Chapter 3 - Lansing School District
advertisement

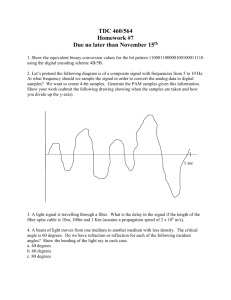
Module 3 Reading Organizer Using the curriculum define and explain the following terms: Coulomb’s Law Bohr’s model – Electromotive Force (EMF) – Attenuation Semiconductor Electrical current Alternating current (AC) - voltages vary over time by changing their polarity, or direction. AC flows in one direction, then reverses its direction and flows in the other direction, and then repeats the process. AC voltage is positive at one terminal, and negative at the other. Then the AC voltage reverses its polarity, so that the positive terminal becomes negative, and the negative terminal becomes positive. This process repeats itself continuously. Direct Current (DC) - always flows in the same direction, and DC voltages always have the same polarity. One terminal is always positive, and the other is always negative. They do not change or reverse. 10BASE-T - refers to the speed of transmission at 10 Mbps. The type of transmission is baseband, or digitally interpreted. The T stands for twisted pair. 10BASE5 – Modulation - The process of altering the carrier signal that will enter the antenna of the transmitter. Questions: 1. What characteristics comprise impedance? a. b. c. CCNA 1: Networking Basics V 3.0 1 3/6/2016 2. List four Semiconductors: a. carbon (C), b. germanium (Ge) c. d. 3. The unit of measurement for current is Ampere. 4. Current flows in closed loops called______ . These ______ must be composed of conducting materials, and must have sources of voltage. 5. What are three specifications or expectations for data transmission cable performance? a. b. What kind of transmission is being considered? Will the transmissions be digital or will they be analog-based? c. 6. What are the advantages of using coaxial cable? a. b. Coaxial cable is less expensive than fiber-optic cable. 7. Shielded twisted-pair cable (STP) reduces electrical noise within the cable such as pair to pair coupling and crosstalk. STP also reduces electronic noise from outside the cable, for example electromagnetic interference (EMI) and radio frequency interference (RFI). 8. STP affords greater protection from all types of external interference than UTP. Why isn’t it used more often instead of UTP? 9. Why does the metallic shielding materials in STP and ScTP need to be grounded at both ends? If improperly grounded or if there are any discontinuities in the entire length of the shielding material, STP and ScTP become susceptible to major noise problems. They are susceptible because they allow the shield to act like an antenna picking up unwanted signals. 10. Unshielded twisted-pair (UTP) cable relies solely on the cancellation effect produced by the ______________, to limit signal degradation caused by EMI and RFI. To further reduce crosstalk between the pairs in UTP cable, the number of twists in the wire pairs varies. CCNA 1: Networking Basics V 3.0 2 3/6/2016 11. What are the advantages of using UTP cable? a. b. It is c. It has a small external diameter 12. What are the disadvantages of using UTP cable? a. b.The distance between signal boosts is shorter for UTP than it is for coaxial and fiber optic cables 13. The cable that connects from the switch port to the computer NIC port is called a _________________ 14. The cable that connects from one switch port to another switch port is called a __________________ 15. The cable that connects the RJ-45 adapter on the com port of the computer to the console port of the router or switch is called a ________________ 16. Human can see electromagnetic energy with wavelengths between _________________ and ???? nanometers (nm). 17. Describe the ray model of light. (or why is light able to travel through a an optical fiber even when it curves) The light energy in the incident ray that is not reflected will enter the glass. The entering ray will be bent at an angle from its original path. This ray is called the refracted ray. How much the incident light ray is bent depends on the angle at which the incident ray strikes the surface of the glass and the different rates of speed at which light travels through the two substances. 18. What two conditions must be met for the light rays in a fiber to be reflected back into the fiber without any loss due to refraction? a. The core of the optical fiber has to have a larger index of refraction (n) than the material that surrounds it. The material that surrounds the core of the fiber is called the cladding. b. The angle of incidence of the light ray is greater than the critical angle for the core and its cladding. 