CIT484_Layer 2 Security Plan
advertisement

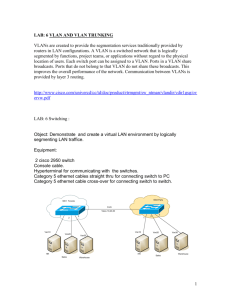
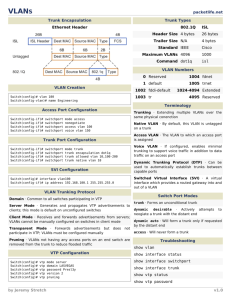
Name: Adam A. Akka Date: July 14, 2014 Course: CIT-484-001: Network Security Instructor: Teresa Riley Assignment: Layer 2 Security Plan Team members: Adam Akka, Abdullah Almarshad, Christopher Holman, Rease Morelock, Christopher Moyer ====================================================== Our layer 2 security plan: 1. Select an unused VLAN (other than VLAN 1) and use that for the native VLAN for all your trunks. 2. Administratively configure access ports as access ports so that users cannot negotiate a trunk and disable the negotiation of trunking (no Dynamic Trunking Protocol [DTP]). 3. Limit the number of MAC addresses learned on a given port with the port security feature. 4. Control spanning tree to stop users or unknown devices from manipulating spanning tree. This can be done by using the BPDU guard and root guard features. 5. Turn off Cisco Discovery Protocol (CDP) on ports facing untrusted or unknown networks that do not require CDP for anything positive. 6. Shut down all ports that are not used and assign them to a VLAN that is not used for anything else other than a parking lot. Configurations: 1. This is our configuration to Administratively configure access ports as access ports: Switch-7A(config)# interface range gigabitethernet1/0/1 - 3 Switch-7A(config-if)# switchport trunk encapsulation dot1q Switch-7A(config-if)# switchport mode trunk Switch-7A(config-if)# switchport trunk native vlan 2 Switch-7A(config-if)# switchport nonegotiate Switch-7A(config)# interface range gigabitethernet1/0/4 - 10 Switch-7A(config-if)# switchport mode access Switch-7A(config-if)# switchport access VLAN 2 Switch-7A(config-if)# switchport nonegotiate Switch-7A(config)# interface range gigabitethernet1/0/11 - 20 Switch-7A(config-if)# switchport mode access Switch-7A(config-if)# switchport access VLAN 3 Switch-7A(config-if)# switchport nonegotiate ========================================================================== Switch-7B(config)# interface range gigabitethernet1/0/23 - 24 Switch-7B(config-if)# switchport trunk encapsulation dot1q Switch-7B(config-if)# switchport mode trunk Switch-7B(config-if)# switchport trunk native vlan 2 Switch-7B(config-if)# switchport nonegotiate Switch-7B(config)# interface range gigabitethernet1/0/1 - 10 Switch-7B(config-if)# switchport mode access Switch-7B(config-if)# switchport access VLAN 2 Switch-7B(config-if)# switchport nonegotiate Switch-7B(config)# interface range gigabitethernet1/0/11 - 20 Switch-7B(config-if)# switchport mode access Switch-7B(config-if)# switchport access VLAN 3 Switch-7B(config-if)# switchport nonegotiate ========================================================================== Switch-8A(config)# interface range gigabitethernet1/0/1 - 3 Switch-8A(config-if)# switchport trunk encapsulation dot1q Switch-8A(config-if)# switchport mode trunk Switch-8A(config-if)# switchport trunk native vlan 2 Switch-8A(config-if)# switchport nonegotiate Switch-8A(config)# interface range gigabitethernet1/0/4 - 10 Switch-8A(config-if)# switchport mode access Switch-8A(config-if)# switchport access VLAN 2 Switch-8A(config-if)# switchport nonegotiate Switch-8A(config)# interface range gigabitethernet1/0/11 - 20 Switch-8A(config-if)# switchport mode access Switch-8A(config-if)# switchport access VLAN 3 Switch-8A(config-if)# switchport nonegotiate ========================================================================== Switch-8B(config)# interface range gigabitethernet1/0/23 - 24 Switch-8B(config-if)# switchport trunk encapsulation dot1q Switch-8B(config-if)# switchport mode trunk Switch-8B(config-if)# switchport trunk native vlan 2 Switch-8B(config-if)# switchport nonegotiate Switch-8B(config)# interface range gigabitethernet1/0/1 - 10 Switch-8B(config-if)# switchport mode access Switch-8B(config-if)# switchport access VLAN 2 Switch-8B(config-if)# switchport nonegotiate Switch-8B(config)# interface range gigabitethernet1/0/11 - 20 Switch-8B(config-if)# switchport mode access Switch-8B(config-if)# switchport access VLAN 3 Switch-8B(config-if)# switchport nonegotiate ========================================================================== ********************************************* Show commands to verify settings: show interfaces switchport show interfaces trunk ********************************************* 2. Limit the number of MAC addresses learned on a given port with the port security feature. This is our configuration to Limit the number of MAC addresses learned: ========================================================================== Switch-7A(config)# interface range gigabitethernet1/0/4 - 24 Switch-7A(config-if)# switchport port-security Switch-7A(config-if)# switchport port-security maximum 5 Switch-7A(config-if)# switchport port-security violation protect Switch-7A(config-if)# switchport