How To: Integrate Active Directory with StreamStudio
advertisement
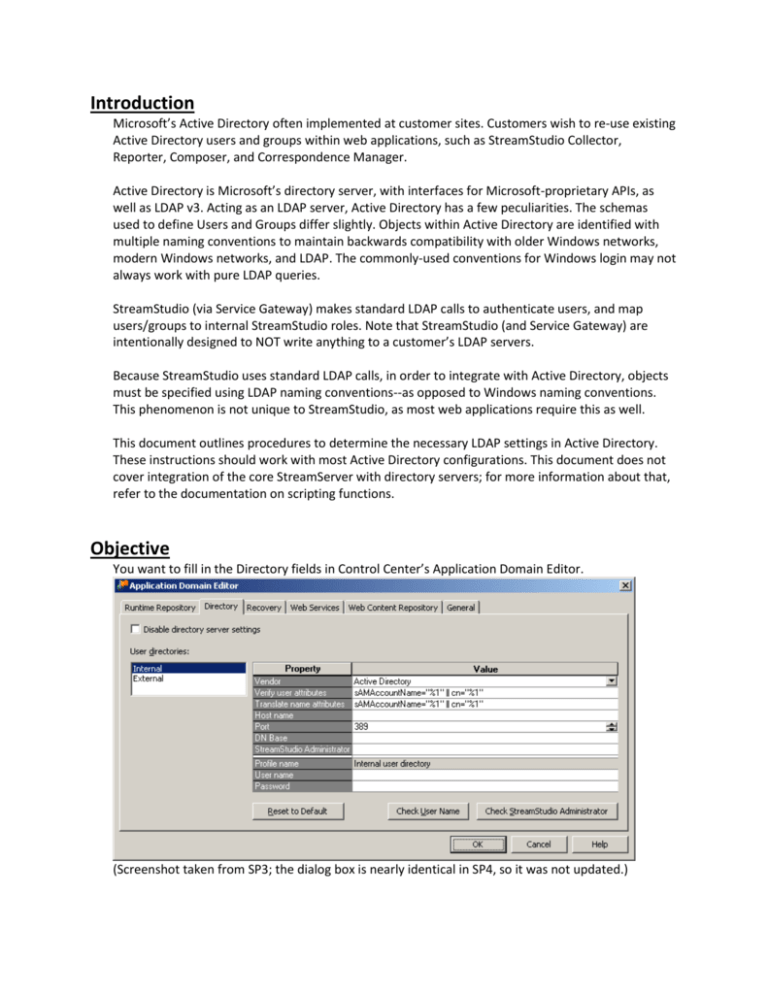
Introduction Microsoft’s Active Directory often implemented at customer sites. Customers wish to re-use existing Active Directory users and groups within web applications, such as StreamStudio Collector, Reporter, Composer, and Correspondence Manager. Active Directory is Microsoft’s directory server, with interfaces for Microsoft-proprietary APIs, as well as LDAP v3. Acting as an LDAP server, Active Directory has a few peculiarities. The schemas used to define Users and Groups differ slightly. Objects within Active Directory are identified with multiple naming conventions to maintain backwards compatibility with older Windows networks, modern Windows networks, and LDAP. The commonly-used conventions for Windows login may not always work with pure LDAP queries. StreamStudio (via Service Gateway) makes standard LDAP calls to authenticate users, and map users/groups to internal StreamStudio roles. Note that StreamStudio (and Service Gateway) are intentionally designed to NOT write anything to a customer’s LDAP servers. Because StreamStudio uses standard LDAP calls, in order to integrate with Active Directory, objects must be specified using LDAP naming conventions--as opposed to Windows naming conventions. This phenomenon is not unique to StreamStudio, as most web applications require this as well. This document outlines procedures to determine the necessary LDAP settings in Active Directory. These instructions should work with most Active Directory configurations. This document does not cover integration of the core StreamServer with directory servers; for more information about that, refer to the documentation on scripting functions. Objective You want to fill in the Directory fields in Control Center’s Application Domain Editor. (Screenshot taken from SP3; the dialog box is nearly identical in SP4, so it was not updated.) The Application Domain Editor modifies the master territory.xml file, which defines connectivity parameters for Service Gateway and StreamStudio. In the Directory tab, un-check “Disable directory server settings,” and select the settings for an “Internal” user directory, and under “Vendor” select “Active Directory.” The following fields must be completed in order for StreamStudio to query AD users and groups 1. Hostname – This specifies an Active Directory domain controller 2. BaseDN – This specifies the branch of the LDAP tree from which StreamStudio will search for users and groups. 3. Service user/password – Active Directory requires authentication prior to running any queries or browsing the LDAP tree. The service user does not require any elevated permissions in the Active Directory. 4. StreamStudio Administrator – This user will be mapped to the “System Manager” role in StreamStudio. The StreamStudio Administrator can be the same as the service account, or could be any Windows Domain User. The StreamStudio Administrator user does not require any elevated permissions in the Active Directory. The following fields should be verified for better performance Hostname – This field was specified above. If there are multiple Active Directory controllers, ensure that the server specified here has a copy of the Global Catalog. BaseDN – This field was specified above. More specific RDNs will yield faster searches. Especially with Active Directory, specifying the RootDN of the Active Directory forest will result in extremely slow searches. Verify user attributes – Depending on the naming conventions used in the customer’s Active Directory, most of the time, only one attribute is really needed here. Translate name attributes – Depending on the naming conventions used in the customer’s Active Directory, most of the time, only one attribute is really needed here. Ideally, you should be using a Windows system which is a member of the target Active Directory domain, and logged in as a Domain User on that AD domain as well. You do not need to be a Domain Administrator, nor should you require direct access to a Domain Controller. If you do not have access to a Windows system on the Active Directory domain, and/or cannot log in as a Domain User, this will be more difficult. Ask somebody in the customer’s Windows/Network/Security group for assistance. The following diagram illustrates