Studying the Pervasiveness of Internet
advertisement
Studying the Pervasiveness of Internet Interception with Honey{POP,SMTP,Telnet}
Tavish Vaidya
Eric Burger
Micah Sherr
Clay Shields
Georgetown University
1 How common is interception?
§ Unencrypted communication is (still) very common
(e.g., HTTP, email, FTP, telnet, etc.)
§ Conventional wisdom tells us not to send sensitive
information over unencrypted channels. It does not tell
us the level of danger associated with sending
unencrypted info
§ Interception is easy -- but is it pervasive?
Goal: Find experimental evidence of interception
§ How often is unencrypted communication intercepted
(and acted upon)?
§ Where does interception occur?
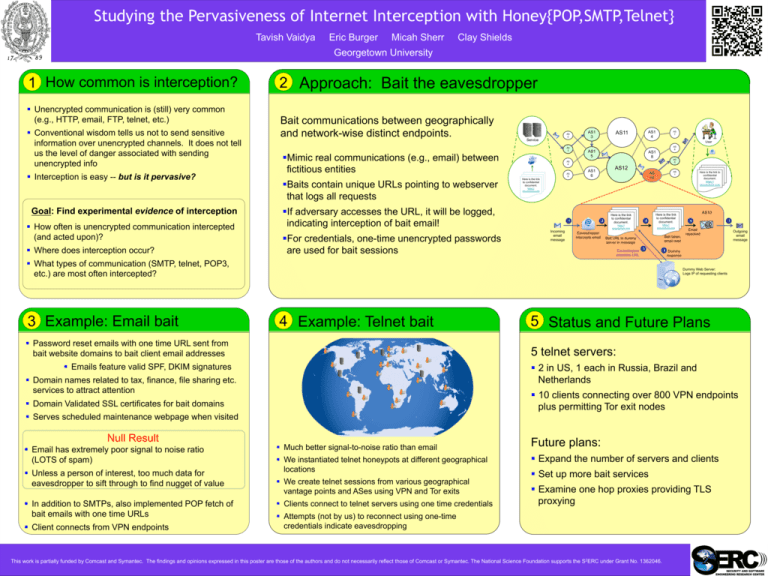
2 Approach: Bait the eavesdropper
Bait communications between geographically
and network-wise distinct endpoints.
AS
2
Service
§ Mimic real communications (e.g., email) between
fictitious entities
AS1
5
AS
7
AS
5
AS
8
AS1
8
AS
4
AS12
AS1
6
AS
9
AS
1
AS
10
Here is the link
to confidential
document.
1
Incoming
email
message
2
Here is the link
to confidential
document.
5
https://
secureshare.com
https://
secureshare.com
Eavesdropper
intercepts email
Here is the link
to confidential
document.
Bait taken,
email read
Bait URL to dummy
server in message
Eavesdropper
accesses URL
3
§ What types of communication (SMTP, telnet, POP3,
etc.) are most often intercepted?
3 Example: Email bait
4 Example: Telnet bait
§ Serves scheduled maintenance webpage when visited
§ Client connects from VPN endpoints
Outgoing
email
message
4 Dummy
response
5 Status and Future Plans
§ 10 clients connecting over 800 VPN endpoints
plus permitting Tor exit nodes
§ Domain Validated SSL certificates for bait domains
§ In addition to SMTPs, also implemented POP fetch of
bait emails with one time URLs
Email
repacked
@
7
§ 2 in US, 1 each in Russia, Brazil and
Netherlands
§ Domain names related to tax, finance, file sharing etc.
services to attract attention
§ Unless a person of interest, too much data for
eavesdropper to sift through to find nugget of value
6
5 telnet servers:
§ Emails feature valid SPF, DKIM signatures
§ Email has extremely poor signal to noise ratio
(LOTS of spam)
AS10
Dummy Web Server:
Logs IP of requesting clients
§ Password reset emails with one time URL sent from
bait website domains to bait client email addresses
Null Result
Here is the link to
confidential
document.
https://
secureshare.com
https://
secureshare.com
§ If adversary accesses the URL, it will be logged,
indicating interception of bait email!
§ For credentials, one-time unencrypted passwords
are used for bait sessions
AS1
4
User
AS
3
§ Baits contain unique URLs pointing to webserver
that logs all requests
AS11
AS1
3
§ Much better signal-to-noise ratio than email
§ We instantiated telnet honeypots at different geographical
locations
§ We create telnet sessions from various geographical
vantage points and ASes using VPN and Tor exits
§ Clients connect to telnet servers using one time credentials
Future plans:
§ Expand the number of servers and clients
§ Set up more bait services
§ Examine one hop proxies providing TLS
proxying
§ Attempts (not by us) to reconnect using one-time
credentials indicate eavesdropping
This work is partially funded by Comcast and Symantec. The findings and opinions expressed in this poster are those of the authors and do not necessarily reflect those of Comcast or Symantec. The National Science Foundation supports the S2ERC under Grant No. 1362046.