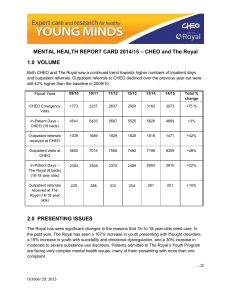
Access Control to Information Systems
advertisement

Access Control to Information Systems Manual/Section: Administrative/Information Services Policy No. 160 Key Words: security, access, remote access, special access, remote control 1. PURPOSE: 2. POLICY: 1.1 Define procedures for managing local and remote access to Children’s Hospital of Eastern Ontario (CHEO) Information Systems. 1.2 Define procedures for managing the software and hardware used by CHEO. 1.3 Protect CHEO’s Information systems’ confidentiality, integrity and availability. 1.4 Uphold CHEO’s obligations under the Personal Health Information Protection Act (PHIPA) and other statutes not to disclose or make use of information/data except for purposes specified in those acts and as described and applied in CHEO’s Confidentiality Agreement (Form No 6021). 2.1 Any individual who does not comply with this policy shall be subject to appropriate action, up to and including termination. 2.2 System Access: Information Technology (IT) equipment belonging to CHEO shall only be operated by authorized individuals. All individuals with access to these systems must ensure that they do not operate IT equipment or access information without possessing the proper authorization for that equipment or information. 2.2.1 Access to CHEO’s Information Systems will not be granted until the individual signs the Information System Access Control form (Form No 4056) that outlines the conditions of access CHEO’s Information Systems. Individual’s Director must submit to CHEO’s IS Helpdesk the Information Systems Access Control form that contains the list of IT resources individuals need to perform their job duties. 2.2.2 Administrative Access-level users must ensure that they are sufficiently trained and aware of the various operating systems and software configurations in their designated area of the CHEO IS environment. 2.2.3 Individuals must request Remote Access privilege from their Director and receive authorization before attempting to access any CHEO’s IT resources from a remote location. Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 1 2.2.4 End users are not to attempt to gain access to any system, data or programs for which they do not have explicit authorization or consent from their Director through a signed Access to Information Systems Control Form. 2.2.5 User IDs, passwords, and authentication devices should not be shared, given, or used by any person other than the person to whom they were issued. If the practice of sharing is determined as required, the Department Director assumes responsibility and accountability for the security and privacy of information. 2.3 Software: CHEO may specify or prohibit software which will be processed on Hospital IT equipment used to access IT resources. 2.3.1 Without prior written authorization from CHEO, users may not: a) Copy software for use on their home/ personal computers. b) Provide copies of software to any independent contractor or clients of CHEO or to any third party. c) Install software on any of CHEO’s IT equipment. d) Download any software from the Internet or other online source to any of CHEO’s IT equipment. e) Modify, decompile, transform, reverse-engineer, or adapt any software. 2.3.2 All requests for new software for use on CHEO IT equipment must go through approval process (Appendix A) and be requested through IS Helpdesk to be placed on any CHEO IT equipment. 2.3.3 In the event when an urgent ad-hoc software download is required to fulfill job related duties, prior authorization from reporting Director is required. Both the user and reporting Director are responsible for ensuring license compliance and that downloaded software is taken from a safe and workrelated site. Follow-up communication to IS Helpdesk is required. 2.3.4 Using manual or automated methods, CHEO IS may periodically audit IT equipment that has been used to access CHEO IT Resources to determine if appropriate software is being used. Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 2 2.4 Hardware: Only IT equipment that is approved and configured appropriately by IS Department can be connected to CHEO’s trusted network. If non-standard IT equipment needs to be used, IS Department will assess device features to determine the compatibility with other CHEO’s IT equipment. If deemed compatible and secure IS Department will provide limited "best effort" assistance in connecting the device to the public portion of the network and installing Citrix client. 2.4.1 Disposal of all returned, surplus or damaged equipment shall be carried out with the participation of the IS Department. 