ECE 358: Computer Networks Homework #3 Chapter 5 and 6
advertisement

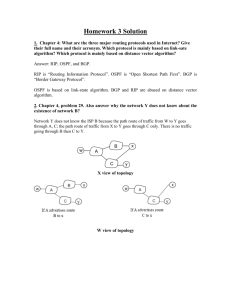
ECE 358: Computer Networks Homework #3 Chapter 5 and 6 Review Questions1 Chapter 5: The Link Layer P26. Let's consider the operation of a learning switch in the context of a network in which 6 nodes labeled A through F are star connected into an Ethernet switch. Suppose that (i) B sends a frame to E, (ii) E replies with a frame to B, (iii) A sends a frame to B, (iv) B replies with a frame to A. The switch table is initially empty. Show the state of the switch table before and after each of these events. For each of these events, identify the link(s) on which the transmitted frame will be forwarded, and briefly justify your answers. Solution: Action Switch Table State is Explanation B sends a frame Switch learns interface A, C, D, E, and F to E corresponding to MAC address of B Since switch table is empty, so switch does not know the interface corresponding to MAC address of E E replies with a Switch learns interface B frame to B corresponding to MAC address of E Since switch already knows interface corresponding to MAC address of B A sends a frame Switch learns the interface B to B corresponding to MAC address of A Since switch already knows the interface corresponding to MAC address of B B replies with a Switch table state remains A frame to A the same as before Since switch already knows the interface corresponding to MAC address of A 1 Link(s) packet forwarded to Th From the textbook (Computer Networking: A Top-­‐Down Approach, 6 edition) Pages 508, 579 & 581 P27. In this problem, we explore the use of small packets for Voice-over IP applications. One of the drawbacks of a small packet size is that a large fraction of link bandwidth is consumed by overhead bytes. To this end, suppose that the packet consists of L bytes and 5 bytes of header. a. Consider sending a digitally encoded voice source directly. Suppose the source is encoded at a constant rate of 128 kbps. Assume each packet is entirely filled before the source sends the packet into the network. The time required to fill a packet is the packetization delay. In terms of L, determine the packetization delay in milliseconds. b. Packetization delays greater than 20 msec. can cause a noticeable and unpleasant echo. Determine the packetization delay for L = 1,500 bytes (roughly corresponding to a maximumsized Ethernet packet) and for L = 50 (corresponding to an ATM packet). c. Calculate the store-and-forward delay at a single switch for a link rate of R = 622 Mbps for L=1,500 bytes, and for L = 50 bytes. d. Comment on the advantages of using a small packet size. Solution a) The time required to fill L ⋅ 8 bits is L ⋅8 L sec = m sec . 3 16 128 ×10 b) For L = 1,500, the packetization delay is 1500 m sec = 93.75m sec. 16 For L = 50, the packetization delay is 50 m sec = 3.125m sec . 16 c) Store-and-forward delay = L ⋅ 8 + 40 R For L = 1,500 , the delay is 1500 ⋅ 8 + 40 sec ≈ 19.4µ sec 622 × 10 6 For L = 50, store-and-forward delay < 1µ sec . d) Store-and-forward delay is small for both cases for typical link speeds. However, packetization delay for L = 1500 is too large for real-time voice applications. Chapter 6: Wireless Networks R6. True or false: Before an 802.11 station transmits a data frame; it must first send an RTS frame and receive a corresponding CTS frame. False R10. Suppose the IEEE 802.11 RTS and CTS frames were as long as the standard DATA and ACK frames. Would there be any advantage to using the CTS and RTS frames? Why or why not? Solution No, there wouldn’t be any advantage. Suppose there are two stations that want to transmit at the same time, and they both use RTS/CTS. If the RTS frame is as long as a DATA frames, the channel would be wasted for as long as it would have been wasted for two colliding DATA frames. Thus, the RTS/CTS exchange is only useful when the RTS/CTS frames are significantly smaller than the DATA frames. P7. Suppose an 802.11b station is configured to always reserve the channel with the RTS/CTS sequence. Suppose this station suddenly wants to transmit 1,000 bytes of data, and all other stations are idle