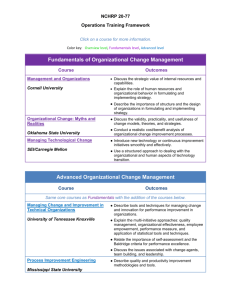
Security+ Guide to Network Security Fundamentals
advertisement

Security+ Guide to Network Security Fundamentals, Third Edition Chapter 1 Introduction to Security Objectives • Describe the challenges of securing information • Define information security and explain why it is important • Identify the types of attackers that are common today • List the basic steps of an attack • Describe the five steps in a defense • Explain the different types of information security careers and how the Security+ certification can enhance a security career Security+ Guide to Network Security Fundamentals, Third Edition 2 Challenges of Securing Information • There is no simple solution to securing information • This can be seen through the different types of attacks that users face today – As well as the difficulties in defending against these attacks Security+ Guide to Network Security Fundamentals, Third Edition 3 Today’s Security Attacks • Typical warnings: – A malicious program was introduced at some point in the manufacturing process of a popular brand of digital photo frames – Nigerian e-mail scam claimed to be sent from the U.N. – “Booby-trapped” Web pages are growing at an increasing rate – A new worm disables Microsoft Windows Automatic Updating and the Task Manager – Apple has issued an update to address 25 security flaws in its operating system OS X Security+ Guide to Network Security Fundamentals, Third Edition 4 Today’s Security Attacks (continued) • Typical warnings: (continued) – The Anti-Phishing Working Group (APWG) reports that the number of unique phishing sites continues to increase – Researchers at the University of Maryland attached four computers equipped with weak passwords to the Internet for 24 days to see what would happen • These computers were hit by an intrusion attempt on average once every 39 seconds Security+ Guide to Network Security Fundamentals, Third Edition 5 Today’s Security Attacks (continued) • Security statistics bear witness to the continual success of attackers: – TJX Companies, Inc. reported that over 45 million customer credit card and debit card numbers were stolen by attackers over an 18 month period from 2005 to 2007 – Table 1-1 lists some of the major security breaches that occurred during a three-month period – The total average cost of a data breach in 2007 was $197 per record compromised – A recent report revealed that of 24 federal government agencies, the overall grade was only “C−” Security+ Guide to Network Security Fundamentals, Third Edition 6 Security+ Guide to Network Security Fundamentals, Third Edition 7 Difficulties in Defending against Attacks • Difficulties include the following: – – – – Speed of attacks (now faced with zero-day attacks) Greater sophistication of attacks Simplicity of attack tools Attackers can detect vulnerabilities more quickly and more readily exploit these vulnerabilities – Delays in patching hardware and software products – Most attacks are now distributed attacks, instead of coming from only one source – User confusion Security+ Guide to Network Security Fundamentals, Third Edition 8 Security+ Guide to Network Security Fundamentals, Third Edition 9 Security+ Guide to Network Security Fundamentals, Third Edition 10 Difficulties in Defending against Attacks (continued) Security+ Guide to Network Security Fundamentals, Third Edition 11 What Is Information Security? • Knowing why information security is important today and who the attackers are is beneficial Security+ Guide to Network Security Fundamentals, Third Edition 12 Defining Information Security • Security can be considered as a state of freedom from a danger or risk – This state or condition of freedom exists because protective measures are established and maintained • Information security – The tasks of guarding information that is in a digital format – Ensures that protective measures are properly implemented – Cannot completely prevent attacks or guarantee that a system is totally secure Security+ Guide to Network Security Fundamentals, Third Edition 13 Defining Information Security (continued) • Information security is intended to protect information that has value to people and organizations – This value comes from the characteristics of the information: • Confidentiality • Integrity • Availability • Information security is achieved through a combination of three entities Security+ Guide to Network Security Fundamentals, Third Edition 14 Security+ Guide to Network Security Fundamentals, Third Edition 15 Defining Information Security (continued) Security+ Guide to Network Security Fundamentals, Third Edition 16 Defining Information Security (continued) • A more comprehensive definition of information security is: – That which protects the integrity, confidentiality, and availability (CIA) of information on the devices that store, manipulate (process), and transmit the information through products, people, and procedures Security+ Guide to Network Security Fundamentals, Third Edition 17 Information Security Terminology • Asset – Something that has a value (examples?) • Threat – An event or object that may defeat the security measures in place and result