that StreamStudio connects to LDAP repositories through an instance of Service Gateway. If there are firewalls between Service Gateway and the target Active Directory server, make sure the appropriate TCP port (usually 389) is open. Tools The following tools are freely available, and do not require installation. Download them, and extract them to your workstation. Or run directly from a USB memory stick. ldapsearch.exe This is a command-line tool that comes with most LDAP servers, but not Active Directory It can be copied from most LDAP servers (e.g. Netscape/iPlanet/Sun/AOL/Fedora/Red Hat, Apache, CA, IBM, OctetString, OpenDS, OpenLDAP, Oracle, Siemens…) It can be downloaded from http://www.mozilla.org/directory/ For your convenience, it can also be found on Download Center LDAP Admin This is a Windows GUI tool, which can bind to most LDAP servers It can be downloaded from http://ldapadmin.sourceforge.net/ For your convenience, it can also be found on Download Center Basic Procedure Initially, we just want to establish a working connection to the customer’s Active Directory. We can—and should—look into optimizing these parameters later. 1. Identify an Active Directory Controller If you are running on a Windows system that is a member of the Active Directory Domain, and logged in as a Domain User, a. Open a Command Prompt b. Run the command ‘echo %LOGONSERVER%’ echo %LOGONSERVER% \\BOS3K01 c. The result of this command (minus the backslashes) is the unqualified hostname of an Active Directory controller There may be other AD controllers on the network, but this is the one you are logged into d. To get the server’s fully qualified DNS hostname and IP address, run ‘nslookup’ or ‘ping -a’ nslookup BOS3K01 Name: bos3k01.streamserve.com Address: 192.168.127.25 e. Enter the fully-qualified domain name (or IP address) into the “Host name” field If you are not running on a Windows system that is a member of the Active Directory Domain, or are not logged in as a Domain User, ask the customer’s Windows administrators for assistance. Or, try to guess it… Refer to the later section “Guessing the AD Controller” for hints. 2. Find the Active Directory Root DN Quite often, the Windows Domain Administrators will not remember the LDAP namespaces for their Active Directories. Fortunately, once an AD Controller has been identified, the LDAP namespaces are easy enough to obtain. All you need are some LDAP tools and a single query. You could also try and guess the Root DN. See the corresponding section for hints. Especially with Active Directory, the RootDN is not the optimal BaseDN for LDAP queries. It is the base of the entire directory structure. Choosing a more specific branch of the directory would yield faster queries. After the initial directory server configuration, back and re-examine this field: refer to the sections on BaseDN tuning and Browsing the Active Directory tree with LDAPadmin. a. Run ‘ldapsearch -h [hostname] -s base -b "" (objectclass=*)’ Substitute the hostname or IP address of the AD controller (from Step 1) Append “namingcontexts rootdomainnamingcontext “ to the command line to only return those attributes The multi-valued namingContexts attribute lists the tops of directory trees hosted on the AD Controller The single-valued rootDomainNamingContext attribute identifies the root naming context for the domain ldapsearch -h bos3k01 -p 389 -T -1 -s base -b "" (objectclass=*) namingcontexts rootdomainnamingcontext dn: namingContexts: DC=streamserve,DC=com namingContexts: CN=Configuration,DC=streamserve,DC=com namingContexts: CN=Schema,CN=Configuration,DC=streamserve,DC=com namingContexts: DC=DomainDnsZones,DC=streamserve,DC=com namingContexts: DC=ForestDnsZones,DC=streamserve,DC=com rootDomainNamingContext: DC=streamserve,DC=com b. Copy and paste the value of the rootDomainNaming Context into the “DN Base” field e.g. “DC=streamserve,DC=com” If there is no rootDomainNamingContext, or no defaultNamingContext, select the most appropriate value from namingContexts 3. Specify a StreamStudio service login and password Some LDAP servers, including Active Directory, require authentication prior to running any queries. The StreamStudio service user does not require any special privileges in the Active Directory; it just needs to be a Domain User, able to authenticate, enumerate, and query the