Wireshark Tutorial – Part 1
advertisement

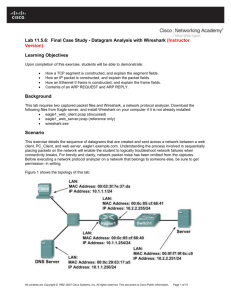
Mobile and Distributed Computing Systems Semester 1 2009 Wireshark Tutorial – Part 1 HTTP and TCP Objective In this tutorial, you will learn how to use Wireshark. Wireshark is a live network monitoring and packet analysing tool. In this exercise, you will use Wireshark to capture live network packets while making a HTTP connection and investigate the packets trying to answer the questions below. Procedure: 1. 2. 3. 4. Start wireshark Click on Capture->Interfaces Click on options next to the interface named DLink DWA547 Leave all options to default except the option “Capture packets in promiscuous mode” ->In windows this option does not work 5. Click on start 6. Open Internet explorer 7. Open any website 8. Click a few links 9. Close IE 10. Stop the packet capture (Capture->stop) Analysis: 1. DNS ? What is it. Do you see DNS packets. Why are they used ? Identify the IP address of the webserver to which you connected from the DNS packet (If you don’t see DNS packets, try to enter a new website and not just www.google.com as this might be in the cache) 2. Which underlying protocol does HTTP use ? Identify the TCP three way handshake from the captured packets 3. Use the Follow TCP Stream from Analyse->Follow TCP Stream to look at the HTTP packets 4. Do you see FIN in the packet. Use step 3 to reconstruct the entire TCP stream and identify why FIN is used PS: Using wireshark to monitor data link layer packets in promiscuous mode is possible but does not work under windows with the DLINK network card. You can still try it at your own time on a linux machine. The following are some useful links to get it working Wireshark Information on WLAN capture setup using Linux http://wiki.wireshark.org/CaptureSetup/WLAN#head7d5b1ad712c3556edc8f0687640caaa056a75706 A open source Linux driver that support Wireshark promiscuous monitoring showing data link layer packets. http://en.opensuse.org/Atheros_madwifi The PDF document resource Wireless Sniffing with Wireshark.pdf