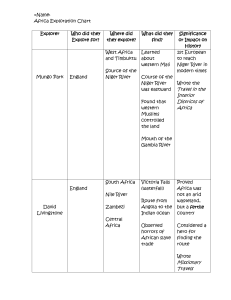
TimbuktuPro
The #1 Remote Control and File Transfer Software
Contents
1
Introduction
1
Application Level Security
2
Network Level Security
2
Usage Examples
4
Summary
4
Appendix A–Setting Up a
Firewall for Timbuktu Pro
5
Appendix B–Differences
Among the Timbuktu Pro
Family
Timbuktu Pro Enterprise
Security White Paper
A secure approach to deployment
of remote control technology
TimbuktuPro
Introduction
Master Password
Netopia has gone to great lengths to ensure that the
security features built into the Timbuktu Pro line of
software are not only stringent enough to meet IS
needs, but have the flexibility to work with existing
security standards such as firewall, Virtual Private
Networks (VPN), PAP, CHAP, Point-to-Point Tunneling
Protocol (PPTP), SecureID™, etc.
Timbuktu Pro can be configured with a Master
Password to prevent any changes to the security
specifications on a machine. When configured in this
way, Timbuktu Pro requires the correct Master
Password whenever somebody tries to change security-related preferences, such as the defined users or
incoming access.
This high level of security allows Timbuktu Pro to be
an essential tool for safety conscious organizations
such as Banker’s Trust, the Pentagon and Hughes
Aircraft.
Site Keys and Administrators
Timbuktu Pro’s security can be divided into application level security and network level security.
Application level security refers to features in
Timbuktu Pro that make it a secure application on
your network. The network level security section of
this document illustrates how Timbuktu Pro interacts
with security hardware and software already in
place on your network.
Application Level Security
Password Protection (User level access)
At its most basic level, Timbuktu Pro is designed to
require a specific user name and password for each
person needing access to a given machine. In addition, users can be set up with varying levels of access
depending on their individual needs. For example, a
Timbuktu Pro machine can be easily configured so
that one or more remote accounts have “control
access” for administrative purposes, others have
“observe access” for training purposes, and all
accounts have send privileges to facilitate communication and collaboration across the Intranet.
The Timbuktu Site Key Generator can be used to
enforce the established security policy for corporate
use of Timbuktu Pro. Enforcement can involve disabling various features, modifying the TCP ports used
for Timbuktu Pro, requiring Site Keys in order to connect to members of the site, and restricting modifications after the initial installment and configuration of
Timbuktu Pro.
Secure Screen Blanking
Timbuktu Pro for Windows supports secure screen
blanking on Windows NT and Windows 95
machines. When this option is enabled, a remote
control session will automatically blank the screen on
the host, preventing the disclosure of any sensitive or
confidential information to somebody with physical
access to the host machine.
Remote Control Notification
Timbuktu Pro for Windows can be configured to
warn you of active remote control or observe sessions in two ways. You either can configure it to
beep periodically, show a warning dialog, or both.
This feature ensures that you don’t inadvertently display sensitive information while somebody observes
your screen.
Attended Access
Activity Logging
In attended access mode, access can be restricted
only to specifically authorized users. Here, the user of
the Timbuktu Pro machine must specifically authorize–on a per-session basis–any incoming connections. For maximum security, the administrator can
permit only attended access mode.
Every Timbuktu Pro connection established to a
machine is logged to an Activity Log. This file is a
continuous record of which machines (including IP
addresses where applicable) have used a given service. This information is logged in a standard format
and may be audited on a regular basis for security
violations. Under Windows NT, Timbuktu Pro also
logs connection information to the Application Event
Log. This enables integration with standard Windows
NT monitoring and auditing software.
1
TimbuktuPro
Network Level Security
Network Management Integration
Firewalls
Timbuktu Pro is integrated with popular network management and help desk software such as SMS and
Remedy. This integration lets a Network
Administrator automatically use Timbuktu Pro’s
remote control capability to access a machine from
within their existing network management software.