19. Fiber-optic cable used for networking consists of two glass fibers encased in separate sheaths. Why? CCNA 1: Networking Basics V 3.0 3 3/6/2016 20. Fiber-optic cable is usually made in five parts. List and describe each. a. the core – describe …. b. the cladding c. a buffer d. a strength material e. an outer jacket 21. A single-mode core fiber optic cable is eight to ten microns in diameter. 22. What are the advantages of single mode fiber over multimode fiber cable? a. b. 23. Why are laser lights used in single mode considered dangerous? 24. What causes a PIN photodiode to produce an electric current of the proper voltage for the network? When it’s struck by a pulse of light at the proper wavelength 25. List and explain three factors that can lead to a loss of signal strength in fiber optic cable? a. Scattering – explain each … b. Absorption c. Dispersion CCNA 1: Networking Basics V 3.0 4 3/6/2016 26. When the fiber has been pulled, the ends of the fiber must be cleaved (cut) and properly polished to ensure that the ends are smooth. Improperly installed connectors, improper splices, or the splicing of two cables with different core sizes will dramatically _________________ of a light signal. 27. After the fiber-optic cable and connectors have been installed, the connectors and the ends of the fibers must be kept _______________. The ends of the fibers should be covered with protective covers to prevent ______________ to the fiber ends. When these covers are removed prior to connecting the fiber to a port on a switch or a router, the fiber ends must be cleaned. Clean the fiber ends with lint free lens tissue moistened with isopropyl alcohol. The fiber ports on a switch or router should also be kept covered when not in use and cleaned with lens tissue and isopropyl alcohol before a connection is made. Dirty ends on a fiber will cause a drop in the amount of light that reaches the receiver. 28. Explain what an optical link loss budget is. When a fiber-optic link is being planned, the amount of signal power loss that can be tolerated must be calculated. 29. Which wireless standard operates at 1, 2, 5.5 and 11 Mbps. 30. What is the minimum number of devices that can make up a wireless network? 31. Explain scanning. When a client is activated within the WLAN, it will start "listening" for a compatible device with which to "associate". This is referred to as "scanning" and may be active or passive. 32. When a source node on a wireless LAN sends a frame, the receiving node returns a positive acknowledgment (ACK). This can cause consumption of _____ of the available bandwidth. This overhead when combined with the collision avoidance protocol overhead reduces the actual data throughput to a maximum of 5.0 to 5.5 Mbps on an 802.11b wireless LAN rated at ________. 33. Explain the following authentication and association types: Unauthenticated and unassociated Authenticated and unassociated Authenticated and associated The node is connected to the network and able to transmit and receive data through the access point. 34. List and explain the three basic ways in which a radio carrier signals can be modulated. CCNA 1: Networking Basics V 3.0 5 3/6/2016 a. Amplitude Modulated (AM) radio stations modulate the height (amplitude) of the carrier signal. b. Frequency Modulated (FM) radio stations modulate the frequency of the carrier signal as determined by the electrical signal from the microphone. c. Phase Modulation is used to superimpose the data signal onto the carrier signal that is broadcast by the transmitter. 35. Which devices can cause interference in home and small office wireless networks? a. b. 2.4GHZ Wireless phones 36. List and explain several security solutions or protocols used in WLANs. a. EAP-MD5 Challenge – Extensible Authentication Protocol is the earliest b. c. d. e. authentication type, which is very similar to CHAP password protection on a wired network. LEAP (Cisco) – Lightweight Extensible Authentication Protocol is the type primarily used on Cisco WLAN access points. LEAP provides security during credential exchange, encrypts using dynamic WEP keys, and supports mutual authentication. User authentication – Allows only authorized users to connect, send and receive data over the wireless network. Encryption – Provides encryption services further protecting the data from intruders. Data authentication – Ensures the integrity of the data, authenticating source and destination devices. CCNA 1: Networking Basics V 3.0 6 3/6/2016