Classes of Routing Protocols
advertisement
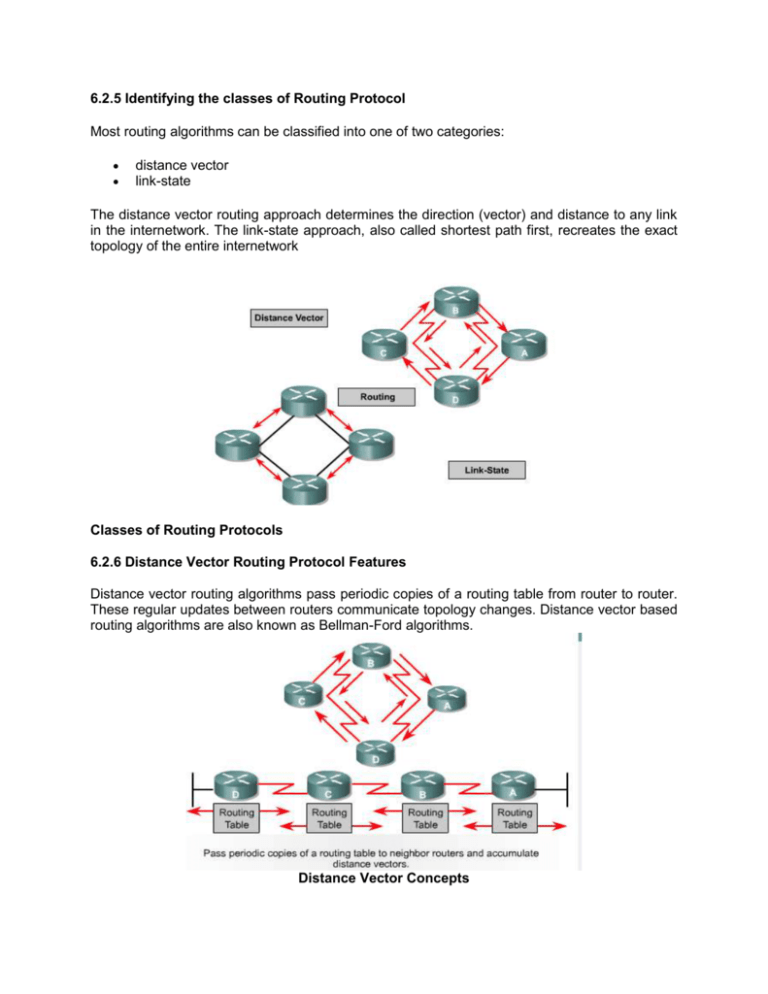
6.2.5 Identifying the classes of Routing Protocol Most routing algorithms can be classified into one of two categories: distance vector link-state The distance vector routing approach determines the direction (vector) and distance to any link in the internetwork. The link-state approach, also called shortest path first, recreates the exact topology of the entire internetwork Classes of Routing Protocols 6.2.6 Distance Vector Routing Protocol Features Distance vector routing algorithms pass periodic copies of a routing table from router to router. These regular updates between routers communicate topology changes. Distance vector based routing algorithms are also known as Bellman-Ford algorithms. Distance Vector Concepts Each router receives a routing table from its directly connected neighbor routers. Router B receives information from Router A. Router B adds a distance vector number (such as a number of hops), which increases the distance vector. Then Router B passes this new routing table to its other neighbor, Router C. This same step-by-step process occurs in all directions between neighbor routers. The algorithm eventually accumulates network distances so that it can maintain a database of network topology information. However, distance vector algorithms do not allow a router to know the exact topology of an internetwork as each router only sees its neighbor routers. Distance Vector Network Discovery Each router that uses distance vector routing begins by identifying its own neighbors. The interface that leads to each directly connected network is shown as having a distance of 0. As the distance vector network discovery process proceeds, routers discover the best path to destination networks based on the information they receive from each neighbor. Router A learns about other networks based on the information that it receives from Router B. Each of the other network entries in the routing table has an accumulated distance vector to show how far away that network is in a given direction. Distance Vector Topology Changes Routing table updates occur when the topology changes. As with the network discovery process, topology change updates proceed step-by-step from router to router. Distance vector algorithms call for each router to send its entire routing table to each of its adjacent neighbors. The routing tables include information about the total path cost as defined by its metric and the logical address of the first router on the path to each network contained in the table. Routing Metric Components An analogy of distance vector could be the signs found at a highway intersection. A sign points towards a destination and indicates the distance to the destination. Further down the highway, another sign points toward the destination, but now the distance is shorter. As long as the distance is shorter, the traffic is following the best path. 6.2.6 Link-state routing protocol features The second basic algorithm used for routing is the link-state algorithm. Link-state algorithms are also known as Dijkstras algorithm or as SPF (shortest path first) algorithms. Link-state routing algorithms maintain a complex database of topology information. The distance vector algorithm has nonspecific information about distant networks and no knowledge of distant routers. A linkstate routing algorithm maintains full knowledge of distant routers and how they interconnect. Link-state routing uses: Link-state advertisements (LSAs) – A link-state advertisement (LSA) is a small packet of routing information that is sent between routers. Topological database – A topological database is a collection of information gathered from LSAs. SPF algorithm – The shortest path first (SPF) algorithm is a calculation performed on the database resulting in the SPF tree. Routing tables – A list of the known paths and interfaces. Link-state Concepts Network discovery processes for link state routing LSAs are exchanged between routers starting with directly connected networks for which they have direct information. Each router in parallel with the others constructs a topological database consisting of all the exchanged LSAs. The SPF algorithm computes network reachability. The router constructs this logical topology as a tree, with itself as the root, consisting of all possible paths to each network in the link-state protocol internetwork. It then sorts these paths Shortest Path First (SPF). The router lists the best paths and the interfaces to these destination networks in the routing table. It also maintains other databases of topology elements and status details. Link-state Discovery Network The router that first becomes aware of a link-state topology change forwards the information so that all other routers can use it for updates. This involves sending common routing information to all routers in the internetwork. To achieve convergence, each router keeps track of its neighbor routers, the router name, interface status, and the cost of the link to the neighbor. The router constructs an LSA packet that lists this information along with new neighbors, changes in link costs, and links that are no longer valid. The LSA packet is then sent out so that all other routers receive it. Link-state Topology Changes When the