NAKSHA TECHNOLOGIES INC. Sunnyvale,CA
advertisement

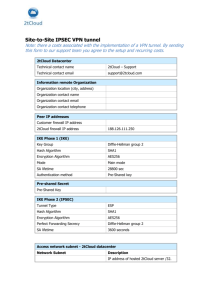
NAKSHA TECHNOLOGIES INC. Sunnyvale,CA-USA IPSEC-Tunneling Mode Using NetGear Prosafe VPN Firewall Disclaimer: Information in this publication is subject to change without notice and does not represent a commitment on the part of Naksha Technologies Inc(NTI). The information contained here in is the proprietary and confidential information of NTI. The procedures described in this application note are deliberately broad and generic. Your specific design might require procedures that are slightly different from those described here. Revision Index: 1.1 Initial Version to setup the NETGEAR VPN ----- (June-15-2009) IPSEC-Tunnel Mode using Netgear VPN Required Equipment: 1) Three pc's. One of them should act as a gateway & the remaining two are end peers 2) For the gate way machine we need o have 2 Ethernet cards. 3) Netgear prosafe Vpn firewall (model: FVS318) Software Requirements: 1) Gate way machine is expected to have a minimum of 2.6.23 linux kernal & a setkey version of >=0.5. For additional details on setting up the kernel modules please refer Twiki. 2) Remaining two machines which are acting as peers can be of any OS. Basic Setup for VPN: 1) login to Netgear VPN. (By default the IP will be 192.168.0.1 , user-name: admin , Passwd: password. 2) Go to “Basic Settings” option Internet IP Address --> Use Static IP Address IP Address : 192.168.1.1 IP Subnet Mask : 255.255.255.0 Gateway IP Address :192.168.1.2 Domain Name Server (DNS) Address --> Use These DNS Servers Primary DNS : 4.2.2.1 (You can choose any DNS) Click “APPLY” 3) Go to Security --> Rules your OUTBOUND services action should be ALLOW Always Now you have to Modify the INBOUND Services Please Create one INBOUND services Service --> It could be SFTP or SSH or ICMP (You can have all three of them individually) Action --> ALLOW always Send to LAN Server --> 192.168.0.3 WAN Users --> Any Click “APPLY” 4) Go to “VPN Policies” option Add Manual policy General --> Policy Name --> manual_1 Remote VPN End point --> Address Type --> IP Address Address Data --> 192.168.1.2 Traffic Selector --> Local IP --> subnet address Start IP Address : 192.168.0.0 Finish IP Address: 0.0.0.0 Subnet Mask : 255.255.255.0 Remote IP --> Subnet Address Start IP Address : 192.168.2.0 Finish IP Address: 0.0.0.0 Subnet Mask : 255.255.255.0 ESP Configuration --> SPI-Incoming --> 201 SPI-Outgoing --> 301 Enable Encryption --> 3DES Key IN --> 111111112222222233333333 Key OUT--> 111111112222222233333333 Enable Authentication --> MD5 Key IN --> 1111222222223333 Key Out --> 1111222222223333 Click “APPLY” 4) Go to Maintenance --> Router Status (please follow step-5 to reflect step-4 values) Your LAN PORT should reflect the following values IP Address : 192.168.0.1 DHCP : ON IP Subnet Mask : 255.255.255.0 5) Go to Advanced --> LAN Setup LAN TCP/IP Setup IP Address : 192.168.0.1 IP Subnet Mask : 255.255.255.0 RIP Direction : None RIP Version : Disabled LAN IP Address Management --> Use Router as DHCP Server DHCP Server Info Starting IP Address : 192.162.0.2 Ending IP Address : 192.168.0.51 DNS Server Address --> Router is DNS Proxy Now we have configured the VPN for our custom test. Basic Structure: Please follow the following ethernet settings for your PC's . We have already set the config for VPN in the previous step. PC1-----(port1)VPN(internet)----------------------(Eth1)PC2(Eth0)--------PC3 Eth0-----Manual Config-------------------------------------Eth0---------------Eth0 192.168.0.3 192.168.0.1 192.168.2.1 192.168.2.2 Internet Eth1 192.168.1.1<----------------------------------->192.168.1.2 SETKEY Conf file for PC2: please have the following conf file in PC2 #!/sbin/setkey -f #the SAD and SPD flush; spdflush; # ESP SAs doing encryption using 192 bit long keys (168 + 24 parity) # and authentication using 128 bit long keys add 192.168.1.2 192.168.1.1 esp 0x201 -m tunnel -E 3des-cbc "111111112222222233333333" -A hmac-md5 "1111222222223333"; add 192.168.1.1 192.168.1.2 esp 0x301 -m tunnel -E 3des-cbc "111111112222222233333333" -A hmac-md5 "1111222222223333"; # Security policies spdadd 192.168.0.0/24 192.168.2.0/24 any -P in ipsec esp/tunnel/192.168.1.1-192.168.1.2/require; spdadd 192.168.2.0/24 192.168.0.0/24 any -P out ipsec esp/tunnel/192.168.1.2-192.168.1.1/require; Save the serkey_tunnel.conf file in /etc folder. Testing the Tunnel Mode Environment: Cmd: setkey -f /etc/setkey_tunnel.conf (In PC2) Please ping from the PC1 ping 192.168.2.2 Please ping from the PC2 ping 192.168.0.1