protocol is used there is a "guaranteed delivery." This is due largely in part to a method called "flow control." Flow control determines when data needs to be re-sent, and stops the flow of data until previous packets are successfully transferred. This works because if a packet of data is sent, a collision may occur. When this happens, the client rerequests the packet from the server until the whole packet is complete and is identical to its original. UDP (User Datagram Protocol) is anther commonly used protocol on the Internet. However, UDP is never used to send important data such as webpages, database information; UDP is commonly used for streaming audio and video. Streaming media such as Windows Media audio files (.WMA), Real Player (.RM), and others use UDP because it offers speed! The reason UDP is faster than TCP is because there is no form of flow control or error correction. The data sent over the Internet is affected by collisions, and errors will be present. Remember that UDP is only concerned with speed. This is the main reason why streaming media is not high quality. 8. Firewalls fall into four broad categories: packet filters, circuit level gateways, application level gateways and stateful multilayer inspection firewalls. Packet filtering firewalls work at the network level of the OSI model, or the IP layer of TCP/IP. They are usually part of a router. Circuit level gateways work at the session layer of the OSI model, or the TCP layer of TCP/IP. They monitor TCP handshaking between packets to determine whether a requested session is legitimate. Information passed to remote computer through a circuit level gateway appears to have originated from the gateway. Application level gateways, also called proxies, are similar to circuit-level gateways except that they are application specific. They can filter packets at the application layer of the OSI model. Incoming or outgoing packets cannot access services for which there is no proxy. Stateful multilayer inspection firewalls combine the aspects of the other three types of firewalls. They filter packets at the network layer, determine whether session packets are legitimate and evaluate contents of packets at the application layer. They allow direct connection between client and host, alleviating the problem caused by the lack of transparency of application level gateways. Exercise 2 2. Timbuktu is a remote control software product developed by WOS Data systems. Remote control software allows a user to control another computer across the local network or the Internet, viewing its screen and using its keyboard and mouse as if he or she were sitting in front of it. Timbuktu is compatible with computers running both Mac OS X and Windows. Case Exercises 1. What is more efficient for the company? What is a better set up, subnet with bastion hosts? Or a screened subnet with proxy servers? How will that decision affect the way they implement application and web servers? What type of security protection program does the company need? 2. Cost versus maintaining high security for SLS; I think that in the long run maintaining high security is more important than the cost. Not having high security can result in spending more money therefore cost versus maintaining high security I would choose a high security because that is most important at this moment.