router receives an LSA, the database is updated with the most recent information and computes a map of the internetwork using the accumulated data and calculates the shortest path to other networks using the SPF algorithm. Each time an LSA packet causes a change to the link-state database, SPF recalculates the best paths and updates the routing table. Link-state concerns: Processor overhead Memory requirements Bandwidth Consumption Routers running link-state protocols require more memory and perform more processing than distance vector routing protocols. Routers must have sufficient memory to be able to hold all the information from the various databases, the topology tree, and the routing table. Initial link-state packet flooding consumes bandwidth. During the initial discovery process, all routers using linkstate routing protocols send LSA packets to all other routers. This action floods the internetwork and temporarily reduces bandwidth available for routed traffic carrying user data. After this initial flooding, link-state routing protocols generally require only minimal bandwidth to send infrequent or event triggered LSA packets reflecting topology changes. 6.3 Routing Protocols Overview 6.3.1 Path Determination A router determines the path of a packet from one data link to another, using two basic functions: A path determination function A switching function Path determination occurs at the network layer. The path determination function enables a router to evaluate the paths to a destination and to establish the preferred handling of a packet. The router uses the routing table to determine the best path and proceeds to forward the packet using the switching function. The switching function is the internal process used by a router to accept a packet on one interface and forward it to a second interface on the same router. A key responsibility of the switching function of the router is to encapsulate packets in the appropriate frame type for the next data link. Figure 5 illustrates how routers use addressing for these routing and switching functions. The router uses the network portion of the address to make path selections to pass the packet to the next router along the path. 6.3.2 Routing Configuration Enabling an IP routing protocol on a router involves the setting of both global and routing parameters. Global tasks include selecting a routing protocol, such as RIP, IGRP, EIGRP or OSPF. The major task in the routing configuration mode is to indicate IP network numbers. Dynamic routing uses broadcasts and multicasts to communicate with other routers. The routing metric helps routers find the best path to each network or subnet. The router command starts a routing process. Router(config)# router protocol - defines an IP routing protocol Router(config-router)# network network-number - The network subcommand is a mandatory configuration command for each IP routing process. The network command is required because it enables the routing process to determine which interfaces participate in the sending and receiving of routing updates. An example of a routing configuration is: GAD(config)#router rip GAD(config-router)#network 172.16.0.0 The network numbers are based on the network class addresses, not subnet addresses or individual host addresses. Major network addresses are limited to Class A, B, and C network numbers. 6.3.3 Routing Protocols At the Internet layer of the TCP/IP suite of protocols, a router can use an IP routing protocol to accomplish routing through the implementation of a specific routing algorithm. Examples of IP routing protocols include: RIP – A distance vector interior routing protocol IGRP – Cisco's distance vector interior routing protocol OSPF – A link-state interior routing protocol EIGRP – Cisco’s advanced distance vector interior routing protocol BGP – A distance vector exterior routing protocol Routing Information Protocol (RIP) was originally specified in RFC 1058. Its key characteristics include the following: It is a distance vector routing protocol. Hop count is used as the metric for path selection. If the hop count is greater than 15, the packet is discarded. Routing updates are broadcast every 30 seconds, by default. Interior Gateway Routing Protocol (IGRP) is a proprietary protocol developed by Cisco. Some of the IGRP key design characteristics emphasize the following: It is a distance vector routing protocol. Bandwidth, load, delay and reliability are used to create a composite metric. Routing updates are broadcast every 90 seconds, by default. Open Shortest Path First (OSPF) is a nonproprietary link-state routing protocol. The key characteristics of OSPF are as follows: It is a link-state routing protocol. Open standard routing protocol described in RFC 2328. Uses the SPF algorithm to calculate the lowest cost to a destination. Routing updates are flooded as topology changes occur. EIGRP is a Cisco proprietary enhanced distance vector routing protocol. The key characteristics of EIGRP are as follows: It is an enhanced distance vector routing protocol. Uses load balancing. Uses a combination of distance vector and link-state features. Uses Diffused Update Algorithm (DUAL) to calculate the shortest path. Routing updates are broadcast every 90 seconds or as triggered by topology changes. Border Gateway Protocol (BGP) is an