directory. You will need to know the password for this account. If a StreamServe service account has already been created, use it. Service accounts should have passwords that do not expire. If a service account has not already been created, any user with a Windows Domain User login can be specified here. With Active Directory, the StreamStudio service account user can be specified in various formats: LDAP Distinguished Name o e.g. CN=StreamServe, CN=Service Accounts, CN=Users, DC=localdomain,DC=com NTLM Domain/Username o e.g. LOCALDOMAIN\STREAMSERVE Active Director User Principal Name (“UPN”) o e.g. streamserve@localdomain.com Refer to the section about Active Directory Naming Formats for more details. With other directory servers, the StreamStudio service user’s login must be specified as an LDAP Distinguished Name. a. First, pick a Windows Domain User for the StreamStudio service account b. Determine the Domain User’s Windows UPN and/or NTLM login If the Windows Administrator is around, ask for the user’s userPrincipalName NTLM login: NT Domain Name\sAMAccountName password You can figure this out yourself A userPrincipalName looks like an e-mail address (e.g. “dsh01@streamserve.com”), with an at symbol separating the username from the domain name An NTLM name consists of a Windows Domain name and a User Name, usually separated by a backslash (e.g. “IDSDOMAIN\dsh01”) If you are logged into Windows as the desired Domain User, your username and the domain name are stored as environment variables Open a command prompt Run ‘echo %USERNAME% This is your username Run ‘echo %USERDOMAIN%’ If the result is one word in ALL_CAPS e.g. “IDSDOMAIN” your NTLM login is %USERDOMAIN%\%USERNAME% If the result looks like a DNS domain name e.g. “streamserve.com” your userPrincipalName is %USERNAME%@%USERDOMAIN% NTLM format UPN format echo %USERNAME% STREAMSERVE echo %USERNAME% strs_service echo %USERDOMAIN% LOCALDOMAIN echo %USERDOMAIN% localdomain.com Use %USERDOMAIN%\%USERNAME% e.g. LOCALDOMAIN\STREAMSERVE Use %USERNAME%@%USERDOMAIN e.g. strs_service@localdomain.com c. Enter the service user’s NTLM login or User Principal Name into “User Name” e.g. “LOCALDOMAIN\STREAMSERVE” or “strs_service@localdomain.com” d. Enter the service user’s network password into its “Password” field. e. Click on the “Check User Name” button… 4. Specify a StreamStudio Administrator user account The StreamStudio Administrator logs into StreamStudio, and performs initial configuration tasks, such as assigning other LDAP users and groups to StreamStudio Roles. This user is automatically mapped to the StreamStudio “System Manager” Role, but does not require any special privileges in Active Directory. Up through Persuasion SP3 (5.0.0-5.3.0), the StreamStudio Administrator user had to be an LDAP user on the Internal directory. It does not require any special privileges; it can just be a regular Domain User in Active Directory. StreamStudio does not need to know this user’s password: just its identity. The LDAP user is mapped to the StreamStudio System Manager Role in the Runtime Repository database. As of Persuasion SP4 (5.4.0+), the initial StreamStudio Administrator is stored in the territory.xml file (i.e. outside of LDAP). The initial StreamStudio configuration is much easier, since the LDAP integration is not entirely necessary. (i.e. StreamStudio can be run with just this one user. Or the integration with LDAP can be postponed until a more convenient time.) In SP4, the StreamStudio system manager user is specified on the Administrator tab in the Application Domain Editor. Since it is not an LDAP user, it will not be discussed further in this document. The following instructions pertain to Persuasion prior to SP4. The StreamStudio Administrator user can be the same user as the service user. It can be any Windows Domain User. If you don’t know, or can’t decide, just use the service user account; it can be changed at a later date. The StreamStudio Administrator user must be specified as an LDAP DN. The StreamStudio Administrator’s LDAP DN must be within the search BaseDN specified in Step 2. e.g. if the BaseDN is “dc=localdomain,dc=com”, and the StreamStudio Administrator is “cn=StreamServe,cn=Users,dc=localdomain,dc=com”, that’s fine e.g. if the BaseDN is “cn=UK,dc=mydomain,dc=com”, and the desired StreamStudio Administrator is “cn=StreamServe,cn=US,dc=localdomain,dc=com”, then it will not work a. First, pick a Windows Domain User that will become the StreamStudio Administrator b. Obtain the username of the desired StreamStudio Administrator sAMAccountName or userPrincipalName, or %USERNAME% e.g. “hol01” c. Determine the LDAP Distinguished Name for the user Run ‘ldapsearch -h [hostname]-b "[BaseDN]" -D "[ UPN]" -w "(|(samaccountname=[username]) (userprincipalname=[username]*))" dn’ Substitute [hostname] with the AD controller’s hostname or IP address, from Step 1 Substitute [BaseDN] with the naming context from Step 2 Substitute [UPN] with the User Principal Name (or NTLM login) from Step 3 You could log in as any user on the Windows Domain, but we might as well test the service user’s login. Why not? Substitute [USERNAME] with just the user name of the desired StreamStudio Administrator user that we are querying In this example, the desired StreamStudio Administrator is “hol01” Enter the service user’s password when prompted Not the password of the StreamStudio Administrator user ldapsearch -h bos3k01 -p 389 -T -1 -b "dc=streamserve,dc=com" -D "strs_service@streamserve.com" -w "(|(samaccountname=hol01)(userprincipalname=hol01*))" dn Enter bind password: ******** dn: CN=Olsson\, Hans,OU=Users,OU=IT,OU=Sth,OU=Sweden,DC=streamserve,DC=com d. Copy and paste the StreamStudio Administator’s DN value to the “StreamStudio Administrator” field e. Click on the “Check StreamStudio Administrator” button The desired net result might look something like this: In this particular example, The LDAP server is bos3k01.streamserve.com o It’s running Active Directory on TCP port 389 o This AD controller is a Global Catalog master The Base DN for StreamStudio queries is “dc=streamserve,dc=com” o Unfortunately, this is the root directory object, so searches could be very slow The service user is a service account called strs_service o Note that this field can take an NTLM, UPN, or DN o We chose the UPN syntax because it’s easier than DN o userPrincipalName: strs_service@streamserve.com The StreamStudio Administrator is Hans Olsson o Note that this field must be in DN syntax o The user specified here must be within the Base DN specified above o DN: CN=Olsson\, Hans,OU=Users,OU=IT,OU=Sth,OU=Sweden,DC=streamserve,DC=com The relevant user attribute for authentication is sAMAccountName o i.e. Hans Olsson would log in as “hol01”, instead of “Olsson\, Hans” or “hol01@streamserve.com” Basic Procedure - Tuning 1. Hostname – This field was specified earlier, but should be re-examined a. If there are multiple Active Directory controllers on the network, verify that the server specified has a copy of the Global Catalog The Global Catalog is a master copy of the Active Directory tree An AD server without a complete copy of the GC will usually take longer to respond to queries, because it does not have all the data Do an ldapsearch on the RootDSE object of the AD controller, and check the “isGlobalCatalogReady” value ldapsearch -h bos3k01 -p 389 -x -T -1 -s base -b "" (objectclass=*) namingcontexts defaultnamingcontext rootdomainnamingcontext dnshostname issynchronized isglobalcatalogready domainfunctionality forestfunctionality domaincontrollerfunctionality dn: namingContexts: DC=streamserve,DC=com namingContexts: CN=Configuration,DC=streamserve,DC=com namingContexts: CN=Schema,CN=Configuration,DC=streamserve,DC=com namingContexts: DC=DomainDnsZones,DC=streamserve,DC=com namingContexts: DC=ForestDnsZones,DC=streamserve,DC=com defaultNamingContext: DC=streamserve,DC=com rootDomainNamingContext: DC=streamserve,DC=com dnsHostName: bos3k01.streamserve.com isSynchronized: TRUE isGlobalCatalogReady: TRUE domainFunctionality: 2 forestFunctionality: 0 domainControllerFunctionality: 2 If “isGlobalCatalogReady” is not “TRUE” then try to find another AD controller If “forestFuncionality” is anything but “0”, then this Active Directory Domain is actually part of a Forest b. The Windows Domain Administrators can log into an existing AD Controller, and add the Global Catalog FSMO role 2. BaseDN – This field was specified earlier, but should be re-examined a. We specified the top of the Active Directory tree as the root for all queries b. More specific RDNs will yield faster searches c. Especially with Active Directory, specifying the RootDN of the Active Directory