Potential Pohlig-Hellman decomposition attack on APKAS-AMP
advertisement
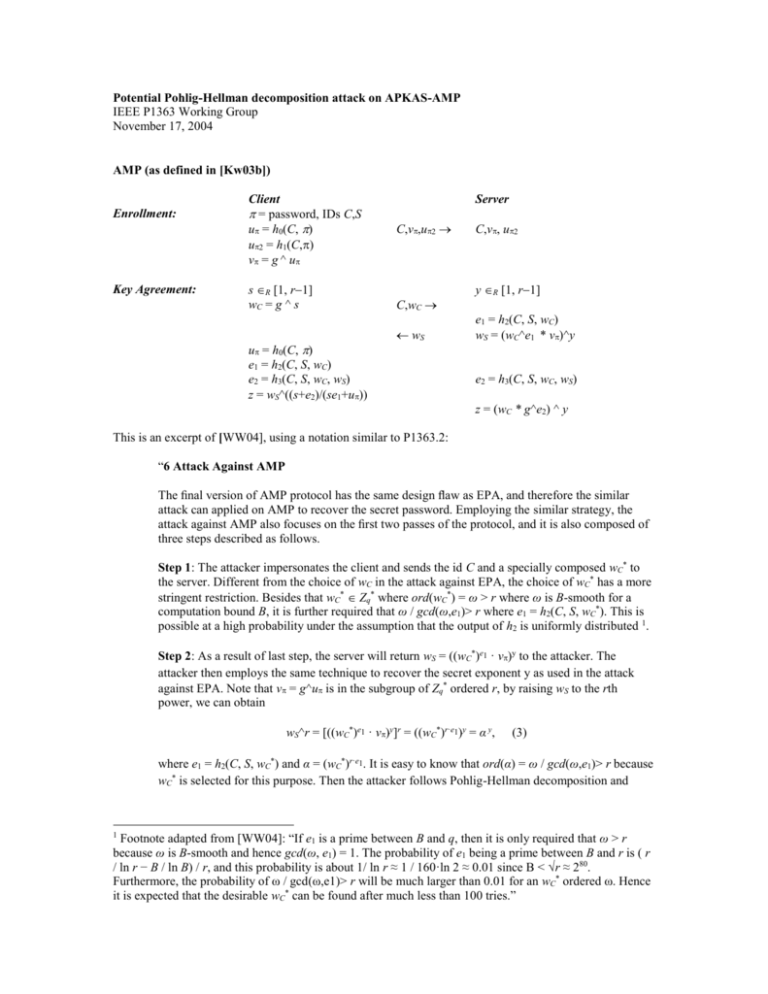
Potential Pohlig-Hellman decomposition attack on APKAS-AMP IEEE P1363 Working Group November 17, 2004 AMP (as defined in [Kw03b]) Enrollment: Key Agreement: Client = password, IDs C,S u = h0(C, ) u2 = h1(C,) v = g ^ u s R [1, r1] wC = g ^ s u = h0(C, ) e1 = h2(C, S, wC) e2 = h3(C, S, wC, wS) z = wS^((s+e2)/(se1+u)) Server C,v,u2 C,wC wS C,v, u2 y R [1, r1] e1 = h2(C, S, wC) wS = (wC^e1 * v)^y e2 = h3(C, S, wC, wS) z = (wC * g^e2) ^ y This is an excerpt of [WW04], using a notation similar to P1363.2: “6 Attack Against AMP The final version of AMP protocol has the same design flaw as EPA, and therefore the similar attack can applied on AMP to recover the secret password. Employing the similar strategy, the attack against AMP also focuses on the first two passes of the protocol, and it is also composed of three steps described as follows. Step 1: The attacker impersonates the client and sends the id C and a specially composed wC* to the server. Different from the choice of wC in the attack against EPA, the choice of wC* has a more stringent restriction. Besides that wC* Zq* where ord(wC*) = ω > r where ω is B-smooth for a computation bound B, it is further required that ω / gcd(ω,e1)> r where e1 = h2(C, S, wC*). This is possible at a high probability under the assumption that the output of h2 is uniformly distributed 1. Step 2: As a result of last step, the server will return wS = ((wC*)e1 · v)y to the attacker. The attacker then employs the same technique to recover the secret exponent y as used in the attack against EPA. Note that v = g^u is in the subgroup of Zq* ordered r, by raising wS to the rth power, we can obtain wS^r = [((wC*)e1 · v)y]r = ((wC*)r·e1)y = α y, (3) where e1 = h2(C, S, wC*) and α = (wC*)r·e1. It is easy to know that ord(α) = ω / gcd(ω,e1)> r because wC* is selected for this purpose. Then the attacker follows Pohlig-Hellman decomposition and Footnote adapted from [WW04]: “If e1 is a prime between B and q, then it is only required that ω > r because ω is B-smooth and hence gcd(ω, e1) = 1. The probability of e1 being a prime between B and r is ( r / ln r − B / ln B) / r, and this probability is about 1/ ln r ≈ 1 / 160·ln 2 ≈ 0.01 since B < √r ≈ 280. Furthermore, the probability of ω / gcd(ω,e1)> r will be much larger than 0.01 for an wC* ordered ω. Hence it is expected that the desirable wC* can be found after much less than 100 tries.” 1 Pollard’s methods to recover y0 = y mod ω / gcd(ω,e1) . Since y Zq* and ω / gcd(ω,e1)> r, we claim that y0 = y. Step 3: At last, the attacker can mount a dictionary attack against wS to recover the password π on the basis of last step. With the knowledge of y, the attacker can easily obtain wS as follows: −1 v = [wS · (wC*)−e1·y]y = gh0(C,π). (4) Then a dictionary attack against equation (4) can yield the secret password π.” References [WW04] Z. Wan & S. Wang, Cryptanalysis of Two Password-Authenticated Key Exchange Protocols, H. Wang et al. (Eds.): ACISP 2004, LNCS 3108, pp. 164-175, Springer-Verlag, Berlin, Heidelberg, 2004. <http://jablon.org/passwordlinks.html#WW04> [Kw03b] T. Kwon, Addendum to Summary of AMP, Contribution to IEEE P1363 working group, received November 20 2003. <http://grouper.ieee.org/groups/1363/passwdPK/contributions/ampsummary2.pdf>