exterior routing protocol. The key characteristics of BGP are as follows: It is a distance vector exterior routing protocol. Used between ISPs or ISPs and clients. Used to route Internet traffic between autonomous systems 6.3.4 Autonomous System and IGP versus EGP Interior routing protocols are designed for use in a network whose parts are under the control of a single organization. The design criteria for an interior routing protocol require it to find the best path through the network. In other words, the metric and how that metric is used is the most important element in an interior routing protocol. An exterior routing protocol is designed for use between two different networks that are under the control of two different organizations. These are typically used between ISPs or between a company and an ISP. For example, a company would run BGP, an exterior routing protocol, between one of its routers and a router inside an ISP. IP exterior gateway protocols require the following three sets of information before routing can begin: A list of neighbor routers with which to exchange routing information. A list of networks to advertise as directly reachable. The autonomous system number of the local router. An exterior routing protocol must isolate autonomous systems. Remember, autonomous systems are managed by different administrations. Networks must have a protocol to communicate between these different systems. Autonomous systems have an identifying number, which is assigned to it by the American Registry of Internet Numbers (ARIN) or a provider. This autonomous system number is a 16-bit number. Routing protocols such as Cisco’s IGRP and EIGRP require that a unique, autonomous system number be assigned. 6.3.5 Distance Vector Distance vector algorithms (also known as Bellman-Ford algorithms) call for each router to send all or some portion of its routing table only to its neighbors. Distance vector algorithms perform routing decisions based upon information provided by neighboring routers. Distance vector protocols use fewer system resources but can suffer from slow convergence and may use metrics that do not scale well to larger systems. Distance vector protocols are based on finding the distance (number of hops) and vector (direction) to any link on the internetwork. The algorithms involve passing copies of a complete routing table from router to router on a periodic basis. This type of routing protocol requires that each router simply inform its neighbors of its routing table. For each network path, the receiving routers pick the neighbor advertising the lowest cost and then adds this entry into their routing table for readvertisement. RIP and IGRP are common distance vector routing protocols 6.3.6 Link-state Link-state algorithms (also known as shortest path first algorithms) flood routing information to all routers in the internetwork that creates a map of the entire network. Each router sends packets to all its neighbors. These packets contain descriptions of the network or networks to which the router is linked. The routers assemble all the information into a complete view of the internetwork topology to calculate the shortest path to all known sites on the network. It then generates routing tables showing the best path for any destination on the network. Once converged, link state protocols use small update packets, which contain only changes rather than copies of the entire routing table. Update packets are passed across the network in eventtriggered updates, so convergence is fast. Because they converge more quickly than distance vector protocols, link-state algorithms are less prone to routing loops. Link-state protocols are also less prone to routing errors, but they use more system resources. Link-state protocols, therefore, can be more expensive to implement and support. However, they are generally more scalable than distance vector protocols. When a network link changes state, a notification called a link-state advertisement (LSA) is flooded throughout the network. All the routers note the change and adjust their routes accordingly. This method is more reliable, easier to debug, and less bandwidth-intensive than distance vector. OSPF and IS-IS are examples of link-state routing protocols Summary An understanding of the following key points should have been achieved: A router will not forward a packet without a route to a destination network. Network administrators manually configure static routes. Default routes are special static routes that provide routers with gateways of last resort. Static and default routes are configured using the ip route command. Static and default route configuration can be verified using the show ip route, ping, and traceroute commands. Verify and troubleshoot static and default routes Routing protocols Autonomous systems Purpose of routing protocols and autonomous systems The classes of routing protocols Distance vector routing protocol features and examples Link-state protocol features and examples Route determination Routing configuration Routing protocols (RIP, IGRP, OSPF, EIGRP, BGP) Autonomous systems and IGP versus EGP Distance vector routing Link-state routing

![Internetworking Technologies [Opens in New Window]](http://s3.studylib.net/store/data/007474950_1-04ba8ede092e0c026d6f82bb0c5b9cb6-300x300.png)