port-security mac-address sticky ========================================================================== Switch-7B(config)# interface range gigabitethernet1/0/1 - 22 Switch-7B(config-if)# switchport port-security Switch-7B(config-if)# switchport port-security maximum 5 Switch-7B(config-if)# switchport port-security violation protect Switch-7B(config-if)# switchport port-security mac-address sticky ========================================================================== Switch-8A(config)# interface range gigabitethernet1/0/4 - 24 Switch-8A(config-if)# switchport port-security Switch-8A(config-if)# switchport port-security maximum 5 Switch-8A(config-if)# switchport port-security violation protect Switch-8A(config-if)# switchport port-security mac-address sticky ========================================================================== Switch-8B(config)# interface range gigabitethernet1/0/1 - 22 Switch-8B(config-if)# switchport port-security Switch-8B(config-if)# switchport port-security maximum 5 Switch-8B(config-if)# switchport port-security violation protect Switch-8B(config-if)# switchport port-security mac-address sticky ========================================================================== ********************************************* Show command to verify settings: show port-security [interface] ********************************************* 3. Control spanning tree to stop users or unknown devices from manipulating spanning tree. This can be done by using the BPDU guard and root guard features. This is our configuration to Implementing BPDU guard and Root guard : ========================================================================== Switch-7A(config)# interface range gigabitethernet1/0/4 - 24 Switch-7A(config-if)# spanning-tree bpduguard enable Switch-7A(config)# interface range gigabitethernet1/0/1 - 3 Switch-7A(config-if)# spanning-tree guard root ========================================================================== Switch-7B(config)# interface range gigabitethernet1/0/1 - 22 Switch-7B(config-if)# spanning-tree bpduguard enable Switch-7B(config)# interface range gigabitethernet1/0/23 - 24 Switch-7B(config-if)# spanning-tree guard root ========================================================================== Switch-8A(config)# interface range gigabitethernet1/0/4 - 24 Switch-8A(config-if)# spanning-tree bpduguard enable Switch-8A(config)# interface range gigabitethernet1/0/1 - 3 Switch-8A(config-if)# spanning-tree guard root ========================================================================== Switch-8B(config)# interface range gigabitethernet1/0/1 - 22 Switch-8B(config-if)# spanning-tree bpduguard enable Switch-8B(config)# interface range gigabitethernet1/0/23 - 24 Switch-8B(config-if)# spanning-tree guard root ========================================================================== ********************************************* Show command to verify the status of the switchport: show interface status ********************************************* 4. Turn off Cisco Discovery Protocol (CDP) on ports facing untrusted or unknown networks that do not require CDP for anything positive. These are the commands to turn off Cisco Discovery Protocol (CDP) as needed: Switch-XX(config)#interface [interface] Switch-XX(config-if)#no cdp enable ********************************************* Show command to verify CDP status: show cdp neighbors ********************************************* 5. Shut down all ports that are not used and assign them to a VLAN that is not used for anything else other than a parking lot. This is our configuration to shut down all ports that are not used and assign them to a VLAN: ========================================================================== Switch-7A(config)# interface range gigabitethernet1/0/21 - 24 Switch-7A(config-if)#switchport mode access Switch-7A(config-if)#switchport access vlan 99 Switch-7A(config-if)#shutdown ========================================================================== Switch-7B(config)# interface range gigabitethernet1/0/21 - 22 Switch-7B(config-if)#switchport mode access Switch-7B(config-if)#switchport access vlan 99 Switch-7B(config-if)#shutdown ========================================================================== Switch-8A(config)# interface range gigabitethernet1/0/21 - 24 Switch-8A(config-if)#switchport mode access Switch-8A(config-if)#switchport access vlan 99 Switch-8A(config-if)#shutdown ========================================================================== Switch-8B(config)# interface range gigabitethernet1/0/21 - 22 Switch-8B(config-if)#switchport mode access Switch-8B(config-if)#switchport access vlan 99 Switch-8B(config-if)#shutdown ========================================================================== ********************************************* Show command to verify VLANs' settings: show vlan all-ports *********************************************