in a loss (examples?) • Threat agent – A person or thing that has the power to carry out a threat (examples?) • This definition is more broad than others that limit threat agents to also possessing an intent to attack or damage Security+ Guide to Network Security Fundamentals, Third Edition 18 Information Security Terminology (continued) • Vulnerability – Weakness that allows a threat agent to bypass security (i.e. configuration errors or software “bugs”) • Risk – The likelihood, or probability, that a threat agent will exploit a vulnerability – Risk is usually expressed as a percentage (90% chance of a web server being hacked in a year) – Realistically, risk cannot ever be entirely eliminated Security+ Guide to Network Security Fundamentals, Third Edition 19 Information Security Terminology (continued) • Impact must then be calculated – What is the resultant loss if the event occurs? Information Security Terminology (continued) • Would the Loss of stereo really be the threat – or the impact? • If it is the impact, what then is the threat? • What if the stereo was a USB thumb drive with healthcare records on it? Security+ Guide to Network Security Fundamentals, Third Edition 21 Information Security Terminology Loss of USB Thumb Drive with PII Example Asset Threat Threat Agent Vulnerability Impact Security+ Guide to Network Security Fundamentals, Third Edition Mitigation 22 Information Security Terminology Loss of USB Thumb Drive with PII Example Asset Threat Threat Agent Vulnerability Customer Data Loss or theft of equipment with data Employee or USBs are theif easily lost or misplaced. Data is in plain text on the drives. Impact Mitigation Loss of PII results in heavy fines and loss of customer confidence (loss of sales) Enable encryption on all drives (including USB drives) Security+ Guide to Network Security Fundamentals, Third Edition 23 Vulnerability Matrix Vulnerabilities/Controls Matrix Risk No. Vulnerabilities Impact on Business (Optional) Ex: Users use internal modem to bypass Internet Web proxy and access unauthorized sites Users can download malicious code. Unattended modems can provide access to an external attacker Recommended Controls 1. Disable all internal modems 2.Enforce IE proxy access throug Windows GPOs 3.Schedule regular vulnerability assessments using war dialing software Malicious Code (Chapter 2) 1. 2. 3. Hardware-Based (Chapter 2) 4. 5. 6. Email (Chapter 3) 7. 8. 9. Web Vulnerabilities (Chapter 3) 10. 11. 12. Network Vulnerabilities (i.e. switches, communications protocols – Chapter 4) 13. 14. 15. Wireless Vulnerabilities (Chapter 6) 16. Understanding the Importance of Information Security • Preventing data theft – Security is often associated with theft prevention – The theft of data is one of the largest causes of financial loss due to an attack – Individuals are often victims of data thievery • Thwarting identity theft – Identity theft involves using someone’s personal information to establish bank or credit card accounts • Cards are then left unpaid, leaving the victim with the debts and ruining their credit rating Security+ Guide to Network Security Fundamentals, Third Edition 25 Understanding the Importance of Information Security (continued) • Avoiding legal consequences – A number of federal and state laws have been enacted to protect the privacy of electronic data • The Health Insurance Portability and Accountability Act of 1996 (HIPAA) • The Sarbanes-Oxley Act of 2002 (Sarbox, or SOX) • The Gramm-Leach-Bliley Act (GLBA) • USA Patriot Act (2001) • The California Database Security Breach Act (2003) • Children’s Online Privacy Protection Act of 1998 (COPPA) Security+ Guide to Network Security Fundamentals, Third Edition 26 Understanding the Importance of Information Security (continued) • Maintaining Productivity – Cleaning up after an attack diverts resources such as time and money away from normal activities Security+ Guide to Network Security Fundamentals, Third Edition 27 Understanding the Importance of Information Security (continued) • Foiling cyberterrorism – Cyberterrorism • Attacks by terrorist groups using computer technology and the Internet – Utility, telecommunications, and financial services companies are considered prime targets of cyberterrorists Security+ Guide to Network Security Fundamentals, Third Edition 28 Who Are the Attackers? • The types of people behind computer attacks are generally divided into several categories – These include hackers, script kiddies, spies, employees, cybercriminals, and cyberterrorists Security+ Guide to Network Security Fundamentals, Third Edition 29 Hackers • Hacker • – Generic sense: anyone who illegally breaks into or attempts to break into a computer system – Narrow sense: a person who uses advanced computer skills to attack computers only to expose security flaws Although breaking into another person’s computer system is illegal – Some hackers believe it is ethical as long as they do not commit theft, vandalism, or breach any confidentiality – Q: What is the difference between a “Cracker” and a “Hacker” – Q: What is the difference between White hat hacking and black hat hacking? – Q: What is “ethical hacking”? Security+ Guide to