at this time. As a function of SIFS and DIFS, and ignoring propagation delay and assuming no bit errors, calculate the time required to transmit the frame and receive the acknowledgment. Solution A frame without data is 32 bytes long. Assuming a transmission rate of 11 Mbps, the time to transmit a control frame (such as an RTS frame, a CTS frame, or an ACK frame) is (256 bits)/(11 Mbps) = 23 usec. The time required to transmit the data frame is (8256 bits)/(11 Mbps) = 751 DIFS + RTS + SIFS + CTS + SIFS + FRAME + SIFS + ACK = DIFS + 3SIFS + (3*23 + 751) usec = DIFS + 3SIFS + 820 usec Selected questions from previous midterms 1. In this part of the question, all stations use the IEEE 802.11 MAC protocol, DIFS = 130 µs and aSlot = 50 µs. Assume that, while in the DCF mode of operation, station A generates a random value 12 for its BTC (Back-off Time Counter) at time instant t1. The carrier sensing mechanism of station A detects the medium to be busy/free as follows: - Busy for 400 µs from instant t1. - Free for 300 µs after the previous busy period. - Busy for 1000 µs after the previous free period. - Free for long enough for BTC to expire at some time instant t2. Compute the actual time gap between t2 and t1. Solution Only the last period X (free for long enough until BTC=0) is unknown. Δ= t -t = (400+300+1000+X)µs 2 1 DIFS: Distributed InterFrame Spaces; the medium needs to be idle for this period of time, before station can start transmitting. BTC: once medium is sensed to be idle for DIFS, BTC is decreased by one, then the medium is sensed again after an aSlot period. Every time, i.e. after an aSlot period, the medium is sensed to be idle, the counter is decremented. Station starts transmitting once medium is idle and BTC=0 t2-­‐t1 = 1700 + DIFS + 9*aSlot = 2280 300µs 400µs 1000µs DIFS 12 t1 DIFS 11 10 9 9 8 76 5 4 3 2 1 0 BTC=12 2. Three important time intervals in the operation of the IEEE 802.11 MAC protocol are DIFS, SIFS, and PIFS. - State the desired relationship among the three intervals, and explain where and why those intervals are used. - Explain the consequence(s) of a faulty protocol implementation where PIFS > DIFS. Solution Relation: SIFS<PIFS<DIFS • SIFS (Short Inter Frame Spacing): Is the smallest interval; gives the highest priority to on-going communications. Separates RTS, CTS, DATA, ACK. The ACK or RTS are sent after SIFS and before PIFS. • PIFS (Point Inter Frame Spacing): The second priority goes to Access Point. It gives the Access Point (working in PCF mode) a chance to grab the control of the channel. Access Point can either starts transmitting to the desired station or gives the permission to desired stations to communicate. PIFS>SIFS, to detect an on-going transmission. • DIFS (Distributed Inter Frame Spacing): Third (lowest) priority. After this interval all the stations, in DCF mode, start competing for the channel. DIFS>SIFS, to detect an on-going transmission. DIFS>PIFS, to give the priority to Access Point (see part 2). If PIFS>DIFS, stations in DCF mode have higher priority than Access Point. The Access Point can only grab the channel when no other station wants to transmit anything. It may take a long time before Access Point is being able to grab the control of the channel. 3. In the IEEE 802.11 standard, explain the function and operation of the Network Allocation Vector (Be sure to use a diagram to help in your explanation). Solution • • • • • In DCF mode, A sender obtains permission from the intended receiver before transmitting a packet by sending a Request to Send (RTS) packet The receiver granting permission by transmitting a Clear To Send (CTS) packet Stations other than the two communicating hearing either RTS or CTS will lock themselves out of the channel for a period of time – this is the Network Allocation Vector – NAV – this process is also called virtual carrier sense The objective is to provide collision avoidance or reduce the number of collisions (but preventing other stations from transmitting) It is important to note that stations may be within range of only one of the two communicating parties so they respond differently to the RTS and CTS messages.