Virtually every corporate LAN connected to the
Internet has a firewall in place. Because of its flexible TCP/IP implementation, Timbuktu Pro can be
blocked or permitted on a service-by-service basis at
the firewall level. Every service that Timbuktu Pro
provides can be configured with the Site Key
Generator for distinct and unique TCP/IP ports. For
example, the firewall could be configured to allow
Observe and Send to take place across a WAN, but
prohibit services like Control and Exchange Files
across insecure connections.
Usage Example
The following examples are accounts of how
Timbuktu Pro can be used in a corporate environment. They are examples based on feedback that
Netopia’s Technical Support department received
from customers.
See Appendix A for detailed information involving
firewall configuration.
Example 1
Virtual Private Networks (VPNs)
The problem:
A Virtual Private Network allows secure communication over a connection that would normally be either
blocked by a firewall or unsuitable for sensitive material due to the inherent insecurity of Internet communications. A number of companies are providing
VPNs as either stand-alone products or as add-ons to
firewalls. These VPNs are capable of encrypting an
entire WAN connection, tunneling it through the
Internet or some other insecure link, and decrypting
it at the other end, all the while ensuring the data hasn’t been tampered with or spied on while in transit.
Many such VPNs are capable of 128-bit encryption,
which is more than suitable for today’s computing
technology. Please see Example 3 in the Usage
Example section for details on how such technologies
can be used in conjunction with Timbuktu Pro.
Company A is a financial organization that needed
a more effective way of supporting and training their
users. They were experiencing two problems:
Remote Access Authentication
In order to prevent dial-up users from gaining access,
you can require various levels of authentication from
your Remote Access Server (RAS). Because Timbuktu
Pro for Windows doesn’t contain a direct dial component, it is possible to require that remote access
users go through a standard security mechanism such
as PAP or CHAP PPP access as well as have a closely monitored central RAS box. For the highest level of
security, you can supplement PPP access with
SecureID (or other token-card technology) to ensure
that only authorized users are able to access your
LAN and your Timbuktu Pro resources.
1. Users were frustrated by the time required to
get support from the help desk
2. The help desk was department frustrated with
the amount of time and effort spent fixing or
explaining simple problems.
Management did not want to double the help desk
staff in order to meet the needs of the end users in a
timely fashion.
The solution:
In a pilot program, Timbuktu Pro was rolled out to
two help desk people and twenty end users.
Whenever any of these users required support, they
used the standard mechanism already in place to
contact the help desk. Without ever leaving their
seats, the help desk was able to observe or control
the user’s screen in attended access mode and either
fix the software problem or demonstrate how to
accomplish a task. Timbuktu Pro had the necessary
components to effectively double the productivity and
responsiveness of the help desk department without
any staffing changes.
TimbuktuPro
The security:
This organization was extremely security conscious,
but had fairly simple requirements for Timbuktu Pro.
They had an Internet connection, but didn’t want
Timbuktu Pro to be accessible across the Internet.
Since their existing firewall implementation completely blocked the IP ports used by Timbuktu Pro, this was
not a problem. They eventually installed Timbuktu Pro
on every user’s machine for support purposes, but
didn’t want or need to take advantage of the peer-topeer collaboration capabilities of the software. This
was easily addressed by having a corporate–wide
Site Key that was pre-installed on all Timbuktu Pro
machines. This Site Key locked down the preferences
so that only somebody with the administrator’s key
was able to connect. The help desk department then
installed the administrator’s key on all of their
machines so only they could connect to the users with
Timbuktu Pro.
Example 2
The problem:
Company B was in a similar situation to Company A.
However, as a computer manufacturer targeting vertical markets, they wanted to provide technical support to their customers using the same tools the help
desk used to provide internal support.
The solution:
Similar to Example 1, Company B used a corporate–wide Site Key, but allowed employees to use
Timbuktu Pro for collaboration purposes. Their
employees find Timbuktu Pro to be an extremely useful tool for sending files and ideas to coworkers
instantaneously. Company B also purchased a site
license allowing them to ship Timbuktu Pro to any customer with a support contract. When Company B’s
support staff communicates via phone or email with
a customer, they are able to use their existing Internet
connection to provide the same kind of support their
help desk provides internally.