Network Security Fundamentals, Third Edition 30 Script Kiddies • Script kiddies – Want to break into computers to create damage – Unskilled users – Download automated hacking software (scripts) from Web sites and use it to break into computers • They are sometimes considered more dangerous than hackers – Script kiddies tend to be computer users who have almost unlimited amounts of leisure time, which they can use to attack systems Security+ Guide to Network Security Fundamentals, Third Edition 31 Spies • Computer spy – A person who has been hired to break into a computer and steal information • Spies are hired to attack a specific computer or system that contains sensitive information – Their goal is to break into that computer or system and take the information without drawing any attention to their actions • Spies, like hackers, possess excellent computer skills Security+ Guide to Network Security Fundamentals, Third Edition 32 Employees • One of the largest information security threats to a business actually comes from its employees • Reasons – An employee might want to show the company a weakness in their security – Disgruntled employees may be intent on retaliating against the company – Industrial espionage – Blackmailing Security+ Guide to Network Security Fundamentals, Third Edition 33 Cybercriminals • Cybercriminals – A loose-knit network of attackers, identity thieves, and financial fraudsters – More highly motivated, less risk-averse, better funded, and more tenacious than hackers • Many security experts believe that cybercriminals belong to organized gangs of young and mostly Eastern European attackers • Cybercriminals have a more focused goal that can be summed up in a single word: money Security+ Guide to Network Security Fundamentals, Third Edition 34 Cybercriminals (continued) Security+ Guide to Network Security Fundamentals, Third Edition 35 Cybercriminals (continued) • Cybercrime – Targeted attacks against financial networks, unauthorized access to information, and the theft of personal information • Financial cybercrime is often divided into two categories – Trafficking in stolen credit card numbers and financial information – Using spam to commit fraud Security+ Guide to Network Security Fundamentals, Third Edition 36 Cyberterrorists • Cyberterrorists – Their motivation may be defined as ideology, or attacking for the sake of their principles or beliefs • Goals of a cyberattack: – To deface electronic information and spread misinformation and propaganda – To deny service to legitimate computer users – To commit unauthorized intrusions into systems and networks that result in critical infrastructure outages and corruption of vital data Security+ Guide to Network Security Fundamentals, Third Edition 37 Attacks and Defenses • Although there are a wide variety of attacks that can be launched against a computer or network – The same basic steps are used in most attacks • Protecting computers against these steps in an attack calls for five fundamental security principles Security+ Guide to Network Security Fundamentals, Third Edition 38 Steps of an Attack • The five steps that make up an attack – – – – – Probe for information Penetrate any defenses Modify security settings Circulate to other systems Paralyze networks and devices Security+ Guide to Network Security Fundamentals, Third Edition 39 Security+ Guide to Network Security Fundamentals, Third Edition 40 Defenses against Attacks • Although multiple defenses may be necessary to withstand an attack – These defenses should be based on five fundamental security principles: • • • • • Protecting systems by layering Limiting Diversity Obscurity Simplicity Security+ Guide to Network Security Fundamentals, Third Edition 41 Layering • Information security must be created in layers • One defense mechanism may be relatively easy for an attacker to circumvent – Instead, a security system must have layers, making it unlikely that an attacker has the tools and skills to break through all the layers of defenses • A layered approach can also be useful in resisting a variety of attacks • Layered security provides the most comprehensive protection Security+ Guide to Network Security Fundamentals, Third Edition 42 Limiting • Limiting access to information reduces the threat against it • Only those who must use data should have access to it – In addition, the amount of access granted to someone should be limited to what that person needs to know • Some ways to limit access are technology-based, while others are procedural Security+ Guide to Network Security Fundamentals, Third Edition 43 Diversity • Layers must be different (diverse) – If attackers penetrate one layer, they cannot use the same techniques to break through all other layers • Using diverse layers of defense means that breaching one security layer does not compromise the whole system Security+ Guide to Network Security Fundamentals, Third Edition 44 Obscurity • An example of obscurity would be not revealing the type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it • Obscuring information can be an important way to protect information Security+ Guide to Network Security Fundamentals, Third Edition 45 