High Performance Computing: An Introduction
advertisement
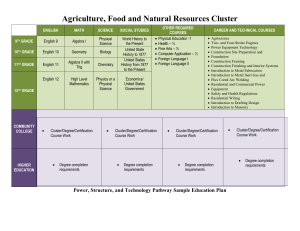
TCP/IP Security Protocol Suite for High Performance Computing Systems Harish Rohil, Assistant Professor (CSA), Ch. Devi Lal University, Sirsa [1] Vikas Kamra, M.Tech (CSE), Ch. Devi Lal University, Sirsa [2] ABSTRACT High Performance Computing Systems (HPCS) aims to do complex and large computations in an environment where work is performed by many communicating computers on a single task. To provide security in high performance computing systems is a difficult task. Operating systems, distributed environments and Internet currently suffer from poor security. They cannot resist common security attacks. The paper aims to apply various existing technologies at different levels of security on HPCS which leads to an increased rank of security. This paper intends to achieve three major tasks. First, it divides the security in levels, second it covers how to define these levels on architectures and third it proposes the existing technologies of TCP/IP on the levels defined here. In this paper we propose a solution for applying TCP/IP Security Protocol Suite to high performance computing systems. KEYWORDS: CLUSTER SECURITY, GRID SECURITY, HPCS HIGH PERFORMANCE COMPUTING: AN INTRODUCTION High performance computing is best achieved by parallelism. Parallelism (using parallel computers) is one of the best ways to overcome the speed bottleneck of single processors. Many computer systems supporting high performance computing have emerged like MPP, SMP, Distributed Systems, Cluster, and Grid. Their taxonomy is based on how their Processor, memory and interconnect are laid out. Cluster and Grid both are sincere source of High Performance computing. Cluster is type of distributed processing system which consists of a collection of interconnected standalone computers working together as a single integrated computing resource. Grid as a system that coordinates distributed resource using standard, open general purpose protocol and interfaces to deliver non trivial quality of services. Security is very important in every work platform. Security in Cluster and Grid deals with the issues of Security at Resource level, Security at Communication level, Security at User level. Various Security disciplines are Authentication, Delegation, Single sign on, Credential life span and renewal, Authorization, Privacy, Confidentiality, Message Integrity, Policy Exchange, Secure Logging, Assurance, Manageability, and Firewall Traversal. Security Facilities in TCP/IP Protocol Suite IPsec provide security to IP layer. It provides the capability to secure communication across a LAN and across the internet. IPsec encompasses three functional areas like Authentication, Confidentiality, Key Management. Authentication Header (AH) protocol, Encryption Security Payload (ESP), Internet security Association and key management protocol (ISAKMP) are the working protocols of IPsec. Secure Socket layer (SSL) make use of TCP to provide a reliable end to end secure services. SSL is combination of four Protocols. i) SSL Record Protocol. ii) SSL Handshake Protocol. iii) SSL Change Cipher Specification Protocol. iv) SSL Alert Protocol. Application layer security is achieved by all these facilities. One of them is Kerberos. Kerberos is an Authentication service designed for use in a Distributed Environment. Kerberos makes use of a trusted third part Authentication service that enables client and server to establish authenticated communication. Secure/Multipurpose Internet Mail Extension (S/MIME) is a security environment to the MIME internet E-Mail format standard, based on technology from Rivest Shannon Algorithm data security. Pretty Good Policy (PGP) Provides Confidentiality and Authentication service that can be used for electronic mail and file storage application. PGP provide five services i) Authentication ii) Confidentiality iii) Compression iv) E-Mail Compatibility v) Segmentation. Secure Electronic Transaction (SET) it is an open Encryption and security specification designed to protect credit card transaction on the internet. Figure 1: Security Facilities in TCP/IP Protocol Suite SECURITY APPLYING IN CLUSTER ARCHITECTURE Cluster Architecture includes High Speed Network/Switch layer, PC workstation, communication software, and Network Interface Hardware layer SSI and Availability infrastructure, Sequential, Parallel Application Parallel Programming Environments. High Speed Network/Switch layerThis part in the Cluster Architecture is responsible for the communication in between the nodes. Every Node in the Cluster is attached to this i.e. Gigabit Ethernet and Myrinet. So need of Communication Level Security is arrived here PC workstation, communication software, Network Interface Hardware layer- this layer consist of many high performance computers. Communication software offers fast and reliable data communication with the help of high speed Network. Network Interface Hardware acts as a Communication