The security:
Company B used their existing firewall implementation to block incoming Timbuktu Pro connections, and
rolled out a less restrictive Site Key that allowed peerto-peer usage of Timbuktu Pro while still providing the
help desk benefits outlined in Example 1. The
machines used for external customer support were
put in an external “no-mans-land” between two levels
of firewall. Most importantly, these machines were
located outside of a firewall to ensure that even if a
machine used for support is compromised, it will not
be a risk to corporate data or security since no sensitive information is stored on these machines, and
the firewall prevents these machines from being used
to leapfrog into the internal network. Also, there is a
useful external firewall protecting these external support machines from non-Timbuktu attacks such as
SYN-ACK denial of service and routed packets.
Example 3
The goal:
Company C is a global organization with locations
in twenty U.S. states and thirteen countries. Their primary use of Timbuktu Pro is collaboration, as well as
administering about 75 file servers, web servers, and
application servers running Windows NT. All of their
offices are connected via various methods to a single
WAN. Many of their connections are over dedicated
leased lines, but nearly half tunnel their WAN connection through the Internet to reduce the costs of
leasing high-speed international data lines.
The solution:
Timbuktu Pro is running on virtually every machine in
the company and is used in a number of different
ways.
1. The web masters use it to administer their web
servers for both internal and external information publishing.
2. The engineers use it to share ideas and files
among themselves, and to quickly facilitate a
review process between engineering, QA, product management, and marketing.
3. The sales force uses it to access information on
their desktop machines when they are dialed in
to the corporate network while traveling.
The security:
These links are secured with Virtual Private Network
technology. Some of these VPNs use the Point-to-Point
Tunneling Protocol available in Windows NT and
many modern routers while others use more proprietary VPNs from Trusted Information Systems (TIS) —
a well–regarded firewall manufacturer. In both cases,
these VPNs are used to provide an encrypted LAN-toLAN connection that can be tunneled over any
3
TimbuktuPro
Internet connection. Because they have no need to
communicate outside of their own network, their
external links to the Internet are configured to completely block Timbuktu Pro traffic. Site Keys are used
only on the servers that need to be administered and
only the server administrators are provided with the
administration keys for these machines.
Timbuktu Pro UDP Ports
Summary
Control
Observe
Send Files
Exchange Files
Chat
Timbuktu Pro has an extensive set of security features
built into it. Even more important, it has been
designed from the ground up to be flexible enough to
work with and extend a corporation’s existing security policies and mechanisms. This document is an
introductory look at the ways Timbuktu Pro’s administration, communication, and collaboration features
can be securely used on your network. Netopia has
focused for years on the security needs of a corporate network, and our support department can assist
you in design and implementation of Timbuktu Pro
usage on your network. If you would like to discuss
implementation possibilities or problems, or if you
have some unique requirements that aren’t addressed
by this document or the Timbuktu Pro feature set, contact us to see exactly how our product can be adapted to meet your needs.
Appendix A–Setting Up a Firewall
for Timbuktu Pro
For security reasons, network managers on TCP/IP
networks usually want to restrict external access to
their networks. Most of the time they will only open
TCP/UDP ports for Telnet, FTP and other common services. To do that, they will configure their IP routers
(sometimes referred to as gateways) to filter out
access to different ports. These filters are usually
referred to as “firewalls”.
TCP/IP security firewalls may be configured in ways
that selectively allow or block various types of
Timbuktu Pro connections. The firewall administrator
should configure the firewall for use with Timbuktu
Pro to meet the needs of the corporate security policy.
Timbuktu Pro uses well-defined UDP Port 407 for connection handshaking. Once the UDP connection is
established, Timbuktu Pro uses TCP ports for each of
the seven types of Timbuktu sessions.
Connection (handshaking) - UDP Port 407
(Timbuktu Pro for MacOS and Netopia Virtual Office
use UDP port 1419)
Timbuktu Pro TCP Ports
Notify
Intercom
TCP port 1417
TCP port 1418
TCP port 1419
TCP port 1420
Dynamic TCP port (NVO and
Timbuktu for MacOS only)
Dynamic TCP port (NVO and
Timbuktu for MacOS only)
Dynamic UDP and TCP ports
(NVO and Timbuktu for MacOS
only)
These ports are used during access from “registered
users” - those users who have valid user accounts and
passwords on the Timbuktu Pro hosts. Any or all of
these ports can be firewalled to ensure security from
unauthorized users. Some network managers will firewall all ports, but allow a connection to be established to UDP Port 407 and TCP Port 1419. This
allows anyone on the Internet to send files via
Timbuktu Pro. The Timbuktu Administrator’s Toolkit
(included with the Timbuktu Pro for Enterprise package) provides the ability for network administrators to
reconfigure the TCP ports used by Timbuktu Pro.