forest can result in extremely slow searches Within the root naming context, Active Directory stores many other trees See the sample above… searches on all of “dc=streamserve,dc=com” would also reference “CN=Configuration,dc=streamserve,dc=com”, “CN=Schema,CN=Configuration,dc=streamserve,dc=com”, “DC=DomainDnsZones,dc=streamserve,dc=com”, “DC=ForestDnsZones,dc=streamserve,dc=com” With Active Directory, there are thousands of additional entries in those other d. The BaseDN specified here must include All User objects that will be mapped to StreamStudio Roles All Group objects that will be mapped to StreamStudio Roles (Up through SP3) The special StreamStudio Administrator user that will be mapped to the StreamStudio System Manager Role e. See the section (below) on browsing the directory tree with LDAP Admin 3. Verify user attributes a. This field defines which LDAP attribute(s) can be used for the StreamStudio login username b. Most of the time, only one attribute is really needed here c. Depending on the naming conventions used in the customer’s Active Directory, the key attribute could be “sAMAccountName”, “cn”, or “userPrincipalName” d. Most of the time, just use sAMAccountName="%1" e. See the section (below) on Active Directory Naming Conventions 4. Translate name attributes a. Most of the time, only one attribute is really needed here b. Most of the time, just use the same value as in the “Verify user attributes” field Assigning StreamStudio Administrator (Up through SP3), the StreamStudio Administrator user’s role is mapped in the Runtime Repository database After specifying (or modifying) the StreamStudio Administrator user, it is necessary to update the Runtime Repository database o In Control Center, select your Application Domain o Right-click on it, and go to Create Database… o Choose “Assign Administrator role to the StreamStudio Administrator account” o Click on Start o Enter the database credentials for a user that has write access to the Runtime Repository database for this Application Domain In SQL Server, this could be the “sa” user or the “StrsSecurity” user In Oracle, this could be the “SYSTEM” user, or the database schema owner like “StrsRuntimeAccess” (As of SP4), the StreamStudio Administrator is specified on the “Administrator” tab of Control Center’s Application Domain Editor. The StreamStudio Administrator account is stored in the territory.xml file, with its password encrypted using a reversible hash. The user does not reside within the LDAP repository, and its role is not mapped in any of the databases. Updating StreamServe Application Domain file After specifying or updating information in the Application Domain Editor, it is necessary to update the Application Domain configuration file (territory.xml). If prompted “Do you want to update the domain information for all applications in the Application Domain?” just click on “Yes” o Up through SP3, make sure to restart the StreamStudio J2EE engine (i.e. Tomcat) after updating the territory.xml file o As of SP4, it is not necessary to restart Tomcat, though it probably wouldn’t hurt Alternately, the file can be updated manually through Control Center o In Control Center, select your Application Domain o Right-click on it, and go to Update Application Domain file o Restart the StreamStudio J2EE engine, if necessary If the StreamStudio J2EE engine is not running on a node with Management Gateway, the Application Domain file must be copied manually o Find a copy of the territory.xml file e.g. from Service Gateway (C:\ManagementGateway\1.0\root\applications\ServiceGateway\wd\) o Copy it to the $STRS_DOC_PORTAL_ROOT directory e.g. with Tomcat running on Windows, that might be C:\Program Files\Apache Tomcat 5.5\webapps\applications\WEBINF\spring\properties\ o Restart the StreamStudio J2EE engine, if necessary Active Directory Naming Formats Some of the naming conventions supported by Active Directory and Window systems include Old Windows standalone sAMAccountName o This is a single-part username o The sAMAccountName identifies a user on an NTLM host o e.g. “DSH01” Old Windows domain NTLM login o This Windows-specific format consists of the NTLM domain name, plus the sAMAcountName o Prepending the NTLM domain name allows identification of a user within an NTLM workgroup or domain o This syntax is extremely common, but is