Chapter 6 Hashing
advertisement

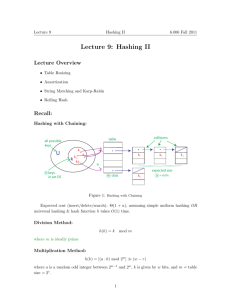
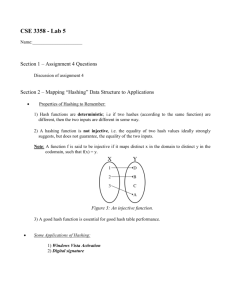
Chapter 6 Hashing Dictionary operations: Dictionary implementations and complexity of operations unsorted array— sorted array linked list Hashing 1. 2. 3. Potential problems we have to work around: Open Hashing (Separate Chaining) Notation: A[0]…A[m-1] h Hash Functions Characteristics of a good hash function 1. 2. Hash Functions A commonly used hash function is obtained by choosing a prime number p as the table size with function h(key) = key (mod p). Consider the hash function h(x) = x2 (mod 10). Two other hashing strategies--truncation and folding: Treating the key as a string More hash functions function h(s) z0 for i 0 to k-1 do z (z + s[i]*W[i])mod q z z mod m return z Also read about the polynomial hash function on p. 205. Complexity of the Find Operation Assumptions: 1. 2. Space required: Worst case time complexity The load factor of a hash table is the ratio of the number of items in the table to the size of the table. notation: = n/m. A probe is an access into the data structure. a. unsuccessful search— b. successful search— Closed Hashing—Open Addressing Collision resolution strategies linear probing 0 1 X 2 X 3 X 4 5 6 X 7 8 X 9 10 Suppose the next item to be placed in the table hashes to 3. Claim (without proof) The expected number of probes is ½ [1 + 1/(1 - 2)] for insertions and unsuccessful searches and ½ [1 + 1/(1 - )] for successful searches. Hash Table Deletions Other Collision Resolution Strategies Quadratic probing is a collision resolution strategy in which i2 is the increment where i is the number of collisions encountered. Double hashing uses a second hash function h2 to help determine where the element will be placed. Rehashing is used to rebuild the hash table when it gets too full.