However, UDP Port 407 and 1419 cannot be
changed.
Timbuktu Pro also supports “attended access” from
temporary guests where the host’s user admits a
guest on a one-time basis without requiring a password. Timbuktu Pro defaults to using a dynamic port
assignment for attended access connections thereby
bypassing the firewall on the static ports. If network
administrators wish to firewall this attended access
feature, they can simply assign it to a static port using
the Administrator’s Toolkit.
Registered port numbers are used only by computers
receiving a connection. Users who initiate connections are using dynamic port numbers. A dynamic
TCP port is negotiated by the two computers involved
in a Timbuktu Pro connection. Dynamic ports usually
have numbers greater than 1023. If these dynamic
ports are firewalled, Timbuktu Pro will not be able to
complete a TCP/IP connection.
The network manager will need to re-configure the
TimbuktuPro
firewall permissions to permit TCP and UDP port
assignments. Refer to the firewall or router documentation for details. If the default TCP port assignments
are not the preferred ones, a network administrator
can use the Timbuktu Pro Administrator’s Toolkit to
designate which TCP/IP ports are used for Timbuktu
Pro services throughout the site. For information
about the Toolkit, contact Netopia’s Customer Service
at (510) 814-5000.
Netopia Virtual Office
While Netopia Virtual Office doesn’t contain
“Timbuktu” in the product name, it does use Timbuktu
Pro Remote Control and File Transfer technology.
Therefore, this document applies equally to both
Timbuktu Pro and Netopia Virtual Office. In addition
to the features covered in this document, Netopia
Virtual Office 1.1 also contains a miniature web server. This HTTP server operates on TCP port 80 by
default, but can be overridden with a Site Key.
Appendix B–Differences Among the
Timbuktu Pro Family
Timbuktu Pro for Windows
All portions of this document are relevant to Timbuktu
Pro for Windows 1.5x. References to the Chat and
Intercom features are not currently available in this
product. Versions of Timbuktu Pro prior to 1.5 do not
support all of the Window’s NT specific features. If
you are running Window’s NT and have an earlier
version of Timbuktu Pro, contact Netopia to upgrade
to 1.5.
Timbuktu Pro for MacOS
Timbuktu Pro for MacOS supports two transports protocols that are not found in the Windows version and
may require special considerations.
The first transport is AppleTalk. If your network uses
the AppleTalk protocol, then Timbuktu Pro for MacOS
can take advantage of this for easy communications
between Macintoshes on the LAN. Unless you have
AppleTalk bridges to untested networks, this will not
be a security concern.
The second Mac specific transport is Dial Direct. This
feature allows two machines with Timbuktu Pro for
MacOS to communicate directly with each other over
a modem without going through a network connection. To address security concerns about unmonitored remote access and remote control, this feature
can be configured and/or disabled with a Site Key.
In addition, Timbuktu Pro 4.0 introduces a feature
allowing a network administrator to monitor the network for machines configured for Direct Dial. For further information about this feature, contact Netopia
at 510-814-5000.
5
TimbuktuPro
More than five million network users and 300,000 network administrators depend on Netopia innovation. Since
1986, Netopia has been the industry leader in providing
networking products that connect personal computers, and
help users communicate quickly, easily, and effectively.
With products for PCs, Macs, notebooks, workstations,
and printers, Netopia offers easy-to-use solutinos for connectivity and communications.
Netopia, Inc.
2470 Mariner Square Loop
Alameda, CA 94501-1010
USA
(510) 814-5000
(510) 814-5023 Fax
©1997 Netopia, Inc. All rights reserved. All trademarks
are the property of their respective holders. Printed in the
USA. v.1097.
ZPK800