Simplicity • Information security is by its very nature complex • Complex security systems can be hard to understand, troubleshoot, and feel secure about • As much as possible, a secure system should be simple for those on the inside to understand and use • Complex security schemes are often compromised to make them easier for trusted users to work with – Keeping a system simple from the inside but complex on the outside can sometimes be difficult but reaps a major benefit Security+ Guide to Network Security Fundamentals, Third Edition 46 Surveying Information Security Careers and the Security+ Certification • Today, businesses and organizations require employees and even prospective applicants – To demonstrate that they are familiar with computer security practices • Many organizations use the CompTIA Security+ certification to verify security competency Security+ Guide to Network Security Fundamentals, Third Edition 47 Types of Information Security Jobs • Information assurance (IA) – A superset of information security including security issues that do not involve computers – Covers a broader area than just basic technology defense tools and tactics – Also includes reliability, strategic risk management, and corporate governance issues such as privacy, compliance, audits, business continuity, and disaster recovery – Is interdisciplinary; individuals who are employed in it may come from different fields of study Security+ Guide to Network Security Fundamentals, Third Edition 48 Types of Information Security Jobs (continued) • Information security, also called computer security – Involves the tools and tactics to defend against computer attacks – Does not include security issues that do not involve computers • Two broad categories of information security positions – Information security managerial position – Information security technical position Security+ Guide to Network Security Fundamentals, Third Edition 49 Security+ Guide to Network Security Fundamentals, Third Edition 50 CompTIA Security+ Certification • The CompTIA Security+ (2008 Edition) Certification is the premiere vendor-neutral credential • The Security+ exam is an internationally recognized validation of foundation-level security skills and knowledge – Used by organizations and security professionals around the world • The skills and knowledge measured by the Security+ exam are derived from an industry-wide Job Task Analysis (JTA) Security+ Guide to Network Security Fundamentals, Third Edition 51 CompTIA Security+ Certification (continued) • The six domains covered by the Security+ exam: – Systems Security, Network Infrastructure, Access Control, Assessments and Audits, Cryptography, and Organizational Security Security+ Guide to Network Security Fundamentals, Third Edition 52 Other Stuff • Join Organizations and get certified: – ISSA – Student Memberships $30 www.issa.org – IAPP – student memberships $50, become CIPP/G certified – Start a computer club at NVCC (participate in the CCDC!!!) – ISC2 – Associate of (ISC)² - pass SSCP exam www.isc2.org • Read Books and Magazines: • Hackin9 • 2600 Magazine • Everything else you can get your hands on • Pay attention to your personal life and activities so you can get a security clearance, companies and agencies DO NOT hire hackers You are a part of CyberWatch!!! IAPP • SEEKING PRIVACY SCHOLARS Each year, the IAPP awards Privacy Academy scholarships to outstanding college students who may be interested in entering the field of privacy and data protection. Up to five students will receive scholarships to attend this year's Privacy Academy, which takes place in Baltimore, MD, next month. Do you know of a motivated full-time college student who would like the chance to attend, learn, network and have one-on-one time with a professional mentor? If so, please let them know about this valuable opportunity. Interested candidates should send a resume and letter of interest to scholarships@privacyassociation.org Summary • Attacks against information security have grown exponentially in recent years • There are several reasons why it is difficult to defend against today’s attacks • Information security may be defined as that which protects the integrity, confidentiality, and availability of information on the devices that store, manipulate, and transmit the information through products, people, and procedures Security+ Guide to Network Security Fundamentals, Third Edition 56 Summary (continued) • The main goals of information security are to prevent data theft, thwart identity theft, avoid the legal consequences of not securing information, maintain productivity, and foil cyberterrorism • The types of people behind computer attacks are generally divided into several categories • There are five general steps that make up an attack: probe for information, penetrate any defenses, modify security settings, circulate to other systems, and paralyze networks and devices Security+ Guide to Network Security Fundamentals, Third Edition 57 Summary (continued) • The demand for IT professionals who know how to secure networks and computers from attacks is at an all-time high Security+ Guide to Network Security Fundamentals, Third Edition 58