2.5 Malicious Code Management: All Users are responsible for preventing virus infection of CHEO’s IT equipment. IT equipment being used to access CHEO’s IT resources is required to have a virus detection software installed and will be enabled with current virus definitions. Any removable storage device used to transfer information from one machine to another must be scanned for viruses prior to accessing the information stored on the device. All items downloaded from the Internet or received from an untrusted source must be scanned for viruses prior to execution. 2.5.1 CHEO has the ability to, and will randomly scan all systems, communications equipment and computers to ensure adherence of this and other related policies. 2.6 Data Transmission: Sensitive information should not be transmitted over unprotected communication lines or Public medium such as the Internet. 2.6.1 Encryption should be used for the transmission of sensitive information if sent over unprotected communication lines or Public medium such as the Internet. 2.6.2 Network access control devices such as firewalls will be implemented to prevent access to sensitive information by unauthorized individuals. 2.6.3 Users of CHEO’s Remote Access services will not use or configure those services to act as servers for other users or the general public, unless specifically authorized by IS Department. 2.6.4 In the event a private computer system is being used to process corporate information/data, it is the user’s responsibility to ensure proper data encryption, confidentiality and safe storage of information is adhered to. 2.7 Approved by: Executive Team Revision Number: 1 Data Protection: CHEO IS Department will backup data residing in designated locations on scheduled basis. All information/data backed up will be stored in an approved Date: April 20, 2010 3 manner, depending on level of sensitivity. 2.7.1 2.8 Users saving sensitive information outside of CHEO’s IS Systems are responsible for preventing unauthorized access to it. This includes but not limited to: a) Encrypt data on Universal Serial Bus (USB) sticks. b) Encrypt or password protect sensitive files on optical and magnetic removable media. c) Encrypt or password protect information stored on portable IT equipment. d) Periodically check portable IT equipment for malicious code and report infections to IS Helpdesk Physical Security: Media control and destruction shall only be carried out under the authorization of CHEO IS. All CHEO IT devices must be physically protected to the value of the equipment and /or the highest sensitivity level of the information/data processed. 2.8.1 Users utilizing portable IT equipment and removable media (USB memory, optical and magnetic media) must take reasonable precaution to ensure physical security of these devices. Users should never leave these devices unattended and must notify Hospital IS Helpdesk and CHEO Security immediately if the device is missing. 3. SCOPE: 4. DEFINITIONS: 2.9 Auditing and Monitoring: As an owner of IT resources with vested interest in its performance and security, CHEO IS Department is obliged to audit and monitor those resources to ensure that they are secure from damage (for example, through computer viruses or excessive, unauthorized use of computer memory resources) and are used only for authorized purposes. 3.1 All CHEO IT equipment, systems and services owned, leased, or in the custody of CHEO 3.2 All CHEO Users inclusive of the Research Institute 3.3 All CHEO information systems records Administrative access: is higher level of access control to a system or application that allows such user to perform configuration changes and to establish access privileges for other users of the system. This level of access is typically restricted to IS personnel or approved vendors and contractors. Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 4 BSA: is Business Systems Analyst from IS Department at CHEO who is responsible for applications. CHEO IS: Information Services Department at CHEO. CHEO IS Helpdesk: is team within IS Department that provides front-line support to CHEO users. CHEOnet: is CHEO’s intranet (internal website). CHEO public network: is portion of CHEO wired or wireless network that is allowed for use by patients and visitors (similar to airport hot spot). CHEO trusted network: is portion of CHEO wired or wireless network that is reserved for use by CHEO staff using trusted devices approved and maintained by Hospital IS Department. Citrix: is a remote access and application delivery solution that allows Users to connect to applications available from central servers. Designated locations: are network file shares (example: J:\ Drive) Encryption: is the process of transforming information (referred to as plain text) using an algorithm (called cipher) to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. Firewall: is a dedicated appliance or software running on another computer, which inspects network traffic passing through it, and denies or permits passage based on a set of rules. Individual: is any person who does not meet the criteria of “User”. IT equipment: is any computing hardware used to access, process and store or transmit CHEO information (ex. Personal Computer (PC) or server). Portable IT equipment includes laptop, tablet PC, handhelds and smartphones. IT resource: is any tool or application that is used in CHEO and is maintained by CHEO IS Department (ex. shared network drive, ADT application or printer). Remote Access: is the ability to access a CHEO computer, network drive, or application from a remote location. Remote access is applicable to many forms of connectivity methodologies including but not limited to dial-up, VPN, and Citrix. Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 5 Remote Control: is remote monitoring/assistance software employed to assist users with problems by being able to access their desktop remotely. Sensitive Data: any information that CHEO has obtained and is responsible for according to the applicable provincial and federal legislation. This term also includes any CHEO internal information that may harm its public image. This may include but not limited to Patient, Corporate and HR information. User: is an individual who has authorized access to the Hospital information systems and has signed the “Confidentiality Agreement”(Form No. 6021) VPN (virtual private network): is a connectivity method that creates a secure tunnel connection between remote user/location and company IT resources over a public network infrastructure such as Internet. Data passing between the two ends of the tunnel is encrypted. 5. RESPONSIBILITY: 5.1 Directors are responsible: to ensure that they grant access to appropriate CHEO IT resources only to those individuals who require this access in order to perform their job duties. For signing and submitting an “Information Systems Access Control” form. Informing IS Department when access to an IT resource is no longer needed due to the employment status change or other reason. When in doubt consult with IS Department to determine the appropriate access level for a User to adequately perform their job duties. This document is to be forwarded to CHEO’s IS Helpdesk who will initiate the account provisioning process to estimate and absorb any licensing and additional IS related costs of granting access (ex. network and voice connections). If in doubt Directors should consult with IS Department to determine these costs. to approve and ensure license compliance for any urgent ad hoc software downloads. 5.2 IS Department is responsible: for the optimal configuration, availability, data protection and security of CHEO IT resources. for software license control and asset management will be carried out by IS Department Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 6 for ensuring compliance for compiling a list of Users with access to CHEO’s IT resources. 5.3 All Users are responsible: for ensuring conditions set out in this policy are adhered to and report any violations to their supervisor or IS Department to store all sensitive data in designated locations for complying with the terms of the applicable software license agreements 5.4 6. PROCEDURE: Human Resources (HR) and Office of Medical Staff are responsible: for storing the signed “Confidentiality Agreement” form on each individual’s file for providing individuals with copies of the Acceptable Use of Information Systems and Privacy and Confidentiality of Personal Health Information policies upon hiring. New user accounts creation and change of access 6.1 Any individual wanting to access CHEO’s IT resources on CHEO’s grounds must have CHEO’s identification as described in Employee Identification Policy and agree with provisions of this policy and “Acceptable Use of Information Systems Policy” by signing “Confidentiality Agreement” form If individual will only access CHEO’s IT resources remotely (vendor support, consultants, affiliated providers, etc.), initiating Director must validate the identity of the individual and securely communicate the user ID and password. At IS Management discretion “Confidentiality Agreement” form can be replaced with appropriate Non-Disclosure Agreement or Data Sharing Agreement. 6.2 CHEO’s IS Helpdesk will create the network account, email box and forward access request to the appropriate BSAs if access to clinical or enterprise systems is required. BSAs will provision the applications accounts and arrange for appropriate training. CHEO’s IS Department will retain all signed copies of “Information Systems Access Control” form. 6.3 CHEO’s IS Helpdesk will confirm that the individual’s work location is equipped with appropriate data and voice connections, and if required, will arrange for the work to be completed. Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 7 6.4 On the first day of work, the user must report to CHEO’s IS Helpdesk to obtain their account information and to reset their network password. The user will receive brief instruction on how to logon to CHEO’s network. The temporary password is set to expire at the time of the first login. At that time, the user will be required to enter a new password as per Acceptable Use of Information Systems Policy. 6.5 If changes to the existing user’s access are required, an “Information Systems Access Control” form will be completed by the Director and forwarded to CHEO’s IS Helpdesk to initiate the change process. If access to clinical or enterprise systems is required, CHEO’s IS Helpdesk will forward access change request to the BSA responsible for the application. The BSA will make changes to the existing account reflecting the changes in access level and arrange for appropriate training. Terminations of employment with CHEO 6.6 The Director will notify CHEO’s IS Helpdesk when a user has been terminated. CHEO’s IS Helpdesk will forward an access revocation request to the BSAs to disable the applications accounts as of the effective date or has left employment with the hospital. CHEO’s IS Helpdesk will set the network account to expire at the last day of employment and disable any remote access privileges. User’s account information, emails and files will be retained for a minimum of three (3) months after which time all this data will be purged. Any time within this three (3) month period reporting Director may request CHEO’s IS Helpdesk to forward new incoming email, move old email and old files to another user. 6.7 In case of immediate dismissal CHEO Senior Management will notify IS Management immediately to disable all access privileges for affected user(s). Remote Access 6.8 Remote access is authorized by the user’s Director through the “Information Systems Access Control” form forwarded to CHEO IS Helpdesk who will notify the user and arrange for the installation of the remote access client and appropriate training. General Access 6.9 Approved by: Executive Team Revision Number: 1 To have their application or network password reset, users must report to IS Helpdesk in person and provide CHEO’s Date: April 20, 2010 8 identification (Employee Identification Policy). For password resets outside of normal IS Helpdesk hours users must report to switchboard or CHEO Security for their identity validation. Once their identity is confirmed, IS Helpdesk on-call will reset user’s password remotely. 6.10 For general use and management of systems, regular user accounts should be used. System accounts should only be used for performing the tasks they were issued to conduct. 6.11 When CHEO IS Staff access a User’s PC using the remote control tools, they will always ask the user for permission as a common courtesy. In the event that the User is not present, the IS staff will leave a note [e.g. via email] explaining the activity that took place in his/her absence. Exceptions to this protocol will occur in an emergency situation or on direction from CHEO Senior Management. 6.12 Log files for remote control tools will be turned on when in use and monitored by CHEO IS Management. Patient Information 6.13 Patients/Patient Guardians who require access to personal health information that is stored in digital format may do so through an authorized clinical provider from CHEO in accordance with the Access to and Disclosure of Patient Health Information Policy. 7. CROSSREFERENCES: CHEO, Acceptable Use of Information Systems Policy CHEO, Access to and Disclosure of Patient Health Information Policy CHEO, Employee Identification Policy CHEO, Privacy And Confidentiality of Patient Personal Health Information Policy Information System access Control (Form No 4056) Confidentiality Agreement (Form No 6021) 8. REFERENCES: 9. ATTACHMENTS Appendix A: New Software Approval Process 10. DEVELOPED BY: Pavlo Ignatusha, Manager, Information Services Brian Vezina, Senior Business Systems Analyst, Information Services Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 9 Appendix A New Software Approval Process Software Request Requirements Analysis Requirement Confirmed? No Yes Change Advisory Board Approval? No No Is the Package Supported? Yes Yes Terms & Conditions Disclaimer Sent to User Do we need to Buy License? No Yes Request Dropped No Does the Requestor want to Proceed? Yes Standard Procurement Once Purchase Order Sent Schedule Installation Status Updates Infor Purchasing System Notes 1. Need Standard Terms & Conditions for use of Non-Supported Software 2. Establish List of Supported, NonSupported (rest is prohibited) 3. Establish Regular Review of Non-Supported Software to see if should indeed be Supported. Approved by: Executive Team Revision Number: 1 Date: April 20, 2010 10