Encrypted File System (EFS) Implementation

Encrypted File System (EFS) Implementation
Overview
This is the first comprehensive project that is given to the students. This project is intended for make them understand almost all the fundamental concepts they have learnt in the class. Encrypted File System (EFS) provides the core file encryption technology used to store encrypted files on the File System. Traditional file system does not encrypt the files that are stored on a disk, so if the disk is stolen, contents of those files can be recovered. An Encrypted File System (EFS) solves this problem by encrypting all files on the disk, such that only users who know the encryption keys can access the files.
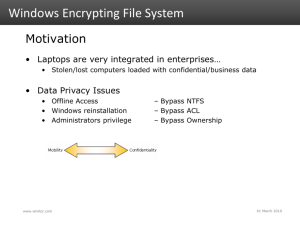
The primary benefit of the encrypted disk system is defense against device theft, and making your system a more secured one. Though, the risks are partially mitigated. We need the students to do the encryption/decryption operations transparent to users. Designing and implementing such a system require students to combine together the knowledge about encryption, key management, authentication, access control, and security in OS kernels and file systems.
Prerequisites
Have a basic understanding of what you mean by an encrypted file system
( Note: we are not asking you to build an entire new file system and not to demonstrate an encryption utility, but add security features to the existing file system and devise ways to encrypt / decrypt files using the encryption algorithms)
Required to go through how the encryption algorithm works (AES) in Minix
Operating System.
Go through the presentation about the various File System implementations.
Knowledge about encryption, key management, authentication, access control, security in the OS kernel, and file systems.
Challenges in the project
1.
Mounting a file system . - In my opinion, this is the hardest step. The mounting procedure basically is used to mount the encrypted file system. Here the user is given the flexibility to mount the file system on to any directory.
This forms the major part for the Encrypted File system.
2.
Reading and writing data on the way to/from user processes .
- This can't be too difficult, but would still take some time to figure out and get to work.
This is not that difficult, but the user should know which files he needs to change and where to insert the proper lines of code.
3.
Encrypting/decrypting the intercepted data blocks – Please use the AES algorithm for the Encryption and Decryption (Source: Rijndael Webpage, algorithm is on my Webpage http://web.syr.edu/~sasankar ). Accounting for size and file position changes are an important part while doing the encryption and decryption. The encrypting part should be very easy, almost trivial.
Calculating block sizes, splitting/combining blocks and calculating file offsets would take work. But the user doesn’t need to figure out how this happens since it happens automatically.
4.
The file pointer issues – This is not a major issue, but think of the ways by which you can deal with file pointer problems. But this is not that difficult a part that you cannot overcome.
5.
Buffer overflow problems – Will your system encounter buffer overflow? If so how are you going to deal with this? To my opinion, not a major issue.
6.
System Policy
– Think about how you are going to define the system security policy for the whole system.
Requirements & Some Important Things:
Students are required to design and implement a working encrypted file system for the Minix operating system. The students can work individually or in a group of 2-3 people. The whole system has to be designed and implemented matching the set of requirements stated below. We will award bonus points to those students who are providing creative and useful features.
You are required to submit a post lab report , which will contain the design about your implementation details, how you are planning to do the implementation, and all the relevant details that you would think would be needed. This report should be submitted within 10days the requirements are posted. Students will loose points if they do not meet the deadline date. Each group will have to demonstrate the system (demo) after the implementation.
Requirement 1
Demonstrate how are you planning to mount the file system. What are the key decisions you have taken with regard to this requirement?
Requirement 2
You have to demonstrate the whole implementation at the kernel level ( Note: No user level or library level implementations will be accepted)
Requirement 3
The architecture should enable individual users to have their keys for encrypting and decrypting files. You need to demo how the files are encrypted and decrypted in your implementation.
Requirement 4
Your implementation should demonstrate the management of the keys in the system.
How effectively have you done the key management, adding a new key, where have you stored your keys etc should be clearly demonstrated.
Requirement 5
The system should clearly demonstrate the file management i.e. file sharing, pass phrase sharing, and user transparency.
Requirement 6
Your system should demonstrate change of file ownership and revocation. (Hint: If a user is not interested in sharing his/her pass phrase with another user?).
Requirement 7
The system should authenticate the user trying to login to the system. If he is a valid user, the system should prompt him to enter his password and then he should be authenticated
If he has entered the password incorrectly, you can display an error message saying
“invalid password” and he should not be allowed to enter the system.
Requirement 8
Bonus points will be awarded to students who demonstrate user management and effective key management (A part of your creative design).
Demo for the project
After the students complete the project, each of them will present what they have implemented.
1.
Students are entirely responsible for showing the demo, in the way they feel is in accordance to the project. We will not even touch the keyboard during the demonstration; so don’t depend on us to test your system. If you fail to demo the important features of your system, we will assume that your system does not have those features.
2.
The total time of the demo will be 15mins, no more additional time would be given. So prepare your demonstration so you can cover the important features.
3.
During the demo, you should consider yourself as salesmen, and you want to sell your system to us. You are given 15 minutes to show us how good your system is.
So think about your sales strategies. If you have implemented a great system, but fail to show us how good it is, you won’t get good grade.
Some General Guidelines
Try running an EFS and see how it works to get an overall picture. Refer to the presentation on EFS.
Play around with the encryption algorithm to be comfortable as to how it works.
Have a look at the presentation slides on the implementation and design of various file systems.
Documents
Encrypted File System Presentation [ PPT ]
Websites
Steganographic File System (StegFS) for Linux [ PDF ]
Encrypted File System Project [ PPT ]
File System with integrated user management [ PDF ] ( link to PDF file there)
Cryptographic File System [ PDF ]
Windows2000 Encrypted File System [ ASP ]
CryptFS: A stackable Vnode encryption file system [ HTML ] ( link to PDF file there)





![[#SPEC-162] End-to-End Crypto](http://s3.studylib.net/store/data/007411769_1-d6d0a02f1d7fa9d60bcad2d0afe6cac5-300x300.png)