Processor and is responsible for transmitting and receiving packets of data between cluster nodes via network/interfaces so need of Resource and Communication Level Security is required here. SSI and Availability infrastructure-this layer is also known as cluster middleware layer which is responsible for providing unified system image. Sequential, Parallel Application Parallel Programming Environments-this layer includes Applications and tools like Compiler, PVM and MPI. That is the reason that’s why User Level Security is applying here. Figure 2: Cluster Architecture SECURITY APPLYING IN GRID ARCHITECTURE Grid Architecture is layered Architecture it includes four layers these are Fabric, Resource and Connectivity, Collective and finally User Application Layer. Fabric Layer- The Fabric layer provides the Resources to which shared access is required .So need of Resource Level security is arrived here. Resource and Connectivity Layer- Resource Layer include two types of protocols one is information and another one is Management for Resources. Connectivity layer defines core communication and authentication protocols. Communication protocols enable the exchange of data between fabric layer resources. So need for both Resource and Communication level security is arrived. Collective Layer- contains protocols and services not associated with anyone specific resource but instead capturing interaction across collection of resources. It provides directory, co-allocation, and scheduling, brokering, monitoring, data replication services. So, need of communication level security is arrived here. User Application Layer- The final layer n our Grid Architecture comprises the user application that operate within a VO environment. So, here User level security is needed. Figure 3: Grid Architecture SECURITY ACHIEVE THROUGH EXISTING TECHNOLOGIES There are many technologies existing that are following different security disciplines. Here we are applying technologies that were actually applied on TCP/IP model and then we will propose these technologies to security levels. Table 1 is defining this relationship between levels, disciplines, and technologies. like to say User application level need to follow Authentication, Authorization and Confidentiality etc. According to TCP/IP model Application Level Security can be achieved by Kerberos, S/MIME, PGP, SET technologies and these technologies can satisfy the disciplines required to follow at User/Application level. Communication Level Security needs to follow Privacy in communication Message Integrity required policy Exchange is required to negotiation between two authorized parties. Firewall Traversal, Delegation, Single Sign On, Credential life span and renewal are also required at communication level. SSL/TLS work on Transport layer in TCP/IP model so some of disciplines required at communication level can be satisfied by this. Although we need some technologies extra then SSL/TLS yet it solve purpose up to some extent. Resource level security need to follow Secure logging, Assurance, Manageability disciplines. IPsec is working on IP layer so it can provide resource level security up to some extent. Table 1: Technologies Applied on Different Levels CONCLUSION Cluster and Grid systems are good example of HPCS. Requirement of security in HPCS is not ignorable. Security is best defined by its discipline. Security can be divided into three levels User, Resource and Communication Level. TCP/IP model is well known model for Communication. Layer by layer security is applied in TCP/IP model. This paper presents the Cluster and Grid Architecture and security level applied on each layer of Architectures. Lastly, we gave a proposal of applying existing technologies from TCP/IP on cluster and grid Architecture by security levels. Every security technology is having constraints. Constraints of technology and architecture should be compatible like no. of users in communication like key management issues like intrusion detection and policy management. REFERENCES [1] Journal of Grid Computing Main editor: P. Kacsuk ISSN: 1570-7873 (print version) Journal no. 10723 Springer, Netherlands. [2] High Performance Computing and Communications. Second International Conference, HPCC 2006, Munich, Germany, Vol. 4208, p. 938, ISBN: 978-3-540-39368-9. [3] Research on Security Architecture and Protocols of Grid Computing System by Xiangming Fang, Shoubao Yang , Leitao Guo and Lei Zhang. [4] Jean-Francois Lalande, David Rodriguez and Christian Toinard, Security Properties in an Open Peer-to-Peer Network, International Journal of Network Security & Its Applications, Academy & Industry Research Collaboration Center, Vol.1, No.3, pp.73-89, October 2009. [5] Cryptography and Network security principles and practices by William Stallings. ISBN-81203-3018-8. [6] High performance Cluster Computing by Raj Kumar Buyya. ISBN-978-81-317-1693-9. [7] Foster, I., Kesselman, C.: The Grid: Blueprint for a New Computing Infrastructure. Morgan Kaufmann, San Francisco (1999).