not actually stored as an attribute in AD o USERDOMAIN\SAMACCOUNTNAME o e.g. “IDSDOMAIN\DSH01” Newer Active Directory userPrincipalName o This Windows-specific format looks like an e-mail address, but should not be confused with an e-mail address o The userPrincipalName uniquely identifies a user within an Active Directory forest o user@dnsdomainname o e.g. “dsh01@streamserve.com” LDAP Distinguished Name (“DN”) o This LDAP format uniquely identifies objects within an LDAP directory tree o An object’s full distinguished name consists of multiple relative distinguished name components, in a comma-separated list o e.g. “cn=Shih\, David, OU=Users,OU=Bos, OU=USA, DC=streamserve, DC=com” LDAP Common Name (“CN”) o This LDAP format refers to a single attribute o e.g. “Shih\, David” In general, CN, sAMAccountName, and userPrincipalName are all completely independent of one another, and do not have to resemble each other at all CN, sAMAccountName, and the username portion of the userPrincipalName often are identical, though In Active Directory, the Distinguished Name (DN) is always based on the CN Here are the results of an ldapsearch, showing examples of the different ways one user can be identified by Active Directory. ldapsearch -h bos3k01 -p 389 -T -1 -b "dc=streamserve,dc=com" -D "%USERDOMAIN%\%USERNAME%" -w - "(samaccountname=%USERNAME%)" dn cn samaccountname userprincipalname Enter bind password: ******** dn: CN=Shih\, David,OU=Users,OU=Bos,OU=USA,DC=streamserve,DC=com cn: Shih, David sAMAccountName: dsh01 userPrincipalName: dsh01@streamserve.com In this example CN bears no resemblance to the sAMAccountName or userPrincipalName sAMAccountName and the username portion of the userPrincipalName are identical CN contains a comma-space, so when used in an RDN syntax, the comma must be escaped CN is probably not a good choice of attribute for StreamStudio login sAMAccountName should be used for the StreamStudio login instead Browsing the Active Directory tree with LDAP Admin LDAP Admin is a free, open source graphical LDAP browser tool for Windows. More information can be found at http://ldapadmin.sourceforge.net/. LDAP Admin allows you to easily view the hierarchy of an Active Directory tree. Among other things, it can help you decide the most appropriate Base DN for your queries. Download and run LDAPAdmin Define a new conection Start | Connect | New Connection Provide a name for the connection, e.g. “My Active Directory” Enter the hostname of a domain controller, e.g. “bos3k01.streamserve.com” Enter the Root DN, e.g. “dc=streamserve,dc=com” Un-check Anonymous Connection Enter the Username of the service account user, e.g. “strs_service@streamserve.com” Enter the service account user’s password (or leave it blank to be prompted every time) Click on “Test connection” Click on “OK” to save Open the connection, and start browsing! Example 1: All the users and groups were within “CN=Users,DC=streamserve,DC=com” The BaseDN for StreamStudio should be “CN=Users,DC=streamserve,DC=com” Example 2: UK-based users are within “OU=Users,OU=UK,DC=streamserve,DC=com” UK-based groups are within “OU=Groups,OU=UK,DC=streamserve,DC=com” Swedish-based users are within “OU=Users ,OU=SE,DC=streamserve,DC=com” Swedish-based groups are within “OU=Groups,OU=SE,DC=streamserve,DC=com” If StreamStudio is only going to be used in the UK, then the BaseDN for StreamStudio should be “OU=UK,DC=streamserve,DC=com” Example 3: UK-based users are within “OU=Users,OU=UK,DC=streamserve,DC=com” UK-based groups are within “OU=Groups,OU=UK,DC=streamserve,DC=com” Swedish-based users are within “OU=Users ,OU=SE,DC=streamserve,DC=com” Swedish-based groups are within “OU=Groups,OU=SE,DC=streamserve,DC=com” If StreamStudio is going to be used in the UK and Sweden, then the BaseDN for StreamStudio should be “DC=streamserve,DC=com” Example 4: UK-based users are within “OU=Users,OU=UK,DC=streamserve,DC=com” UK-based groups are within “OU=Groups,OU=UK,DC=streamserve,DC=com” All groups are within “OU=Groups ,DC=streamserve,DC=com” The BaseDN for StreamStudio should be “DC=streamserve,DC=com” Example 5: Regular users are within “CN=Users,C=streamserve,DC=com” Regular groups are within “OU=Groups,CN=Users,DC=streamserve,DC=com” The StreamStudio Administrator is in “OU=Service Accounts,DC=streamserve,DC=com” The BaseDN for StreamStudio should be “DC=streamserve,DC=com” Guessing the AD Controller If you are not logged into the AD Domain as a Domain User, or aren’t running on Windows, try asking a knowledgeable Windows Admin. If they’re not available, you can try finding the AD controller on your own. a. AD Controllers are often used as DNS, WINS, and DHCP servers Run ‘ipconfig /all’ Check the DNS, WINS, and DHCP servers listed there b. AD Controllers tend to have the Master Computer Browser role on a network segment Run ‘nbtstat -A [IP Address]’ and look for “MSBROWSE” nbtstat -A 192.168.127.25 NetBIOS Remote Machine Name Table Name Type Status --------------------------------------------BOS3K01 <00> UNIQUE Registered IDSDOMAIN <00> GROUP Registered IDSDOMAIN <1C> GROUP Registered BOS3K01 <20> UNIQUE Registered IDSDOMAIN <1E> GROUP Registered IDSDOMAIN <1D> UNIQUE Registered ..__MSBROWSE__.<01> GROUP Registered c. AD Controllers tend to be extremely chatty Note that customers’ security administrators object violently to us running packet sniffers on their networks If you happen to have a packet sniffer or traffic analyzer, like ‘netcat’, note the busiest broadcast hosts on SMB (TCP ports 135, 139) and ARP d. AD Controllers often have IP addresses that are relatively easy to remember Quite often, the last numbers of the IP address will be 254, 253, or 250 e. AD controllers often have hostnames that are easy to guess It all depends on the customer site and naming convention f. Functional-based naming conventions often have AD controllers with the strings “DC” “PDC” or “AD” somewhere in their hostnames Sequential naming conventions often reserve lower numbers like 0, 1, 00, or 01 for AD controllers AD Controllers almost always listen on TCP port 389 Note that many customers’ security administrators get upset if we run port scanners like ‘nmap’ on their networks You can check whether a single host has TCP:389 open by using a telnet command: ‘telnet [hostname] 389’ Guessing Active Directory’s LDAP namespaces If you are lazy, cannot remember the appropriate LDAP queries, or your LDAP tools do not seem to be working properly, you can try guessing the LDAP namespaces of Active Directory. Over ninety percent of the time with Active Directory, the LDAP Root namespace is based on the DNS domain name. This is the default setting in ‘dcpromo’ and most Windows admins do not change it. Example 1. Running ‘ipconfig’ reports that the local DNS domain name is “streamserve.com”. For the LDAP root DN, try “dc=streamserve,dc=com”. Example 2. If the local DNS domain name is “uk.mycompany.com”, try “dc=uk,dc=mycompany,dc=com” or “dc=mycompany,dc=com” Example 3. If the external DNS domain name is “megacompany.com” and the internal DNS domain name is “london.uk.megacompany.net”, then try “dc=megacompany,dc=net”, “dc=uk,dc=megacompany,dc=net”, “dc=london,dc=uk,dc=megacompany,dc=net”, “dc=megacompany,dc=com”… The Active Directory’s LDAP Root DN does not have to be of the format “dc=x,dc=y” but could be something like “o=MyAD” or “ou=uk,o=internaldomain”. But most of the time, with Active Directory, the root namespace does look like “dc=whatever,dc=com”. Active Directory Attributes, versus what Windows Admins usually see AD stores a lot of information about objects. In LDAP, each object has multiple attributes; some attributes are mandatory, others are optional; some attributes are multi-valued, others can only be single-valued. Some AD attributes and values are easily visible in common Microsoft Windows administrative tools, but others are hidden and only used internally. Here are some screen shots, illustrating the appearance of common LDAP attributes, in the Windows world. The attribute mappings can be helpful for defining StreamStudio Administrator/Customers queries. In the main Active Directory Users and Computers (dsa.msc) display The Name column corresponds to the LDAP “cn” (or commonName) attribute The Description column corresponds to the LDAP “description” attribute In Active Directory Users and Computers (dsa.msc), General Properties of an individual User object (objectClass: top, person, organizationalPerson, user) First Name = LDAP “givenname” Initials = LDAP “initials” Last Name = LDAP “sn” Display Name = LDAP “displayName”, “name” Description = LDAP “description” Office = LDAP “physicalDeliveryOfficeName” Telephone number = LDAP “telephoneNumber”, “otherTelephone” E-mail = LDAP “mail” Web page = LDAP “wWWHomePage”, “url” In Active Directory Users and Computers (dsa.msc), Account Properties of an individual User object User logon name: LDAP “userPrincipalName” The first part of the UPN can be mapped to %USERNAME% The second part of the UPN can be mapped to %USERDOMAIN% User logon name (pre-Windows 2000): LDAP “sAMAccountName” The first part of the NTLM login is not stored in Active Directory, but can be mapped to %USERDOMAIN% The second part of the NTLM login is the sAMAccountName, and can be mapped to %USERNAME% Address tab: Street = LDAP “streetAddress” or “street” P.O. Box = LDAP ”postOfficeBox” City = LDAP ”l” State/province = LDAP ”st” Zip/Postal Code = LDAP ”postalCode” Country/region: United States = LDAP c: US, co: USA, countryCode:840 Telephones tab: Home = LDAP ”homePhone”, “otherHomePhone” Pager = LDAP ”pagerPhone”, “otherPager” Mobile = LDAP ”mobile”, “otherMobile” Fax = LDAP ”facsimileTelephoneNumber”, “otherFacsimileTelephoneNumber” IP phone = LDAP ”ipPhone”, “otherIpPhone” Notes = LDAP ”info” Organization tab: Title = LDAP ”title” Department = LDAP ”department” Company = LDAP ”company” Manager = LDAP ”manager” Member Of tab: Member Of = LDAP ”memberOf” Groups (main display): LDAP “cn”, “displayName”, “name” Groups: (objectClass: top, group) Group name (pre-Windows 2000) = LDAP ”sAMAccountName” Description = LDAP ”description” E-mail = LDAP ”mail” Group scope (Domain local, Global, Universal) = LDAP ”groupType” Group type (Security, Distribution) = LDAP ”groupType” Notes = LDAP ”info” Members = LDAP ”member” Member Of = LDAP ”memberOf” Managed By Name = LDAP ”managedBy” Troubleshooting StreamStudio login fails o Is the Service Gateway instance running? By default, it’s only set to start Manually o Is there a Service Gateway instance? o Is the Service Gateway configured in the Application Domain Editor e.g. Primary URL “http://sgw-host” on TCP Port 2718 o Has the Application Domain file been updated? o Have you restarted Tomcat and Service Gateway? o Did the “Check User Name” button work in the Application Domain Editor? o Did the “Check StreamStudio Administrator” button work in the Application Domain Editor? o Did you remember to Assign the StreamStudio Administrator user in the Runtime Repository database? o Check the StreamStudio framework.log file C:\Program Files\Apache Tomcat 5.5\webapps\applications\WEB-INF\ o Check the Service Gateway servicegateway.log file C:\ManagementGateway\1.0\root\applications\ServiceGateway\wd\ o Check the Tomcat stdout.log and stderr.log files C:\Program Files\Apache Tomcat 5.5\logs\ “Check User Name” button fails in the Application Domain Editor o ldapsearch -h [hostname] -p [port] -D "[username]" -w "[password]" -b "[basedn]" -s sub (objectclass=*) Copy and paste the AD Controller’s hostname into the [hostname] Copy and paste the AD Controller’s port number (389) into the [port] Copy and paste the service account’s username into the [username] Copy and paste the service account’s password into the [password] Copy and paste the BaseDN into the [basedn] o If running SP4 GA, the Get Domain Controller, Get Naming Context, and Check User buttons do not always seem to work; if those buttons fail, take it with a grain of salt “Check StreamStudio Administrator” button fails in the Application Domain Editor o ldapsearch -h [hostname] -p [port] -D "[username]" -w "[password]" -b "[administrator_rdn]" -s one (objectclass=*) Copy and paste the AD Controller’s hostname into the [hostname] Copy and paste the AD Controller’s port number (389) into the [port] Copy and paste the service account’s username into the [username] Copy and paste the service account’s password into the [password] Copy and paste the StreamStudio Administrator’s Distinguished Name into the [administrator_rdn] Verify connectivity to the Active Directory controller from Service Gateway o ping [hostname] o telnet [hostname] 389 o nslookup [hostname] o make sure there are no firewalls blocking TCP:389 LDAP errors o Double-check your typing o Pay attention to the double quotes o If an RDN is specified in a command line, look at the comma-space delimiters o Look up the LDAP error codes online: http://leto.net/docs/ldap_error_code.php Anything else? o Please don’t call me. o Well, if it’s necessary or interesting, let me know.





