Lab 1
advertisement

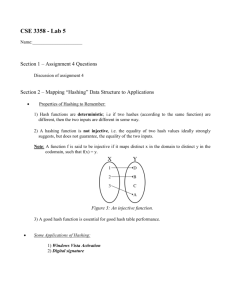
CSE 3358 - Lab 5 Name:______________________ Mapping “Hashing” Data Structure to Applications Properties of Hashing to Remember: 1) Hash functions are deterministic; i.e if two hashes (according to the same function) are different, then the two inputs are different in some way. 2) A hashing function is not injective, i.e. the equality of two hash values ideally strongly suggests, but does not guarantee, the equality of the two inputs. Note: A function f is said to be injective if it maps distinct x in the domain to distinct y in the codomain, such that f(x) = y. Figure 3: An injective function. 3) A good hash function is essential for good hash table performance. Some Applications of Hashing: 1) Windows Vista Activation 2) Digital signature 1) Windows Vista Activation: Product activation: is a license validation procedure required by some computer software programs. Specifically, product activation refers to a method where a software application Hashes hardware serial numbers and an ID number specific to the product's license (a product key) to generate a unique Installation ID. Installation ID is sent to the manufacturer to verify the authenticity of the product key and determine that the product key is not being used for multiple installations. Question 1: If I uninstall the OS from the computer and I install it again on the same computer, will it allow me to reactivate? What if I install it on another machine? Question 2: What guarantees that there will not be any intruder in the middle of the authentication process? Answer: Use cryptography. 2) Digital Signature: Some definitions: Cryptography: Is the study of message secrecy. Asymmetric Cryptography( Public key Cryptography): is a form of cryptography in which a user has a pair of cryptographic keys - a public key and a private key. The private key is kept secret, while the public key may be widely distributed. The keys are related mathematically, but the private key cannot be practically derived from the public key. A message encrypted with the public key can only be decrypted with the corresponding private key. The two main branches of Asymmetric Cryptography are: 1) Public key encryption: a message encrypted with a user's public key cannot be decrypted by anyone except the user possessing the corresponding private key. This is used to ensure confidentiality. 2) Digital Signatures: a message signed with a user's private key can be verified by anyone who has access to the user's public key, thereby proving that the user signed it and that the message has not been tampered with. This is used to ensure authenticity. An analogy for public key encryption is that of a locked mailbox with a mail slot. The mail slot is exposed and accessible to the public; its location (the street address) is in essence the public key. Anyone knowing the street address can go to the door and drop a written message through the slot. However, only the person who possesses the key can open the mailbox and read the message. An analogy for digital signatures is the sealing of an envelope with a personal wax seal. The message can be opened by anyone, but the presence of the seal authenticates the sender. Example: Figure 1: A big random number is used to make a public-key pair. Figure 2: Anyone can encrypt using the public key, but only the holder of the private key can decrypt. Secrecy depends on the secrecy of the private key. Figure 3: Using a private key to encrypt (thus signing) a message; anyone can check the signature using the public key. Validity depends on private key security. How is hashing involved? The most obvious application of a public key encryption system is confidentiality and non-repudiation; a message which a sender encrypts using the recipient's public key can only be decrypted by the recipient's paired private key. Public-key digital signature algorithms can be used for sender authentication. For instance, a user can encrypt a message with his own private key and send it. If another user can successfully decrypt it using the corresponding public key, this provides assurance that the first user (and no other) sent it. In practice, a cryptographic hash value of the message is calculated (as shown in figure 4), encrypted with the private key and sent along with the message (resulting in a cryptographic signature of the message). The receiver can then verify message integrity and origin by calculating the hash value of the received message and comparing it against the decoded signature (the original hash). If the hash from the sender and the hash on the receiver side do not match, then the received message is not identical to the message which the sender "signed", or the sender's identity is wrong. Figure 4: A hash function at work Question: What prevents us from man in the middle attack. Another way said, what prevents a hacker from finding a message that has a specific hash value. Answer: Preimage Attack: a preimage attack on a cryptographic hash is an attempt to find a message that has a specific hash value. Given a fixed message m1, find a different message m2 such that hash(m2) = hash(m1). Solution: One Way Function: A one-way function is a function that is easy to compute but hard to invert — given the output of the function it is difficult to find any input which yields this output.